samba server
introduce
Samba is a free software that links UNIX operating systems to the SMB/CIFS (Server Message Block/Common Internet File System) network protocol of Microsoft Windows. In the current version (v3), not only can SMB folders and printers be accessed and shared, but also can be integrated into the domain of Windows Server, played as Domain Controller, and joined Active Directory members. In short, this software builds a bridge between Windows and UNIX OS, so that their resources can be interoperable.
In short: a samba server is a shared service that can be used by both linux and windows.
samba server environment deployment
- Install three software:
yum install samba-common.x86_64 samba.x86_64 samba-client.x86_64 -y
- Close the firewall: system CTL stop firewalld.service
- View the configuration file for samba: rpm-qc samba-common
- Modify the configuration file: vim/etc/samba/smb.conf
Write in:
[mac] ##Shared name path = /westos ##Actual shared directory
- Because selinux is open, you need to modify the security context of the shared directory
semanage fcontext -a -t samba_share_t '/westos(/.*)?' ##Modifying the security context of shared directories restorecon -RvvF /westos/ ##All contents of the catalogue take effect
- Open the selinux policy Boolean value and add samba users
getsebool -a | grep samba ##View the Boolean values of selinux policy samba-related policies setsebool -P samba_enable_home_dirs on ##Allow access to samba's user home directory smbpasswd -a student ##To add samba users, the student must be a local user, entering the relevant password for client login pdbedit -L ##View User List systemctl restart smb
- Some operations for samba users:
smbpasswd -a student ##To add samba users, student s must be local users useradd westos useradd lee smbpasswd -a westos ##Add westos users smbpasswd -a lee ##Add lee users pdbedit -L ##View users pdbedit -x student ##Delete users if necessary
Testing on the client side:
- Install client software Yum install samba-client.x86_64-y
- Anonymous user view test: smbclient-L//172.25.254.125
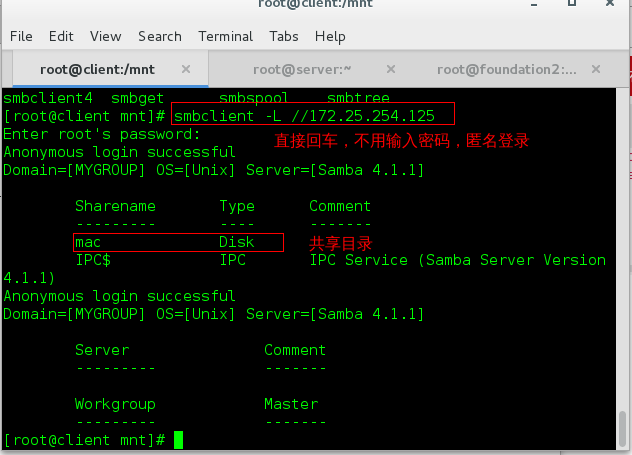 - Specific samba user view: smbclient-L//172.25.254.125-U student
- Specific samba user view: smbclient-L//172.25.254.125-U student
To enter the password you just set on the server.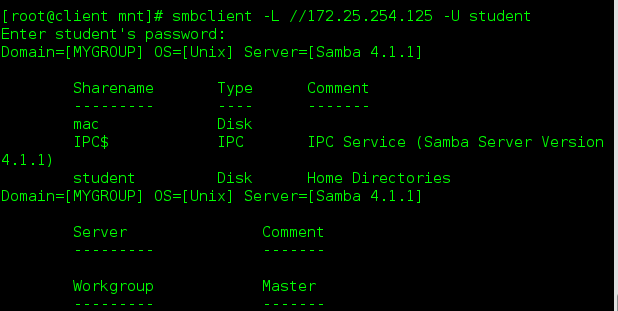 - Log in to the samba server shared directory: smbclient //172.25.254.125/mac-U student
- Log in to the samba server shared directory: smbclient //172.25.254.125/mac-U student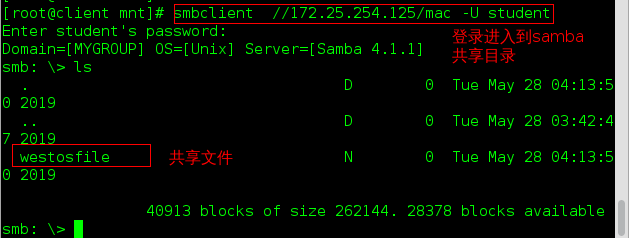 At this point, anonymous users will not be able to log in.
