Reference reading
Experiment details: manually specify the LSP of MPLS (Huawei equipment)
Detailed explanation of data level routing black hole generated by MPLS+BGP
Double label meaning

For MPLS+BGP networking, it is necessary to connect the routes between various CE S, so that two layers of label s will appear inside the public network;
- label for public network routing assigned by mpls ldp inside the public network
- label for private network routing assigned by VPN 4 of MP-BGP
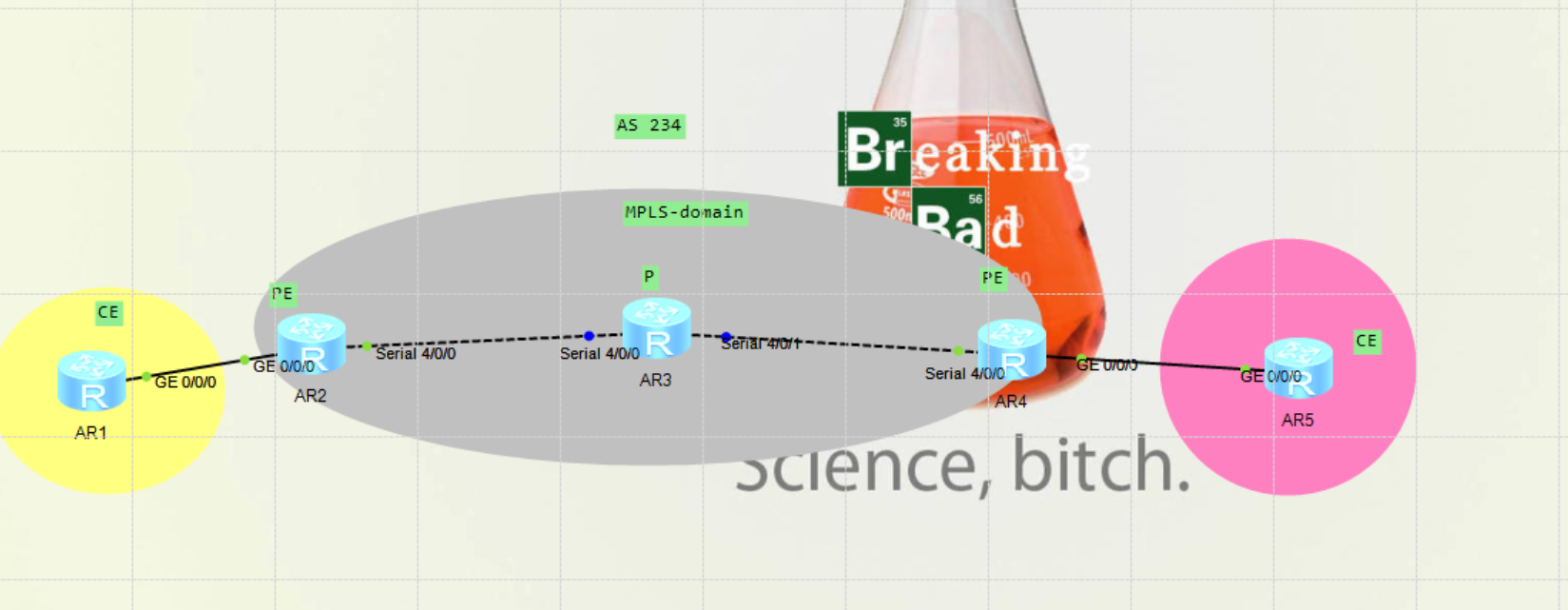
Experimental topology
explain:
1. A neighbor of bgp-vpn 4 is established between R2 and R4, and R3 does not run the BGP process
2. R2, R3 and R4 form an MPLS domain
3. R1 and R5 are independent clients respectively, and their routing network segments are 172.16.1.0/24 and 172.16.5.0/24
