10.19 iptables rule backup and recovery
service iptables save saves rules to/etc/sysconfig/iptables
Iptables-save > target file Save rules to another file
[root@arslinux-01 ~]# iptables-save > /tmp/ipt.txt [root@arslinux-01 ~]# cat !$ cat /tmp/ipt.txt # Generated by iptables-save v1.4.21 on Wed Apr 17 19:56:24 2019 *filter :INPUT ACCEPT [0:0] :FORWARD ACCEPT [0:0] :OUTPUT ACCEPT [192:17603] -A INPUT -m state --state RELATED,ESTABLISHED -j ACCEPT -A INPUT -p icmp -j ACCEPT -A INPUT -i lo -j ACCEPT -A INPUT -p tcp -m state --state NEW -m tcp --dport 22 -j ACCEPT -A INPUT -j REJECT --reject-with icmp-host-prohibited -A FORWARD -j REJECT --reject-with icmp-host-prohibited COMMIT # Completed on Wed Apr 17 19:56:24 2019
Iptables-restore <archive file] restore iptables rules
[root@arslinux-01 ~]# iptables -F [root@arslinux-01 ~]# iptables -nvL Chain INPUT (policy ACCEPT 24 packets, 1584 bytes) pkts bytes target prot opt in out source destination Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination Chain OUTPUT (policy ACCEPT 13 packets, 1228 bytes) pkts bytes target prot opt in out source destination [root@arslinux-01 ~]# iptables-restore < /tmp/ipt.txt [root@arslinux-01 ~]# iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 40 2640 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 21 packets, 1964 bytes) pkts bytes target prot opt in out source destination
9 zone s of 10.20 firewalld
Disable iptables and open firewalld
[root@arslinux-01 ~]# systemctl disable iptables Removed symlink /etc/systemd/system/basic.target.wants/iptables.service. [root@arslinux-01 ~]# systemctl stop iptables
[root@arslinux-01 ~]# systemctl enable firewalld Created symlink from /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service to /usr/lib/systemd/system/firewalld.service. Created symlink from /etc/systemd/system/multi-user.target.wants/firewalld.service to /usr/lib/systemd/system/firewalld.service. [root@arslinux-01 ~]# systemctl start firewalld
[root@arslinux-01 ~]# iptables -nvL Chain INPUT (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 23 1528 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 1 92 INPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 1 92 INPUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 1 92 INPUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT 0 packets, 0 bytes) pkts bytes target prot opt in out source destination 0 0 ACCEPT all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate RELATED,ESTABLISHED 0 0 ACCEPT all -- lo * 0.0.0.0/0 0.0.0.0/0 0 0 FORWARD_direct all -- * * 0.0.0.0/0 0.0.0.0/0 0 0 FORWARD_IN_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 0 0 FORWARD_IN_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 0 0 FORWARD_OUT_ZONES_SOURCE all -- * * 0.0.0.0/0 0.0.0.0/0 0 0 FORWARD_OUT_ZONES all -- * * 0.0.0.0/0 0.0.0.0/0 0 0 DROP all -- * * 0.0.0.0/0 0.0.0.0/0 ctstate INVALID 0 0 REJECT all -- * * 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT 13 packets, 1180 bytes) pkts bytes target prot opt in out source destination 13 1180 OUTPUT_direct all -- * * 0.0.0.0/0 0.0.0.0/0 Chain FORWARD_IN_ZONES (1 references) pkts bytes target prot opt in out source destination 0 0 FWDI_public all -- ens37 * 0.0.0.0/0 0.0.0.0/0 [goto] 0 0 FWDI_public all -- ens33 * 0.0.0.0/0 0.0.0.0/0 [goto] 0 0 FWDI_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_IN_ZONES_SOURCE (1 references) pkts bytes target prot opt in out source destination Chain FORWARD_OUT_ZONES (1 references) pkts bytes target prot opt in out source destination 0 0 FWDO_public all -- * ens37 0.0.0.0/0 0.0.0.0/0 [goto] 0 0 FWDO_public all -- * ens33 0.0.0.0/0 0.0.0.0/0 [goto] 0 0 FWDO_public all -- * + 0.0.0.0/0 0.0.0.0/0 [goto] Chain FORWARD_OUT_ZONES_SOURCE (1 references) pkts bytes target prot opt in out source destination Chain FORWARD_direct (1 references) pkts bytes target prot opt in out source destination Chain FWDI_public (3 references) pkts bytes target prot opt in out source destination 0 0 FWDI_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 0 0 FWDI_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 0 0 FWDI_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 Chain FWDI_public_allow (1 references) pkts bytes target prot opt in out source destination Chain FWDI_public_deny (1 references) pkts bytes target prot opt in out source destination Chain FWDI_public_log (1 references) pkts bytes target prot opt in out source destination Chain FWDO_public (3 references) pkts bytes target prot opt in out source destination 0 0 FWDO_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 0 0 FWDO_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 0 0 FWDO_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 Chain FWDO_public_allow (1 references) pkts bytes target prot opt in out source destination Chain FWDO_public_deny (1 references) pkts bytes target prot opt in out source destination Chain FWDO_public_log (1 references) pkts bytes target prot