- Background introduction
Single sign on (SSO) means that in a multi system environment, users do not have to log in to other systems after logging in to one system.
In the early days, our web systems were all single applications, and all functions were written into a war package. The user login authentication function is relatively simple to handle. After the user logs in successfully, the server writes the user information into the session. The session id will be generated to mark that this memory interval belongs to you, and this session id (jssessionid) will be written into your browser cookie. As long as your browser is not closed, every time you send a request to the server, the server will get this session id from the cookie you sent, Then, according to the session id, go to the corresponding memory to retrieve the data you previously stored. However, if you exit the login. The server will clear the memory area belonging to you and regenerate a new session when logging in again.
However, with the continuous expansion of application visits, single applications can not meet the application requirements, so distributed applications came into being. In the distributed application environment, when the access volume of a subsystem increases, we will deploy multiple copies of the system at the same time. When the same user logs in successfully, because the Nignx reverse proxy policy cannot be saved, the user can access the same subsystem, that is, the session with successful user login cannot be shared in multiple subsystems, which will lead to its login failure. Therefore, in distributed applications, we should solve the problem of session synchronization, which is the origin of single sign on.
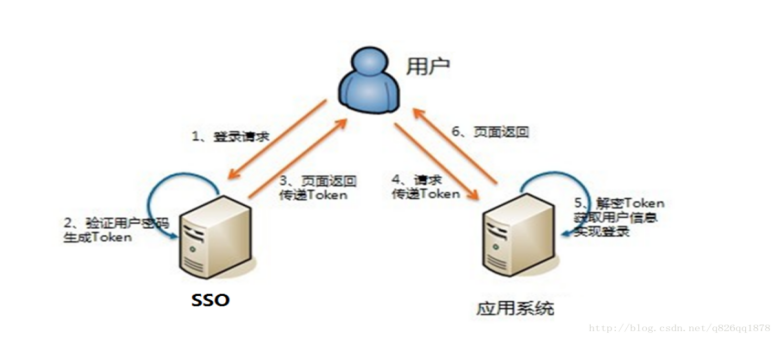
2. Solution: kisso based identity authentication scheme
kisso = cookie sso Cookie based SSO middleware, which is a Swiss Army knife for rapid development of java Web login system (SSO). In addition, kisso is a single sign on Middleware Based on JWT specification.
Open source address: https://gitee.com/baomidou/kisso.git
### Code example ###
SSOToken ssoToken = SSOToken.create();
ssoToken.setIp(request).setId("1001").setIssuer("admin");
int cookieMaxage = SSOConfig.getInstance().getCookieMaxage();
ssoToken.setTime(new Date().getTime()+cookieMaxage*1000);//Set expiration time
// Log in in cookie mode and write the encrypted token value
SSOHelper.setCookie(request, response, ssoToken, true);
// Generate jwt bill and set 'accessToken = bill content' in the access request header
String jwtToken = ssoToken.getToken();
// Analytical bill
SSOToken ssoToken = SSOToken.parser(jwtToken);
// Obtain login user id and login account
ssoToken = SSOHelper.getSSOToken(request);
String userId = ssoToken.getId();
String loginName = ssoToken.getIssuer();
// Log out (clear the token information corresponding to the cookie)
SSOHelper.logout(request, response);
// For multi terminal login and calling kick off, the SSOCache interface needs to be implemented
SSOHelper.kickLogin(userId);
// Permission interceptor class SSOSpringInterceptor
// Annotation does not intercept @ Login(action = Action.Skip)
// yml configure kisso config....
kisso:
config:
signkey: xxxx #Symmetric signature key (not required)
cookieName: accessToken #COOKIE key name
cookieDomain: www.domain.com # COOKIE domain name
3. Solution: SA token based single sign on + authority authentication framework
If your project belongs to the background management system or has permission authentication related requirements, recommend another open source project: SA token, which is a lightweight Java permission authentication framework;
Main solutions: login authentication, authority authentication, Session session, single sign on, oauth2 0 and a series of permission related problems.
Compared with the traditional old framework: Shiro and Spring Security need to customize the Realm, write global filters and write various configuration files during integration; The API design of SA token is super simple!
Open source address: https://gitee.com/dromara/sa-token.git Examples of core functions are as follows:
- Login authentication - easy login authentication, and provides five breakdown scenario values
- Permission verification - adapt to RBAC permission model, and different roles have different authorization
- Session - a professional data caching Center
- Kick people off the line - immediately remove the illegal users from the line
- Distributed session - provides two distributed session schemes: jwt integration and shared data center
- Microservice Gateway authentication - Request interception authentication adapted to common Gateway components such as Gateway, Soul and Zuul
- Single sign on - one sign on, everywhere
- Same end mutually exclusive login - like QQ, mobile phones and computers are online at the same time, but the two mobile phones are mutually exclusive login
### Code example ###
// Write the account id of the current session when logging in
StpUtil.setLoginId(10001);
// Then call the following API at any login that needs to be verified
// If the current session is not logged in, this code will throw an 'NotLoginException' exception
StpUtil.checkLogin();
// Permission authentication example (only sessions with user:add permission can enter the request)
@SaCheckPermission("user:add")
@RequestMapping("/user/insert")
public String insert(SysUser user) {
// ...
return "User increase";
}
// Log off the session with account id 10001
StpUtil.logoutByLoginId(10001);
StpUtil.setLoginId(10001); // Mark the account id of the current session login
StpUtil.getLoginId(); // Get the login account id of the current session
StpUtil.isLogin(); // Gets whether the current session has been logged in, and returns true or false
StpUtil.logout(); // Current session logout login
StpUtil.logoutByLoginId(10001); // Log out the session with account number 10001 (kick people off the line)
StpUtil.hasRole("super-admin"); // Query whether the current account contains the specified role ID
StpUtil.hasPermission("user:add"); // Query whether the current account contains the specified permission, and return true or false
StpUtil.getSession(); // Get the current Session id
StpUtil.getSessionByLoginId(10001); // Get the Session with account id 10001
StpUtil.getTokenValueByLoginId(10001); // Get the token token value with account id 10001
StpUtil.setLoginId(10001, "PC"); // Specify device ID login
StpUtil.logoutByLoginId(10001, "PC"); // Specify the device ID for forced logoff (different ends are not affected)
StpUtil.switchTo(10044); // Temporarily switch the current session identity to another account