Discovery host refers to the host that detects activity in the network. Discovering hosts is the first and most important step in implementing penetration testing. Penetration testing can only be performed further if the target host is determined to be active. Hosts can be discovered in Nmap s in different ways, such as IP discovery, ICMP discovery, TCP discovery, UDP discovery, etc.
I. IP Discovery
Internet Protocol is a network layer protocol in the tcp/ip system. Upload various protocol information such as TCP/UDP for transport layer; On the down side, IP packets can be placed in the link layer and transmitted through various technologies such as Ethernet and token network.
To identify the transport layer protocol type, an IP message contains a field Protocol that holds the transport layer protocol number.
Nmap allows users to build probing datagrams over IP for building different types of transport layer packets. Field Protocol allows users to set which transport layer protocol is used for the current package. Once the target responds to such packets, the host is proven to exist.
Grammar:
-PO <protocol list>: Use IP Packet Detection Target Host is on. among protocol list Is a list of agreement numbers. User can specify multiple IP Number, such as: 6-tcp,17-udp,1-ICMP,2-IGMP Use commas to separate multiple numbers. If no protocol is specified, the default protocol is 1 ( ICMP)2(IGMP)And 4 ( IP),Equivalent to -PO 1,2,4
Note: In option-PO, O is the capital letter O, not the number 0. In addition, there is no space between the option and the protocol number. If the specified protocol is ICMP, IGMP, TCP, UDP, the corresponding protocol header is added by default as the data load of the IP layer. In the case of other protocols, no data payload is added by default unless specified using either -, data-string, or -, data-length.
Use the default IP to detect an offline host to analyze the packets it sends and receives.
┌──(root💀kali)-[~] └─# nmap --packet-trace -PO 10.10.1.1 Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-09 23:35 CST # ICMP message sent SENT (0.0738s) ICMP [192.168.220.138 > 10.10.1.1 Echo request (type=8/code=0) id=33 seq=0] IP [ttl=45 id=64436 iplen=28 ] # IGMP message sent SENT (0.0741s) igmp (2) 192.168.220.138 > 10.10.1.1: ttl=37 id=30379 iplen=28 # IPV4 message sent SENT (0.0742s) ipv4 (4) 192.168.220.138 > 10.10.1.1: ttl=40 id=51474 iplen=20 # ICMP message received RCVD (0.0743s) ICMP [192.168.220.2 > 192.168.220.138 Protocol 2 unreachable (type=3/code=2) ] IP [ttl=128 id=26347 iplen=56 ] # ICMP message received RCVD (0.0744s) ICMP [192.168.220.2 > 192.168.220.138 Protocol 4 unreachable (type=3/code=2) ] IP [ttl=128 id=26348 iplen=48 ] SENT (2.0790s) ipv4 (4) 192.168.220.138 > 10.10.1.1: ttl=57 id=18487 iplen=20 SENT (2.0792s) igmp (2) 192.168.220.138 > 10.10.1.1: ttl=57 id=31605 iplen=28 SENT (2.0794s) ICMP [192.168.220.138 > 10.10.1.1 Echo request (type=8/code=0) id=20005 seq=0] IP [ttl=47 id=12773 iplen=28 ] RCVD (2.0792s) ICMP [192.168.220.2 > 192.168.220.138 Protocol 4 unreachable (type=3/code=2) ] IP [ttl=128 id=26349 iplen=48 ] RCVD (2.0792s) ICMP [192.168.220.2 > 192.168.220.138 Protocol 2 unreachable (type=3/code=2) ] IP [ttl=128 id=26350 iplen=56 ] # Host not online Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn Nmap done: 1 IP address (0 hosts up) scanned in 3.09 seconds
The detection results can be seen in the output information
-
Nmap first sends three default IP probing messages to the target host in turn, ICMP/IGMP/IPV4
# ICMP message sent SENT (0.0738s) ICMP [192.168.220.138 > 10.10.1.1 Echo request (type=8/code=0) id=33 seq=0] IP [ttl=45 id=64436 iplen=28 ] # IGMP message sent SENT (0.0741s) igmp (2) 192.168.220.138 > 10.10.1.1: ttl=37 id=30379 iplen=28 # IPV4 message sent SENT (0.0742s) ipv4 (4) 192.168.220.138 > 10.10.1.1: ttl=40 id=51474 iplen=20
-
Received two ICMP unreachable error packets
# ICMP message received RCVD (0.0743s) ICMP [192.168.220.2 > 192.168.220.138 Protocol 2 unreachable (type=3/code=2) ] IP [ttl=128 id=26347 iplen=56 ] # ICMP message received RCVD (0.0744s) ICMP [192.168.220.2 > 192.168.220.138 Protocol 4 unreachable (type=3/code=2) ] IP [ttl=128 id=26348 iplen=48 ]
Protocol 2 and Protocol 4 correspond to transport layer protocol field values 2 and 4 respectively, which correspond to IGMP and IP. The two protocol types are 3 and the message code is 2, indicating that the protocol is not reachable, that is, the destination host is not successfully reached.
