##########1, Features of Selinux###############
1. Observation
When Selinux is not turned on
The files created in / mnt are moved to / var/ftp and can be accessed by vsftpd service
Anonymous users can upload files after setting
Displays "? When viewing a file using ls -Z /var/ftp
When selinux is on:
The files created in / mnt are moved to / var/ftp and cannot be accessed by vsftpd service
Anonymous users can still not upload files after setting
Displays information when viewing a file using ls -Z /var/ftp
selinux:
Impact on documents:
When selinux is turned on, the kernel will load labels for each file and each open program
The security context of programs and files is recorded in the tag
Impact on program functions:
When selinux is turned on, it will load the switch for the function of the program and set the status of this switch to off
When this function is required, the function switch needs to be turned on manually
This switch is called sebool
#########2, Status and management of Selinux##########
1. Enable SELinux
vim /etc/selinux/config
SELINUX=disabled # selinux shutdown
SELINUX=enforcing # selinux startup is set to the forced state. This state is selinux startup
SELINUX=permissive # selinux boot is set to the warning state. This state is selinux on
"selinux needs to restart the system to start or shut down"
enforcing: if the conditions are not met, it must not be allowed, and a warning message will be received
Permission: if the conditions are not met, it is allowed and will receive a warning message
Viewing selinux status:
getenforce
Forced and warning level conversion after selinux is turned on
Setenforce0 ## warning
Setenforce1 ## mandatory
selinux log location: / var/log/audit/audit.log
#########3, Security context for Selinux##########
1. View
ls -Z ## View the security context of a file
ls -Zd ## view the security context of the directory
ps axZ ## view the security context of the process
2. Modify security context