opt in out source destination Chain INPUT_ZONES (1 references) pkts bytes target prot opt in out source destination 0 0 IN_public all -- ens37 * 0.0.0.0/0 0.0.0.0/0 [goto] 1 92 IN_public all -- ens33 * 0.0.0.0/0 0.0.0.0/0 [goto] 0 0 IN_public all -- + * 0.0.0.0/0 0.0.0.0/0 [goto] Chain INPUT_ZONES_SOURCE (1 references) pkts bytes target prot opt in out source destination Chain INPUT_direct (1 references) pkts bytes target prot opt in out source destination Chain IN_public (3 references) pkts bytes target prot opt in out source destination 1 92 IN_public_log all -- * * 0.0.0.0/0 0.0.0.0/0 1 92 IN_public_deny all -- * * 0.0.0.0/0 0.0.0.0/0 1 92 IN_public_allow all -- * * 0.0.0.0/0 0.0.0.0/0 0 0 ACCEPT icmp -- * * 0.0.0.0/0 0.0.0.0/0 Chain IN_public_allow (1 references) pkts bytes target prot opt in out source destination 1 92 ACCEPT tcp -- * * 0.0.0.0/0 0.0.0.0/0 tcp dpt:22 ctstate NEW Chain IN_public_deny (1 references) pkts bytes target prot opt in out source destination Chain IN_public_log (1 references) pkts bytes target prot opt in out source destination Chain OUTPUT_direct (1 references) pkts bytes target prot opt in out source destination
firewalld defaults to 9 zone s
block,dmz,drop,external,home,internal,public,trusted,work
firewalld default zone is public
Each zone is a collection of rules with some rules
firewall-cmd --get-zones View all zones
[root@arslinux-01 ~]# firewall-cmd --get-zones block dmz drop external home internal public trusted work
firewall-cmd --get-default-zone View default zone
[root@arslinux-01 ~]# firewall-cmd --get-default-zone public
Detailed explanation of nine zone s

10.21 Firealld's operations on zone s
Firewall-cmd--set-default-zone=name Set default zone
[root@arslinux-01 ~]# firewall-cmd --get-default-zone public [root@arslinux-01 ~]# firewall-cmd --set-default-zone=work success [root@arslinux-01 ~]# firewall-cmd --get-default-zone work
firewall-cmd --get-zone-of-interface=network card name
[root@arslinux-01 ~]# firewall-cmd --get-zone-of-interface=ens33 work [root@arslinux-01 ~]# firewall-cmd --get-zone-of-interface=ens37 work [root@arslinux-01 ~]# firewall-cmd --get-zone-of-interface=lo no zone
Firewall-cmd--zone=public--add-interface=lo Set zone for the specified network card
[root@arslinux-01 ~]# firewall-cmd --get-zone-of-interface=lo no zone [root@arslinux-01 ~]# firewall-cmd --zone=public --add-interface=lo success firewall-cmd: error: unrecognized arguments: --get-zone-of-intreface=lo [root@arslinux-01 ~]# firewall-cmd --get-zone-of-interface=lo public
Firewall-cmd--zone=dmz--change-interface=lo)Change zone for network card
[root@arslinux-01 ~]# firewall-cmd --get-zone-of-interface=lo public [root@arslinux-01 ~]# firewall-cmd --zone=dmz --change-interface=lo success [root@arslinux-01 ~]# firewall-cmd --get-zone-of-interface=lo dmz
firewall-cmd --zone=dmz --remove-interface=lo)Delete zone for network card
[root@arslinux-01 ~]# firewall-cmd --get-zone-of-interface=lo dmz [root@arslinux-01 ~]# firewall-cmd --zone=dmz --remove-interface=lo success [root@arslinux-01 ~]# firewall-cmd --get-zone-of-interface=lo no zone
You can delete without specifying a zone
[root@arslinux-01 ~]# firewall-cmd --get-zone-of-interface=lo public [root@arslinux-01 ~]# firewall-cmd --remove-interface=lo success [root@arslinux-01 ~]# firewall-cmd --get-zone-of-interface=lo no zone
Network card ens37, deleting zone will revert to default zone because of NetworkManage
[root@arslinux-01 ~]# firewall-cmd --get-zone-of-interface=ens37 work [root@arslinux-01 ~]# firewall-cmd --zone=public --change-interface=ens37 The interface is under control of NetworkManager, setting zone to 'public'. success [root@arslinux-01 ~]# firewall-cmd --get-zone-of-interface=ens37 public [root@arslinux-01 ~]# firewall-cmd --remove-interface=ens37 The interface is under control of NetworkManager, setting zone to default. success [root@arslinux-01 ~]# firewall-cmd --get-zone-of-interface=ens37 work
firewall-cmd --get-active-zones View the zone where all network cards in the system are located
[root@arslinux-01 ~]# firewall-cmd --get-active-zones work interfaces: ens33 ens37 public interfaces: lo
10.22 Firealld Operations on service
A service is a subunit under a zone, which you can understand as a specified port
firewall-cmd --get-services View all services
[root@arslinux-01 ~]# firewall-cmd --get-services RH-Satellite-6 amanda-client amanda-k5-client bacula bacula-client bgp bitcoin bitcoin-rpc bitcoin-testnet bitcoin-testnet-rpc ceph ceph-mon cfengine condor-collector ctdb dhcp dhcpv6 dhcpv6-client dns docker-registry docker-swarm dropbox-lansync elasticsearch freeipa-ldap freeipa-ldaps freeipa-replication freeipa-trust ftp ganglia-client ganglia-master git gre high-availability http https imap imaps ipp ipp-client ipsec irc ircs iscsi-target jenkins kadmin kerberos kibana klogin kpasswd kprop kshell ldap ldaps libvirt libvirt-tls managesieve mdns minidlna mongodb mosh mountd ms-wbt mssql murmur mysql nfs nfs3 nmea-0183 nrpe ntp open*** ovirt-imageio ovirt-storageconsole ovirt-vmconsole pmcd pmproxy pmwebapi pmwebapis pop3 pop3s postgresql privoxy proxy-dhcp ptp pulseaudio puppetmaster quassel radius redis rpc-bind rsh rsyncd samba samba-client sane sip sips smtp smtp-submission smtps snmp snmptrap spideroak-lansync squid ssh syncthing syncthing-gui synergy syslog syslog-tls telnet tftp tftp-client tinc tor-socks transmission-client upnp-client vdsm vnc-server wbem-https xmpp-bosh xmpp-client xmpp-local xmpp-server zabbix-agent zabbix-server
