Fundamentals of Linux system (6) – permission management
1. Basic concept of authority
☆ why set permissions
1) Data value in server
2) Employees have different job responsibilities and division of labor
3) Respond to external attacks
4) Internal management needs
☆ type of authority
| For file | For directory | |
|---|---|---|
| Read r | Indicates that the file content can be viewed; cat | Indicates that you can (ls) view the file name existing in the directory |
| Write w | Indicates that the contents of the file can be changed; vim modify, save and exit | Indicates whether you can delete sub files in the directory or create a new sub directory (rm/touch/mkdir) |
| Execute x | Indicates whether the program in the file can be called. Generally, it refers to binary file (. SH) = > green | Indicates whether you can enter the directory (cd) |
☆ who is the authority assigned to
File owner: u ser
File ownin g group: Group
Other user (o): other
The permissions are allocated according to the above three categories of users.
2. General authority management
☆ view of authority
ls -l file #View file permissions ls -ld dir #View directory permissions
The attributes of a file are called meta data
A kind of metadata is recorded in 1 byte.
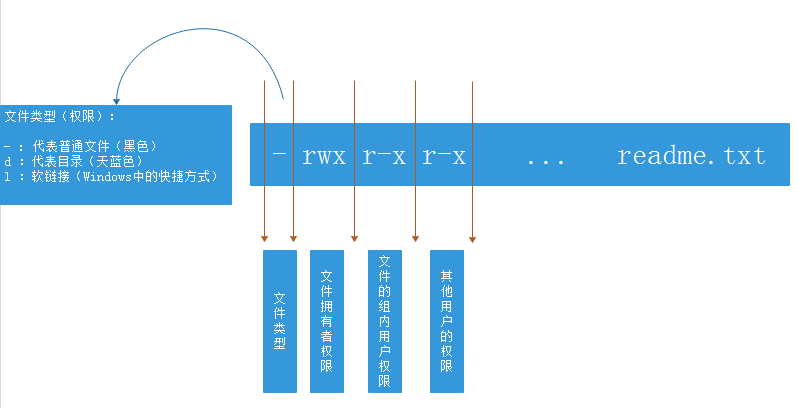
ls -l the information viewed is divided into nine columns
Column 1: document type
- ordinary documents
d directory
l soft link (shortcut in windows)
Block b equipment (hard disk drive, optical drive, etc.)
c character device
s socket
p pipe
Column 2: permission bits
The first three are the permissions of the file owner, the middle three are the permissions of the file owner group, and the last three are the permissions of other users.
Column 3: selinux startup of the system
Column 4: number of nodes in the file
Column 5: document owner
Column 6: File owning group
Column 7: for files: file content size
For directory: the metadata size of the sub file in the directory
Column 8: the time when the contents of the document were last modified
Column 9: file name
☆ setting of general authority
Setting permissions in character mode
chmod u + r file/dir -R #a=all means all users - R means recursion
g - w
o = x
a
eg:
chmod a-rwx /mnt/test
chmod u=rwx,g=rx,o=--- /mnt/test
chmod -R u=rwx,g=rx,o=--- /mnt/testdir/
Setting permissions in digital mode
| jurisdiction | Corresponding number | significance |
|---|---|---|
| r | 4 | readable |
| w | 2 | Writable |
| x | 1 | Executable |
| - | 0 | No permission |
rwx = 111 = 7 rw- = 110 = 6 r-x = 101 = 5 r-- = 100 = 4 -wx = 011 = 3 -w- = 010 = 2 --x = 001 = 1 --- = 000 = 0 eg: chmod 777 /mnt/test #That is, the file is full of permissions
Copy permissions
chmod --reference=/tmp /mnt/test #Permission to copy / tmp directory / mnt/test chmod -R --reference=/tmp /mnt/test/ #Copy / tmp permission to / mnt/test and its sub files
3. System default permissions
☆ what is umask
umask indicates the default permissions when creating files
Under the root user, the default permission of touch a and file a is 644
For ordinary users, the default permission of touch b and file b is 664
What determines the above is the value of umask.
Actual file permission = highest permission - value of umask
File default permission = 777-umask-111
Directory default permission = 777 umask
☆ view / modify umask
umask #View umask 0022 #The first 0 indicates special permission #The default value of umask is different under root and ordinary users, which are 022 and 002 respectively #Modify umask temporarily umask 002 #Permanently modify umask vim /etc/bashrc #shell system configuration file 74 if [ $UID -gt 199 ] && [ "`id -gn`" = "`id -un`" ]; then 75 umask 002-->022 #umask for ordinary users 76 else 77 umask 022 #umask of root user 78 fi vim /etc/profile #System environment profile 59 if [ $UID -gt 199 ] && [ "`id -gn`" = "`id -un`" ]; then 60 umask 002-->022 #umask for ordinary users 61 else 62 umask 022 #umask of root user 63 fi source /etc/bashrc #source enables our changes to be immediately recognized by the system source /etc/profile
4. Document owner and owner group management
chown username file #Change file owner chgrp groupname file #Change file ownership group chown root:root readme.txt #Simultaneous changes chown root.root readme.txt #Simultaneous changes #The - R parameter can be added to the above commands, indicating recursive modification
5. Special authority
☆ sticky position
Function: only the creator and root user of the file are allowed to delete the file (anti false deletion permission bit)
1.open stickyid: chmod 1 Original permissions dir chmod o+t dir 2.close stickyid: chmod 0 Original permissions dir chmod o-t dir
☆ forced bit (sgid)
Function: the newly created files in the directory automatically belong to the group to which the directory belongs
1.Enable forced bit: chmod 2 Original permissions dir chmod g+s dir 2.Off force bit: chmod 0 Original permissions dir chmod g-s dir
☆ suid
effect:
Only for binary executable files (c programs). When running binary executable files, they are run as the file owner, which has nothing to do with the execution user.
1.open suid: chmod 4 Original permissions file chmod u+s file
6.ACL access control
ACL = Access Control List
In Linux system, ACL can set the permission to access files for a single user.
Whether the ACL is enabled can be checked through ls -l. if there is + at the end of the permission bit, it indicates that the ACL is enabled, and no + indicates that the ACL is not enabled.
1.obtain ACL jurisdiction getfacl File or directory name Tips: If on ACL Don't use ls -l To query permission information. 2.set up ACL setfacl -m u:student:rw file #Set specified user permissions setfacl -m g:test:rw file #Set permissions for the specified group setfacl -m u::rwx file #Set file owner permissions setfacl -m g::0 file #Set file group permissions setfacl -x u:student file #Delete lee from the list setfacl -b file #Close acl #The above commands are effective for existing files, and new files will not be set #Effective for new files in / mnt/dir Directory: setfacl -m d:u:student:rwx /mnt/dir/
7.attr authority
attr permission limits all users (including root)
1.see attr jurisdiction lsattr dir|file 2.set up attr jurisdiction chattr +i dir|file #No one can modify it chattr -i dir|file chattr +a dir|file #Add only, delete not allowed chattr -a dir|file