selinux reboot s only after the status changes to disabled
#touch /.autorelabel
#reboot --------- Creating this file can force initialization!!
Initialization scans the file The file is disposable
Experiment: modify the security context (temporary setting permanent setting)
1) Temporary setting
#vim /etc/selinux/config --- The experimental environment SELinux is forcing #getenforce ------ Viewing selinux status #cd /mnt/westosfile #mv /mnt/westosfile /var/ftp #cd /var/ftp #ls -Z --- View security context display pub ---public_content_t westosfile----mnt_t #chcon -t public_content_t /var/ftp/westofile --- Temporary setting #ls -Z Display modified successfully
2) Permanent setting
1. Forced initialization
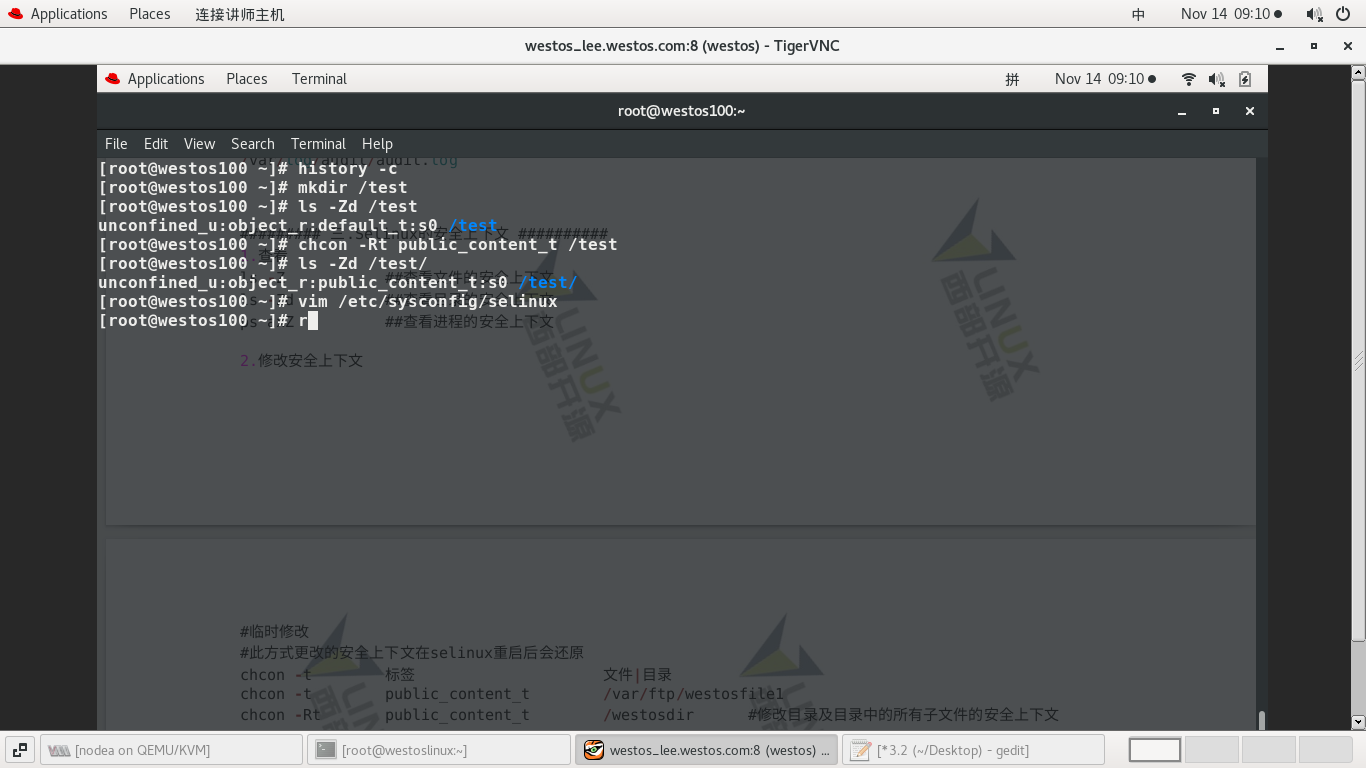
#mkdir /test/ ------ Establish a directory as experimental material #ls -Zd /test/ ----- View the security context of / test / Display as default #chcon -Rt public_content_t /test ---- Temporarily modify