-
Because the first ICMP packet is not responding, Nmap resends:
SENT (2.0794s) ICMP [192.168.220.138 > 10.10.1.1 Echo request (type=8/code=0) id=20005 seq=0] IP [ttl=47 id=12773 iplen=28 ]
-
Since no response has yet been received, it is determined that the target host is not online and outputs the following information:
Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn
Detect an active host using default IP to view sent and received packets
┌──(root💀kali)-[~]
└─# nmap --packet-trace -PO -sn --disable-arp-ping 192.168.137.1
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-10 00:01 CST
# Send ICMP message
SENT (0.0386s) ICMP [192.168.220.138 > 192.168.137.1 Echo request (type=8/code=0) id=12203 seq=0] IP [ttl=56 id=38437 iplen=28 ]
# Send IGMP message
SENT (0.0388s) igmp (2) 192.168.220.138 > 192.168.137.1: ttl=46 id=48232 iplen=28
# Send IPV4 message
SENT (0.0390s) ipv4 (4) 192.168.220.138 > 192.168.137.1: ttl=48 id=39415 iplen=20
# Receive ICMP response message
RCVD (0.0392s) ICMP [192.168.220.2 > 192.168.220.138 Protocol 2 unreachable (type=3/code=2) ] IP [ttl=128 id=26356 iplen=56 ]
RCVD (0.0393s) ICMP [192.168.137.1 > 192.168.220.138 Echo reply (type=0/code=0) id=12203 seq=0] IP [ttl=128 id=26357 iplen=28 ]
NSOCK INFO [0.0390s] nsock_iod_new2(): nsock_iod_new (IOD #1)
NSOCK INFO [0.0390s] nsock_connect_udp(): UDP connection requested to 192.168.220.2:53 (IOD #1) EID 8
NSOCK INFO [0.0400s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 18
NSOCK INFO [0.0400s] nsock_write(): Write request for 44 bytes to IOD #1 EID 27 [192.168.220.2:53]
NSOCK INFO [0.0400s] nsock_trace_handler_callback(): Callback: CONNECT SUCCESS for EID 8 [192.168.220.2:53]
NSOCK INFO [0.0400s] nsock_trace_handler_callback(): Callback: WRITE SUCCESS for EID 27 [192.168.220.2:53]
NSOCK INFO [0.0470s] nsock_trace_handler_callback(): Callback: READ SUCCESS for EID 18 [192.168.220.2:53] (44 bytes): Q............1.137.168.192.in-addr.arpa.....
NSOCK INFO [0.0470s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 34
NSOCK INFO [0.0470s] nsock_iod_delete(): nsock_iod_delete (IOD #1)
NSOCK INFO [0.0470s] nevent_delete(): nevent_delete on event #34 (type READ)
Nmap scan report for 192.168.137.1
# Host is active
Host is up (0.00075s latency).