firewall-cmd --list-services) View which services are in the current zone
[root@arslinux-01 ~]# firewall-cmd --list-services ssh dhcpv6-client
Firewall-cmd--zone=public--list-service View service under specified zone
[root@arslinux-01 ~]# firewall-cmd --zone=public --list-services ssh dhcpv6-client
firewall-cmd --zone=public --add-service=http*) Add service under specified zone
[root@arslinux-01 ~]# firewall-cmd --zone=public --add-service=http success [root@arslinux-01 ~]# firewall-cmd --zone=public --list-services ssh dhcpv6-client http
The above command only adds changes to memory for temporary effect and needs to be added to the configuration file for permanent effect
Configuration file: /etc/firewalld/zones
Firewall-cmd --zone=public --add-service=ftp--permanent * Specify zone to increase service and add to configuration file
[root@arslinux-01 ~]# firewall-cmd --zone=public --add-service=ftp --permanent success [root@arslinux-01 ~]# ls /etc/firewalld/zones/ public.xml public.xml.old [root@arslinux-01 ~]# cat /etc/firewalld/zones/public.xml
<?xml version="1.0" encoding="utf-8"?> <zone> <short>Public</short> <description>For use in public areas. You do not trust the other computers on networks to not harm your computer. Only selected incoming connections are accepted.</description> <service name="ssh"/> <service name="dhcpv6-client"/> <service name="ftp"/> </zone>
[root@arslinux-01 ~]# firewall-cmd --zone=public --list-services ssh dhcpv6-client http
Requirements: ftp service custom port 1121, need to release ftp under work zone
1. Copy ftp template to/etc/firewalld/services/
[root@arslinux-01 ~]# cp /usr/lib/firewalld/services/ftp.xml /etc/firewalld/services/
2. Edit the ftp.xml file and change the port to 1121
[root@arslinux-01 ~]# vim /etc/firewalld/services/ftp.xml
<?xml version="1.0" encoding="utf-8"?> <service> <short>FTP</short> <description>FTP is a protocol used for remote file transfer. If you plan to make your FTP server publicly available, enable this option. You need the vsftpd package installed for this option to be useful.</description> <port protocol="tcp" port="1121"/> ##Change port number to 1121 <module name="nf_conntrack_ftp"/> </service>
3. Copy the work template to/etc/firewalld/zones/
[root@arslinux-01 ~]# cp /usr/lib/firewalld/zones/work.xml /etc/firewalld/zones/
4. Edit work.xml and add a line <service name="ftp"/>
[root@arslinux-01 ~]# vim /etc/firewalld/zones/work.xml
<?xml version="1.0" encoding="utf-8"?> <zone> <short>Work</short> <description>For use in work areas. You mostly trust the other computers on networks to not harm your computer. Only selected incoming connections are accepted.</description> <service name="ssh"/> <service name="dhcpv6-client"/> <service name="ftp"/> ##Add a line of service </zone>
5. Reload
[root@arslinux-01 ~]# firewall-cmd --reload success
6. View services under work zone
[root@arslinux-01 ~]# firewall-cmd --zone=work --list-services ssh dhcpv6-client ftp
Idea: zones are a set of rules, each zone has corresponding iptables rules, each zone has some services, service is a white list, if there is a demand for a service, then the service can be added to the configuration file and released.
Modify service parameters first, add zone to service
10.23 linux Task Schedule cron
crontab profile
[root@arslinux-01 ~]# cat /etc/crontab
SHELL=/bin/bash PATH=/sbin:/bin:/usr/sbin:/usr/bin MAILTO=root # For details see man 4 crontabs # Example of job definition: # .---------------- minute (0 - 59) # | .------------- hour (0 - 23) # | | .---------- day of month (1 - 31) # | | | .------- month (1 - 12) OR jan,feb,mar,apr ... # | | | | .---- day of week (0 - 6) (Sunday=0 or 7) OR sun,mon,tue,wed,thu,fri,sat # | | | | | # * * * * * user-name command to be executed
Task Schedule Profile, defining several environment variables
Format: Minutes, Hours, Dates, Months, Weeks User Commands
Crontab-e * Enter crontab profile
[root@arslinux-01 ~]# crontab -e
no crontab for root - using an empty one crontab: installing new crontab 0 3 * * * /bin/bash /usr/local/sbin/123.sh >>/tmp/123.log 2>>/tmp/123.log ~
Range 1-10 0 3 1-10 * *
Range every two months 0 31-10 */2
Scope Tuesday and Friday 0 3 1-10 * 2,5
systemctl start crond Start crond
[root@arslinux-01 ~]# systemctl start crond
Check startup: ps aux | grep crond to see if crond is started or if systemctl status crond is running in green?