security context #ls -Zd /test/ Display changed to public_content_t #reboot ------ relinux status is enforcing Restart does not initialize scan #ls -Zd /test/ -- The security context is still default #touch /.autorelabel ---- Force initialization #reboot
ps: you must reboot after forced initialization
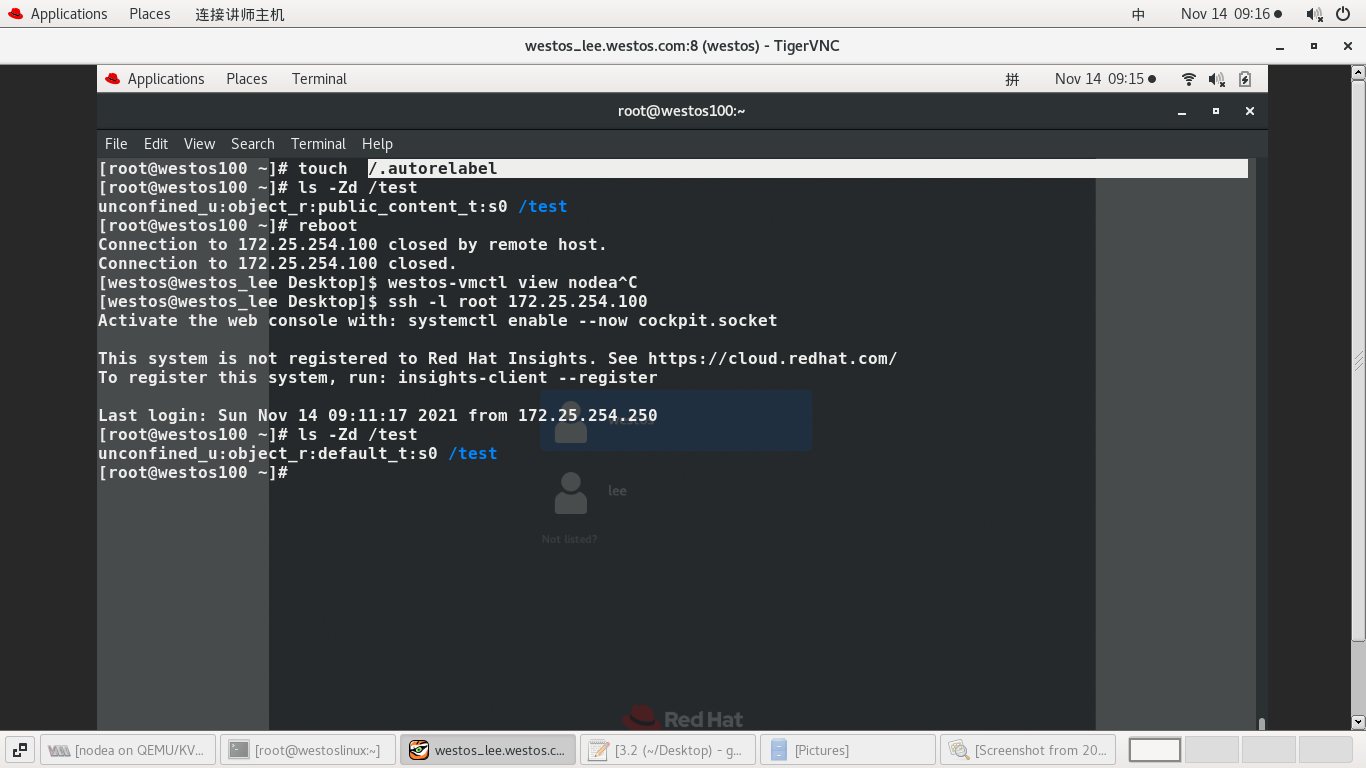
2. Permanent setting
#ls -Zd /test/ ----- The security context is still default Because it is a temporary red setting #semanage fcontext -a -t public_content_t '/test(/.*)?' -- Permanent setting (/.*)----Indicates the directory and its contents #semanage fcontext -l | grep test ---- View context status Display changed to public_content_t #ls -Zd /test/ Display as default Not refreshed #restorecon -RvvF /test/ --- Refresh R-second return vv -- show more detailed information F-refresh #ls -Zd /test/
Display changed to public_content_t And it is set permanently, and the initialization restart still takes effect