Nmap done: 1 IP address (1 host up) scanned in 0.05 seconds
From the output information, you can see that Nmap successively sent ICMP, IGMP, and IPv4 probe messages to the target host, and successfully received an ICMP response message (Echo reply). Among them, the message is the correct Ping reply message for ICMP, and both the type and message code are 0. This indicates that the target host is active.
Set up IP discovery using TCP to detect the state of the target host
┌──(root💀kali)-[~]
└─# nmap --packet-trace -PO6 -sn --disable-arp-ping 192.168.137.1
Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-10 00:19 CST
# Send tcp ack message
SENT (0.0348s) TCP 192.168.220.138:58382 > 192.168.137.1:80 A ttl=55 id=33234 iplen=40 seq=3525990618 win=1024
# TCP RST Messages Received
RCVD (0.0351s) TCP 192.168.137.1:80 > 192.168.220.138:58382 R ttl=128 id=26360 iplen=40 seq=1636168757 win=32767
NSOCK INFO [0.0350s] nsock_iod_new2(): nsock_iod_new (IOD #1)
NSOCK INFO [0.0350s] nsock_connect_udp(): UDP connection requested to 192.168.220.2:53 (IOD #1) EID 8
NSOCK INFO [0.0350s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 18
NSOCK INFO [0.0350s] nsock_write(): Write request for 44 bytes to IOD #1 EID 27 [192.168.220.2:53]
NSOCK INFO [0.0350s] nsock_trace_handler_callback(): Callback: CONNECT SUCCESS for EID 8 [192.168.220.2:53]
NSOCK INFO [0.0350s] nsock_trace_handler_callback(): Callback: WRITE SUCCESS for EID 27 [192.168.220.2:53]
NSOCK INFO [0.0420s] nsock_trace_handler_callback(): Callback: READ SUCCESS for EID 18 [192.168.220.2:53] (44 bytes): b............1.137.168.192.in-addr.arpa.....
NSOCK INFO [0.0420s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 34
NSOCK INFO [0.0420s] nsock_iod_delete(): nsock_iod_delete (IOD #1)
NSOCK INFO [0.0420s] nevent_delete(): nevent_delete on event #34 (type READ)
Nmap scan report for 192.168.137.1
# Host is active
Host is up (0.00041s latency).
Nmap done: 1 IP address (1 host up) scanned in 0.04 seconds
The TCP protocol number is 6 in the executed command. As you can see from the output information, Nmap sends only a TCP ACK probe message to port 80 of the target host to determine the state of the target host. As you can see from the results displayed, port 80 of the target host responds correctly to a TCP RST message. This indicates that the target host is active.
2. ICMP Discovery
1. How ICMP works
-
Working principle
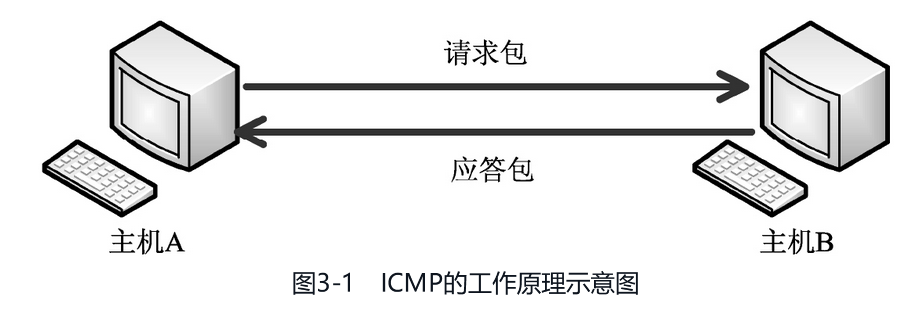
ICMP Workflow:- When Host A tests for proper communication through the ping command, a request packet is sent to Host B.