At this point, anonymous users will not be able to log in. - Mount the shared directory mount //172.25.254.125/mac/mnt-o username = student, password = RedHat
Note: Enter the corresponding samba user and password, otherwise you cannot mount successfully.
[root@client /]# mount //172.25.254.125/mac /mnt -o username=student,password=redhat [root@client /]# df Filesystem 1K-blocks Used Available Use% Mounted on /dev/vda1 10473900 3223980 7249920 31% / devtmpfs 927060 0 927060 0% /dev tmpfs 942648 80 942568 1% /dev/shm tmpfs 942648 17016 925632 2% /run tmpfs 942648 0 942648 0% /sys/fs/cgroup //172.25.254.125/mac 10473900 3209144 7264756 31% /mnt
At this point, enter the shared directory / mnt, read-only, not write, how to write? See the following parameter configuration.
Parameter setting of samba server
Most of these parameters are written at the bottom of the configuration file.
| parameter | Explain |
|---|---|
| comment | Add instructions |
| browseable | Add hiding, whether it can be queried, (yes by default, you can see) but whether it can be hidden can be used |
| valid users = specific users | Adding valid users, other users are rejected. + Or @westos users whose group members can log in |
| writable=yes | Directory is writable |
| write list | Writable User List (Only Users Write in List) |
| guest ok = yes | Anonymous user login |
| Global: All programs recognize anonymous users | |
| map to guest= bad user | Anonymous users can mount maps to user = bad user |
| admin users = student | Upgrading User Level: After logging in to samba with student, this directory is equivalent to root identity |
| workgroup | Modify workspace |
Note: All of the following modifications are to modify the samba configuration file on the server side, and the test is to test on the client side.
Modify comment
[root@server westos]# vim /etc/samba/smb.conf //Write in: comment = this is share dic [root@server westos]# systemctl restart smb.service
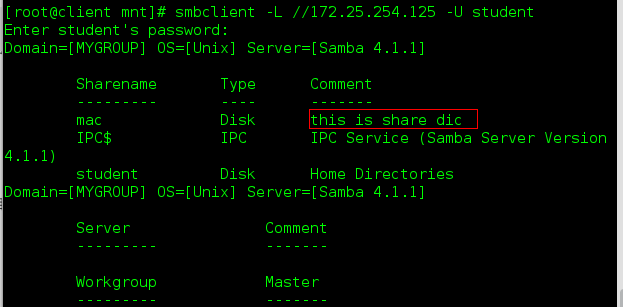
Modify browseable
[root@server westos]# vim /etc/samba/smb.conf //Write in: browseable=no [root@server westos]# systemctl restart smb.service
Test: Shared directories are not visible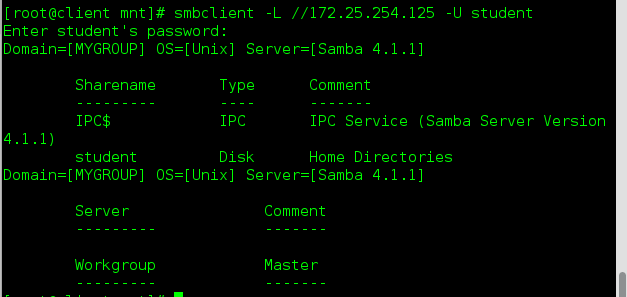
Although hidden, it can still be mounted.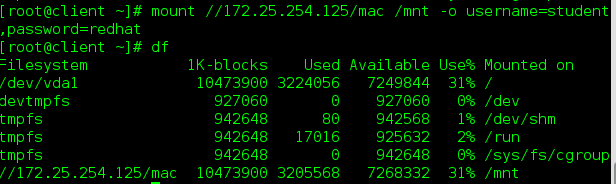
Modify valid users (valid users)
Server:
vim /etc/samba/smb.conf Use; annotate browseable to add valid users systemctl restart smb
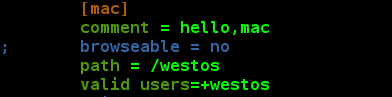
At this time, we add user lee to the additional group of westo, and lee is also a member of westos group, so it is also a valid user, besides, it is not a valid user.