4. CE and PE are connected by static introduction
Configuration ideas
Routing configuration [R1]ip route-static 0.0.0.0 0.0.0.0 172.16.12.2 [R2]ip route-static vpn-instance a 172.16.1.0 255.255.255.0 [R4]ip route-static vpn-instance b 172.16.5.0 255.255.255.0 [R5]ip route-static 0.0.0.0 0.0.0.0 172.16.45.4 MPLS Configuration is global and interface enabling mpls,mpls ldp The experiment that can be read for reference is explained by the configuration vpn-instance to configure [R2-vpn-instance-a]di th [V200R003C00] # ip vpn-instance a ipv4-family route-distinguisher 12:12 vpn-target 15:15 export-extcommunity vpn-target 15:15 import-extcommunity # return [R4-vpn-instance-b]di th [V200R003C00] # ip vpn-instance b ipv4-family route-distinguisher 45:45 vpn-target 15:15 export-extcommunity vpn-target 15:15 import-extcommunity # return BGP to configure [R2-bgp]di th [V200R003C00] # bgp 234 undo default ipv4-unicast peer 10.1.4.4 as-number 234 peer 10.1.4.4 connect-interface LoopBack0 # ipv4-family unicast undo synchronization undo peer 10.1.4.4 enable # ipv4-family vpnv4 policy vpn-target peer 10.1.4.4 enable # ipv4-family vpn-instance a import-route direct import-route static # return [R4-bgp]di th [V200R003C00] # bgp 234 peer 10.1.2.2 as-number 234 peer 10.1.2.2 connect-interface LoopBack0 # ipv4-family unicast undo synchronization undo peer 10.1.2.2 enable # ipv4-family vpnv4 policy vpn-target peer 10.1.2.2 enable # ipv4-family vpn-instance b import-route direct import-route static # return
inspect
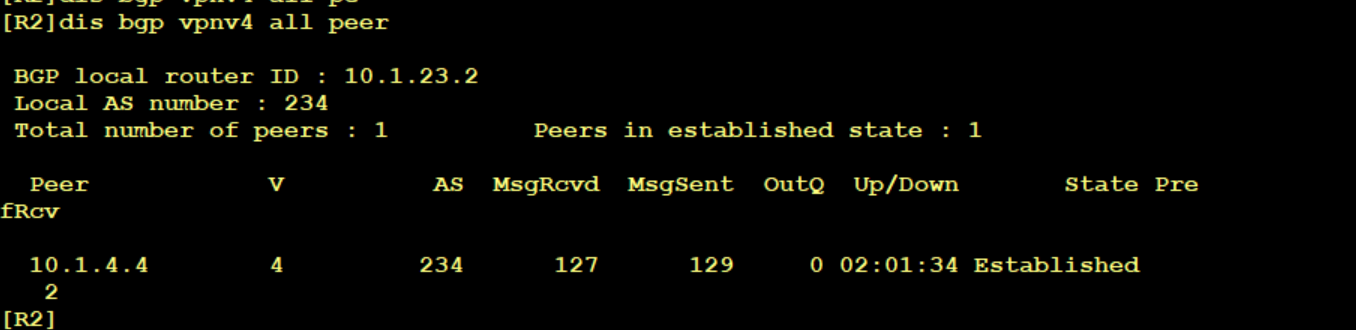
Bgp-vpn 4 neighbor
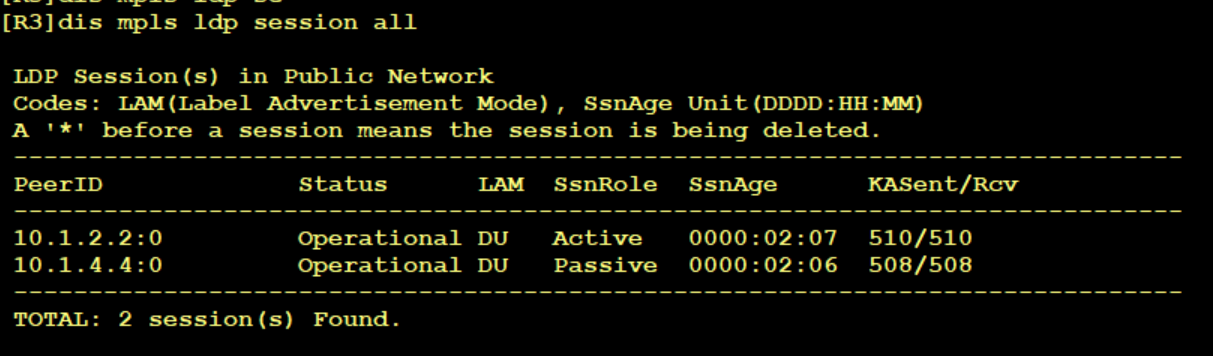
MPLS LDP neighbor
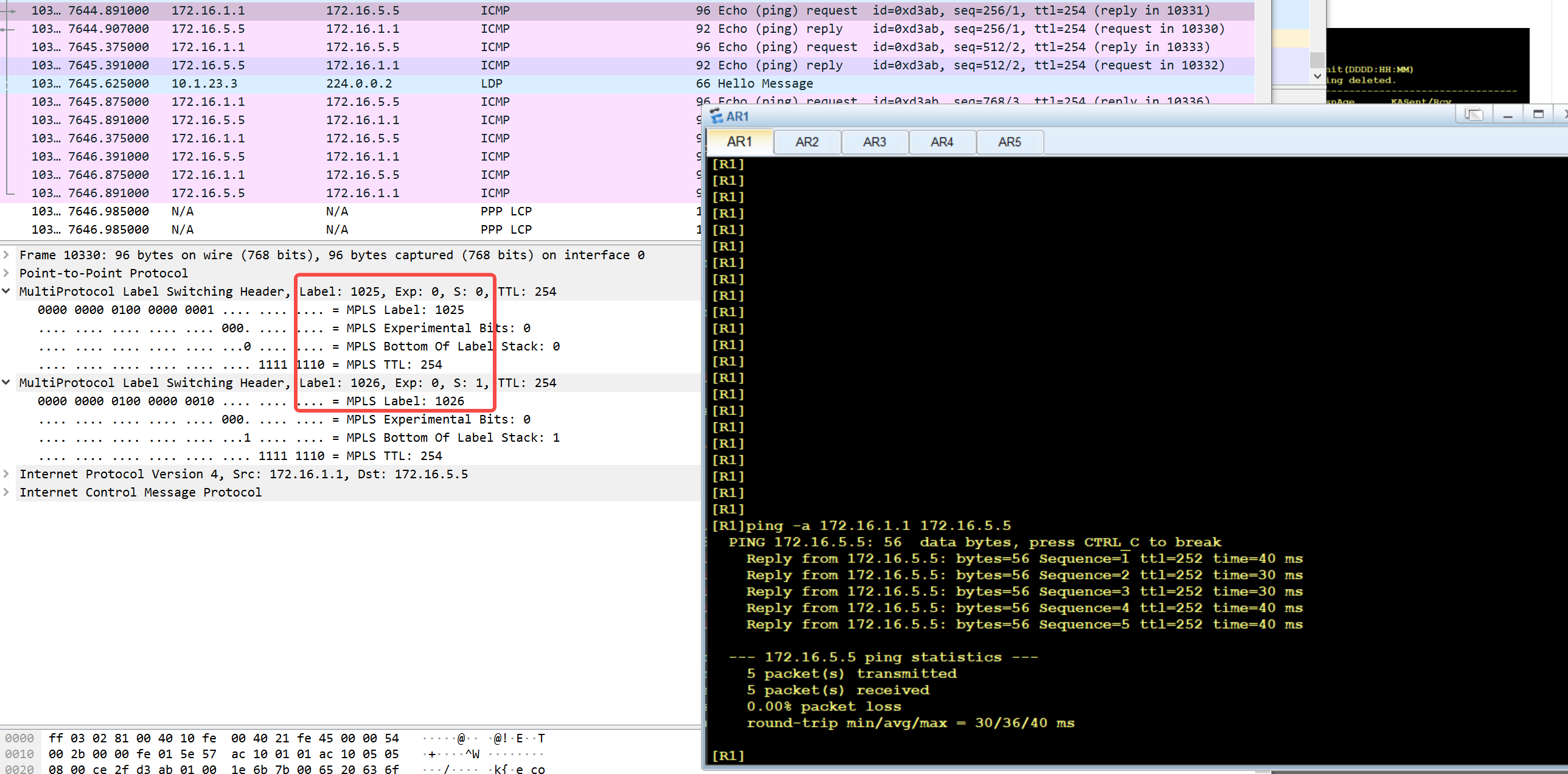