- Host B receives the request and checks its destination address against the local ip address. Receive if it meets, otherwise discard. After receiving, a response packet is sent to host A indicating that the host is reachable, that is, the target host is active.
-
type
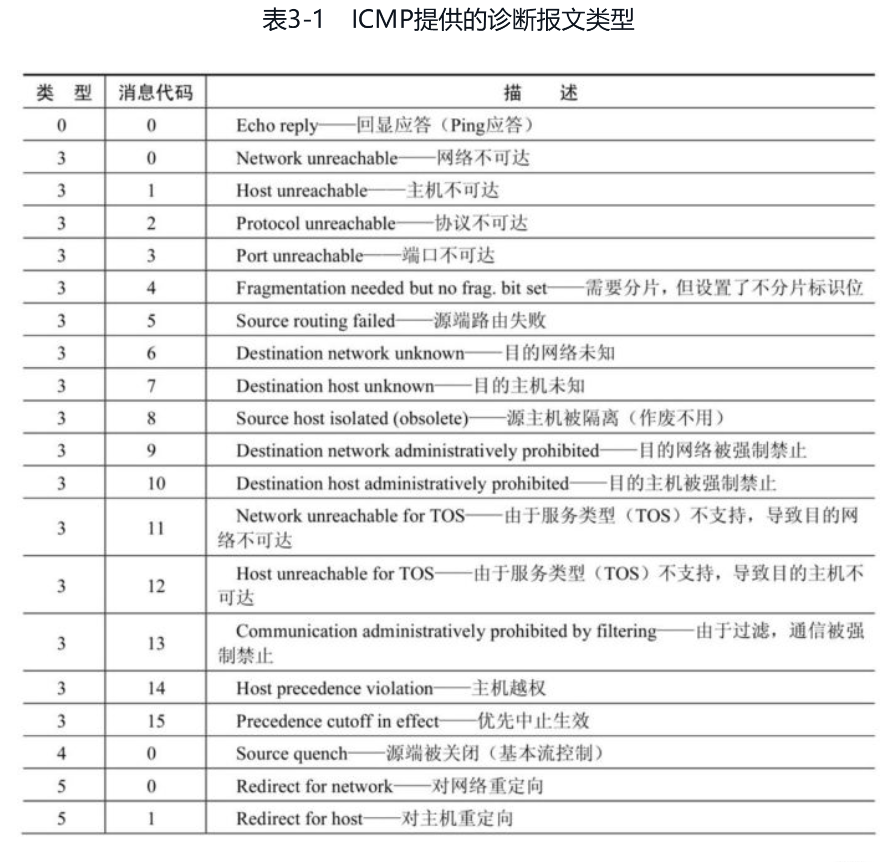
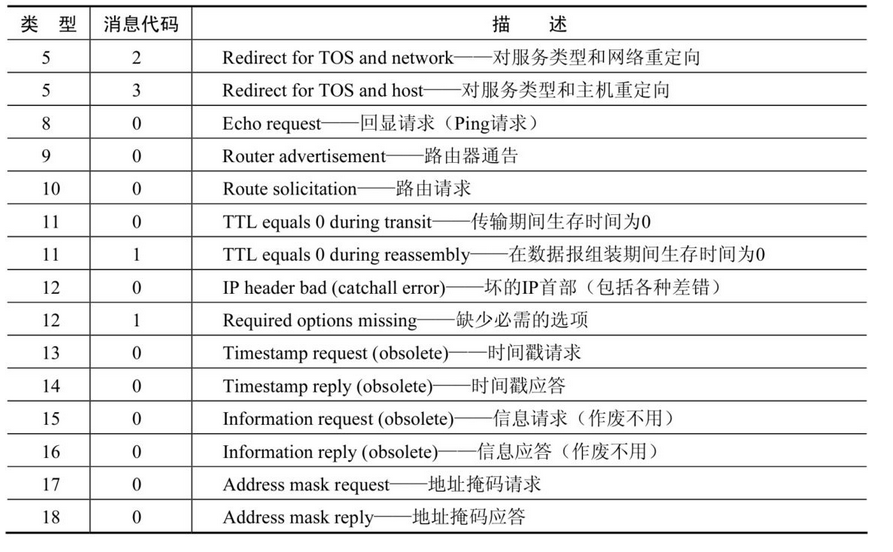
2. ICMP requests
ICMP request: Send a ping request to the target host and wait for the response from the target host. If the target host responds, the target host is online, otherwise it is not.
