Secret
A Secret is an object that contains a small amount of sensitive information, such as a password, token, or key. Such information may be placed in the Pod protocol or in the image. Using Secret means you don't need to include confidential data in your application code. (this passage comes from the official website)
The use process is similar to that of ConfigMap
Unlike ConfigMap:
- ConfigMap is used for plaintext and Secret is used to encrypt files, such as password
- ConfigMap has no type, but Secret has type
Common Secret types:
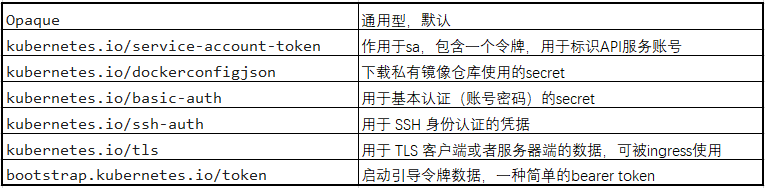
Creation of Secret
Or use two common methods: kubectl and configuration file
- First create an experimental environment: including a folder and two files
[root@k8s-master01 ~]# cd /secret/ [root@k8s-master01 secret]# echo -n 'yyang' > user.txt [root@k8s-master01 secret]# echo -n '1qaz2wsx' > passwd.txt [root@k8s-master01 secret]# ls passwd.txt user.txt
- Use the above environment to create a Secret
[root@k8s-master01 secret]# kubectl create secret generic db-user-pass \ > --from-file=user.txt \ > --from-file=passwd.txt secret/db-user-pass created
- View the content of this secret: the type is Opaque; The content under data in the content has been represented by ciphertext
[root@k8s-master01 secret]# kubectl get secrets NAME TYPE DATA AGE db-user-pass Opaque 2 68s default-token-7h7vk kubernetes.io/service-account-token 3 5h51m [root@k8s-master01 secret]# kubectl get secrets db-user-pass -o yaml apiVersion: v1 data: passwd.txt: MXFhejJ3c3g= user.txt: eXlhbmc= kind: Secret metadata: creationTimestamp: "2022-03-02T07:36:41Z" name: db-user-pass namespace: default resourceVersion: "40252" uid: a46ab9ed-c67c-4195-a5d6-f38dfc3d2016 type: Opaque
- This value can be decrypted: the data in front of the email is the previous encrypted data
[root@k8s-master01 secret]# echo "MXFhejJ3c3g=" | base64 -d 1qaz2wsx You are /var/spool/mail/root New messages in
- The kubectl method has similar creation effect, so only the official example is given (note the single quotation mark)
kubectl create secret generic db-user-pass \ --from-literal=username=devuser \ --from-literal=password='S!B\*d$zDsb='
The other is the configuration file method, which first converts data such as account and password into encrypted data, then creates a yaml file, and then executes the yaml file; This method is more troublesome, so let's take a look at the official example:
Create a Secret using a configuration file
secret applied to docker private warehouse
When you need to verify when pull ing the image of a private warehouse, you can create a corresponding secret for the docker private warehouse. The format is as follows:
I won't write the specific creation
kubectl create secret docker-registry secret-tiger-docker \ --docker-username=user \ --docker-password=pass113 \ --docker-email=tiger@acme.com \ --docker-server=string
The above items include the user name, password, email address and warehouse address of the warehouse
When you use this secret after creating it, you can put it under the spec, which is the same level as containers
spec:
imagePullSecrets:
- name: secret-tiger-docker
containers:
- image: Private warehouse address
name: nginx
In this way, you don't need a password to download the private warehouse image.
Note: pay attention to namespace isolation
Another common type is tls, which is created in a similar way and used in a similar way. I don't write, and I don't have a suitable environment.
other
In other aspects, Secret is similar to ConfigMap. Please see here
ConfigMap