Ctrip's automatic login is still a little troublesome. Let's look at the official website first:
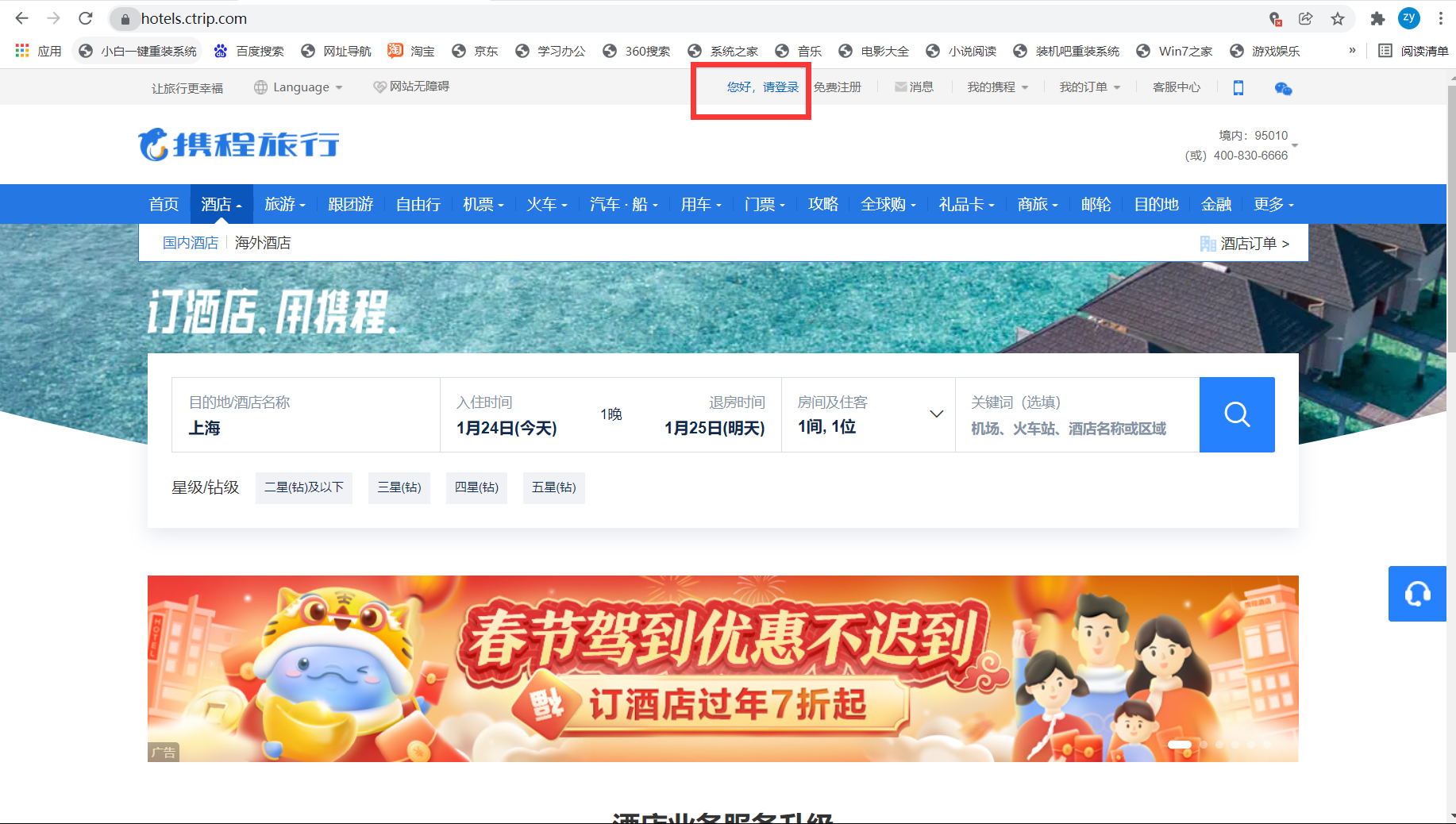
Needless to say, you must locate the label first, locate it in the red box, jump through click(), and come to the following page:
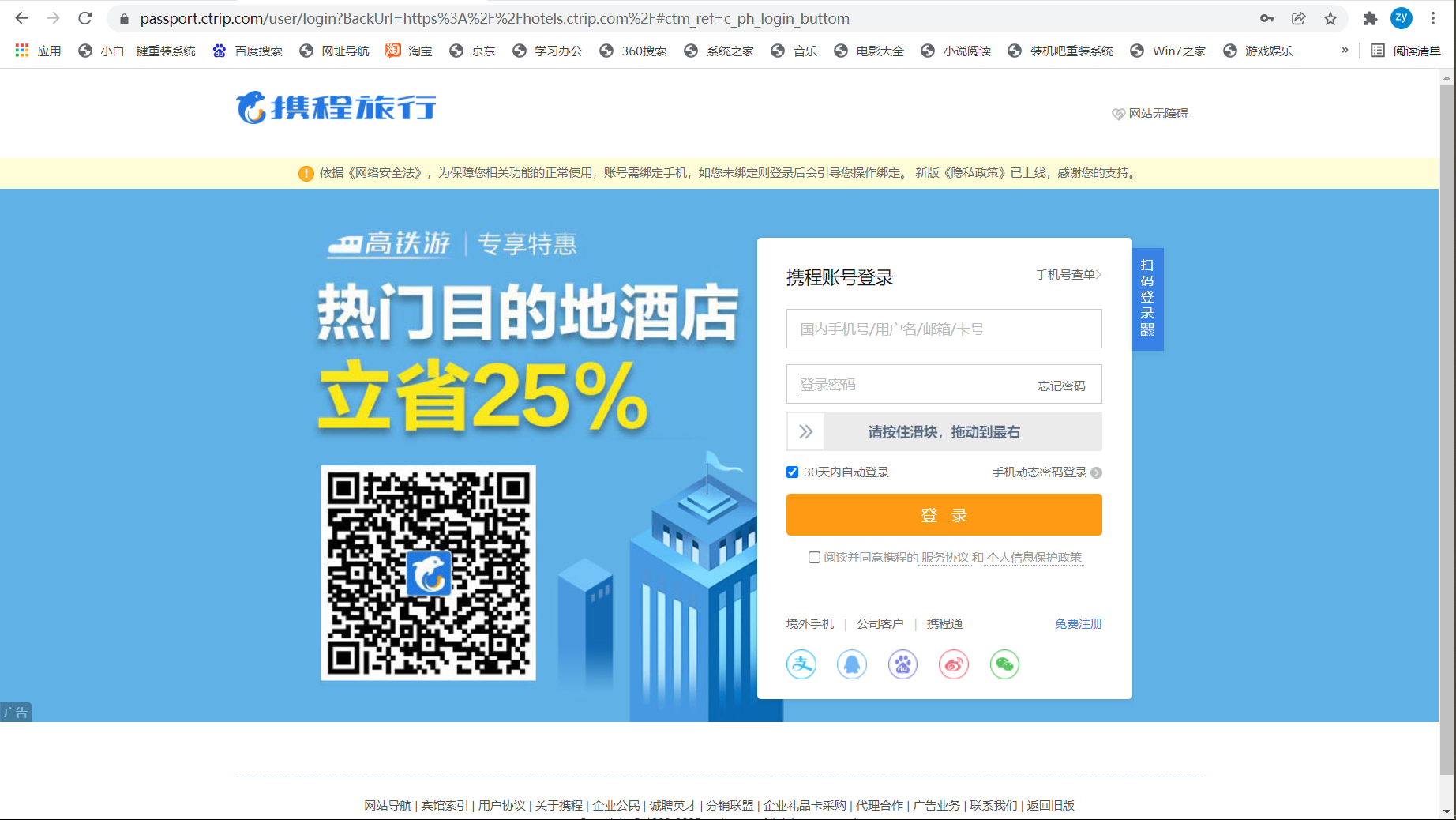
Here, first locate the tag to the place where you enter the user name and password, and then use send_keys() can enter the user name and password, which is very simple here. Then locate the slider, define an action chain, and click_and_hold() drag the slider to the far right. It's also simple here. I thought this simulated Login was successful, but the trouble came. It pops up another verification method!!!