nmap provides two options to implement ICMP requests to detect whether the target host is active:
-sn:[Implementation Ping Scan, no port scan]
With this option, nmap sends four requests by default: ICMP ECHO requests, TCP SYN requests, TCP ACK requests, and ICMP timestamp requests. If you do not want to use ARP requests, you can use the --send-ip option to specify sending IP packets. - The sn option can be used in combination with any hair detection type - P* option for greater flexibility.
-PE:[Implementation ICMP Echo Probe Request Discovery]
If the target host responds to an ICMP Reply message, the target host is online or not.
Detect whether the target host is online by performing a Ping scan
┌──(root💀kali)-[~] └─# nmap --packet-trace -sn www.baidu.com Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-10 01:06 CST # Send ICMP Response Request SENT (0.0442s) ICMP [192.168.220.138 > 180.101.49.11 Echo request (type=8/code=0) id=22759 seq=0] IP [ttl=52 id=28777 iplen=28 ] # Send TCP SYN to 443 SENT (0.0444s) TCP 192.168.220.138:34194 > 180.101.49.11:443 S ttl=57 id=41984 iplen=44 seq=274922632 win=1024 <mss 1460> # Send TCP ack to 80 SENT (0.0445s) TCP 192.168.220.138:34194 > 180.101.49.11:80 A ttl=53 id=35602 iplen=40 seq=0 win=1024 # Send ICMP timestamp request SENT (0.0446s) ICMP [192.168.220.138 > 180.101.49.11 Timestamp request (type=13/code=0) id=32360 seq=0 orig=0 recv=0 trans=0] IP [ttl=58 id=18221 iplen=40 ] # Receive ICMP Answer RCVD (0.0450s) TCP 180.101.49.11:80 > 192.168.220.138:34194 R ttl=128 id=26366 iplen=40 seq=274922632 win=32767 NSOCK INFO [0.0450s] nsock_iod_new2(): nsock_iod_new (IOD #1) NSOCK INFO [0.0450s] nsock_connect_udp(): UDP connection requested to 192.168.220.2:53 (IOD #1) EID 8 NSOCK INFO [0.0450s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 18 NSOCK INFO [0.0450s] nsock_write(): Write request for 44 bytes to IOD #1 EID 27 [192.168.220.2:53] NSOCK INFO [0.0450s] nsock_trace_handler_callback(): Callback: CONNECT SUCCESS for EID 8 [192.168.220.2:53] NSOCK INFO [0.0450s] nsock_trace_handler_callback(): Callback: WRITE SUCCESS for EID 27 [192.168.220.2:53] NSOCK INFO [0.0800s] nsock_trace_handler_callback(): Callback: READ SUCCESS for EID 18 [192.168.220.2:53] (44 bytes): .............11.49.101.180.in-addr.arpa..... NSOCK INFO [0.0810s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 34 NSOCK INFO [0.0810s] nsock_write(): Write request for 44 bytes to IOD #1 EID 43 [192.168.220.2:53] NSOCK INFO [0.0810s] nsock_trace_handler_callback(): Callback: WRITE SUCCESS for EID 43 [192.168.220.2:53] NSOCK INFO [0.1140s] nsock_trace_handler_callback(): Callback: READ SUCCESS for EID 34 [192.168.220.2:53] (44 bytes): .............11.49.101.180.in-addr.arpa..... NSOCK INFO [0.1140s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 50 NSOCK INFO [0.1140s] nsock_write(): Write request for 44 bytes to IOD #1 EID 59 [192.168.220.2:53] NSOCK INFO [0.1140s] nsock_trace_handler_callback(): Callback: WRITE SUCCESS for EID 