1, String type
String is the most basic type of redis. It can store up to 512MB of data. String is binary safe, that is, it can store any data, such as numbers, pictures, serialized objects, etc
1.1,set / get / append / strlen
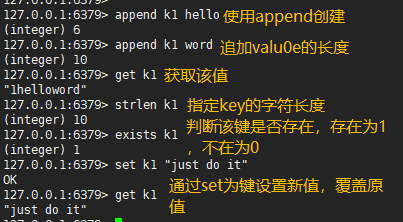
127.0.0.1:6379> append k1 hello #The key does not exist, so append is not created (integer) 5 127.0.0.1:6379> append k1 word #The key already exists, so the length value of the appended value is returned (integer) 9 127.0.0.1:6379> get k1 #Get the key value through the get command "helloword" 127.0.0.1:6379> strlen k1 #Gets the character length of the specified key (integer) 9 127.0.0.1:6379> exists k1 #Judge whether the key exists, return 1 if it exists, otherwise return 0 (integer) 1 127.0.0.1:6379> set k1 "just do it" # OK 127.0.0.1:6379> get k1 #Set a new value for the key through the set command and overwrite the original value "just do it"
1.2 ,incr / decr / incrby / decrby
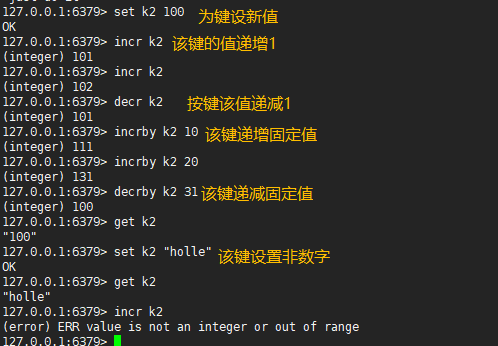
127.0.0.1:6379> set k2 100 #Set new value for key OK 127.0.0.1:6379> incr k2 #The value of this key is incremented by 1 (integer) 101 127.0.0.1:6379> incr k2 (integer) 102 127.0.0.1:6379> decr k2 #The value of this key is decremented by 1 (integer) 101 127.0.0.1:6379> incrby k2 10 #The value of this key is incremented by a fixed value (integer) 111 127.0.0.1:6379> decrby k2 30 #The value of this key is reduced by a fixed value (integer) 81 127.0.0.1:6379> get k2 "81" 127.0.0.1:6379> set k2 "hello" #The value of this key is set to a non numeric value OK 127.0.0.1:6379> get k2 "hello" 127.0.0.1:6379> incr k2 #Non numeric cannot achieve self growth. It must be an integer (error) ERR value is not an integer or out of range
1.3,getset
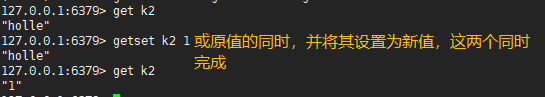
Get the return value of the key and set a new value for the key
127.0.0.1:6379> get k2 "hello" 127.0.0.1:6379> getset k2 1 #When the original value is obtained and set to the new value, the two operations are completed atomically at the same time "hello" 127.0.0.1:6379> get k2 "1"
1.4,setex
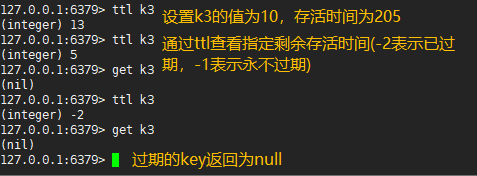
Set the expiration time of the key value to seconds
127.0.0.1:6379> setex k3 20 10 #Set the value of k3 to 10 and the survival time to 20S OK 127.0.0.1:6379> ttl k3 #View the remaining survival time (seconds) of the specified key through the ttl command, - 2 means it has expired and - 1 means it will never expire (integer) 12 127.0.0.1:6379> ttl k3 (integer) 9 127.0.0.1:6379> get k3 "10" 127.0.0.1:6379> ttl k3 (integer) -2 127.0.0.1:6379> get k3 #Expired key s are returned as nil (nil)
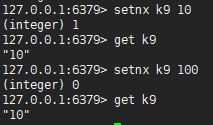
