Control the release and introduction of RIP routes
Principle overview:
RIP protocol is a routing protocol widely used in real networks. Compared with other routing protocols, RIP is very simple and easy to implement.
In RIP protocol, each rip router will regularly release all the routing information it knows to its direct neighbors, and continuously receive the routing information sent by its direct neighbors to update its own routing table. In this way, it iterates repeatedly, so as to realize the routing convergence of the whole network.
In practice, people often use some routing policy tools to control the route publishing of rip router. For example, filter policy and ACL can be used to filter some specific routes published by RIP router. In some cases, people may need to introduce some external routing information into the rip process. In this process, some routing policy tools can also be used to filter the routes introduced into the rip process, so as to realize some special network requirements.
Purpose of the experiment:
Master how to use filter policy to control RIP route publishing
Deepen the understanding of ACL rule matching process
Experiment content:
Use filter policy and ACL to control the route publishing of RIP protocol, and how to use route policy and ACL to filter the routes introduced into RIP;
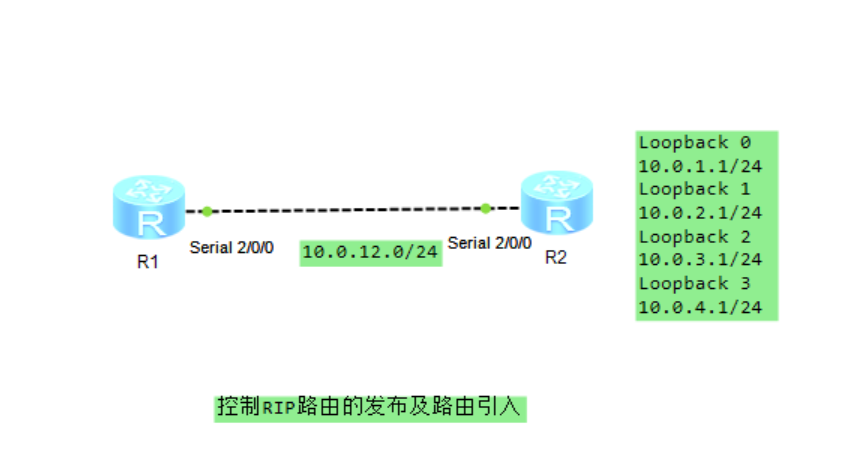
1; Basic configuration:
2: Use filter policy and ACL to control the route publishing of RIP protocol
R1: [R1]rip [R1-rip-1]v 2 [R1-rip-1]un su [R1-rip-1]un summary [R1-rip-1]net [R1-rip-1]network 10.0.0.0 R2: [R2]rip [R2-rip-1]v 2 [R2-rip-1]un su [R2-rip-1]net [R2-rip-1]network 10.0.0.0 [R2-rip-1]import-route direct
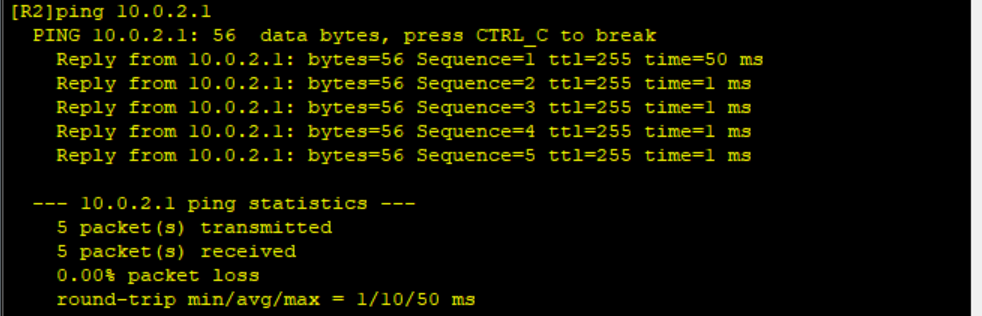
It can be seen that the routing information about Loopback on R2 has been received;
Configure filter policy and ACL to prohibit R2 from publishing 10.0 to R1 1.1/32 and 10.0 3.0/32 these two routing information
[R2]acl 2000 [R2-acl-basic-2000]rule deny source 10.0.1.0 0.0.254.254 [R2-acl-basic-2000]rule permit source any [R2-rip-1]filter-policy 2000 export Serial2/0/0
