What is Secret
The main function of Secret is to keep private data, such as password, OAuth token and ssh key.
Secret is subordinate to the Service Account resource object and a part of the Service Account. A Service Account object can include multiple different secret objects, which are used for authentication activities for different purposes.
Sensitive information in secret is more secure and flexible than in the definition of Pod or container image.
Type of Secret
1. Service Account: Kubernetes automatically creates a secret containing access API credentials and automatically modifies the pod to use this type of secret.
2. Opaque: base64 encoding is used to store information, and the original data can be obtained through base64 --decode decoding, so the security is weak.
3,kubernetes.io/dockerconfigjson: used to store the authentication information of docker registry.
Secret usage
Once a Secret is created, it can be used in the following three ways:
1. When creating a Pod, the Secret is automatically used by specifying a Service Account for the Pod.
2. Use the Secret by attaching it to the pod. It is mounted as a file in volume into one or more containers in the pod.
3. Used when kubelet pulls the image for Pod. Reference the Pod by specifying spc.ImagePullSecrets of the Pod.
Demo environment
server1: 172.25.38.1 harbor Warehouse end server2: 172.25.38.2 k8s master end server3: 172.25.38.3 k8s node end server4: 172.25.38.4 k8s node end
Service Account
When the serviceaccout is created, Kubernetes will create the corresponding secret by default. The corresponding secret will be automatically attached to / run / secrets / Kubernetes IO / serviceaccount directory.
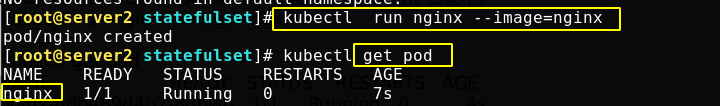
After entering the pod, you can see certificates, token s, etc
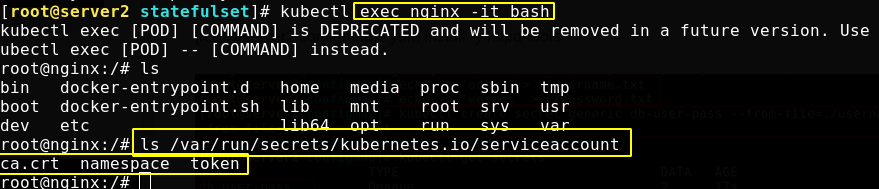
There is a default ServiceAccount object named default under each namespace
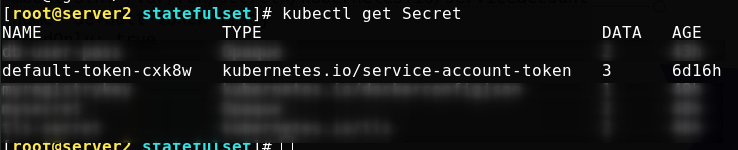
There is a Secret named Tokens in the ServiceAccount that can be mounted to the Pod as a Volume. When the Pod is started, this Secret will be automatically mounted to the specified directory of the Pod to assist in the authentication process when the process in the Pod accesses the API Server.