[root@server westos]# usermod -G westos lee [root@server westos]# id lee uid=1002(lee) gid=1002(lee) groups=1002(lee),1001(westos)
Client test:
Testing westos users:
[root@client ~]# smbclient //172.25.254.125/mac -U westos Enter westos's password: Domain=[MACBASKETBALL] OS=[Unix] Server=[Samba 4.1.1] smb: \> ls . D 0 Sun May 26 01:31:45 2019 .. D 0 Wed May 29 02:54:45 2019 file11 N 0 Sat May 25 22:17:57 2019 file3 N 0 Sat May 25 23:21:35 2019 file4 N 0 Sat May 25 23:21:35 2019 file5 N 0 Sat May 25 23:21:35 2019 anaconda-ks.cfg A 8619 Sat May 25 23:35:34 2019 newfile N 0 Sun May 26 01:28:08 2019 leefile N 0 Sun May 26 01:31:43 2019 40913 blocks of size 262144. 28570 blocks available
Test lee users:
[root@client ~]# smbclient //172.25.254.125/mac -U lee Enter lee's password: Domain=[MACBASKETBALL] OS=[Unix] Server=[Samba 4.1.1] smb: \> ls . D 0 Sun May 26 01:31:45 2019 .. D 0 Wed May 29 02:54:45 2019 file11 N 0 Sat May 25 22:17:57 2019 file3 N 0 Sat May 25 23:21:35 2019 file4 N 0 Sat May 25 23:21:35 2019 file5 N 0 Sat May 25 23:21:35 2019 anaconda-ks.cfg A 8619 Sat May 25 23:35:34 2019 newfile N 0 Sun May 26 01:28:08 2019 leefile N 0 Sun May 26 01:31:43 2019 40913 blocks of size 262144. 28570 blocks available
Test invalid user student, connection rejected.
[root@client ~]# smbclient //172.25.254.125/mac -U student Enter student's password: Domain=[MACBASKETBALL] OS=[Unix] Server=[Samba 4.1.1] tree connect failed: NT_STATUS_ACCESS_DENIED
Add directory writable
First, we mount the shared directory. When we enter the mounted directory, we find that we can't write.
[root@client ~]# mount //172.25.254.125/mac /mnt -o username=lee,password=lee [root@client ~]# df Filesystem 1K-blocks Used Available Use% Mounted on /dev/vda1 10473900 3226164 7247736 31% / devtmpfs 469332 0 469332 0% /dev tmpfs 484920 80 484840 1% /dev/shm tmpfs 484920 12752 472168 3% /run tmpfs 484920 0 484920 0% /sys/fs/cgroup /dev/mapper/vg0-vo 483670 2355 451824 1% /home //172.25.254.125/mac 10473900 3159872 7314028 31% /mnt [root@client ~]# cd /mnt/ [root@client mnt]# ls anaconda-ks.cfg file11 file3 file4 file5 leefile newfile [root@client mnt]# rm -fr file11 rm: cannot remove 'file11': Read-only file system
We return to the server:
vim /etc/samba/smb.conf Write in: writable=yes Restart the service after saving
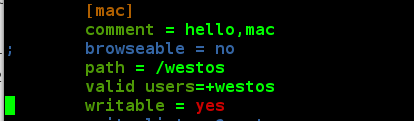
Testing on the client side:
Successful deletion was found and write operations could be performed.