1.5,setnx
Create the specified key. If the key exists, it will not be executed. If it does not exist, it will be executed
127.0.0.1:6379> setnx k9 10 (integer) 1 127.0.0.1:6379> get k9 "10" 127.0.0.1:6379> setnx k9 100 (integer) 0 127.0.0.1:6379> get k9 "10"
1.6,mset / mget / msetnx
Batch instruction
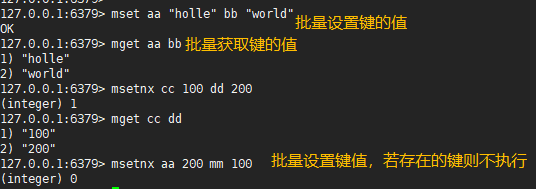
127.0.0.1:6379> mset aa "hello" bb "world" #Value of batch setting key OK 127.0.0.1:6379> mget aa bb #Batch get key values 1) "hello" 2) "world" 127.0.0.1:6379> msetnx cc 100 dd 200 (integer) 1 127.0.0.1:6379> mget cc dd 1) "100" 2) "200" 127.0.0.1:6379> msetnx aa 200 mm 100 #Set key values in batch. If there are existing keys, they will not be executed (integer) 0
2, List type
The element type of the list is string, sorted according to the insertion order, and elements are added at the head or tail of the list
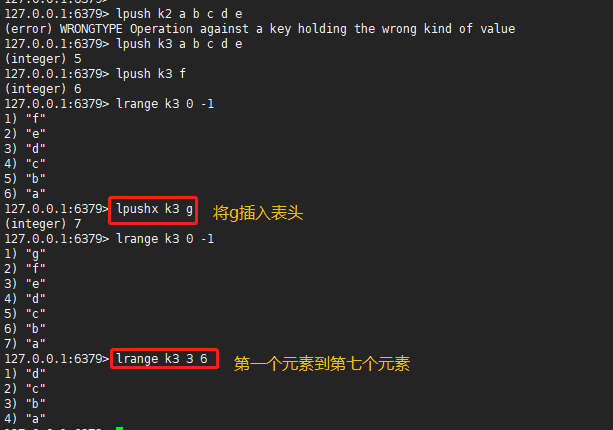
lpush: #The command will create the key and its associated List, and then insert the values in the parameter into the header from left to right lpushx: #This command inserts the value value into the header only when the key exists lrange: #Returns the elements within the specified interval in the list. 0 represents the first element and 1 represents the second element
127.0.0.1:6379> lpush k2 a b c d e (error) WRONGTYPE Operation against a key holding the wrong kind of value 127.0.0.1:6379> lpush k3 a b c d e (integer) 5 127.0.0.1:6379> lpush k3 f (integer) 6 127.0.0.1:6379> lrange k3 0 -1 1) "f" 2) "e" 3) "d" 4) "c" 5) "b" 6) "a" 127.0.0.1:6379> lpushx k3 g #Insert g into header (integer) 7 127.0.0.1:6379> lrange k3 0 -1 1) "g" 2) "f" 3) "e" 4) "d" 5) "c" 6) "b" 7) "a" 127.0.0.1:6379> lrange k3 3 6 #First element to seventh element 1) "d" 2) "c" 3) "b" 4) "a"
2.2,lpop / llen
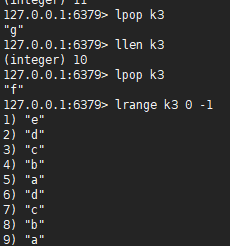
lpop #Remove and return the first element, starting from scratch llen #View the number of elements in the list
127.0.0.1:6379> lpop k3 "g" 127.0.0.1:6379> llen k3 (integer) 10 127.0.0.1:6379> lpop k3 "f" 127.0.0.1:6379> lrange k3 0 -1 1) "e" 2) "d" 3) "c" 4) "b" 5) "a"
2.3,lrem / lset / lindex / ltrim
lrem key count value:Delete from list header count Values are value And returns the actual number of deleted elements lset key index value:Index location as index Set new value for element value lindex key index:Get index is index Element of ltrim key start stop:Keep index from location only start To index stop Element of