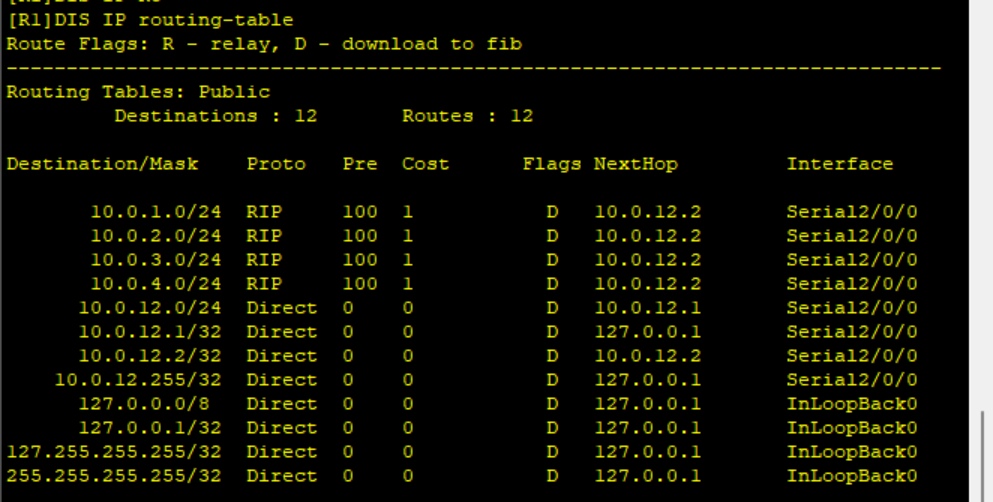
After configuration, view the IP routing table of R1
As you can see, the routing table of R1 is 10.0 1.1/32 and 10.0 3.0/24 these two routes have disappeared, and other routes still exist.
3: Configure static routing
Configure static routing on R1
[R1]ip route-static 1.1.1.1 255.255.255.255 NULL 0 [R1]ip route-static 1.1.1.0 255.255.255.0 NULL 0 [R1]ip route-static 1.1.1.0 255.255.255.128 NULL 0 [R1]ip route-static 1.1.0.0 255.255.0.0 NULL 0 [R1]ip route-static 1.0.0.0 255.0.0.0 NULL 0
After configuration, view the routing table of R1 IP
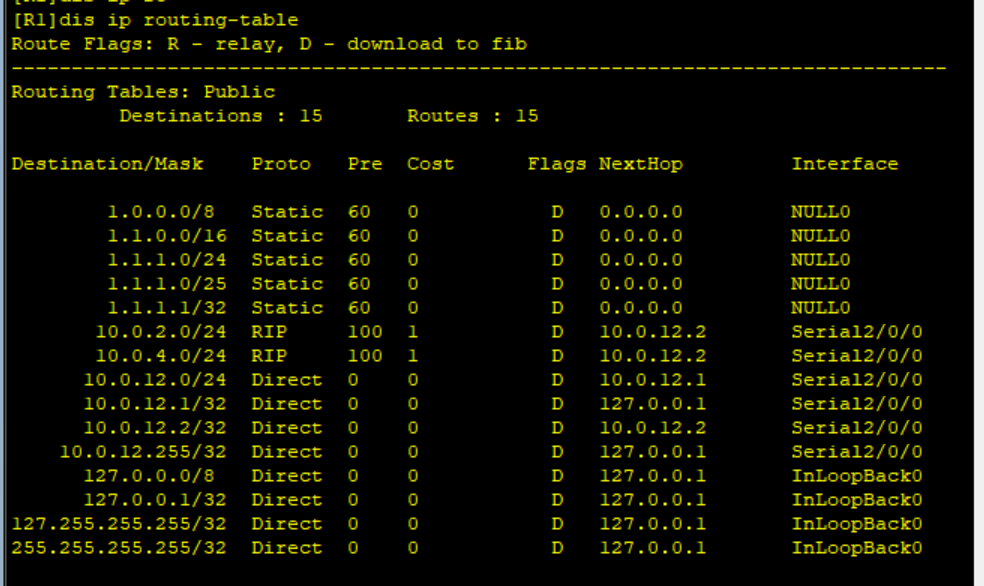
It can be seen that the static route configured on R1 has taken effect;
4: Use route policy and ACL to filter the routes introduced into RIP
Now you need to introduce static routing into the RIP process on R1, but only 1.1.0 is allowed 0.0/16 introduced
Use ACL to match 1.1 0.0/16, the step size of rule number is set to 10