59 [192.168.220.2:53] NSOCK INFO [0.1450s] nsock_trace_handler_callback(): Callback: READ SUCCESS for EID 50 [192.168.220.2:53] (44 bytes): .............11.49.101.180.in-addr.arpa..... NSOCK INFO [0.1450s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 66 NSOCK INFO [0.1450s] nsock_iod_delete(): nsock_iod_delete (IOD #1) NSOCK INFO [0.1450s] nevent_delete(): nevent_delete on event #66 (type READ) Nmap scan report for www.baidu.com (180.101.49.11) # Host is active Host is up (0.00054s latency). Other addresses for www.baidu.com (not scanned): 180.101.49.12 Nmap done: 1 IP address (1 host up) scanned in 0.15 seconds
- Nmap first sends four probe messages to the target host, ICMP, TCP SYN, TCP ACK, and ICMP Timestamp request, as follows:
# Send ICMP Response Request SENT (0.0442s) ICMP [192.168.220.138 > 180.101.49.11 Echo request (type=8/code=0) id=22759 seq=0] IP [ttl=52 id=28777 iplen=28 ] # Send TCP SYN to 443 SENT (0.0444s) TCP 192.168.220.138:34194 > 180.101.49.11:443 S ttl=57 id=41984 iplen=44 seq=274922632 win=1024 <mss 1460> # Send TCP ack to 80 SENT (0.0445s) TCP 192.168.220.138:34194 > 180.101.49.11:80 A ttl=53 id=35602 iplen=40 seq=0 win=1024 # Send ICMP timestamp request SENT (0.0446s) ICMP [192.168.220.138 > 180.101.49.11 Timestamp request (type=13/code=0) id=32360 seq=0 orig=0 recv=0 trans=0] IP [ttl=58 id=18221 iplen=40 ]
- The target host responded to a TCP RST message:
As you can see from the address and port of the message, it responds to a TCP ACK message. Since TCP ACK is an acknowledgment message and no connection is established, the target responds to a TCP RST message to prove that the target host is online.# Receive ICMP Answer RCVD (0.0450s) TCP 180.101.49.11:80 > 192.168.220.138:34194 R ttl=128 id=26366 iplen=40 seq=274922632 win=32767
Use ICMP Echo to detect request discovery hosts
┌──(root💀kali)-[~] └─# nmap --packet-trace -PE www.baidu.com 3 ⚙ Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-10 01:12 CST SENT (0.1805s) ICMP [192.168.220.138 > 180.101.49.12 Echo request (type=8/code=0) id=37100 seq=0] IP [ttl=37 id=62664 iplen=28 ] RCVD (0.1976s) ICMP [180.101.49.12 > 192.168.220.138 Echo reply (type=0/code=0) id=37100 seq=0] IP [ttl=128 id=26374 iplen=28 ] NSOCK INFO [0.1980s] nsock_iod_new2(): nsock_iod_new (IOD #1) NSOCK INFO [0.1980s] nsock_connect_udp(): UDP connection requested to 192.168.220.2:53 (IOD #1) EID 8 NSOCK INFO [0.1980s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 18 NSOCK INFO [0.1980s] nsock_write(): Write request for 44 bytes to IOD #1 EID 27 [192.168.220.2:53] NSOCK INFO [0.1990s] nsock_trace_handler_callback(): Callback: CONNECT SUCCESS for EID 8 [192.168.220.2:53] NSOCK INFO [0.1990s] nsock_trace_handler_callback(): Callback: WRITE SUCCESS for EID 27 [192.168.220.2:53] NSOCK INFO [0.2330s] nsock_trace_handler_callback(): Callback: READ SUCCESS for EID 18 [192.168.220.2:53] (44 bytes): .X...........12.49.101.180.in-addr.arpa..... NSOCK INFO [0.2330s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 