[root@client mnt]# rm -fr file11 rm: cannot remove 'file11': Read-only file system [root@client mnt]# rm -fr file11 [root@client mnt]# ls anaconda-ks.cfg file3 file4 file5 leefile newfile
User Write List
Of course, user writes are built on the premise that the directory is writable. Note that at this time the writable list + or @ indicates that its user group members can also write.
Server:
vim /etc/samba/smb.conf Write in: write list =@westos Restart the service after saving
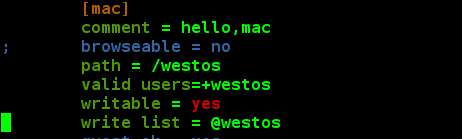
Client test:
When mounted using the westos user group member lee, you can write to the shared directory. Because we just mounted it with lee, we tested it directly and found it writable.
[root@client mnt]# touch filelee [root@client mnt]# ls anaconda-ks.cfg file3 file4 file5 filelee leefile newfile
We uninstall the shared directory / mnt and then mount it through samba user westos to test whether it is writable. Discovery can also be written, because the list of users can be written again.
[root@client ~]# mount //172.25.254.125/mac /mnt -o username=westos,password=westos [root@client ~]# df Filesystem 1K-blocks Used Available Use% Mounted on /dev/vda1 10473900 3226316 7247584 31% / devtmpfs 469332 0 469332 0% /dev tmpfs 484920 80 484840 1% /dev/shm tmpfs 484920 12752 472168 3% /run tmpfs 484920 0 484920 0% /sys/fs/cgroup /dev/mapper/vg0-vo 483670 2355 451824 1% /home //172.25.254.125/mac 10473900 3160012 7313888 31% /mnt [root@client ~]# cd /mnt/ [root@client mnt]# ls anaconda-ks.cfg file3 file4 file5 filelee leefile newfile [root@client mnt]# touch filewestos [root@client mnt]# ls anaconda-ks.cfg file3 file4 file5 filelee filewestos leefile newfile
Similarly, let's test student s who are not in the Writable User List.
At first, we found that it was impossible to mount. After debugging, we found that it was in the server smb.conf configuration file, valid users had no comment, just comment.
[root@client ~]# mount //172.25.254.125/mac /mnt -o username=student,password=redhat [root@client ~]# df Filesystem 1K-blocks Used Available Use% Mounted on /dev/vda1 10473900 3226180 7247720 31% / devtmpfs 469332 0 469332 0% /dev tmpfs 484920 80 484840 1% /dev/shm tmpfs 484920 12752 472168 3% /run tmpfs 484920 0 484920 0% /sys/fs/cgroup /dev/mapper/vg0-vo 483670 2355 451824 1% /home //172.25.254.125/mac 10473900 3160148 7313752 31% /mnt [root@client ~]# cd /mnt/ [root@client mnt]# ls anaconda-ks.cfg file3 file4 file5 filelee filewestos leefile newfile [root@client mnt]# rm -fr filelee rm: cannot remove 'filelee': Permission denied
Discoveries are not authorized and rejected.
Anonymous user login
We found that the client could not log in to the samba shared directory using anonymous users. When the guest ok = yes parameter in the configuration file was modified, the service could be restarted and logged in anonymously.