127.0.0.1:6379> lpush k4 a b c d b a #Create a list (integer) 6 127.0.0.1:6379> lrange k4 0 -1 1) "a" 2) "b" 3) "d" 4) "c" 5) "b" 6) "a" 127.0.0.1:6379> lrem k4 2 a #Delete two elements with a value equal to a from the left variable list to the right variable list, and the return value is the actual deleted quantity. (integer) 2 127.0.0.1:6379> lrange k4 0 -1 1) "b" 2) "d" 3) "c" 4) "b" 127.0.0.1:6379> lset k4 2 f #Set the third element to f OK 127.0.0.1:6379> lrange k4 0 -1 1) "b" 2) "d" 3) "f" 4) "b" 127.0.0.1:6379> lindex k4 3 #Gets the element with index 3 "b" 127.0.0.1:6379> lrange k4 0 -1 1) "b" 2) "d" 3) "f" 4) "b" 127.0.0.1:6379> ltrim k4 0 2 #Retaining only elements with index 0 to index 2 is equivalent to retaining deletion OK 127.0.0.1:6379> lrange k4 0 -1 1) "b" 2) "d" 3) "f"
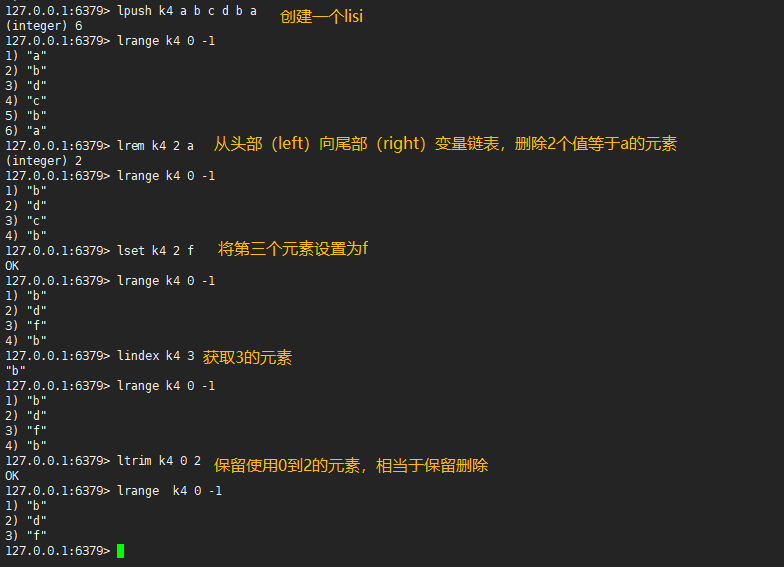
2.4,linsert
linsert #Insert a new element before and after the xxx element of the key
127.0.0.1:6379> lrange k4 0 -1 1) "b" 2) "d" 3) "f" 127.0.0.1:6379> linsert k4 before b 1 (integer) 4 127.0.0.1:6379> lrange k4 0 -1 1) "1" 2) "b" 3) "d" 4) "f" 127.0.0.1:6379> linsert k4 after f 2 (integer) 5 127.0.0.1:6379> lrange k4 0 -1 1) "1" 2) "b" 3) "d" 4) "f" 5) "2" 127.0.0.1:6379> linsert k4 before 1 e (integer) 6 127.0.0.1:6379> lrange k4 0 -1 1) "e" 2) "1" 3) "b" 4) "d" 5) "f" 6) "2" 127.0.0.1:6379>
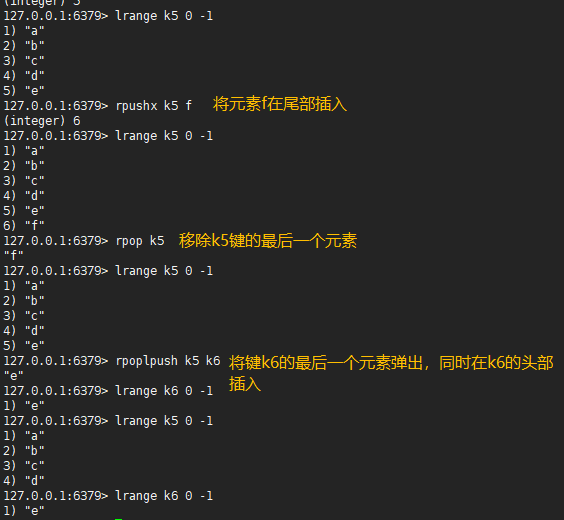
2.5,rpush / rpushx / rpop / rpoplpush
rpush #Insert values from left to right at the end of the table rpushx #The specified key value is inserted from the tail. It will be executed when the key exists, otherwise it will not be executed rpop #Removes and returns the first element of the key, starting at the end rpoplpush #Pop up the element xxx at the end of key 1 and insert it into the head of key 2 (atomically complete these two steps)
127.0.0.1:6379> rpush k5 a b c d e (integer) 5 127.0.0.1:6379> lrange k5 0 -1 1) "a" 2) "b" 3) "c" 4) "d" 5) "e" 127.0.0.1:6379> rpushx k5 f #Insert the element f at the end of the key k5 (integer) 6 127.0.0.1:6379> lrange k5 0 -1 1) "a" 2) "b" 3) "c" 4) "d" 5) "e" 6) "f" 127.0.0.1:6379> rpop k5 #Remove the last element of the k5 key "f" 127.0.0.1:6379> lrange k5 0 -1 1) "a" 2) "b" 3) "c" 4) "d" 5) "e" 127.0.0.1:6379> rpoplpush k5 k6 #Pop up the last element of key K5 and insert it at the head of key K6 "e" 127.0.0.1:6379> lrange k6 0 -1 1) "e" 127.0.0.1:6379> lrange k5 0 -1 1) "a" 2) "b" 3) "c" 4) "d" 127.0.0.1:6379> rpoplpush k5 k6 "d" 127.0.0.1:6379> lrange k5 0 -1 1) "a" 2) "b" 3) "c" 127.0.0.1:6379> lrange k6 0 -1 1) "d" 2) "e"
3, Hash type
hash is used to store objects. This naming method can be adopted: the object category and ID constitute the key name, the field is used to represent the attribute of the object, and the field value stores the attribute value.