The private network route pingR5 of R1 captures packets at the incoming interface (S4/0/0) of R3. It can be seen that it is a double-layer label
Control + data level
Next, we will analyze the routing and label at the control and data levels respectively
Control plane
1. Private network routing, private network label
R4 introduces static in VPN instance B into bgp
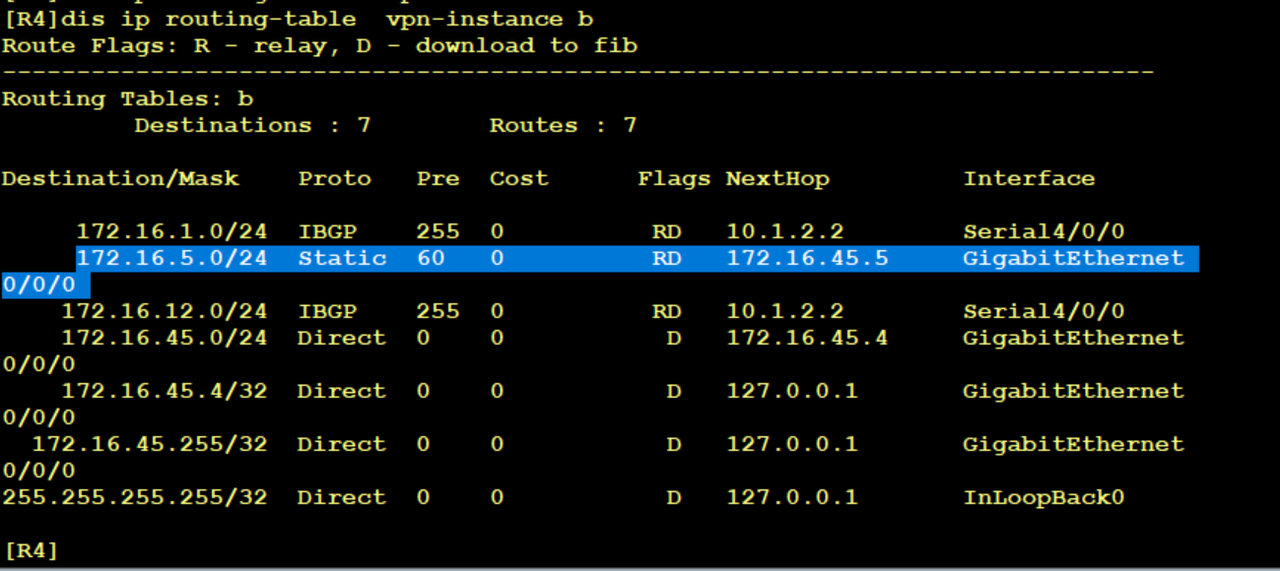
BGP forms RD+ipv4 into a 96bit VPN route, and carries the VPN target45:45 of export. Bgp-vpn 4 assigns a private label to this private route
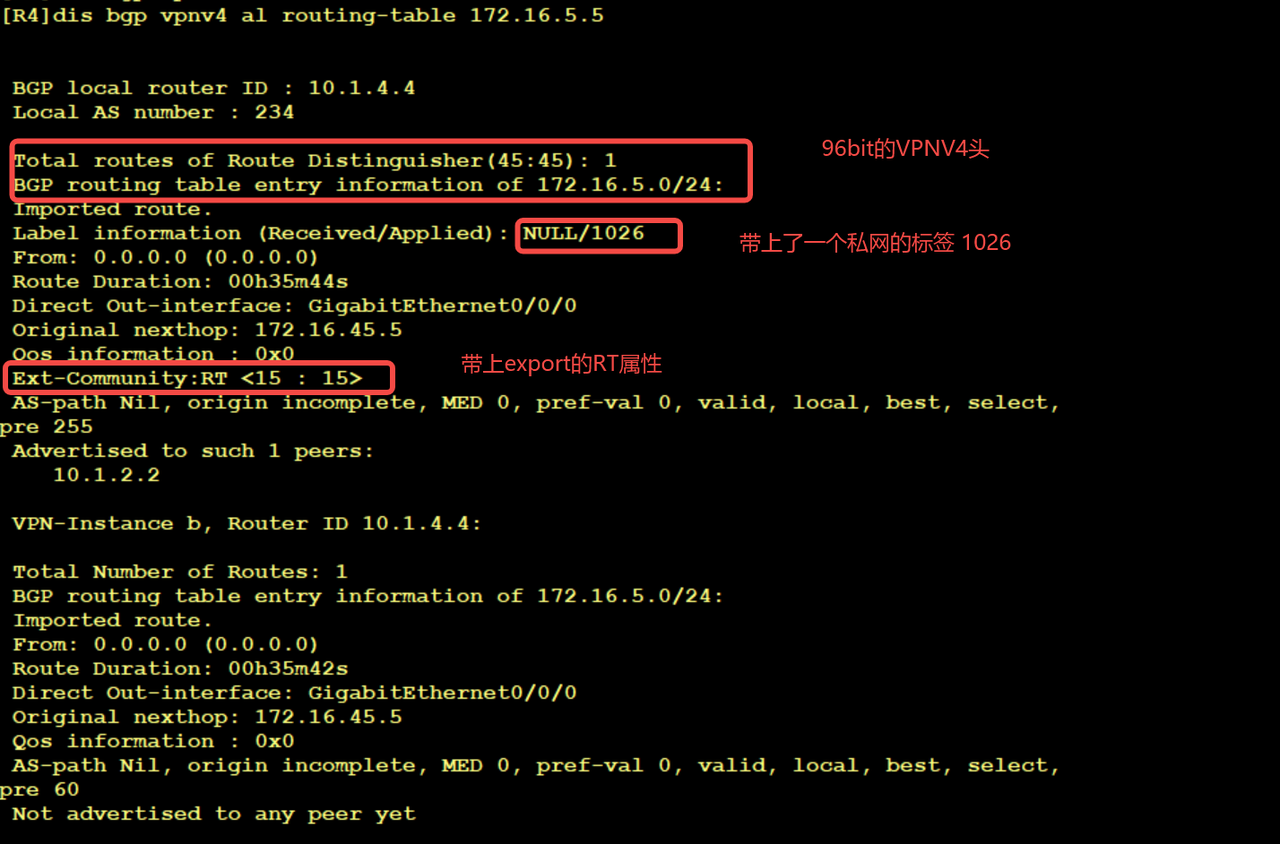
This private network route is passed to R2 through the neighbor relationship of VPN 4, and R2 receives this private network route with label 1026, which is sent through the neighbor of VPN 4 in 10.1.4.4