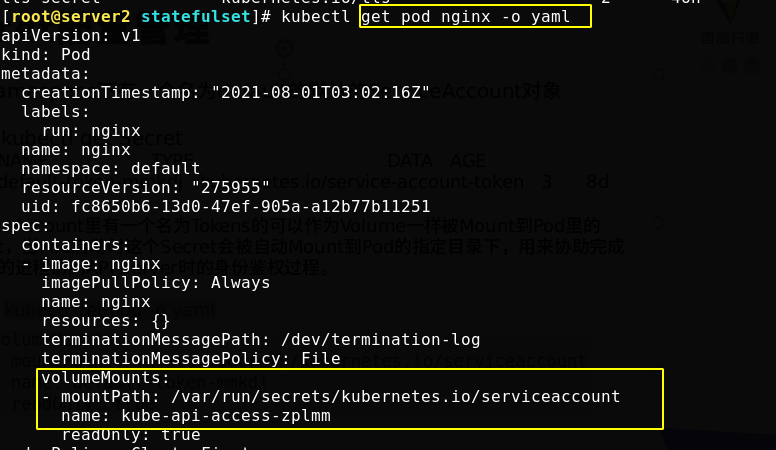
Create Secret from file
First write the user name and password file, and use the file to create a secret named DB user pass
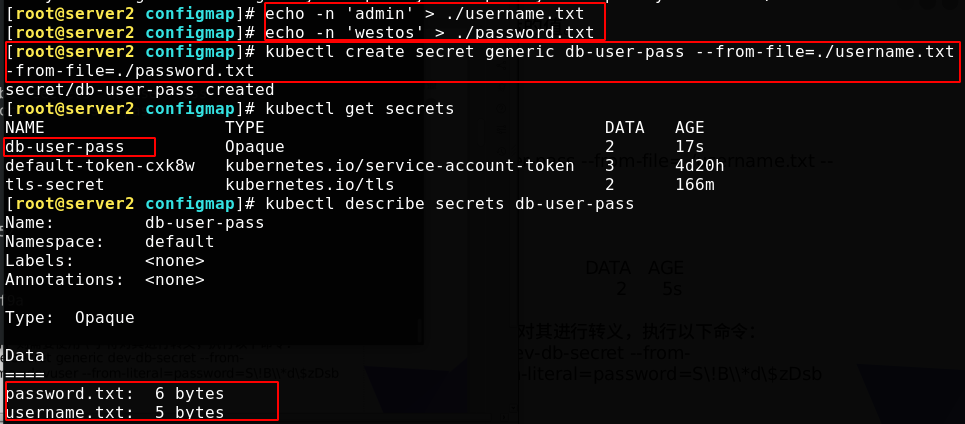
In yaml format, you can see the base64 bit encoded user name and password (by default, kubectl get and kubectl describe will not display the content of the password for security)
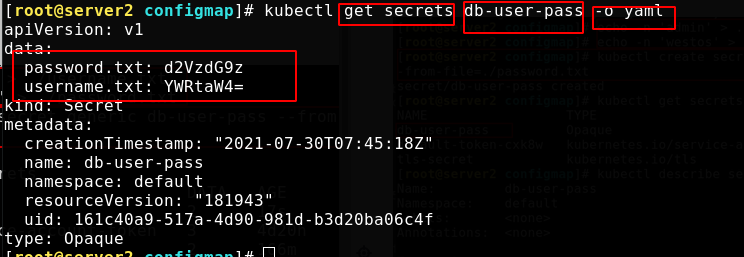
Write a secret object
The contents of the document are as follows:
apiVersion: v1 kind: Secret metadata: name: mysecret type: Opaque data: username: YWRtaW4= password: d2VzdG9z
Use the following command to encode the content you want to encode, and then write it to the file
[root@server2 configmap]# echo redhat | base64 cmVkaGF0Cg==
The following command can be used to decode
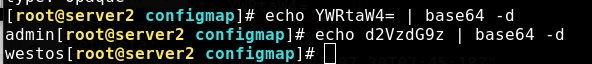
Create a secret and view it
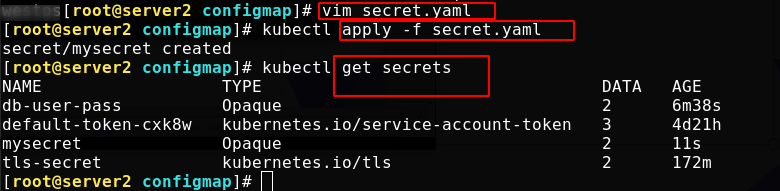
Directly view invisible content
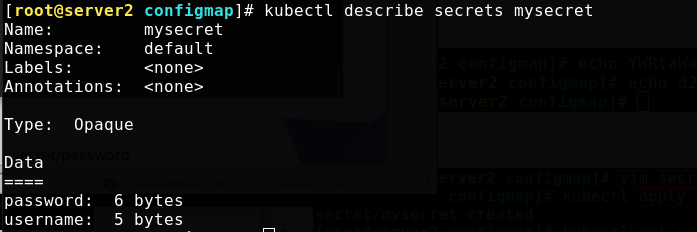
Mount Secret to Volume
On it, secret Add the content of creating pod to yaml file and mount secret to volume
apiVersion: v1
kind: Secret
metadata:
name: mysecret
type: Opaque
data:
username: YWRtaW4=
password: d2VzdG9z
---
apiVersion: v1
kind: Pod
metadata:
name: mysecret
spec:
containers:
- name: nginx
image: nginx
volumeMounts:
- name: secrets
mountPath: "/secret" #pod mount point
readOnly: true #read-only
volumes:
- name: secrets
secret:
secretName: mysecret #The secret that should populate this volume is mysecret