If the Hash contains few fields, this type of data will also take up very little disk space. Each Hash can store 4294967295 key value pairs.
3.1,hset / hget / hdel / hexists / hlen / hsetnx
| command | meaning |
|---|---|
| hset | #Set the field to xxx and the value to xxx for the xxx key |
| hget | #Get the xxx key, and the field is the value of xxx |
| hdel | #Delete the xxx field of the xxx key, and 1 is returned successfully |
| hexists | #Judge whether the xxx field in the xxx key exists, and return 1 if it exists |
| hlen | #Gets the number of fields for the xxx key |
| hsetnx | #To add a new field to the xxx key, whether to execute or not is based on whether this field exists. No matter whether the key exists or not, a return of 1 indicates that the execution is successful |
127.0.0.1:6379> hset k7 zhangsan1 a zhangsan2 b zhangsan3 c (integer) 3 127.0.0.1:6379> get k7 zhangsan1 (error) ERR wrong number of arguments for 'get' command 127.0.0.1:6379> hget k7 zhangsan1 "a" 127.0.0.1:6379> hget k7 zhangsan2 "b" 127.0.0.1:6379> hexists k7 zhangsan4 (integer) 0 127.0.0.1:6379> hlen k7 (integer) 3 127.0.0.1:6379> hget k7 zhangsan3 "c" 127.0.0.1:6379> hsetnx k7 zhangan3 d (integer) 0 127.0.0.1:6379> hget k7 zhangsan3 "c" 127.0.0.1:6379> hsetnx k8 zhangan3 d (integer) 0
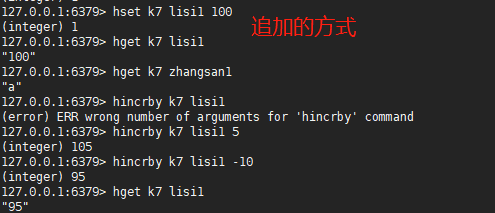
3.2,hincrby
hincrby #Add x to the xxx field value of the xxx key
127.0.0.1:6379> hset k7 lisi1 100 #Additional method (integer) 1 127.0.0.1:6379> hget k7 lisi1 "100" 127.0.0.1:6379> hget k7 zhangsan1 "a" 127.0.0.1:6379> hincrby k7 lisi1 5 (integer) 105 127.0.0.1:6379> hincrby k7 lisi1 -10 (integer) 95 127.0.0.1:6379> hget k7 lisi1 "95"
3.3,hmset / hmget / hgetall / hkeys / hvals
| command | meaning |
|---|---|
| hmset key field value | Create fields and assign values for xxx keys in batches |
| hmget key field | Gets or specifies multiple field values |
| hgetall key | Returns all fields and their values of the xxx key, listed pair by pair |
| hkeys key | Only get all field names in xxx key |
| hvals key | Get only the values of all fields in the xxx key |
127.0.0.1:6379> hmset k8 zhaoliu1 a zhaoliu2 b OK 127.0.0.1:6379> hmget k8 zhaoliu1 zhaoliu2 1) "a" 2) "b" 127.0.0.1:6379> hgetall k8 1) "zhangan3" 2) "d" 3) "zhangan4" 4) "d" 5) "zhangan5" 6) "f" 7) "zhaoliu1" 8) "a" 9) "zhaoliu2" 10) "b" 127.0.0.1:6379> hget k8 zhangsan3 (nil) 127.0.0.1:6379> hget k8 zhaoliu1 "a" 127.0.0.1:6379> hkeys k8 1) "zhangan3" 2) "zhangan4" 3) "zhangan5" 4) "zhaoliu1" 5) "zhaoliu2" 127.0.0.1:6379> hvals k8 1) "d" 2) "d" 3) "f" 4) "a" 5) "b" 127.0.0.1:6379> hget k8 zhaoliu1 zhaoliu2 (error) ERR wrong number of arguments for 'hget' command 127.0.0.1:6379> hmget k8 zhaoliu1 zhaoliu2 1) "a" 2) "b"
4, Set type (unordered set)
Unordered collection. The element type is String. The element is unique. Duplicate members are not allowed. Union, intersection and difference operations can be performed among multiple set types.