[root@arslinux-01 ~]# ps aux |grep crond root 6235 0.0 0.1 126316 1672 ? Ss 19:05 0:00 /usr/sbin/crond -n root 8389 0.0 0.0 112724 988 pts/0 S+ 22:31 0:00 grep --color=auto crond
[root@arslinux-01 ~]# systemctl status crond ● crond.service - Command Scheduler Loaded: loaded (/usr/lib/systemd/system/crond.service; enabled; vendor preset: enabled) Active: active (running) since three 2019-04-17 19:05:38 CST; 3h 26min ago Main PID: 6235 (crond) CGroup: /system.slice/crond.service └─6235 /usr/sbin/crond -n 4 month 17 19:05:38 arslinux-01 systemd[1]: Started Command Scheduler. 4 month 17 19:05:38 arslinux-01 crond[6235]: (CRON) INFO (RANDOM_DELAY will be scaled with factor 34% if used.) 4 month 17 19:05:38 arslinux-01 crond[6235]: (CRON) INFO (running with inotify support) 4 month 17 22:30:01 arslinux-01 crond[6235]: (root) RELOAD (/var/spool/cron/root)
If the task plan is placed in the configuration file but not executed, it is likely that the script is using a command instead of an absolute path
There are two solutions: 1, command write absolute path; 2, add command path to PATH variable in configuration file
Suggestion: Write an appended log for each task schedule, correct and error output
[root@arslinux-01 ~]# crontab -e crontab: installing new crontab 1 10 * 2 * /usr/bin/find /tmp/ -type f -mtime +100 |xargs rm -f [root@arslinux-01 ~]# crontab -l 1 10 * 2 * /usr/bin/find /tmp/ -type f -mtime +100 |xargs rm -f
Task schedules are saved in a file corresponding to the user name under /var/spool/cron/. Backing up the changed file will back up the task schedule
If you want to back up a scheduled task, you can directly copy the corresponding file under /var/spool/cron
Crontab-r* Delete Task Schedule
[root@arslinux-01 ~]# crontab -r [root@arslinux-01 ~]# crontab -r no crontab for root
Crontab-u* View the task plan for the specified user
[root@arslinux-01 ~]# crontab -u root -l no crontab for root
Reference resources: http://man.linuxde.net/
10.24 chkconfig tool
chkconfig --list) View all services
[root@arslinux-01 ~]# chkconfig --list Note: This output only shows the SysV service and does not include Native systemd service.SysV Configuration Data May be overwritten by native systemd configuration. To list the systemd services, execute'systemctl list-unit-files'. View services enabled at a specific target Execute 'systemctl list-dependencies [target]'. netconsole 0:off 1:off 2:off 3:off 4:off 5:off 6:off network: 0:off 1:off 2:on 3:on 4:on 5:on 6:off
/etc/init.d/ where the service script is located
[root@arslinux-01 ~]# ls /etc/init.d/ functions netconsole network README
chkconfig service name off
[root@arslinux-01 ~]# chkconfig --list Note: This output only shows the SysV service and does not include Native systemd service.SysV Configuration Data May be overwritten by native systemd configuration. To list the systemd services, execute'systemctl list-unit-files'. View services enabled at a specific target Execute 'systemctl list-dependencies [target]'. netconsole 0:off 1:off 2:off 3:off 4:off 5:off 6:off network: 0:off 1:off 2:on 3:on 4:on 5:on 6:off [root@arslinux-01 ~]# chkconfig network off [root@arslinux-01 ~]# chkconfig --list Note: This output only shows the SysV service and does not include Native systemd service.SysV Configuration Data May be overwritten by native systemd configuration. To list the systemd services, execute'systemctl list-unit-files'. View services enabled at a specific target Execute 'systemctl list-dependencies [target]'. netconsole 0:off 1:off 2:off 3:off 4:off 5:off 6:off network: 0:Close 1:Close 2:Close 3:Close 4:Close 5:Close 6:Close
Open the specified service
[root@arslinux-01 ~]# chkconfig network on [root@arslinux-01 ~]# chkconfig --list Note: This output only shows the SysV service and does not include Native systemd service.SysV Configuration Data May be overwritten by native systemd configuration. To list the systemd services, execute'systemctl list-unit-files'. View services enabled at a specific target Execute 'systemctl list-dependencies [target]'. netconsole 0:off 1:off 2:off 3:off 4:off 5:off 6:off network: 0:off 1:off 2:on 3:on 4:on 5:on 6:off
Change runlevel: change / etc/inittab, but CentOS7 is no longer in use at first
chkconfig --level digital service name on/off Specify a level to turn on or off
[root@arslinux-01 ~]# chkconfig --level 3 network off [root@arslinux-01 ~]# chkconfig --list Note: This output only shows the SysV service and does not include Native systemd service.SysV Configuration Data May be overwritten by native systemd configuration. To list the systemd services, execute'systemctl list-unit-files'. View services enabled at a specific target Execute 'systemctl list-dependencies [target]'. netconsole 0:off 1:off 2:off 3:off 4:off 5:off 6:off network: 0:off 1:off 2:on 3:off 4:on 5:on 6:off [root@arslinux-01 ~]# chkconfig --level 3 network on [root@arslinux-01 ~]# chkconfig --list Note: This output only shows the SysV service and does not include Native systemd service.SysV Configuration Data May be overwritten by native systemd configuration. To list the systemd services, execute'systemctl list-unit-files'. View services enabled at a specific target Execute 'systemctl list-dependencies [target]'. netconsole 0:off 1:off 2:off 3:off 4:off 5:off 6:off network: 0:off 1:off 2:on 3:on 4:on 5:on 6:off