Run mysecret in the foreground, and enter the mount point to see the user name and password, indicating that the mount is successful
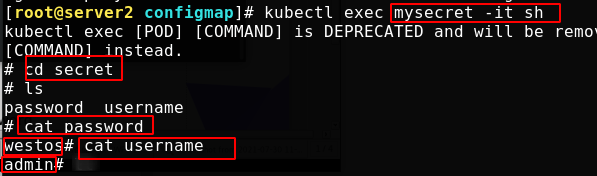
Maps a secret key to the specified path
The latest secret On the basis of yaml file, add the following contents at the end of specifying mysecret:
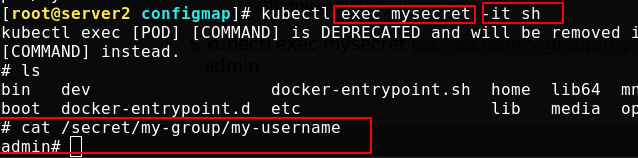
Specify only the mount user name
items:
- key: username
path: my-group/my-username
As shown below, Mount succeeded and view succeeded
Set Secret as the environment variable
Modify secret Yaml file, the modified content is as follows:
apiVersion: v1
kind: Secret
metadata:
name: mysecret
type: Opaque
data:
username: YWRtaW4=
password: d2VzdG9z
---
apiVersion: v1
kind: Pod
metadata:
name: secret-env #Created pod name
spec:
containers:
- name: nginx
image: nginx
env:
- name: SECRET_USERNAME
valueFrom:
secretKeyRef:
name: mysecret #Specify secert
key: username #Specify key
- name: SECRET_PASSWORD
valueFrom:
secretKeyRef:
name: mysecret
key: password
After the application is reused, tune in to the front desk to run pod and execute the env command to view the environment variables.
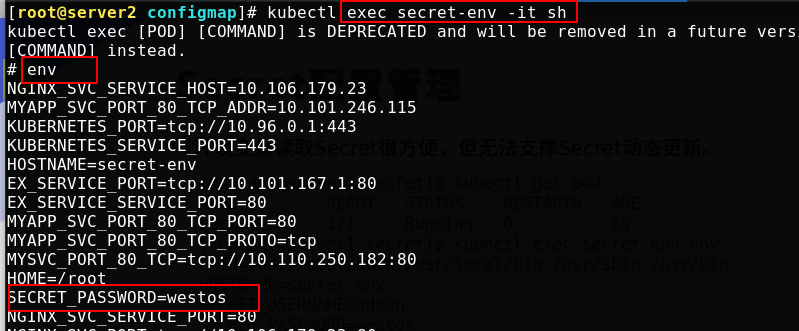
It is convenient for environment variables to read Secret, but it cannot support dynamic update of Secret.
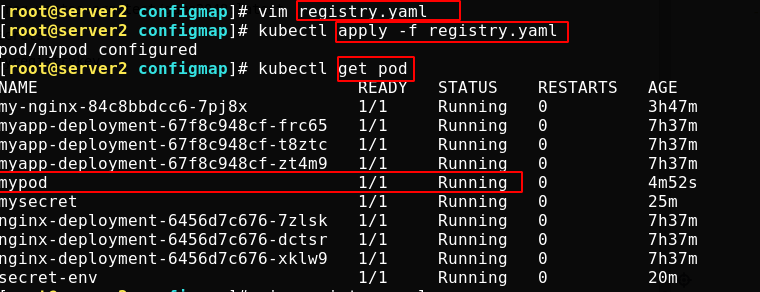
Create authentication information for registry
kubernetes.io/dockerconfigjson is used to store the authentication information of docker registry.