#########4, SEBOOL#######################
getsebool -a ## bool value of real service
setsebool -P ftpd_anon_write on # Change P -- permanent
#########4, SEBOOL#######################
getsebool -a ## bool value of real service
setsebool -P ftpd_anon_write on # Change P -- permanent
Experiment: sebool switch -- anonymous users upload files
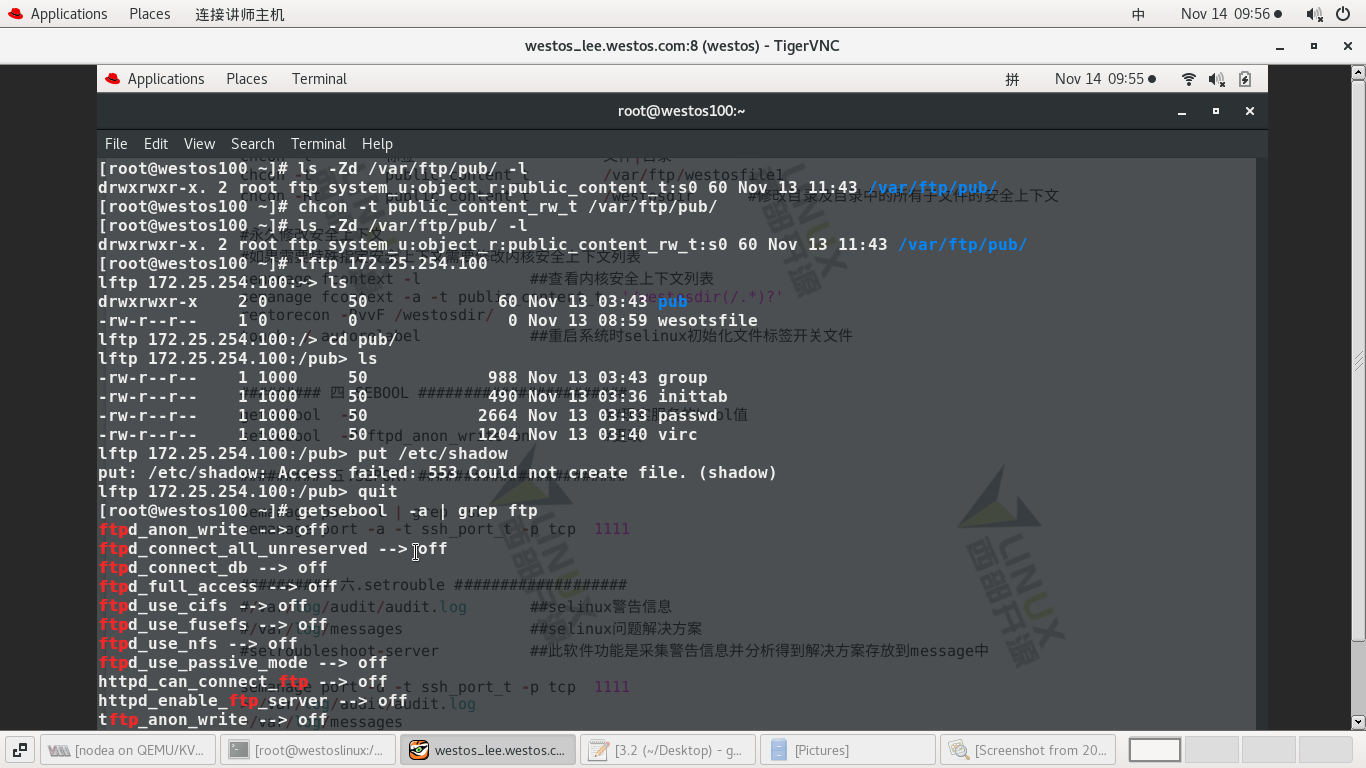
1) Failed to upload file because sebool is closed
#vim /etc/vsftpd/vsftpd.conf ------ Enable anonymous user upload function -------- anon_puload_enable=YES ---------- #systemctl restart vsftpd ------ restart #ls -Zd /var/ftp/pub/ -l - View context #chcon -t public_content_rw_t /var/ftp/pub/ --- Set RW permissions #ls -Zd /var/ftp/pub/ -l --- see #lftp 172.25.254.127 >ls >cd /pub/ >ls >put /etc/group ----Upload file Failed because sebol off >quit
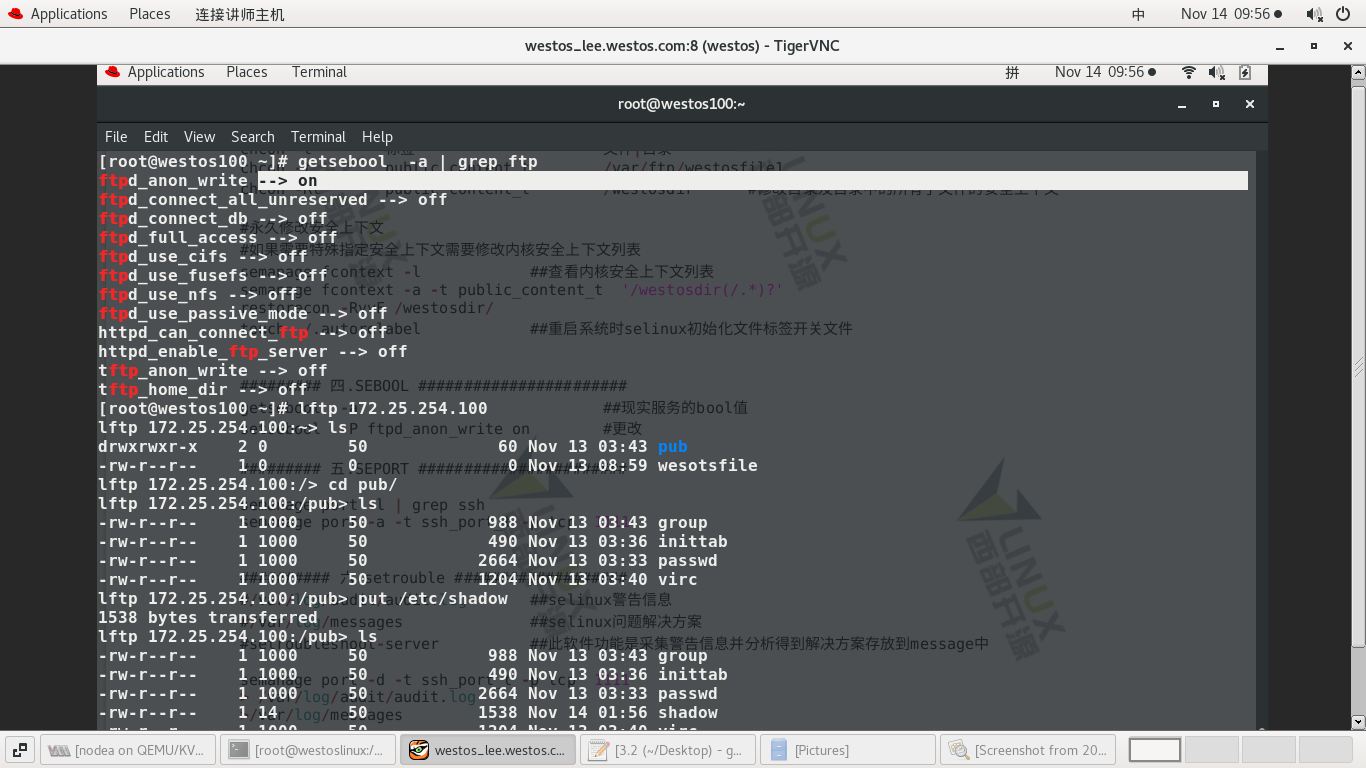
2) Enable sebool permission