--level can be used before or after, no difference
Chkconfig-level Multiple digital service names on/off Specify multiple levels of on/off (numbers without commas)
[root@arslinux-01 ~]# chkconfig --level 345 network off [root@arslinux-01 ~]# chkconfig --list Note: This output only shows the SysV service and does not include Native systemd service.SysV Configuration Data May be overwritten by native systemd configuration. To list the systemd services, execute'systemctl list-unit-files'. View services enabled at a specific target Execute 'systemctl list-dependencies [target]'. netconsole 0:off 1:off 2:off 3:off 4:off 5:off 6:off network: 0:off 1:off 2:on 3:off 4:off 5:off 6:off
0 and 6 are not open
chkconfig --add service name Customize the service and join the service list
[root@arslinux-01 ~]# ls /etc/init.d/ functions netconsole network README [root@arslinux-01 ~]# cp /etc/init.d/network /etc/init.d/123 [root@arslinux-01 ~]# ls /etc/init.d/ 123 functions netconsole network README [root@arslinux-01 ~]# chkconfig --list Note: This output only shows the SysV service and does not include Native systemd service.SysV Configuration Data May be overwritten by native systemd configuration. To list the systemd services, execute'systemctl list-unit-files'. View services enabled at a specific target Execute 'systemctl list-dependencies [target]'. netconsole 0:off 1:off 2:off 3:off 4:off 5:off 6:off network: 0:off 1:off 2:on 3:on 4:on 5:on 6:off [root@arslinux-01 ~]# chkconfig --add 123 [root@arslinux-01 ~]# chkconfig --list Note: This output only shows the SysV service and does not include Native systemd service.SysV Configuration Data May be overwritten by native systemd configuration. To list the systemd services, execute'systemctl list-unit-files'. View services enabled at a specific target Execute 'systemctl list-dependencies [target]'. 123) 0:off 1:off 2:on 3:on 4:on 5:on 6:off netconsole 0:off 1:off 2:off 3:off 4:off 5:off 6:off network: 0:off 1:off 2:on 3:on 4:on 5:on 6:off
First, customize the service in the / etc/init.d directory, and second, format the contents of the file
chkconfig --del Service Name Delete Custom Service
[root@arslinux-01 ~]# chkconfig --del 123 [root@arslinux-01 ~]# chkconfig --list Note: This output only shows the SysV service and does not include Native systemd service.SysV Configuration Data May be overwritten by native systemd configuration. To list the systemd services, execute'systemctl list-unit-files'. View services enabled at a specific target Execute 'systemctl list-dependencies [target]'. netconsole 0:off 1:off 2:off 3:off 4:off 5:off 6:off network: 0:off 1:off 2:on 3:on 4:on 5:on 6:off
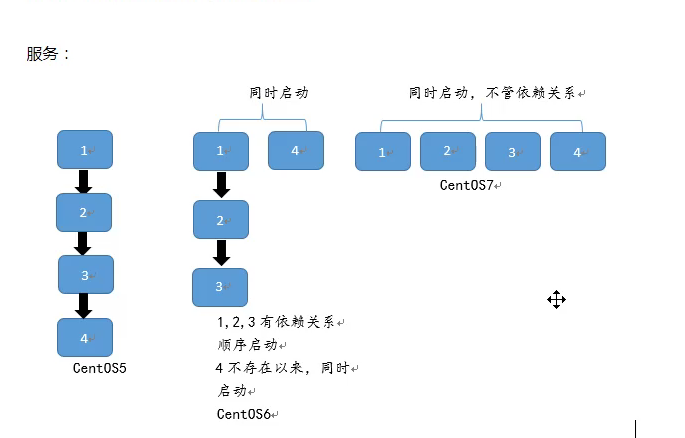
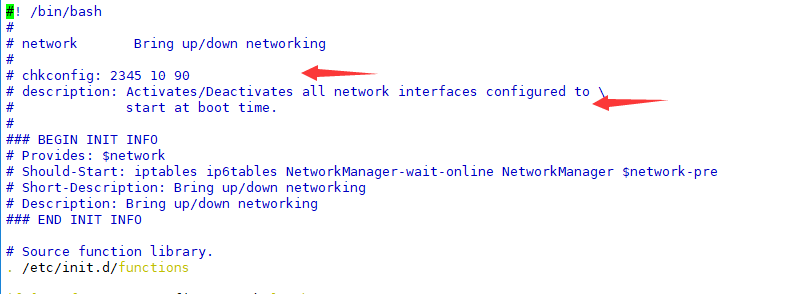
In the format of the service, the two lines indicated by the red arrow must be present in order to be recognized
10.25 systemd Management Service
systemctl list-units --all --type=service List all service services
[root@arslinux-01 ~]# systemctl list-units --all --type=service UNIT LOAD ACTIVE SUB DESCRIPTION 123.service loaded active exited LSB: Bring up/down networking auditd.service loaded active running Security Auditing Service chronyd.service loaded active running NTP client/server cpupower.service loaded inactive dead Configure CPU power related settings crond.service loaded active running Command Scheduler dbus.service loaded active running D-Bus System Message Bus ● display-manager.service not-found inactive dead display-manager.service dm-event.service loaded inactive dead Device-mapper event daemon dracut-shutdown.service loaded inactive dead Restore /run/initramfs ebtables.service loaded inactive dead Ethernet Bridge Filtering tables emergency.service loaded inactive dead Emergency Shell ● exim.service not-found inactive dead exim.service firewalld.service loaded active running firewalld - dynamic firewall daemon getty@tty1.service loaded active running Getty on tty1 ip6tables.service loaded inactive dead IPv6 firewall with ip6tables ● ipset.service not-found inactive dead ipset.service iptables.service loaded inactive dead IPv4 firewall with iptables irqbalance.service loaded inactive dead irqbalance daemon ● kdump.service loaded failed failed Crash recovery kernel arming kmod-static-nodes.service loaded active exited Create list of required static device nod ● lvm2-activation.service not-found inactive dead lvm2-activation.service lvm2-lvmetad.service loaded active running LVM2 metadata daemon lvm2-lvmpolld.service loaded inactive dead LVM2 poll daemon lvm2-monitor.service loaded active exited Monitoring of LVM2 mirrors, snapshots etc lvm2-pvscan@8:17.service loaded active exited LVM2 PV scan on device 8:17 lvm2-pvscan@8:18.service loaded active exited LVM2 PV scan on device 8:18 lines 1-27