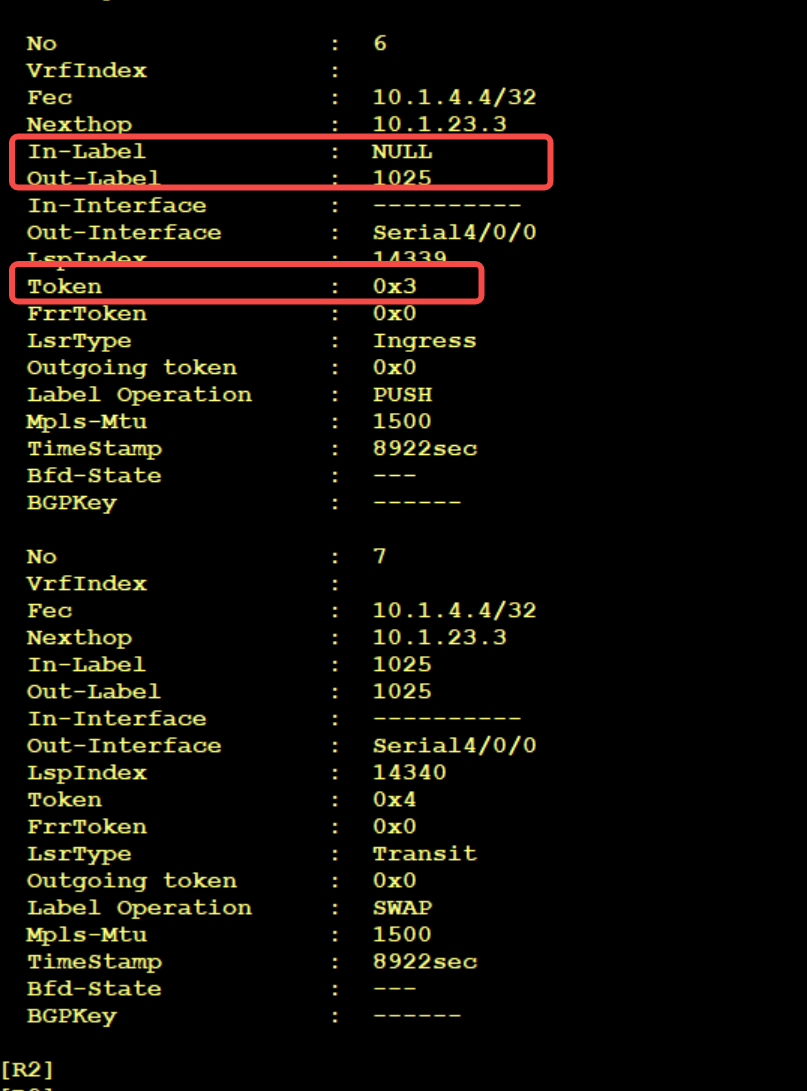
So far, R2 has received the private network route 172.16.5.0/24. The next hop is 10.1.4.4 and the label is 1026, which is generated by the BGP VPN 4 of R4
2. Public network routing
R4 label s its in with 3 as egress, that is, it tells R3 to perform PHP
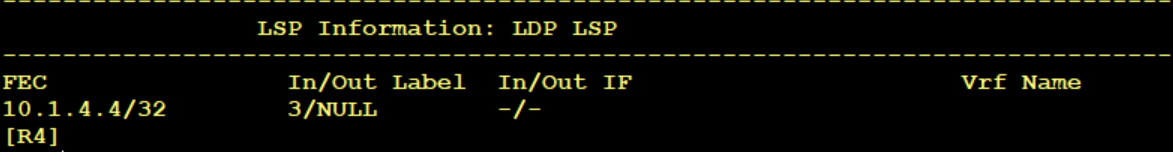
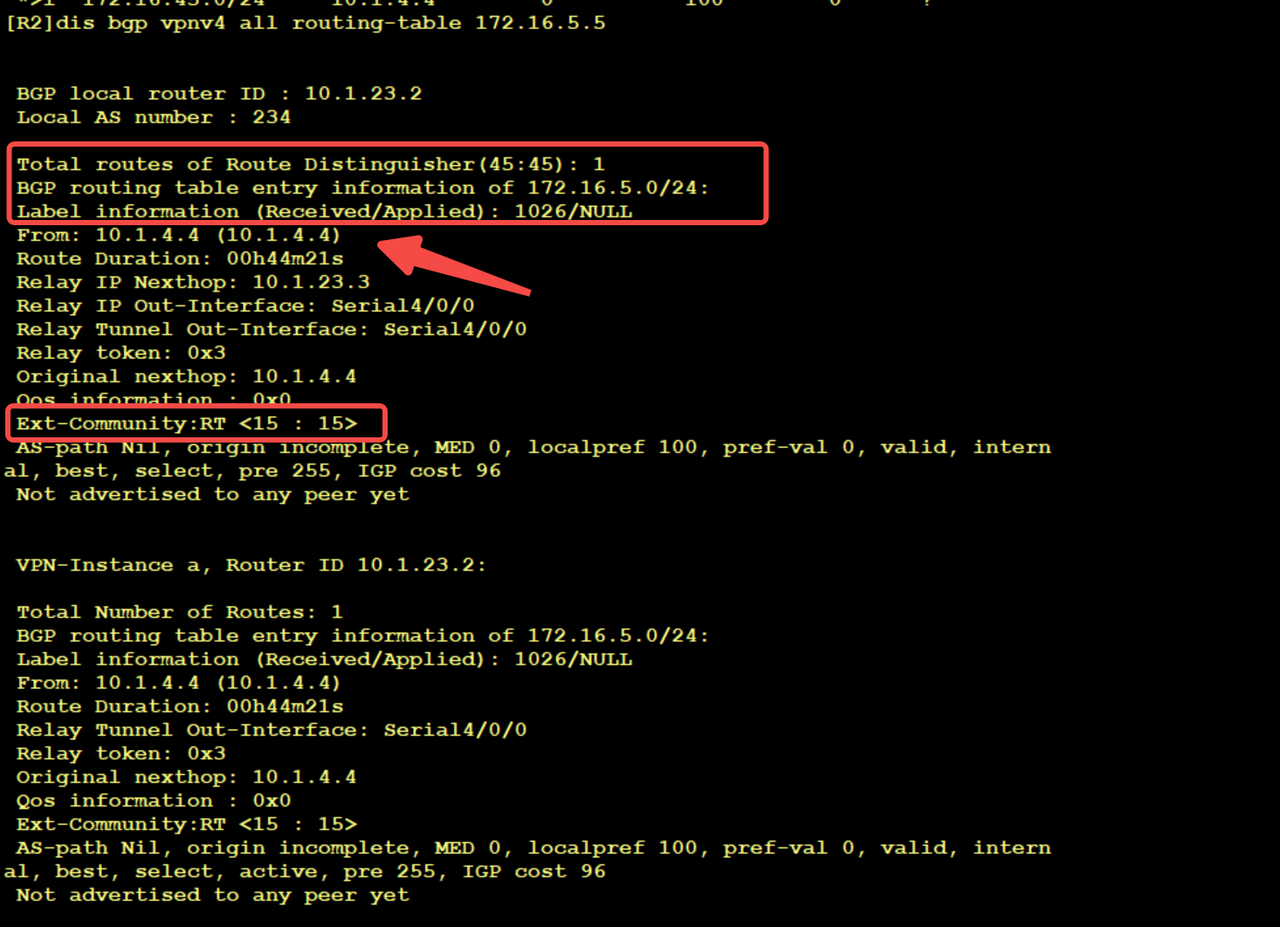
R3 is marked with 1025 and passed to R2
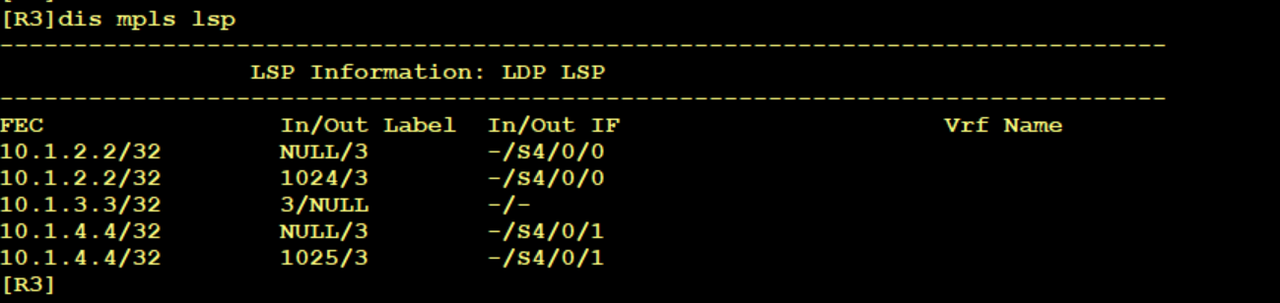
R2 received this 1025 label
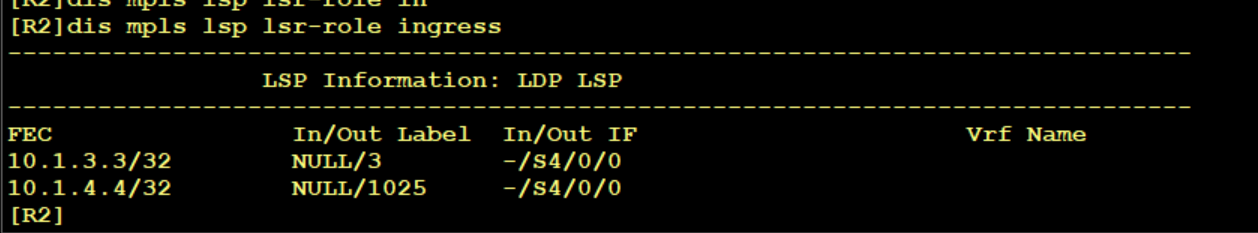
So far, R2 has received the public network route 10.1.4.4/32. The next hop is 10.1.23.3 and the label is 1025, which is allocated by the mpls ldp of R3
Data level
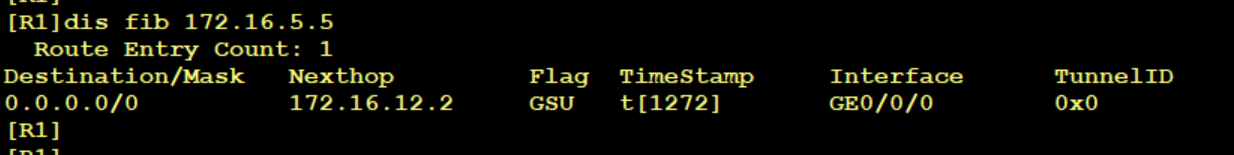
1. R1 queries the local FIB and finds the next hop to R2