Application scope:
① Redis's Set data type can be used to track some unique data, such as the unique IP address information of accessing a blog. For this scenario, we only need to store the visitor's IP in redis every time we visit the blog, and the Set data type will automatically ensure the uniqueness of the IP address.
② Making full use of the convenient and efficient characteristics of Set type server aggregation operation, it can be used to maintain the association relationship between data objects. For example, all customer IDs for purchasing an electronic device are stored in a specified Set, while the customer ID for purchasing another electronic product is stored in another Set. If we want to obtain which customers have purchased these two products at the same time, the intersection command of Set can give full play to its advantages of convenience and efficiency.
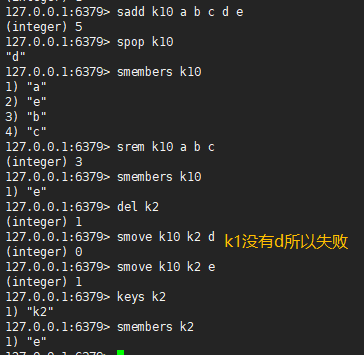
4.1,sadd / smembers / scard / sismember
sadd #If one or more member elements are added to the collection, the member elements that already exist in the collection will be ignored. If the collection key does not exist, create a collection containing only the added elements as members smembers #View the insertion results through the smembers command. The order of output is independent of the insertion order scard #Gets the number of members in the collection sismember #Judge whether the xxx member in the key exists. Return 0 to indicate that it does not exist and 1 to indicate that it exists
127.0.0.1:6379> sadd k1 a b c d e (integer) 5 127.0.0.1:6379> smembers k1 1) "b" 2) "a" 3) "d" 4) "c" 5) "e" 127.0.0.1:6379> scard k1 (integer) 5 127.0.0.1:6379> sismember k1 c (integer) 1 127.0.0.1:6379> sismember k1 f (integer) 0 127.0.0.1:6379>
4.2,spop / srem / srandmember / smove
| command | meaning |
|---|---|
| spop | Randomly remove and return a member of the key |
| srem | Remove xxx, xxx and xxx members from the key and return the number of removed members |
| srandmember | This command returns a member randomly |
| smove | Moving the xxx member of key 1 to key 2 returns 1 for success and 0 for failure |
127.0.0.1:6379> sadd k1 a b c d e (integer) 5 127.0.0.1:6379> spop k1 "d" 127.0.0.1:6379> smembers k1 1) "c" 2) "b" 3) "a" 4) "e" 127.0.0.1:6379> srem k1 a b c (integer) 3 127.0.0.1:6379> smembers k1 1) "e" 127.0.0.1:6379> del k2 (integer) 1 127.0.0.1:6379> smove k1 k2 d #There is no d in k1, so it failed (integer) 0 127.0.0.1:6379> smove k1 k2 e (integer) 1 127.0.0.1:6379> keys k2 1) "k2" 127.0.0.1:6379> smembers k2 1) "e"
5, Sorted Set type (zset, ordered set)
Ordered collection. The element type is String. The element is unique and cannot be repeated.
Each element is associated with a score of double type (representing weight), which can be sorted by the size of weight, and the scores of elements can be the same.