vim /etc/samba/smb.conf
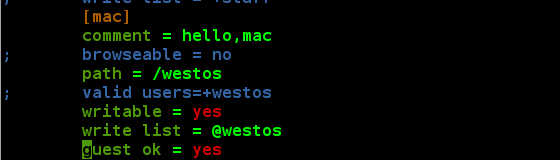
Client test:
[root@client mnt]# smbclient //172.25.254.125/mac Enter root's password: Domain=[MACBASKETBALL] OS=[Unix] Server=[Samba 4.1.1] smb: \> ls . D 0 Wed May 29 03:43:07 2019 .. D 0 Wed May 29 02:54:45 2019 file3 N 0 Sat May 25 23:21:35 2019 file4 N 0 Sat May 25 23:21:35 2019 file5 N 0 Sat May 25 23:21:35 2019 anaconda-ks.cfg A 8619 Sat May 25 23:35:34 2019 newfile N 0 Sun May 26 01:28:08 2019 leefile N 0 Sun May 26 01:31:43 2019 filelee N 0 Wed May 29 03:40:06 2019 filewestos N 0 Wed May 29 03:43:07 2019 40913 blocks of size 262144. 28569 blocks available
Anonymous user can mount
We used to mount shared samba directories through the username and password of specific valid users. Now we can modify configuration file parameters so that anonymous users can also mount.
First, find [global] in the configuration file and add: map to guest = bad user
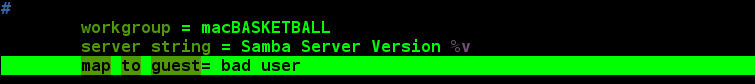
Testing on the client side:
First mount before uninstalling, then try to mount anonymously.
[root@client ~]# mount //172.25.254.125/mac /mnt/ Password for root@//172 [root@client ~]# df Filesystem 1K-blocks Used Available Use% Mounted on /dev/vda1 10473900 3226192 7247708 31% / devtmpfs 469332 0 469332 0% /dev tmpfs 484920 80 484840 1% /dev/shm tmpfs 484920 12752 472168 3% /run tmpfs 484920 0 484920 0% /sys/fs/cgroup /dev/mapper/vg0-vo 483670 2355 451824 1% /home //172.25.254.125/mac 10473900 3159892 7314008 31% /mnt [root@client ~]# cd /mnt/ [root@client mnt]# ls anaconda-ks.cfg file3 file4 file5 filelee filewestos leefile newfile [root@client mnt]# rm -rf leefile rm: cannot remove 'leefile': Permission denied
It was found that the mount was successful, but it was found that anonymous users could not write. The reason is that in addition to services, there is also the issue of shared directory permissions. You can modify permissions 777 on the server side, and anonymous users on the client side can write, but it is generally not recommended to do so.
Upgrading User Level
The parameter admin users = student indicates that the shared directory is equivalent to the root identity after the samba is logged in using student.
On the server side:
Modify configuration files vim /etc/samba/smb.cof Write in: admin users = student Save and restart the service
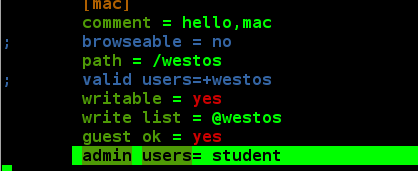
Note: Writable user lists are available only to westos user groups, and student is not.
Testing on the client side:
[root@client ~]# mount //172.25.254.125/mac /mnt/ -o username=student,password=redhat [root@client ~]# df Filesystem 1K-blocks Used Available Use% Mounted on /dev/vda1 10473900 3226196 7247704 31% / devtmpfs 469332 0 469332 0% /dev tmpfs 484920 80 484840 1% /dev/shm tmpfs 484920 12752 472168 3% /run tmpfs 484920 0 484920 0% /sys/fs/cgroup /dev/mapper/vg0-vo 483670 2355 451824 1% /home //172.25.254.125/mac 10473900 3159916 7313984 31% /mnt [root@client ~]# cd /mnt/ [root@client mnt]# ls anaconda-ks.cfg file3 file4 file5 filelee filewestos leefile newfile [root@client mnt]# rm -rf leefile [root@client mnt]# ls anaconda-ks.cfg file3 file4 file5 filelee filewestos newfile
We use student users to mount shared directories, but we do not have writable permissions, but we can still write directories because we have upgraded student user level to root user, root user can of course write.