34 NSOCK INFO [0.2330s] nsock_write(): Write request for 44 bytes to IOD #1 EID 43 [192.168.220.2:53] NSOCK INFO [0.2330s] nsock_trace_handler_callback(): Callback: WRITE SUCCESS for EID 43 [192.168.220.2:53] NSOCK INFO [0.2680s] nsock_trace_handler_callback(): Callback: READ SUCCESS for EID 34 [192.168.220.2:53] (44 bytes): .Y...........12.49.101.180.in-addr.arpa..... NSOCK INFO [0.2680s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 50 NSOCK INFO [0.2690s] nsock_write(): Write request for 44 bytes to IOD #1 EID 59 [192.168.220.2:53] NSOCK INFO [0.2690s] nsock_trace_handler_callback(): Callback: WRITE SUCCESS for EID 59 [192.168.220.2:53] NSOCK INFO [0.3030s] nsock_trace_handler_callback(): Callback: READ SUCCESS for EID 50 [192.168.220.2:53] (44 bytes): .Z...........12.49.101.180.in-addr.arpa..... NSOCK INFO [0.3030s] nsock_read(): Read request from IOD #1 [192.168.220.2:53] (timeout: -1ms) EID 66 NSOCK INFO [0.3030s] nsock_iod_delete(): nsock_iod_delete (IOD #1) NSOCK INFO [0.3030s] nevent_delete(): nevent_delete on event #66 (type READ) SENT (0.3044s) TCP 192.168.220.138:49172 > 180.101.49.12:80 S ttl=40 id=47411 iplen=44 seq=678127315 win=1024 <mss 1460> SENT (0.3045s) TCP 192.168.220.138:49172 > 180.101.49.12:8080 S ttl=56 id=33278 iplen=44 seq=678127315 win=1024 <mss 1460> SENT (0.3045s) TCP 192.168.220.138:49172 > 180.101.49.12:5900 S ttl=55 id=8525 iplen=44 seq=678127315 win=1024 <mss 1460> SENT (0.3046s) TCP 192.168.220.138:49172 > 180.101.49.12:139 S ttl=47 id=56043 iplen=44 seq=678127315 win=1024 <mss 1460> SENT (0.3055s) TCP 192.168.220.138:49172 > 180.101.49.12:993 S ttl=40 id=23236 iplen=44 seq=678127315 win=1024 <mss 1460> SENT (0.3056s) TCP 192.168.220.138:49172 > 180.101.49.12:8888 S ttl=59 id=11898 iplen=44 seq=678127315 win=1024 <mss 1460> SENT (0.3056s) TCP 192.168.220.138:49172 > 180.101.49.12:1720 S ttl=51 id=16621 iplen=44 seq=678127315 win=1024 <mss 1460> SENT (0.3057s) TCP 192.168.220.138:49172 > 180.101.49.12:113 S ttl=51 id=42562 iplen=44 seq=678127315 win=1024 <mss 1460> SENT (0.3057s) TCP 192.168.220.138:49172 > 180.101.49.12:995 S ttl=50 id=1002 iplen=44 seq=678127315 win=1024 <mss 1460> ....... SENT (108.7931s) TCP 192.168.220.138:49333 > 180.101.49.12:80 S ttl=42 id=4968 iplen=44 seq=684353138 win=1024 <mss 1460> SENT (108.9542s) TCP 192.168.220.138:49172 > 180.101.49.12:880 S ttl=50 id=64004 iplen=44 seq=678127315 win=1024 <mss 1460> SENT (109.1160s) TCP 192.168.220.138:49174 > 180.101.49.12:880 S ttl=52 id=10999 iplen=44 seq=677996241 win=1024 <mss 1460> Nmap scan report for www.baidu.com (180.101.49.12) Host is up (0.017s latency). Other addresses for www.baidu.com (not scanned): 180.101.49.11 Not shown: 999 filtered tcp ports (no-response) PORT STATE SERVICE 80/tcp open http Nmap done: 1 IP address (1 host up) scanned in 109.31 seconds
The above output information shows the entire scanning process. In this process, Nmap not only implements host discovery, but also performs port scanning.