No detailed display
systemctl list-units --type=service List active service
[root@arslinux-01 ~]# systemctl list-units --type=service UNIT LOAD ACTIVE SUB DESCRIPTION 123.service loaded active exited LSB: Bring up/down networking auditd.service loaded active running Security Auditing Service chronyd.service loaded active running NTP client/server crond.service loaded active running Command Scheduler dbus.service loaded active running D-Bus System Message Bus firewalld.service loaded active running firewalld - dynamic firewall daemon getty@tty1.service loaded active running Getty on tty1 ● kdump.service loaded failed failed Crash recovery kernel arming kmod-static-nodes.service loaded active exited Create list of required static device nodes for the cur lvm2-lvmetad.service loaded active running LVM2 metadata daemon lvm2-monitor.service loaded active exited Monitoring of LVM2 mirrors, snapshots etc. using dmeven lvm2-pvscan@8:17.service loaded active exited LVM2 PV scan on device 8:17 lvm2-pvscan@8:18.service loaded active exited LVM2 PV scan on device 8:18 lvm2-pvscan@8:19.service loaded active exited LVM2 PV scan on device 8:19 network.service loaded active exited LSB: Bring up/down networking NetworkManager-wait-online.service loaded active exited Network Manager Wait Online NetworkManager.service loaded active running Network Manager polkit.service loaded active running Authorization Manager postfix.service loaded active running Postfix Mail Transport Agent rhel-dmesg.service loaded active exited Dump dmesg to /var/log/dmesg rhel-domainname.service loaded active exited Read and set NIS domainname from /etc/sysconfig/network rhel-import-state.service loaded active exited Import network configuration from initramfs rhel-readonly.service loaded active exited Configure read-only root support rsyslog.service loaded active running System Logging Service sshd.service loaded active running OpenSSH server daemon sysstat.service loaded active exited Resets System Activity Logs lines 1-27
No detailed display
systemctl enable service name Get the service started
systemctl disable service name Keep the service on and off
systemctl status service name View service status
[root@arslinux-01 ~]# systemctl enable crond
[root@arslinux-01 ~]# systemctl status crond ● crond.service - Command Scheduler Loaded: loaded (/usr/lib/systemd/system/crond.service; enabled; vendor preset: enabled) Active: active (running) since four 2019-04-18 18:51:26 CST; 27min ago Main PID: 6132 (crond) CGroup: /system.slice/crond.service └─6132 /usr/sbin/crond -n 4 month 18 18:51:26 arslinux-01 systemd[1]: Started Command Scheduler. 4 month 18 18:51:26 arslinux-01 crond[6132]: (CRON) INFO (RANDOM_DELAY will be scaled with factor 54% if used.) 4 month 18 18:51:26 arslinux-01 crond[6132]: (CRON) INFO (running with inotify support)
[root@arslinux-01 ~]# systemctl disable crond.service Removed symlink /etc/systemd/system/multi-user.target.wants/crond.service.
systemctl stop service name Stop service
systemctl start service name Start service
systemctl restart service name Restart service
[root@arslinux-01 ~]# systemctl stop crond [root@arslinux-01 ~]# systemctl status crond ● crond.service - Command Scheduler Loaded: loaded (/usr/lib/systemd/system/crond.service; disabled; vendor preset: enabled) Active: inactive (dead) 4 month 18 18:51:26 arslinux-01 systemd[1]: Started Command Scheduler. 4 month 18 18:51:26 arslinux-01 crond[6132]: (CRON) INFO (RANDOM_DELAY will be scaled with factor 54% if used.) 4 month 18 18:51:26 arslinux-01 crond[6132]: (CRON) INFO (running with inotify support) 4 month 18 19:22:38 arslinux-01 systemd[1]: Stopping Command Scheduler... 4 month 18 19:22:38 arslinux-01 systemd[1]: Stopped Command Scheduler.
[root@arslinux-01 ~]# systemctl start crond [root@arslinux-01 ~]# systemctl status crond ● crond.service - Command Scheduler Loaded: loaded (/usr/lib/systemd/system/crond.service; disabled; vendor preset: enabled) Active: active (running) since four 2019-04-18 19:23:03 CST; 2s ago Main PID: 7852 (crond) CGroup: /system.slice/crond.service └─7852 /usr/sbin/crond -n 4 month 18 19:23:03 arslinux-01 systemd[1]: Started Command Scheduler. 4 month 18 19:23:03 arslinux-01 crond[7852]: (CRON) INFO (RANDOM_DELAY will be scaled with factor 95% if used.) 4 month 18 19:23:03 arslinux-01 crond[7852]: (CRON) INFO (running with inotify support) 4 month 18 19:23:03 arslinux-01 crond[7852]: (CRON) INFO (@reboot jobs will be run at computer's startup.)