#getsebool -a | grep ftp --- View sebool display ftpd_anon_write-->off #setsebool -P ftpd_anon_write on --- Enable sebool permission #getsebool -a | grep ftp --- View sebool display ftpd_anon_write-->on #lftp 172.25.254.127 >ls >cd /pub/ >ls >put /etc/group ----Upload succeeded ------------ending---------------------
#########5, SEPORT#######################
semanage port -l | grep ssh
semanage port -a -t ssh_port_t -p tcp
Experiment: port seport setting
1) Failed to modify port restart
#vim /etc/ssh/sshd_config ------- Port 2222 --------- #systemctl restart sshd ----- Restart failed
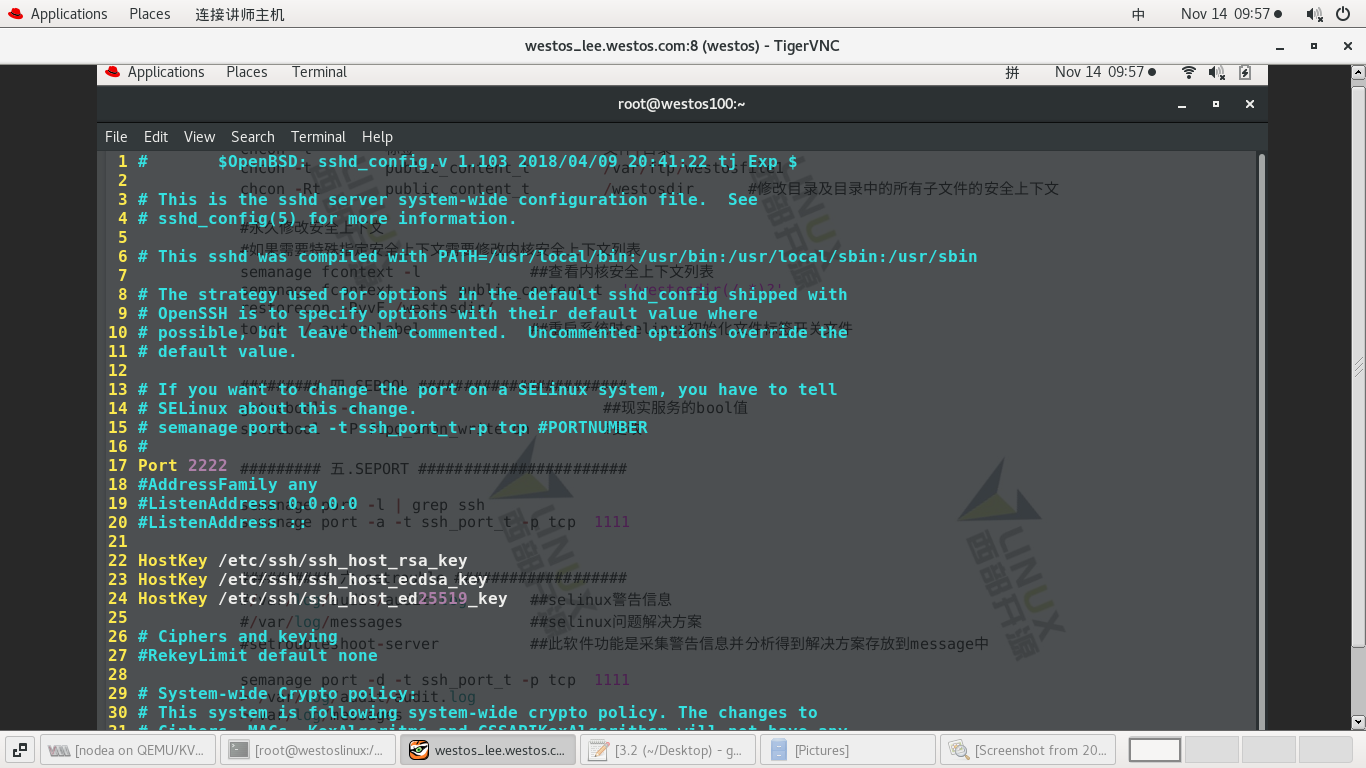
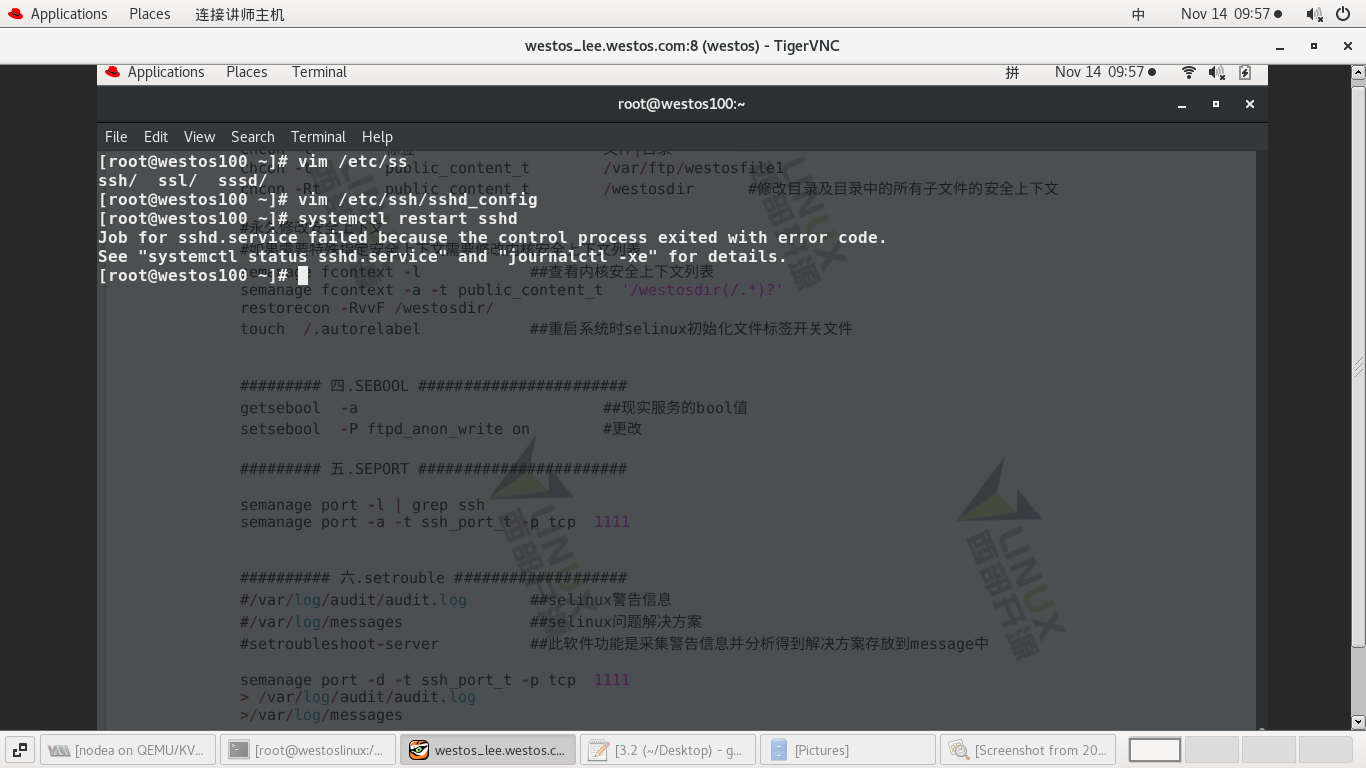
2) Add 2222 port and restart successfully
#semanage port -l | grep ssh - view ssh port status It shows that only 22 ports can be connected #semanage port -a -t ssh_port_t -p tcp 2222 ---- Add 2222 port #semanage port -l | grep ssh Both ends of display 22 and 2222 can be connected #systemctl restart sshd ----- Restart successful
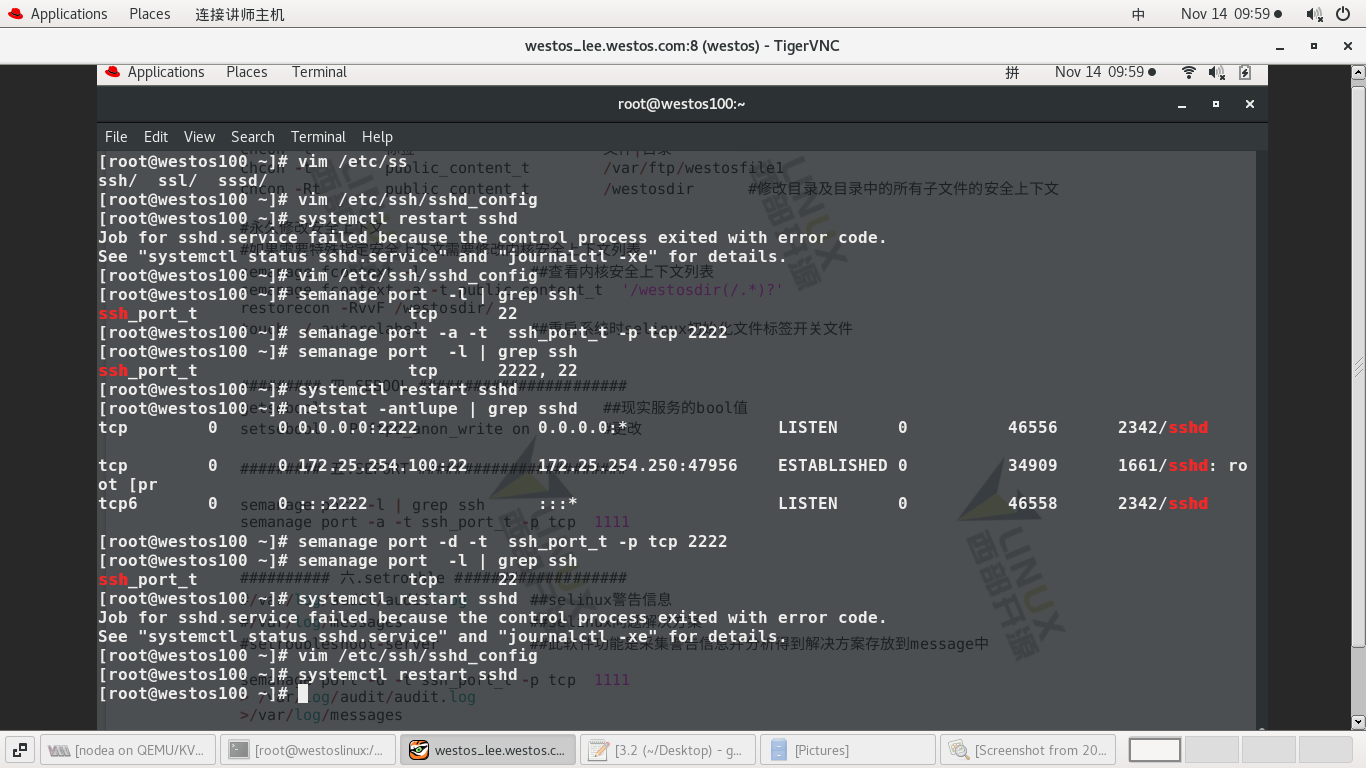
3) Deleting port 2222 and restarting failed again
