1 ACL overview
- Definition: Access Control List access control list. Access Control List (ACL) is an access control technology based on packet filtering. It can filter the data packets on the interface according to the set conditions and allow them to pass or discard.
- Function: access control list is widely used in routers and layer 3 switches. With the help of access control list, users' access to the network can be effectively controlled, so as to ensure network security to the greatest extent.
- Is a list of instructions applied to the router interface. These instruction lists are used to tell the router which packets can be received and which packets need to be rejected.
- Check objects: layer 3 IP packet header (source address, destination address, etc.), layer 4 header (TCP, UDP port number), [layer 5 data].
- Application: router, layer-3 switch and firewall configuration (commonly referred to as policy). This section mainly introduces ACL S applied to routers and layer 3 switches.
2 ACL classification and principle
2.1 standard ACL
- Table number range: 1 ~ 99. As long as the table number is set within this range, it is a standard ACL table.
- Feature: the packet can only be filtered based on the "source IP" in the packet.
- Configuration location: on the router through which the traffic flows, since the standard ACL table can only check the source IP, it needs to be configured on the router close to the target as much as possible to avoid accidental killing.
- Whether it is applied to the inlet or outlet depends on the overall direction of flow control.
- Configure commands on which router to apply to:
'''Create standard ACL And new entries'''
en
conf t
access-list 1 #Create standard ACL Table 1
access-list 1 permit/deny source IP Or source segment anti subnet mask #Each command needs to indicate which table to target
#Inverse subnet mask: reverse the positive subnet mask by bit. For example, the positive subnet mask 255.255.255.0 corresponds to the inverse subnet mask 0.0.0.255
#The function of anti subnet mask: used for matching. The one corresponding to 0 needs to be strictly matched, and the one corresponding to 1 needs to be ignored.
access-list 1 deny 10.1.1.1 0.0.255.255 #Indicates that all source IP addresses are rejected. It is 10.1 x. X packets
access-list 1 deny 10.1.0.0 0.0.255.255 #The meaning is the same as the previous line, which is more convenient to understand
access-list 1 deny 10.1.1.1 255.255.255.255 #Indicates that all packets with source IP x.x.x.x are rejected
access-list 1 deny any #The meaning is the same as the previous line, which is more convenient to understand
access-list 1 deny host 10.1.1.1 #Indicates that the packet with source IP address 10.1.1.1 is rejected
access-list 1 permit any #Indicates that all packets are allowed to pass
'''View table'''
en
show ip access-list 1 #View Table 1. If no table number is specified, view all ACL tables.
'''Delete table'''
en
conf t
no access-list 1 #To delete a table, you need to specify a table number.
'''Finished editing ACL After the table, you need to ACL Which interface and which reverse should the table be used for'''
en
conf t
int f0/0
ip access-group 1 in/out #Either in or out
exit
2.2 extending ACL
- Table number range: 100 ~ 199.
- Features: data packets can be filtered based on source IP, target IP, port number, protocol, etc.
- Configuration location: on the router through which the traffic flows, due to the rich conditions of extending the ACL table, it should be configured on the router close to the source as much as possible to reduce the burden on the router.
- Whether it is applied to the inlet or outlet depends on the overall direction of flow control.
- Configure commands on which router to apply to:
'''Create standard ACL And new entries'''
en
conf t
acc 100 #Create extended ACL Table 1
#Standard command, the action is executed only when all conditions are met.
#Write everything except the port number. eq means equal to.
#The protocol is generally written as tcp/udp/ip/icmp. When there is a write port number, the corresponding protocol TCP or UDP needs to be written. Note that tcp/udp/icmp needs to flow through ip.
acc Table No permit/deny Protocol source IP Or source segment anti subnet mask destination IP Or target network segment anti subnet mask [eq Port number]
# Indicates that host 10.1.1.1 is allowed to access TCP80 port of host 20.1.1.3
acc 100 permit tcp host 10.1.1.1 host 20.1.1.3 eq 80
# Indicates that the UDP53 port of host 10.1.1.1 is prohibited, and the host will not be able to request DNS resolution.
acc 100 deny udp host 10.1.1.1 any eq 53
#Indicates that the host 10.1.1.1 is prohibited from accessing the network segment 20.1.1.0
acc 100 deny ip host 10.1.1.1 20.1.1.0 0.0.0.255
#Indicates that the host 10.1.1.1 is prohibited from all packets flowing to the network segment 20.1.1.0 TCP service
acc 100 deny tcp host 10.1.1.1 20.1.1.0 0.0.0.255
#Indicates that host 10.1.1.1ping20 is prohibited 1.1.0 network segment
acc 100 deny icmp host 10.1.1.1 20.1.1.0 0.0.0.255
# Indicates that all are allowed to pass
acc 100 permit ip any any
'''View table'''
en
show ip access-list 1 #View Table 1. If no table number is specified, view all ACL tables.
'''Delete table'''
en
conf t
no access-list 1 #To delete a table, you need to specify a table number.