5.1,zadd / zcard / zcount / zrem / zincrby / zscore / zrank
| command | meaning |
|---|---|
| zadd | Add one or more member elements and their fractional values to the ordered set |
| zcard | Gets the number of members in the key |
| zcount | Number of members whose score satisfies the expression x < = score < = x |
| zrem | Delete members xxx and xxx, and return the actual number of deleted members |
| zincrby | If the member xxx does not exist, the zincrby command will add the member and assume its initial score is 0 |
| zscore | Get the score of member xxx |
| zrank | Gets the location index value of member xxx |
127.0.0.1:6379> zadd k1 1 a 2 b 3 c 4 d 5 e (integer) 5 127.0.0.1:6379> zrange k1 0 -1 withscores 1) "a" 2) "1" 3) "b" 4) "2" 5) "c" 6) "3" 7) "d" 8) "4" 9) "e" 10) "5" 127.0.0.1:6379> zcard k1 (integer) 5 127.0.0.1:6379> zcount k1 2 4 (integer) 3 127.0.0.1:6379> zrem k1 a b (integer) 2 127.0.0.1:6379> zcard k1 (integer) 3 127.0.0.1:6379> zincrby k1 2 a "2" 127.0.0.1:6379> zrange k1 0 -1 withscores 1) "a" 2) "2" 3) "c" 4) "3" 5) "d" 6) "4" 7) "e" 8) "5" 127.0.0.1:6379> zincrby k1 -4 a "-2" 127.0.0.1:6379> zrange k1 0 -1 1) "a" 2) "c" 3) "d" 4) "e" 127.0.0.1:6379> zrank k1 c (integer) 1 127.0.0.1:6379> zrank k1 d (integer) 2
5.3,zrangebyscore / zremrangebyrank / zremrrangebyscore
| command | meaning |
|---|---|
| zrangebyscore | Gets the member whose score satisfies the expression x < = score < = X |
| zremrangebyrank | Delete members whose positional index satisfies the expression x < = rank < = X |
| zremrrangebyscore | Delete members whose scores satisfy the expression x < = score < = x, and return the actual deleted quantity. |
|127.0.0.1:6379> zadd k1 1 a 2 b 3 c 4 d 5 e (integer) 5 127.0.0.1:6379> zrangebyscore k1 2 4 1) "b" 2) "c" 3) "d" 127.0.0.1:6379> zrangebyscore k1 -inf +inf limit 2 2 1) "c" 2) "d" 127.0.0.1:6379> zremrangebyrank k1 1 3 (integer) 3 127.0.0.1:6379> zrange k1 0 -1 1) "a" 2) "e" 127.0.0.1:6379> zremrangebyscore k1 1 2 (integer) 1 127.0.0.1:6379> zrange k1 0 -1 1) "e"
5.3,zrevrange / zrevrangebyscore / zrevrank
| command | meaning |
|---|---|
| zrevrange | Get and return the members in this interval from high to low by location index |
| zrevrangebyscore | Get the members whose scores satisfy the expression x > = score > = x and output them in the order from high to bottom. |
| zrevrank | Get member index |
127.0.0.1:6379> zadd k1 1 a 2 b 3 c 4 d 5 e (integer) 5 127.0.0.1:6379> zrange k1 0 -1 1) "a" 2) "b" 3) "c" 4) "d" 5) "e" 127.0.0.1:6379> zrevrsnge k1 0 -1 (error) ERR unknown command `zrevrsnge`, with args beginning with: `k1`, `0`, `-1`, 127.0.0.1:6379> zrevrange k1 0 -1 1) "e" 2) "d" 3) "c" 4) "b" 5) "a" 127.0.0.1:6379> zrevrank k1 a (integer) 4 127.0.0.1:6379> zrank k1 a (integer) 0 127.0.0.1:6379> zrevrangebyscore k1 3 1 1) "c" 2) "b" 3) "a" 127.0.0.1:6379> zrevrangebyscore k1 3 1 limit 1 2 1) "b" 2) "a"
6, Summary
- Data type of Resid:
- String -- string
Hash - Dictionary
List - List
Set -- Set
Sorted Set -- ordered set
- String -- string
- String -- string
- Usage scenarios of other redis functions
- Subscription publish system
Pub/Sub literally means Publish and Subscribe (Subscribe). In Redis, you can set message publishing and message subscription for a key value. When a message is published on a key value, all clients subscribing to it will receive corresponding messages. The most obvious use of this function is as a real-time messaging system, such as ordinary instant chat, group chat and other functions.
- Transactions - transactions
Who says NoSQL doesn't support Transactions, Although redis Transactions does not provide strict ACID Transactions (such as a series of commands submitted and executed by EXEC. If the server goes down during execution, some commands will be executed and the rest will not be executed), this transaction still provides the basic function of command packaging and execution (if there is no problem with the server, you can ensure that a series of commands are executed together in sequence, and other client commands will be inserted in the middle). Redis also provides a Watch function. You can Watch a key and then execute Transactions. In this process, if the value of the Watched is modified, the transaction will be executed Actions will find and reject execution.