2. R2 queries the FIB of VPN instance a, and it can be seen that the IP packet will push a 1026 label into a label packet. BGPNextHop here means that this label is transmitted through bgp-vpn 4 of the control plane, and the label transmitted from the private network
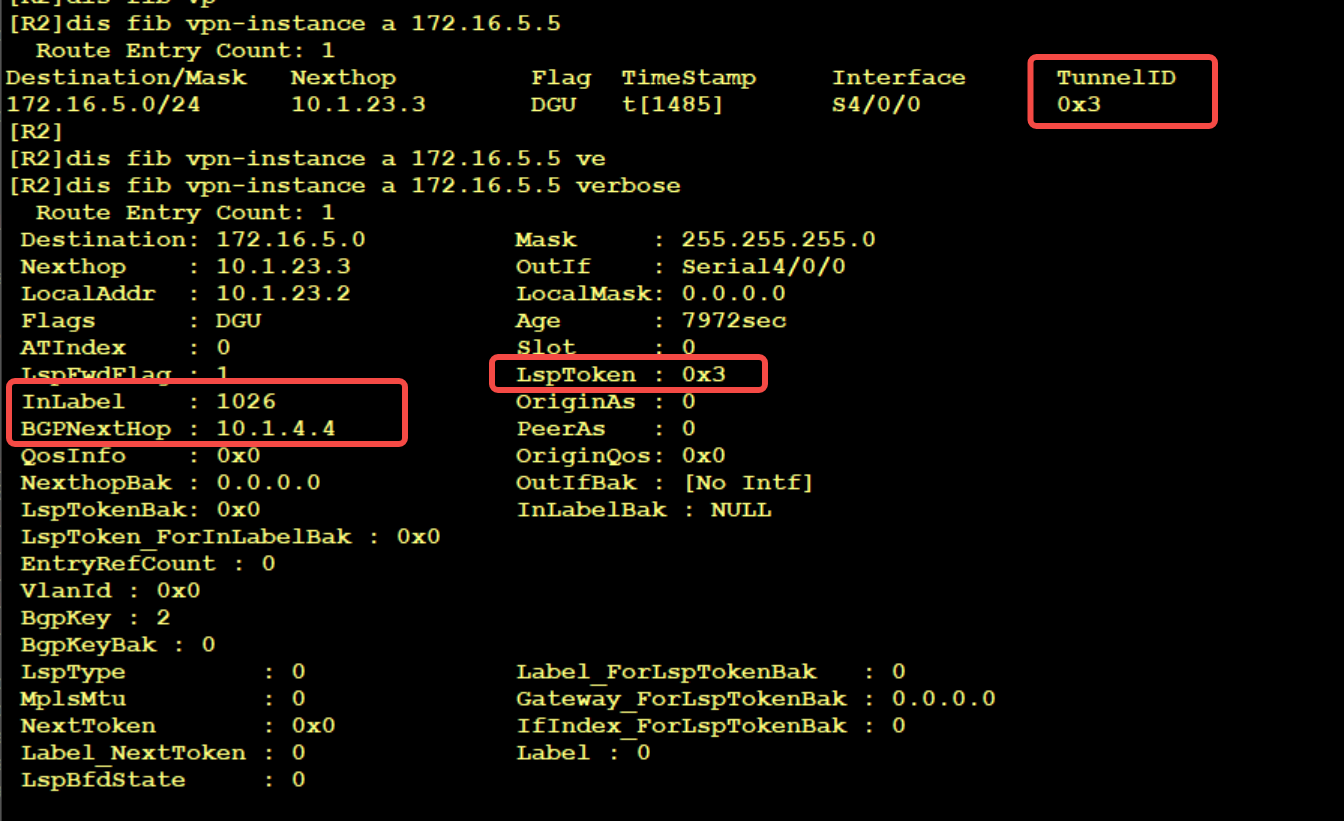
At this time, the data packet enters the MPLS domain (which can be understood as entering the scope of the public network) and needs to be transmitted through BGP. At this time, a public network label will be push ed again. Looking at the LFIB on R2, you can see that there are two operations for 10.1.4.4, namely progress and Transit; Which depends on the Token. The tunnel ID in the previous step corresponds to the Fec and Token here; Continuing to query tunnel ID 0x3, we can see that 1025 label is to be encapsulated for public network 10.1.4.4. So far, there are two layers of labels for this packet, and the next hop is 10.1.23.3, namely R3