'''Finished editing ACL After the table, you need to ACL Which interface and which reverse should the table be used for'''
en
conf t
int f0/0
ip access-group 1 in/out #Either in or out
exit
2.3 principle
- in/out is for routers. There are two directions on each interface.
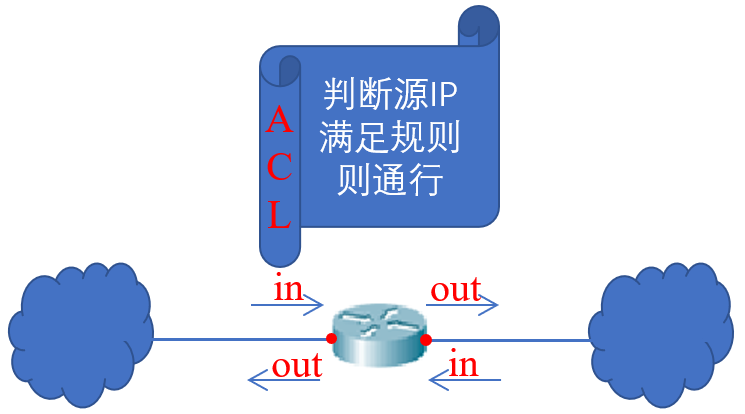
- The ACL table controls the entrance and exit of which exit is pasted. If it is pasted outside the door, it means that the rules are met to enter; If it is pasted in the door, it means that you can go out if you meet the rules.
- Only one ACL table is applied to one direction (in and out) of an interface.
- ACL tables are strictly checked from top to bottom, so the order of entries is very important.
- There are multiple entries from top to bottom in the ACL table, and each entry is composed of conditions and actions. Whenever there is traffic, check the items strictly from top to bottom one by one. When the conditions are fully met, execute the action; When the conditions are not fully met, check the next one; When all the conditions are not met, it is rejected, which is hidden at the end of the ACL table.
3 ACL editing
- ACL table editing and application should be considered after the whole network has been able to ping normally.
- ACL table is used to filter data packets. First, judge which router, interface and direction the application is in according to the flow of traffic.
- Consider which ACL table to use.
- At the beginning of writing, judge whether most traffic is rejected or allowed, and decide how to write the last row of the ACL table.
- It is recommended to write entries from bottom to top. The more up, the stricter the general conditions.
- In general, once the standard or extended ACL table is written, you cannot modify a certain entry, delete a certain entry, modify the order, or insert a certain entry. You can only add a new entry at the end. If you want to modify / delete / adjust the order, you can only delete the whole table and write it again.
4 naming ACL
- It perfects the functions of standard ACL and extended ACL, not the third kind of ACL table.
- Function: you can customize the naming of standard or extended ACL S.
- Advantages: (1) custom naming is easier to identify and remember. (2) You can modify / delete / insert a certain item at will.
- It can be understood that entries can only be modified / deleted / inserted after entering the ACL table configuration mode. In the global configuration mode, only the entire table can be deleted.
- Related commands:
en
conf t
acc 1 deny host 10.1.1.1 #Create standard ACL Table 1 and write rules
acc 1 permit any
acc 100 deny ip host 10.1.1.1 20.1.1.0 0.0.0.255 #Create extended ACL table 100 and write rules
acc 100 permit ip any any
#I hope people on the Intranet can access the website server, and people on the Internet can't access the website server
#Create a named ACL table, where ex represents extension and stan represents standard.
#This command will enter the extended ACL table configuration mode, without each sentence starting with access + table number
ip access-list extended/standard Custom table name
ip access-list ex kongzhi-80-oa
#Allow intranet 192.168 network segment to access tcp80 port of host 10.1.1.1.
permit tcp 192.168.0.0 0.0.255.255 host 10.1.1.1 eq 80
#Allow intranet 172.16 network segment to access tcp80 port of host 10.1.1.1.
permit tcp 172.16.0.0 0.0.255.255 host 10.1.1.1 eq 80
#Prohibit the intranet 192.168 network segment from accessing the ip protocol of host 10.1.1.1
deny ip 192.168.0.0 0.0.255.255 host 10.1.1.0
exit
#View all tables
do sh ip acc
#Enter the named ACL table again and adjust the entries
ip access-list ex kongzhi-80-oa
#Delete the entry with table number 20 in the table
no 20
#To insert an item, write the item serial number first
15 permit tcp 172.16.0.0 0.0.255.255 host 10.1.1.1 eq 80
#View all tables
do sh ip acc
#Modify the extended ACL by naming the ACL
ip access-list ex 100
5 Summary
- NTFS permission list is also an ACL table, and this section has nothing to do with it.
- Focus on understanding the role of anti subnet mask.
- Focus on understanding the execution law of ACL entries.
- Understand which router, interface and direction ACL should be configured in.
- Master relevant commands.
6 references
- <Encyclopedia of access control lists>