#netstat -antlupe | grep sshd ---- View port status #semanage port -d -t ssh_port_t -p tcp 2222 ---- Remove port 2222 #semanage port -l | grep ssh Display only 22 ports #systemctl restart sshd --- Restart failed again
4) Note 2222 port restart succeeded
#vim /etc/ssh/sshd_config ---- ------ #Port 2222 --- notes ------- #systemctl restart sshd ----- Restart successful
##########6, setrouble###################
#/var/log/audit/audit.log # selinux warning message
#/var/log/messages # selinux problem solution
#setroubleshoot-server ## The function of this software is to collect warning information and analyze it
The obtained solution is stored in message
Experiment: set roubleshoot sever function analysis
1) Search for setrouble server installation package
#dnf search setrouble -- Search #dnf remove setroubleshoot-server.x86_ sixty-four --- The last command has replication
2) Delete setrouble server See what the impact will be
Impact: there are warnings and no solutions
#> /var/log/messages -- empty #> /var/log/audit/audit.log --- empty #touch /mnt/testfile1 #mv /mnt/testfile1 /var/ftp #ls /var/ftp #lftp 172.25.254.127 >ls Cannot view testfile1 something the matter >quit #cat /var/log/audit/audit.log --- Warning message yes #cat var/log/messages -- the solution is empty -------------0-----------0-------------------
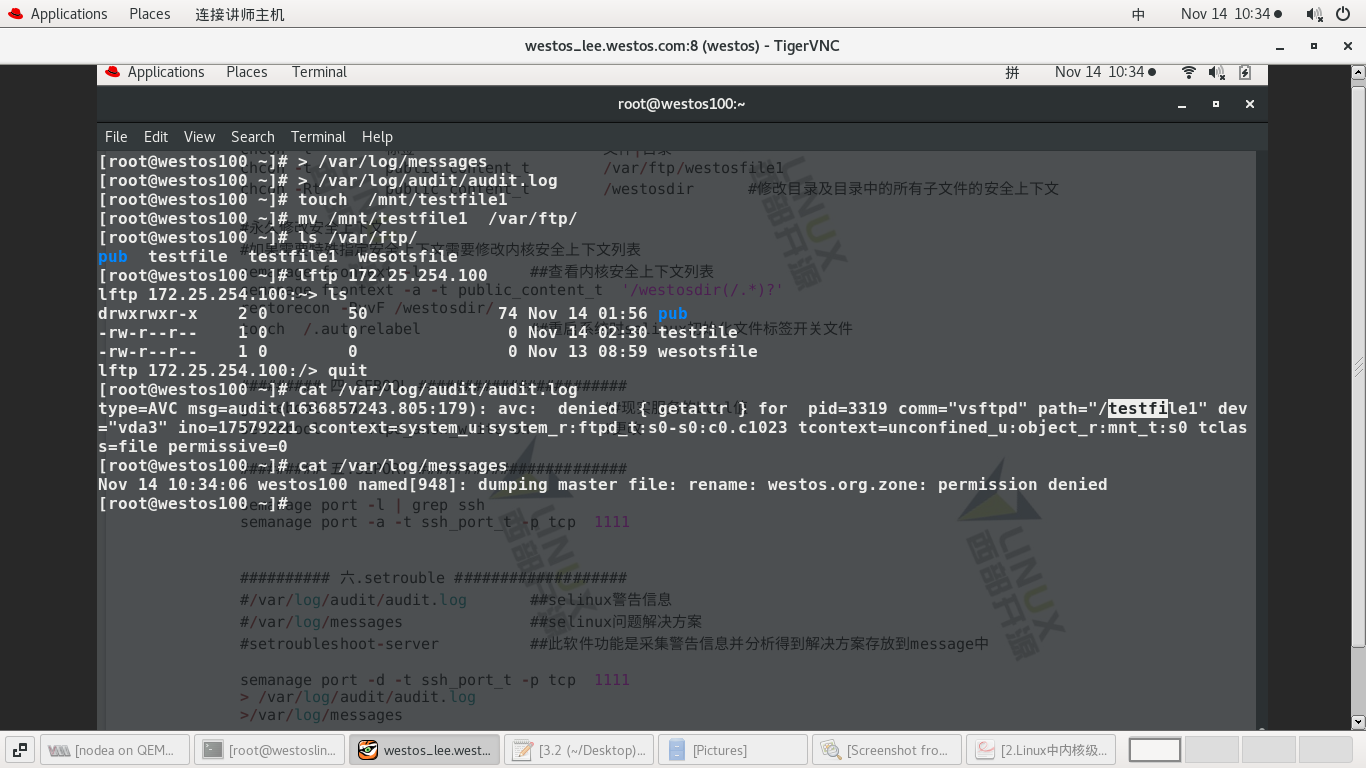
3) Download the software again
#dnf install setroubleshoot-server.x86_64 #> /var/log/messages #> /var/log/audit/audit.log #ls /var.ftp
Found a solution
#lftp 172.25.254.127 >ls Show no testfile1 >quit #cat /var/log/audit/audit.log -- Warning message yes #cat var/log/messages ---- The solution is
4) Problem solving
It's in the plan restorecon -v '/testfile1' #sealert -l 80fce42d-fdca-4d3f-9235-9fe66b580e5b ---- There are also solutions #restorecon -v '/var/ftp/testfile1' #lftp 172.25.254.127 >ls display testfile1 -------------success-----------------