samba server multiuser mount
Safety
Our previous way of mounting is very unsafe, because the password is exposed directly when mounting, and the content mounted by one user can be seen by other users, which is very unsafe.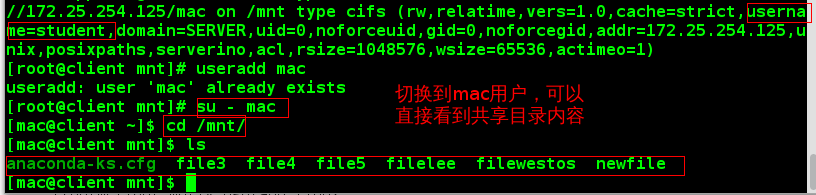
We can install a cifs service that can be mounted by multiple users on the client side, and view the specific configuration information of the service through the man manual:
yum install cifs -y man 8 mount.cifs
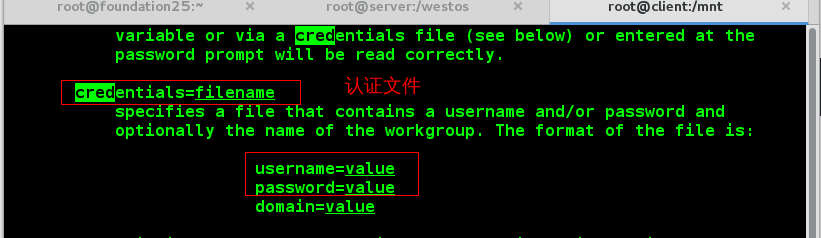
We create a new file / root/smb_auth, which writes the user name and password of the SMB user on the server side, and modifies the permissions of the file. By default, only the root user can read and write:
vim /root/smb_auth //Write in: username=westos password=westos chmod 600 /root/smb_auth
In this way, the password can be mounted directly instead of being displayed directly in the history:
[root@client ~]# mount //172.25.254.125/mac /mnt -o credentials=/root/smb_auth [root@client ~]# df Filesystem 1K-blocks Used Available Use% Mounted on /dev/vda1 10473900 3216928 7256972 31% / devtmpfs 469332 0 469332 0% /dev tmpfs 484920 80 484840 1% /dev/shm tmpfs 484920 12752 472168 3% /run tmpfs 484920 0 484920 0% /sys/fs/cgroup /dev/mapper/vg0-vo 483670 2371 451808 1% /home //172.25.254.125/mac 10473900 3160248 7313652 31% /mnt
At this point, however, other users can still see the contents of the root user's mount directory: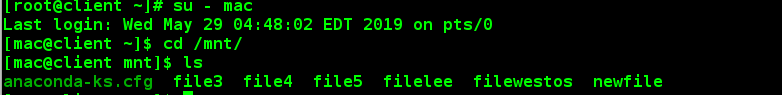
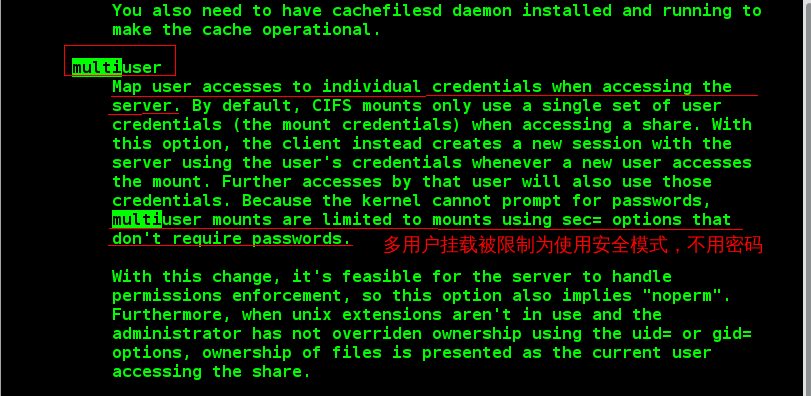
Multiuser Safe Mounting
In order to solve the above problems, combined with man 8 mount.cifs, we can mount in the following format. The authentication method is multi-user mounting, and perfectly solve the security problems:
[root@client ~]# mount //172.25.254.125/mac /mnt -o credentials=/root/smb_auth,sec=ntlmssp,multiuser [root@client ~]# df Filesystem 1K-blocks Used Available Use% Mounted on /dev/vda1 10473900 3216924 7256976 31% / devtmpfs 469332 0 469332 0% /dev tmpfs 484920 80 484840 1% /dev/shm tmpfs 484920 12752 472168 3% /run tmpfs 484920 0 484920 0% /sys/fs/cgroup /dev/mapper/vg0-vo 483670 2371 451808 1% /home //172.25.254.125/mac 10473900 3160012 7313888 31% /mnt
Security parameters, refer to man 8 mount.cifs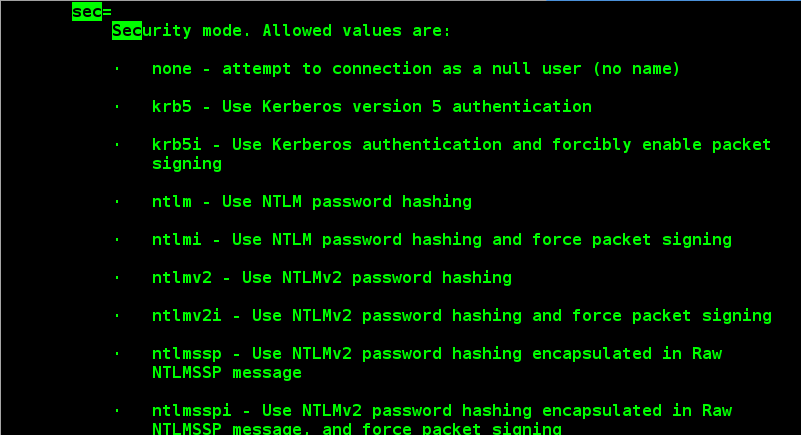
The test found that other users could not view: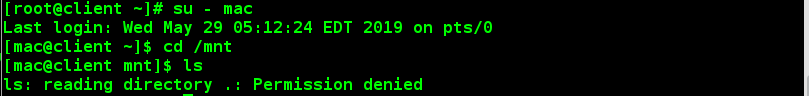
If we want other users to view it, we need to get the identity of a smb user on the server side.
Note: Must be an existing smb user on the server side
[mac@client mnt]$ cifscreds add -u lee 172.25.254.125 Password: [mac@client mnt]$ ls anaconda-ks.cfg file3 file4 file5 filelee filewestos newfile
That is to say, you must know the password of the smb server smb user before you can see the shared directory, which is more secure.
Multiuser permanent mount
On the client side:
vim /etc/fstab //Write in: //172.25.254.125/mac /mnt cifs defaults,credentials=/root/smb_auth,sec=ntlmssp,multiuser 0 0
At this time, cancel the mount, and mount-a, found that the automatic mount, and is a multi-user authentication security mode of mount!
[root@client ~]# df Filesystem 1K-blocks Used Available Use% Mounted on /dev/vda1 10473900 3216932 7256968 31% / devtmpfs 469332 0 469332 0% /dev tmpfs 484920 80 484840 1% /dev/shm tmpfs 484920 12752 472168 3% /run tmpfs 484920 0 484920 0% /sys/fs/cgroup [root@client ~]# mount -a [root@client ~]# df Filesystem 1K-blocks Used Available Use% Mounted on /dev/vda1 10473900 3216932 7256968 31% / devtmpfs 469332 0 469332 0% /dev tmpfs 484920 80 484840 1% /dev/shm tmpfs 484920 12752 472168 3% /run tmpfs 484920 0 484920 0% /sys/fs/cgroup /dev/mapper/vg0-vo 483670 2371 451808 1% /home //172.25.254.125/mac 10473900 3161260 7312640 31% /mnt