[root@arslinux-01 ~]# systemctl restart crond
systemctl is-enabled crond See if the service is powered on and started
[root@arslinux-01 ~]# systemctl is-enabled crond disabled [root@arslinux-01 ~]# systemctl enable crond Created symlink from /etc/systemd/system/multi-user.target.wants/crond.service to /usr/lib/systemd/system/crond.service. [root@arslinux-01 ~]# systemctl is-enabled crond enabled
Service Profile Content: /etc/systemd/system/multi-user.target.wants/crond.service
[root@arslinux-01 ~]# cat /etc/systemd/system/multi-user.target.wants/crond.service
[Unit] Description=Command Scheduler After=auditd.service systemd-user-sessions.service time-sync.target [Service] EnvironmentFile=/etc/sysconfig/crond ExecStart=/usr/sbin/crond -n $CRONDARGS ExecReload=/bin/kill -HUP $MAINPID KillMode=process [Install] WantedBy=multi-user.target
The actual file is in: /usr/lib/systemd/system/crond.service
If disable service, soft connections will be removed
Introduction to 10.26 unit
All unit s of the system, in/usr/lib/systemd/system
They are divided into the following types:
service * System Services
Group of multiple unit s
device * Hardware Devices
Mount* File system mount point
automount* automount Point
path > File or path
scope * is not an external process started by systemd
Slce* Process Group
snapshot systemd * snapshot
socket
Swap* swap file
timer
unit related commands
systemctl list-units List running units
[root@arslinux-01 ~]# systemctl list-units UNIT LOAD ACTIVE SUB DESCRIPTION proc-sys-fs-binfmt_misc.automount loaded active waiting Arbitrary Executable File Formats File Syste sys-devices-pci0000:00-0000:00:07.1-ata2-host2-target2:0:0-2:0:0:0-block-sr0.device loaded active plugged VMwa sys-devices-pci0000:00-0000:00:10.0-host0-target0:0:0-0:0:0:0-block-sda-sda1.device loaded active plugged VMwa sys-devices-pci0000:00-0000:00:10.0-host0-target0:0:0-0:0:0:0-block-sda-sda2.device loaded active plugged VMwa sys-devices-pci0000:00-0000:00:10.0-host0-target0:0:0-0:0:0:0-block-sda-sda3.device loaded active plugged VMwa sys-devices-pci0000:00-0000:00:10.0-host0-target0:0:0-0:0:0:0-block-sda.device loaded active plugged VMware_Vi sys-devices-pci0000:00-0000:00:10.0-host0-target0:0:1-0:0:1:0-block-sdb-sdb1.device loaded active plugged LVM sys-devices-pci0000:00-0000:00:10.0-host0-target0:0:1-0:0:1:0-block-sdb-sdb2.device loaded active plugged LVM sys-devices-pci0000:00-0000:00:10.0-host0-target0:0:1-0:0:1:0-block-sdb-sdb3.device loaded active plugged LVM sys-devices-pci0000:00-0000:00:10.0-host0-target0:0:1-0:0:1:0-block-sdb.device loaded active plugged VMware_Vi sys-devices-pci0000:00-0000:00:11.0-0000:02:01.0-net-ens33.device loaded active plugged 82545EM Gigabit Ethern sys-devices-pci0000:00-0000:00:11.0-0000:02:02.0-sound-card0.device loaded active plugged ES1371/ES1373 / Crea sys-devices-pci0000:00-0000:00:11.0-0000:02:05.0-net-ens37.device loaded active plugged 82545EM Gigabit Ethern sys-devices-platform-serial8250-tty-ttyS1.device loaded active plugged /sys/devices/platform/serial8250/tty/tt sys-devices-platform-serial8250-tty-ttyS2.device loaded active plugged /sys/devices/platform/serial8250/tty/tt sys-devices-platform-serial8250-tty-ttyS3.device loaded active plugged /sys/devices/platform/serial8250/tty/tt sys-devices-pnp0-00:05-tty-ttyS0.device loaded active plugged /sys/devices/pnp0/00:05/tty/ttyS0 sys-devices-virtual-block-dm\x2d0.device loaded active plugged /sys/devices/virtual/block/dm-0 sys-module-configfs.device loaded active plugged /sys/module/configfs sys-subsystem-net-devices-ens33.device loaded active plugged 82545EM Gigabit Ethernet Controller (Copper) sys-subsystem-net-devices-ens37.device loaded active plugged 82545EM Gigabit Ethernet Controller (Copper) -.mount loaded active mounted / boot.mount loaded active mounted /boot dev-hugepages.mount loaded active mounted Huge Pages File System dev-mqueue.mount loaded active mounted POSIX Message Queue File System run-user-0.mount loaded active mounted /run/user/0 lines 1-27
systemctl list units --all List all units
[root@arslinux-01 ~]# systemctl list-units --all
Not only running, but also failed or inactive
systemctl list-units --all --state=inactive List inactive units
[root@arslinux-01 ~]# systemctl list-units --all --state=inactive UNIT LOAD ACTIVE SUB DESCRIPTION UNIT LOAD ACTIVE SUB DESCRIPTION proc-sys-fs-binfmt_misc.mount loaded inactive dead Arbitrary Executable File Formats File Sys sys-fs-fuse-connections.mount loaded inactive dead FUSE Control File System tmp.mount loaded inactive dead Temporary Directory systemd-ask-password-console.path loaded inactive dead Dispatch Password Requests to Console Dire cpupower.service loaded inactive dead Configure CPU power related settings ● display-manager.service not-found inactive dead display-manager.service dm-event.service loaded inactive dead Device-mapper event daemon dracut-shutdown.service loaded inactive dead Restore /run/initramfs ebtables.service loaded inactive dead Ethernet Bridge Filtering tables emergency.service loaded inactive dead Emergency Shell ● exim.service not-found inactive dead exim.service ip6tables.service loaded inactive dead IPv6 firewall with ip6tables ● ipset.service not-found inactive dead ipset.service iptables.service loaded inactive dead IPv4 firewall with iptables irqbalance.service loaded inactive dead irqbalance daemon ● lvm2-activation.service not-found inactive dead lvm2-activation.service lvm2-lvmpolld.service loaded inactive dead LVM2 poll daemon microcode.service loaded inactive dead Load CPU microcode update ● ntpd.service not-found inactive dead ntpd.service ● ntpdate.service not-found inactive dead ntpdate.service plymouth-quit-wait.service loaded inactive dead Wait for Plymouth Boot Screen to Quit plymouth-quit.service loaded inactive dead Terminate Plymouth Boot Screen plymouth-read-write.service loaded inactive dead Tell Plymouth To Write Out Runtime Data plymouth-start.service loaded inactive dead Show Plymouth Boot Screen rc-local.service loaded inactive dead /etc/rc.d/rc.local Compatibility rescue.service loaded inactive dead Rescue Shell lines 1-27