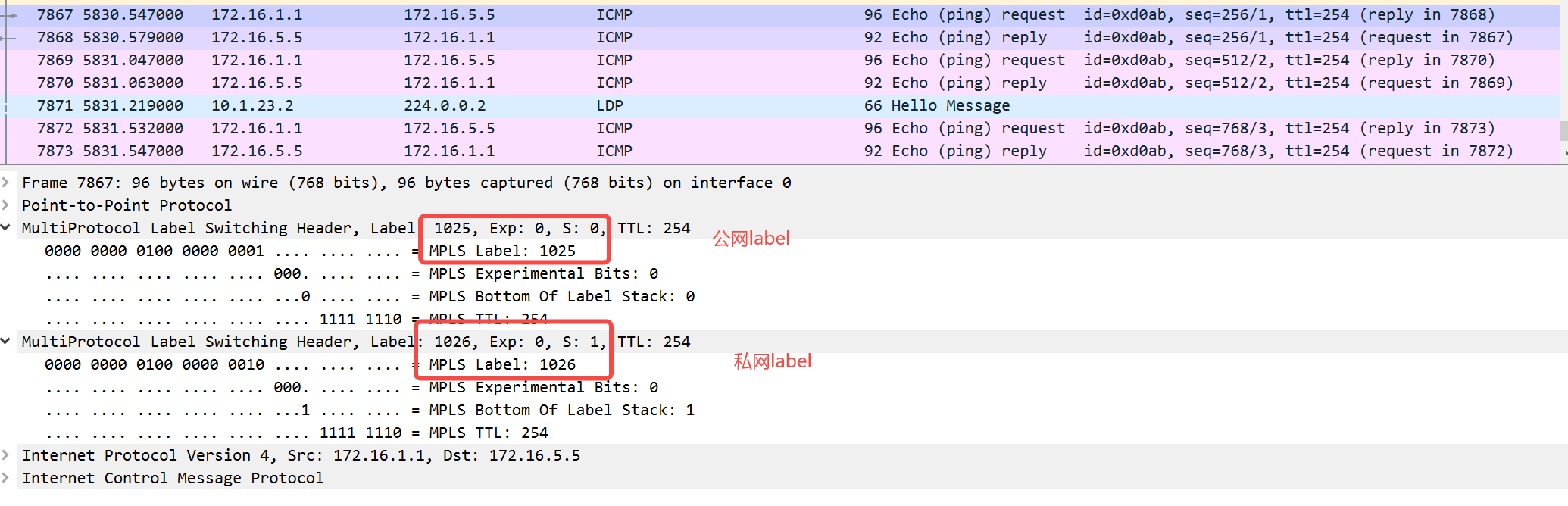
At this point, the packet becomes
Sip 172.16.1.1 dip 172.16.5.5 | Private network label 1026 |Public network label 1025 | ppp
The following is the packet capture of the incoming interface of R3 (serial 4/0/0)
At this time, after the data packet arrives at R3, R3 receives a label packet and must query LFIB. R3 makes a POP operation for the label of the public network. There is an interface and the next one in this LFIB, and throws the label packet to R4
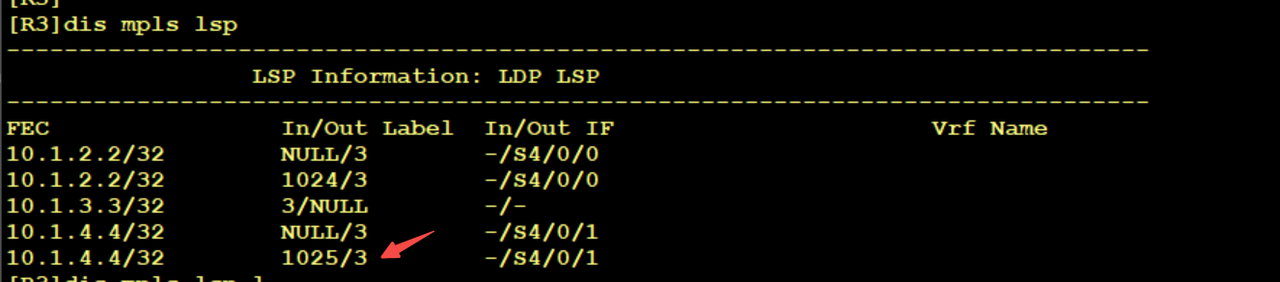
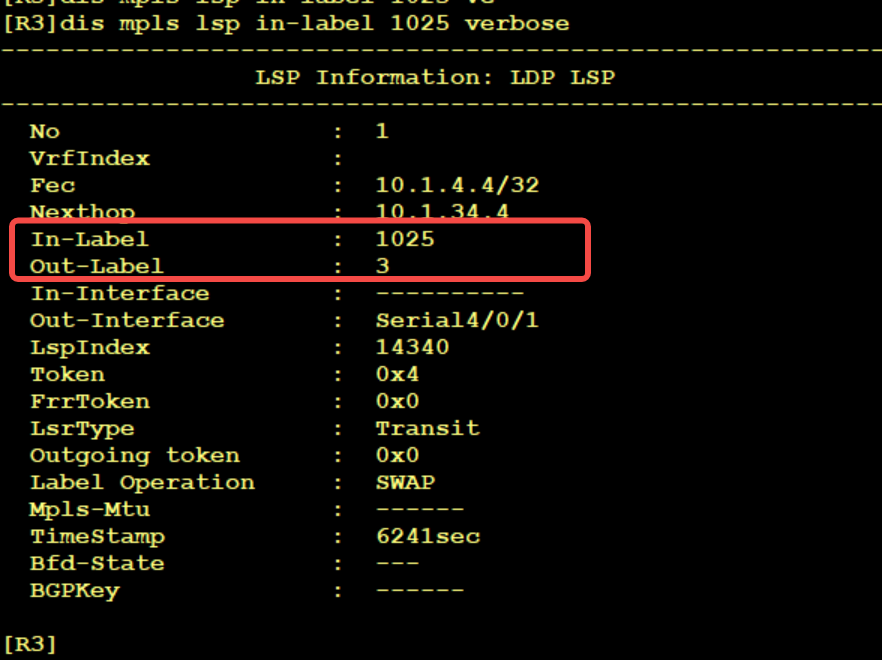
The following is the packet capture of R3's outgoing interface. You can see that the label of the public network is POP, leaving only the label of the private network