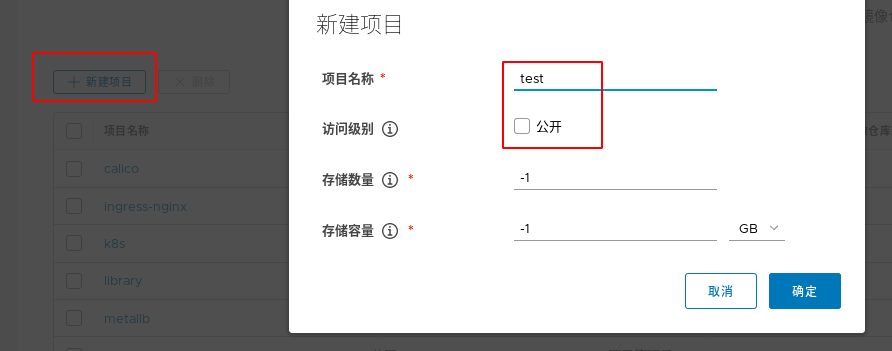
First create a non-public project in the warehouse. In this way, the image under the project cannot be pulled anonymously
Create a secret. The domain name, user name and password should be written in your own warehouse. Don't write it wrong
kubectl create secret docker-registry myregistrykey --docker-server=reg.westos.org --docker-username=admin --docker-password=westos --docker-email=yang@163.com
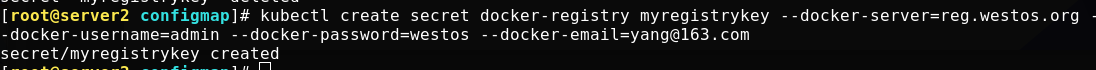
The secret that stores the authentication information of the docker registry is created
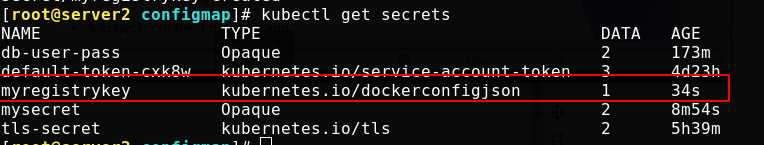
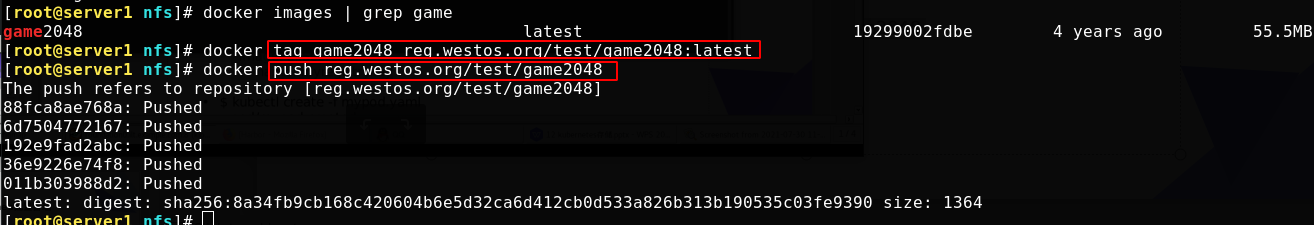
Upload an image to the undisclosed project in the server1 repository
Write a configuration file for creating a pod that completes authentication with secret
apiVersion: v1
kind: Pod
metadata:
name: mypod
spec:
containers:
- name: game2048
image: reg.westos.org/test/game2048:latest #The image address writes the image under the non-public project
imagePullSecrets:
- name: myregistrykey #The image file used to pull the image
When the application file creates a pod, you can see that there is no problem with the image pull, indicating that the authentication is successful!