-
Nmap sent an ICMP Echo request probe message to the target host:
SENT (0.1805s) ICMP [192.168.220.138 > 180.101.49.12 Echo request (type=8/code=0) id=37100 seq=0] IP [ttl=37 id=62664 iplen=28 ]
In this message, the ICMP request type is 8 and the code is 0, which is a normal Ping request.
-
The target host responded to a normal reply ICMP Echo reply:
RCVD (0.1976s) ICMP [180.101.49.12 > 192.168.220.138 Echo reply (type=0/code=0) id=37100 seq=0] IP [ttl=128 id=26374 iplen=28 ]
The response type is 0 and the code is 0, which is a normal Ping response, thus indicating that the target host is active.
When Nmap is used for host discovery, port scanning is done by default. When scanning hosts across a large network, if you only want to detect the state of the host, you can use the -sn option to disable port scanning to save a lot of time.
3.ICMP timestamp
ICMP timestamp requests allow one system to query another system for the current time. If the target host returns time, the target host is active. For security reasons, in practice, some hosts and firewalls usually block ICMP response request messages so that users cannot use ICMP responses to discover hosts. If you forget to block other ICMP query messages, such as ICMP timestamp requests, because the administrator has blocked only the ICMP response request message due to an administrator error, then you can detect the host through the ICMP timestamp request. A -PP option is provided in Nmap to implement ICMP timestamp Ping Ping scans.
Use ICMP timestamp to detect an offline host
┌──(root💀kali)-[~] └─# nmap --packet-trace -sn -PP --send-ip 220.181.38.251 4 ⚙ Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-10 01:38 CST SENT (0.0343s) ICMP [192.168.220.138 > 220.181.38.251 Timestamp request (type=13/code=0) id=45667 seq=0 orig=0 recv=0 trans=0] IP [ttl=42 id=9557 iplen=40 ] SENT (1.0357s) ICMP [192.168.220.138 > 220.181.38.251 Timestamp request (type=13/code=0) id=16815 seq=0 orig=0 recv=0 trans=0] IP [ttl=47 id=38630 iplen=40 ] Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn Nmap done: 1 IP address (0 hosts up) scanned in 2.04 seconds
4. ICMP Address Mask Request
ICMP address mask requests are used by diskless systems to obtain their own subnet mask during boot. If a response from the target host is received, the target host is active. When a user cannot detect the state of the target host using ICMP timestamp, he or she can try using ICMP address mask request mode. The options for implementing ICMP address mask requests and their implications are as follows:
-PM: Conduct ICMP Address mask Ping Scan.
Host discovery using ICMP address mask requests
┌──(root💀kali)-[~] └─# nmap --packet-trace -sn -PM 220.181.38.251 4 ⚙ Starting Nmap 7.92 ( https://nmap.org ) at 2022-03-10 01:41 CST SENT (0.0345s) ICMP [192.168.220.138 > 220.181.38.251 Address mask request (type=17/code=0) id=31595 seq=0 mask=0.0.0.0] IP [ttl=55 id=8706 iplen=32 ] SENT (1.0404s) ICMP [192.168.220.138 > 220.181.38.251 Address mask request (type=17/code=0) id=3363 seq=0 mask=0.0.0.0] IP [ttl=52 id=4988 iplen=32 ] Note: Host seems down. If it is really up, but blocking our ping probes, try -Pn Nmap done: 1 IP address (0 hosts up) scanned in 2.04 seconds
In the above message, the ICMP address mask request type is 17 and the code is 0. There are two probing messages here because Nmap did not receive a response from the target host after sending the first message, so it sent another message for probing, and the result still did not receive a response. It can be judged that the target host is not online.