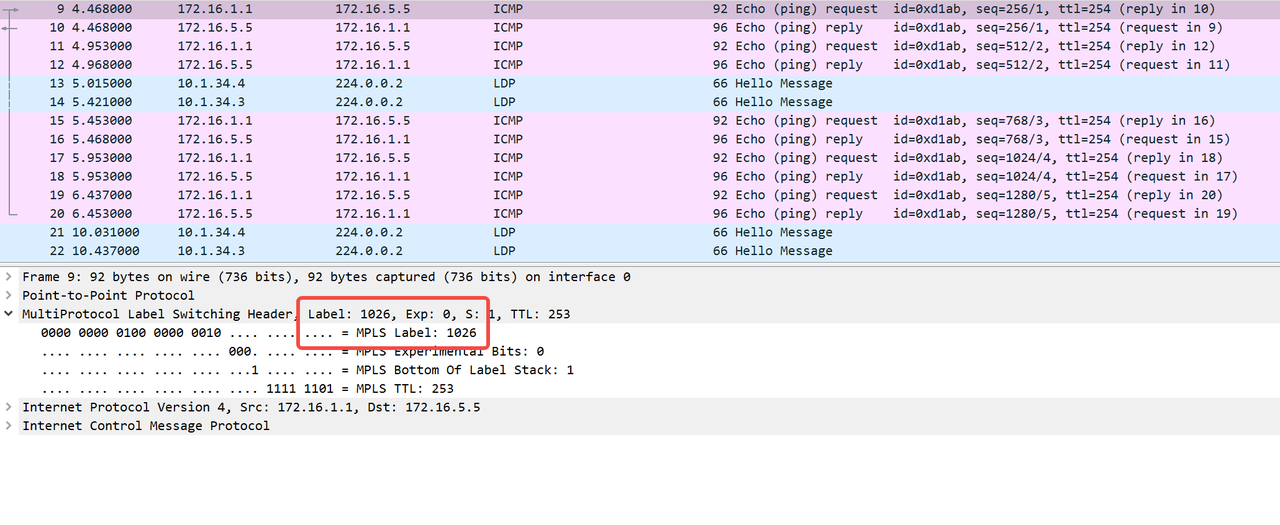
After the packet arrives at R4, query the LFIB whose in label is 1026 and do the POP operation, but there is no interface and next hop. Continue to query the FIB. Note that it is VPN instance B (based on VrfIndex)
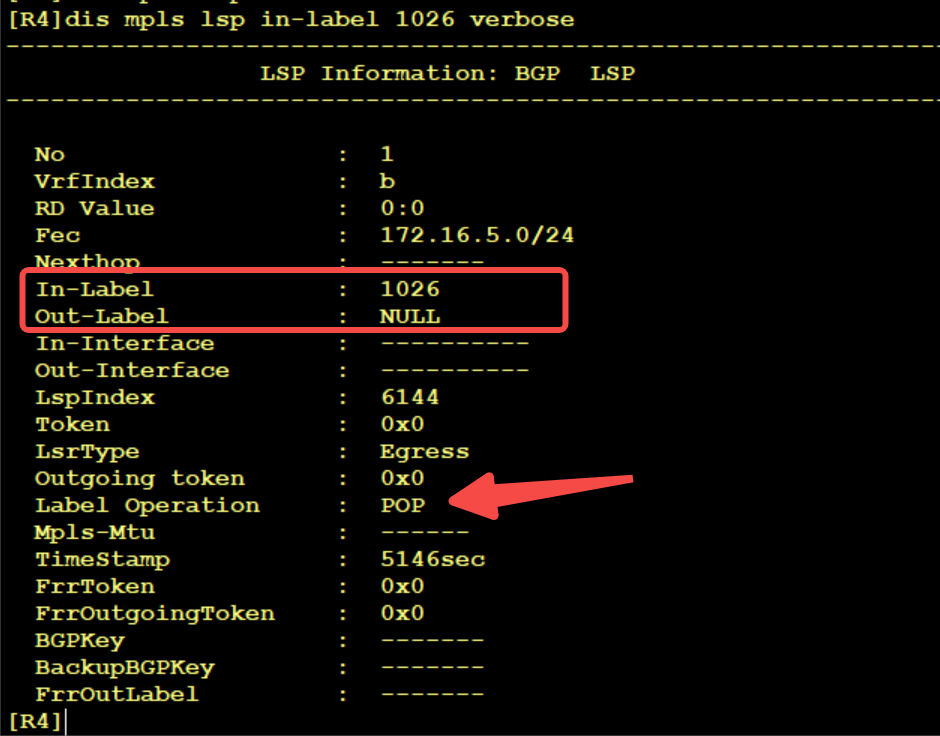
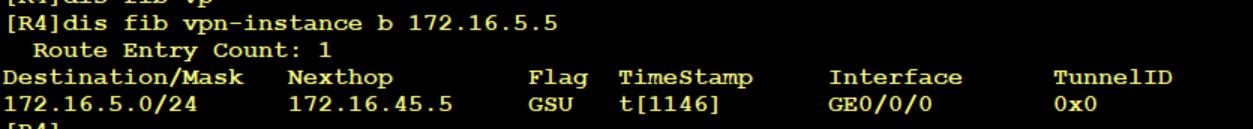
Then the packet is thrown to R5 and the route is connected
summary
- For data packets coming to the router, we should first analyze how to learn and generate the table item information at the control level from a macro perspective
- What table to query depends on whether the data is IP or label
- For double-layer labels, it is necessary to specify how each layer is encapsulated and when to do POP operation when packets are forwarded
The CE linkage of BGP+MPLS+OSPF will be updated later