systemctl list-units --type=service List services with active status
[root@arslinux-01 ~]# systemctl list-units --type=service UNIT LOAD ACTIVE SUB DESCRIPTION 123.service loaded active exited LSB: Bring up/down networking auditd.service loaded active running Security Auditing Service chronyd.service loaded active running NTP client/server crond.service loaded active running Command Scheduler dbus.service loaded active running D-Bus System Message Bus firewalld.service loaded active running firewalld - dynamic firewall daemon getty@tty1.service loaded active running Getty on tty1 ● kdump.service loaded failed failed Crash recovery kernel arming kmod-static-nodes.service loaded active exited Create list of required static device nodes for the cur lvm2-lvmetad.service loaded active running LVM2 metadata daemon lvm2-monitor.service loaded active exited Monitoring of LVM2 mirrors, snapshots etc. using dmeven lvm2-pvscan@8:17.service loaded active exited LVM2 PV scan on device 8:17 lvm2-pvscan@8:18.service loaded active exited LVM2 PV scan on device 8:18 lvm2-pvscan@8:19.service loaded active exited LVM2 PV scan on device 8:19 network.service loaded active exited LSB: Bring up/down networking NetworkManager-wait-online.service loaded active exited Network Manager Wait Online NetworkManager.service loaded active running Network Manager polkit.service loaded active running Authorization Manager postfix.service loaded active running Postfix Mail Transport Agent rhel-dmesg.service loaded active exited Dump dmesg to /var/log/dmesg rhel-domainname.service loaded active exited Read and set NIS domainname from /etc/sysconfig/network rhel-import-state.service loaded active exited Import network configuration from initramfs rhel-readonly.service loaded active exited Configure read-only root support rsyslog.service loaded active running System Logging Service sshd.service loaded active running OpenSSH server daemon sysstat.service loaded active exited Resets System Activity Logs lines 1-27
systemctl is-active service name * See if a service is active
[root@arslinux-01 ~]# systemctl is-active crond active
Similar to: systemctl is-enabled crond.service
Introduction to 10.27 target
For ease of administration, the system manages unit s with a target
systemctl list-unit-files --type=target List all targets in the system
[root@arslinux-01 ~]# systemctl list-unit-files --type=target UNIT FILE STATE basic.target static bluetooth.target static cryptsetup-pre.target static cryptsetup.target static ctrl-alt-del.target disabled default.target enabled emergency.target static final.target static getty-pre.target static getty.target static graphical.target static halt.target disabled hibernate.target static hybrid-sleep.target static initrd-fs.target static initrd-root-fs.target static initrd-switch-root.target static initrd.target static iprutils.target disabled kexec.target disabled local-fs-pre.target static local-fs.target static machines.target disabled multi-user.target enabled network-online.target static network-pre.target static lines 1-27
systemctl list-dependencies target name See which unit s are under the specified target
[root@arslinux-01 ~]# systemctl list-dependencies multi-user.target multi-user.target ● ├─123.service ● ├─auditd.service ● ├─chronyd.service ● ├─crond.service ● ├─dbus.service ● ├─firewalld.service ● ├─irqbalance.service ● ├─kdump.service ● ├─network.service ● ├─NetworkManager.service ● ├─plymouth-quit-wait.service ● ├─plymouth-quit.service ● ├─postfix.service ● ├─rhel-configure.service ● ├─rsyslog.service ● ├─sshd.service ● ├─sysstat.service ● ├─systemd-ask-password-wall.path ● ├─systemd-logind.service ● ├─systemd-readahead-collect.service ● ├─systemd-readahead-replay.service ● ├─systemd-update-utmp-runlevel.service ● ├─systemd-user-sessions.service ● ├─tuned.service ● ├─vmtoolsd.service ● ├─basic.target lines 1-27
You can continue to include target below the target
systemctl get-default
[root@arslinux-01 ~]# systemctl get-default multi-user.target
systemctl set-default target name set default target
[root@arslinux-01 ~]# systemctl set-default multi-user.target Removed symlink /etc/systemd/system/default.target. Created symlink from /etc/systemd/system/default.target to /usr/lib/systemd/system/multi-user.target.
A service belongs to a type of unit
Multiple unit s form a target
A target contains multiple service s
To see which target a service belongs to, see the [Install] section
[root@arslinux-01 ~]# cat /usr/lib/systemd/system/sshd.service
[Unit] Description=OpenSSH server daemon Documentation=man:sshd(8) man:sshd_config(5) After=network.target sshd-keygen.service Wants=sshd-keygen.service [Service] Type=notify EnvironmentFile=/etc/sysconfig/sshd ExecStart=/usr/sbin/sshd -D $OPTIONS ExecReload=/bin/kill -HUP $MAINPID KillMode=process Restart=on-failure RestartSec=42s [Install] WantedBy=multi-user.target
So sshd.service belongs to multi-user.target
There are many units in the system. For convenience of management, units are grouped into several categories, each of which is target.
A target consists of multiple units, a service is a type of unit, and a target contains multiple services
extend
firewalld custom iptables rule https://blog.51cto.com/jevic/1785162
Blog providing a series of iptables articles https://www.zsythink.net/archives/tag/iptables/page/2/
anacron https://www.jianshu.com/p/3009a9b7d024?from=timeline
systemd custom startup script http://www.jb51.net/article/100457.htm
Class Notes
iptables -A INPUT -p tcp --dport 80 -j ACCEPT
firewall-cmd --add-port=80/tcp
firewall-cmd --permanent --add-port=80/tcp; firewall-cmd --reload
firewall-cmd --permanent --add-service=http; firewall-cmd --reload
How firewall-cmd adds custom rules:
https://blog.51cto.com/jevic/1785162