[R1]acl 2000 [R1-acl-basic-2000]step 10 [R1-acl-basic-2000]rule permit source 1.1.0.0 0.0.255.255
Configure route policy
[R1]route-policy import-rip permit node 10 [R1-route-policy]if-match acl 2000
The static route is introduced, and the route policy is used to control the static route
[R1]rip [R1-rip-1]import-route static route-policy import-rip
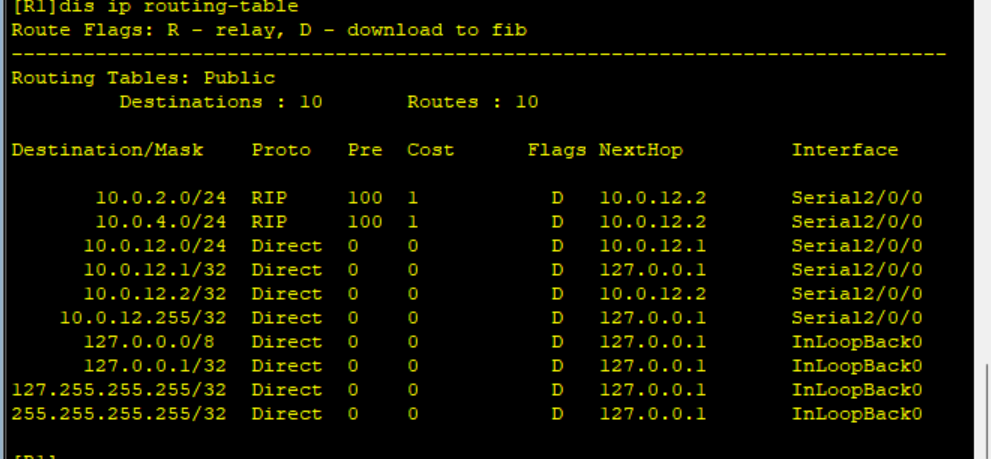
After configuration, view the IP routing table of R2
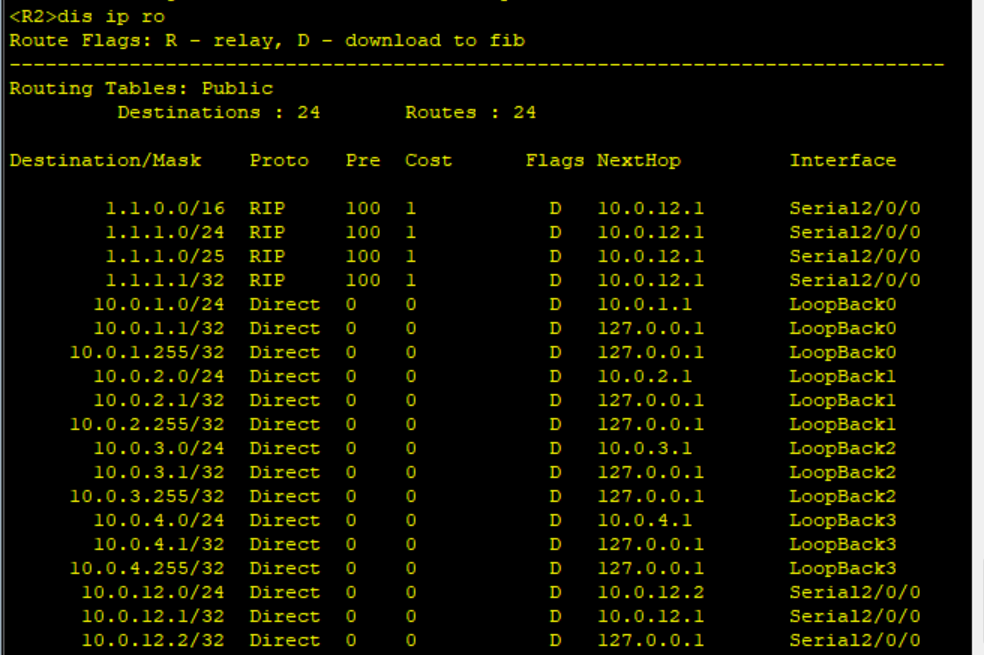
You can see 1.1 0.0 was introduced into the RIP process, but 1.1 1.0/24,1.1. 1.0/25,1.1. 1.0/32 is also introduced into the RIP routing table. This shows that although 1.1 0.0/16 matches the rules of ACL 2000, but at the same time 1.1 1.0/24,1.1. 1.0/25,1.1. 1.0/32 also matches the rules of ACL 2000. The reason for this problem is the improper use of wildcard mask in ACL.
Note that the bits corresponding to "0" of the wildcard mask must be matched, while the bits corresponding to "1" can be ignored.
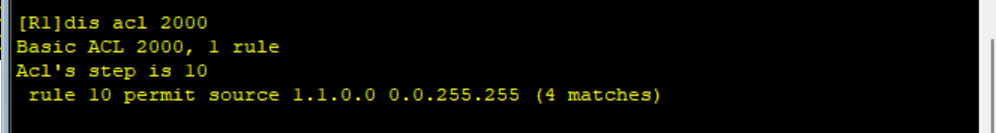
rule 10 of ACL 2000 means that as long as the first 16 bits of the routing item are 0000000, 10000001, it will be matched. Therefore, 1.1 1.0/24,1.1. 1.0/25,1.1. 1.0/32 also match this rule. To uniquely match 1.1 0.0/16, wildcard mask 0.0 should be used 0.0.
Reconfigure ACL on R1
[R1]acl 2000 [R1-acl-basic-2000]undo rule 10 [R1-acl-basic-2000]rule 10 permit source 1.1.0.0 0.0.0.0
View the modified ACL2000
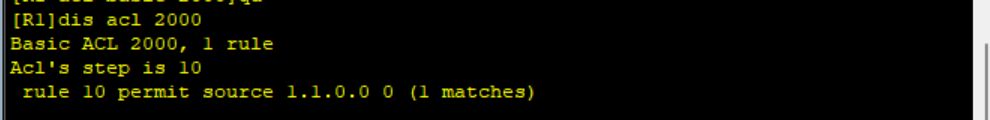
View the IP routing table of R2
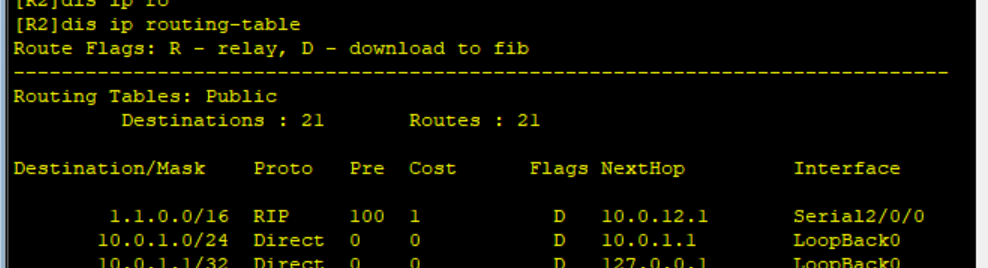
As you can see, 1.1 0.0/16 was received by R2, and the three that could be received were filtered out
Add a rule in ACL2000 1.0/24 and 1.1 1.0/25 is also introduced into RIP
[R1]acl 2000 [R1-acl-basic-2000]rule permit source 1.1.1.0 0.0.0.127
View ACL2000
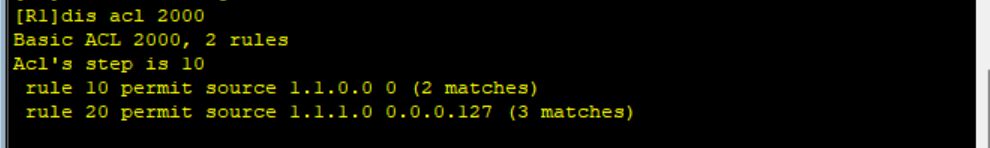
View the IP routing table of R2
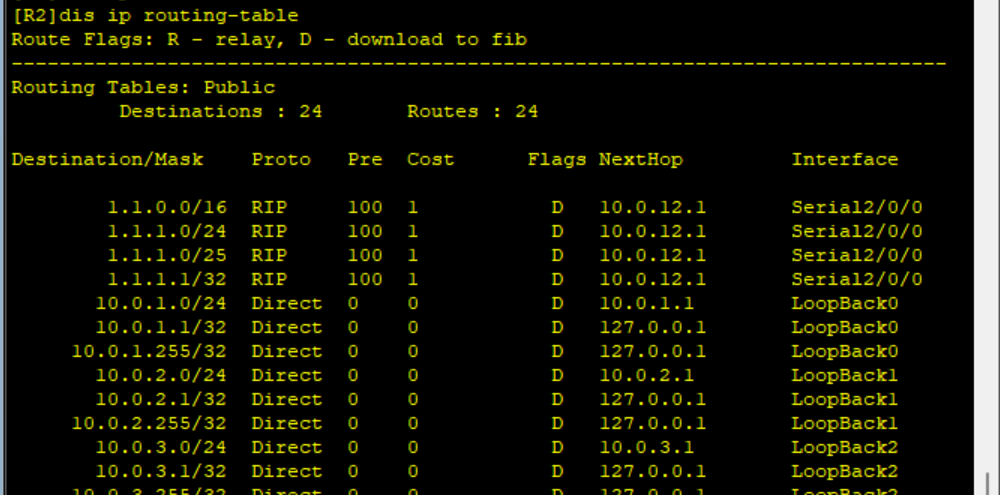
You can see that the target has been introduced, but 1.1 1.1/32 was also introduced, and it was found that 1.1 1.1/32 this road is also matched with rule 20
Modify ACL and reject about 1.1 1.1/32 routing
[R1]acl 2000 [R1-acl-basic-2000]rule deny source 1.1.1.1 0
After configuration, view the RIP routing table
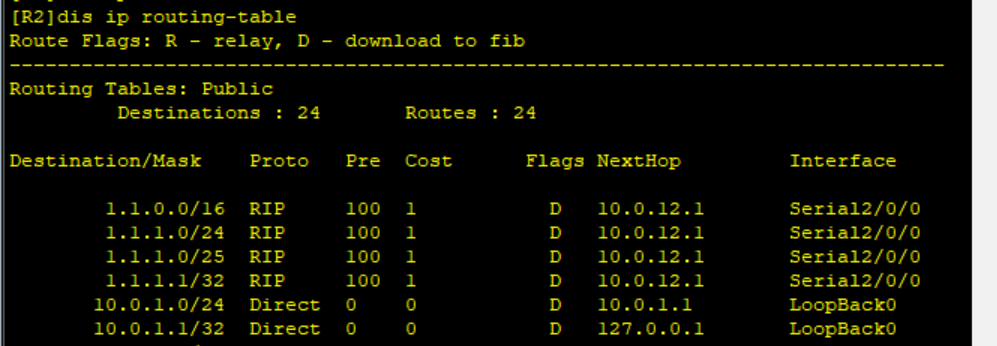
As you can see, route 1.1 1.1/32 is still on the routing table
View ACL2000 again
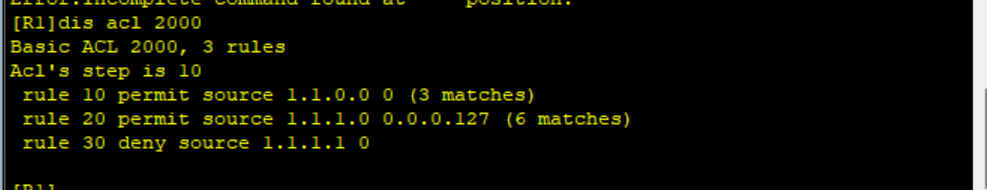
You can see that according to the ACL order rule, 1.1 1.1/32 rule 20 is already matched before rule 30,
Therefore, rule30 does not play a role in filtering 1.1 The role of 1.1/32, the correct process should be to make 1.1 1.1/32 first match to rule 30 Now, delete rule 30, reconfigure a rule, and make the sequence number of the rule less than 20
[R1]acl 2000 [R1-acl-basic-2000]undo rule 30 [R1-acl-basic-2000]rule 15 deny source 1.1.1.1 0
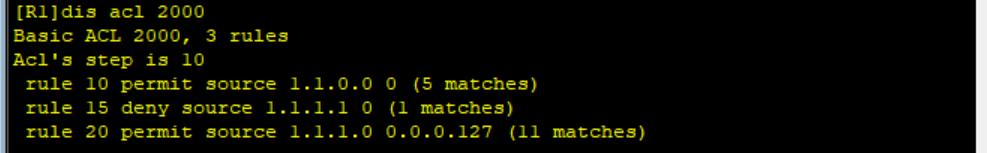
After configuration, view ACL and IP routing table of R2
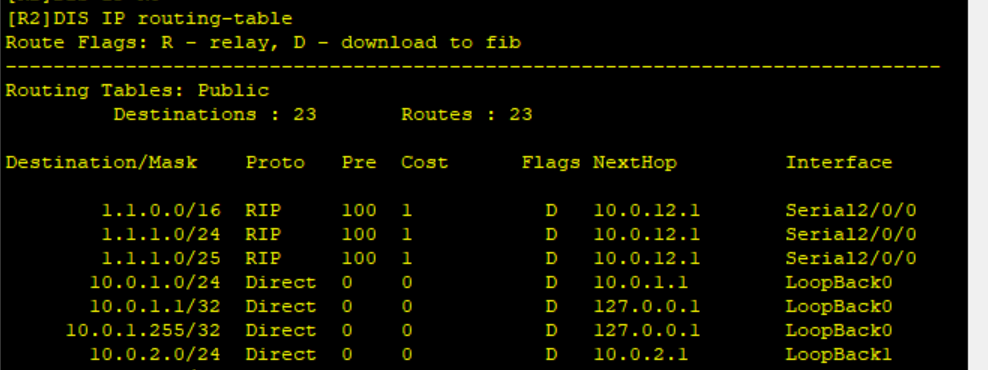
You can see that route 1.1 is no longer in R2's IP routing table 1.1/32, because it has been filtered out when introducing the route on R1.
End of experiment;