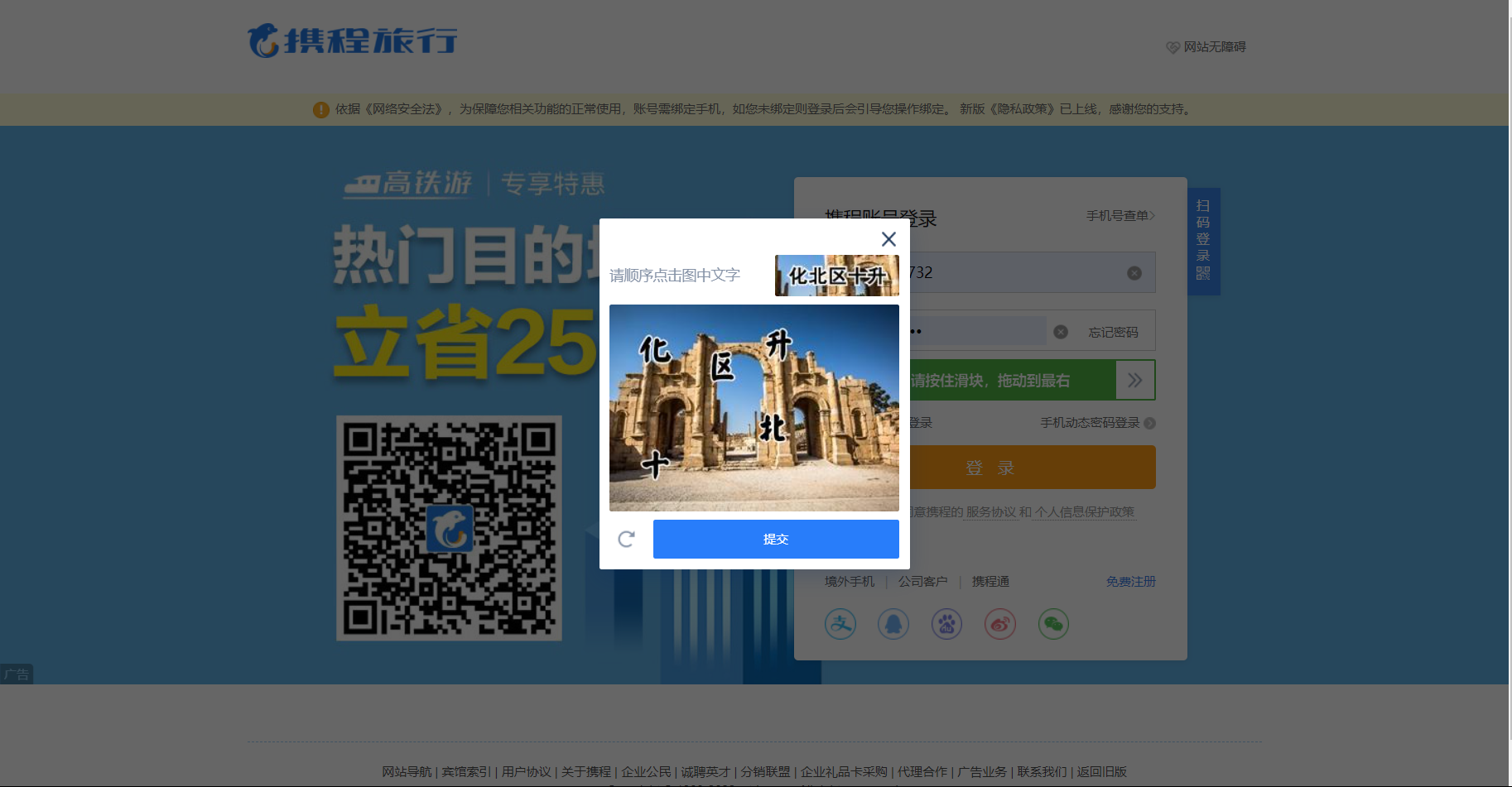
In fact, its appearance surprised me, but it's not difficult to say one thing. First take a screenshot of the current page, then locate the verification code area, obtain the location and size, then calculate the position in the lower right corner, and then use crop() to take a screenshot of the verification code area. Then put the screenshot into the super eagle for detection, and then store the coordinates of the verification code, Finally, use the action chain to click the position specified by X and Y corresponding to each list element, and finally click the submit button. The current verification is successfully completed.
Finally, check the agree agreement box, and the simulated Login will be successful, but the next problem comes:
First, post my previous code:
1 # -*- coding:utf-8 -*- 2 # @Time : 2022/1/24 0024 11:33 3 # @Author : Tzy0425 4 # @File : Simulated Login Ctrip Travel.py 5 6 from selenium import webdriver 7 from selenium.webdriver.chrome.service import Service 8 from selenium.webdriver.common.by import By 9 from selenium.webdriver import ActionChains 10 # Cutting a specific area requires leading the package in advance 11 from PIL import Image 12 from time import sleep 13 from selenium.webdriver import ChromeOptions 14 from hashlib import md5 15 import requests 16 17 #Implementation of circumvention detection 18 options = ChromeOptions() 19 options.add_experimental_option('excludeSwitches', ['enable-automation']) 20 21 # Super Eagle 22 class Chaojiying_Client(object): 23 24 def __init__(self, username, password, soft_id): 25 self.username = username 26 password = password.encode('utf8') 27 self.password = md5(password).hexdigest() 28 self.soft_id = soft_id 29 self.base_params = { 30 'user': self.username, 31 'pass2': self.password, 32 'softid': self.soft_id, 33 } 34 self.headers = { 35 'Connection': 'Keep-Alive', 36 'User-Agent': 'Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0)', 37 } 38 39 def PostPic(self, im, codetype): 40 """ 41 im: Picture byte 42 codetype: Topic type reference http://www.chaojiying.com/price.html 43 """ 44 params = { 45 'codetype': codetype, 46 } 47 params.update(self.base_params) 48 files = {'userfile': ('ccc.jpg', im)} 49 r = requests.post('http://upload.chaojiying.net/Upload/Processing.php', data=params, files=files, headers=self.headers) 50 return r.json() 51 52 def ReportError(self, im_id): 53 """ 54 im_id:Pictures of wrong topics ID 55 """ 56 params = { 57 'id': im_id, 58 } 59 params.update(self.base_params) 60 r = requests.post('http://upload.chaojiying.net/Upload/ReportError.php', data=params, headers=self.headers) 61 return r.json() 62 63 s = Service(r'./chromedriver.exe') 64 driver = webdriver.Chrome(service=s,options=options) 65 driver.get('https://www.ctrip.com/') 66 sleep(1) 67 68 login_href = driver.find_element(By.XPATH,'//*[@id="nav-bar-set-login-person-text"]/span') 69 login_href.click() 70 sleep(2) 71 72 userName_tag = driver.find_element(By.ID,'nloginname') 73 userName_tag.click() 74 userName_tag.send_keys('15110403732') 75 sleep(1) 76 77 passWord_tag = driver.find_element(By.ID,'npwd') 78 passWord_tag.click() 79 passWord_tag.send_keys('080015yuan...') 80 sleep(1) 81 82 slider_btn = driver.find_element(By.XPATH,'//*[@id="sliderddnormal"]/div[1]/div[2]') 83 action = ActionChains(driver) 84 action.click_and_hold(slider_btn) 85 action.move_by_offset(300,0).perform() 86 sleep(1) 87 88 refresh_btn = driver.find_element(By.XPATH,'//*[@id="sliderddnormal-choose"]/div[2]/div[4]/div/a') 89 refresh_btn.click() 90 91 # Take a screenshot of the current page and save it 92 driver.save_screenshot('whole.png') 93 94 # Coordinates of the upper left corner and lower right corner of the verification code picture (the clipping area is determined) 95 code_ele = driver.find_element(By.XPATH,'//*[@id="sliderddnormal-choose"]/div[2]') 96 97 # Get the coordinates of the upper left corner of the verification code picture x,y 98 location = code_ele.location 99 100 # Get the length and width of the verification code picture 101 size = code_ele.size 102 print('location',location) 103 # print('size',size) 104 105 # Calculate the coordinates of the lower right corner, and then determine the verification code area 106 rangle = ( 107 int(location['x']),int(location['y']), 108 int(location['x'] + size['width']),int(location['y'] + size['height']) 109 ) 110 111 # adopt crop()Crop the verification code area 112 i = Image.open('./whole.png') 113 code_img_name = './code.png' 114 frame = i.crop(rangle) 115 frame.save(code_img_name) 116 117 # Submit the verification code picture to super eagle for identification 118 chaojiying = Chaojiying_Client('yyy666', 'a123456789', '928028') # User name, password, software ID 119 im = open('./code.png', 'rb').read() # Local picture file path 120 print(chaojiying.PostPic(im, 9005)['pic_str']) 121 result = chaojiying.PostPic(im,9005)['pic_str'] 122 123 # Store the coordinates of the verification code to be clicked[[x1,y1],[x2,y2],[x3,y3]] 124 all_list = [] 125 if '|' in result: 126 list_1 = result.split('|') 127 for i in range(len(list_1)): 128 x = list_1[i].split(',')[0] 129 y = list_1[i].split(',')[1] 130 xy_list = [] 131 xy_list.append(x) 132 xy_list.append(y) 133 all_list.append(xy_list) 134 else: 135 x = int(result.split(',')[0]) 136 y = int(result.split(',')[1]) 137 xy_list = [] 138 xy_list.append(x) 139 xy_list.append(y) 140 all_list.append(xy_list) 141 print(all_list) 142 143 # Traverse the list, and use the action chain to check the corresponding of each list element x,y Click at the specified location 144 for l in all_list: 145 x = l[0] 146 y = l[1] 147 action = ActionChains(driver) 148 # move_to_element_with_offset()On the verification code area, according to x And y Perform offset positioning (the scope is first adjusted from the current page to the verification code area) 149 # move_by_offset()Directly perform offset positioning on the current page 150 action.move_to_element_with_offset(code_ele,x,y).click().perform() 151 sleep(0.5) 152 sleep(1) 153 154 submit_btn = driver.find_element(By.XPATH,'//*[@id="sliderddnormal-choose"]/div[2]/div[4]/a') 155 submit_btn.click() 156 sleep(1) 157 158 agree_checkbox = driver.find_element(By.XPATH,'//*[@id="normalview"]/p/input') 159 agree_checkbox.click() 160 sleep(1) 161 162 login_btn = driver.find_element(By.ID,'nsubmit') 163 login_btn.click() 164 sleep(1) 165 166 driver.quit()
In advance, I copied the xpath path of line 95 directly on the browser console:
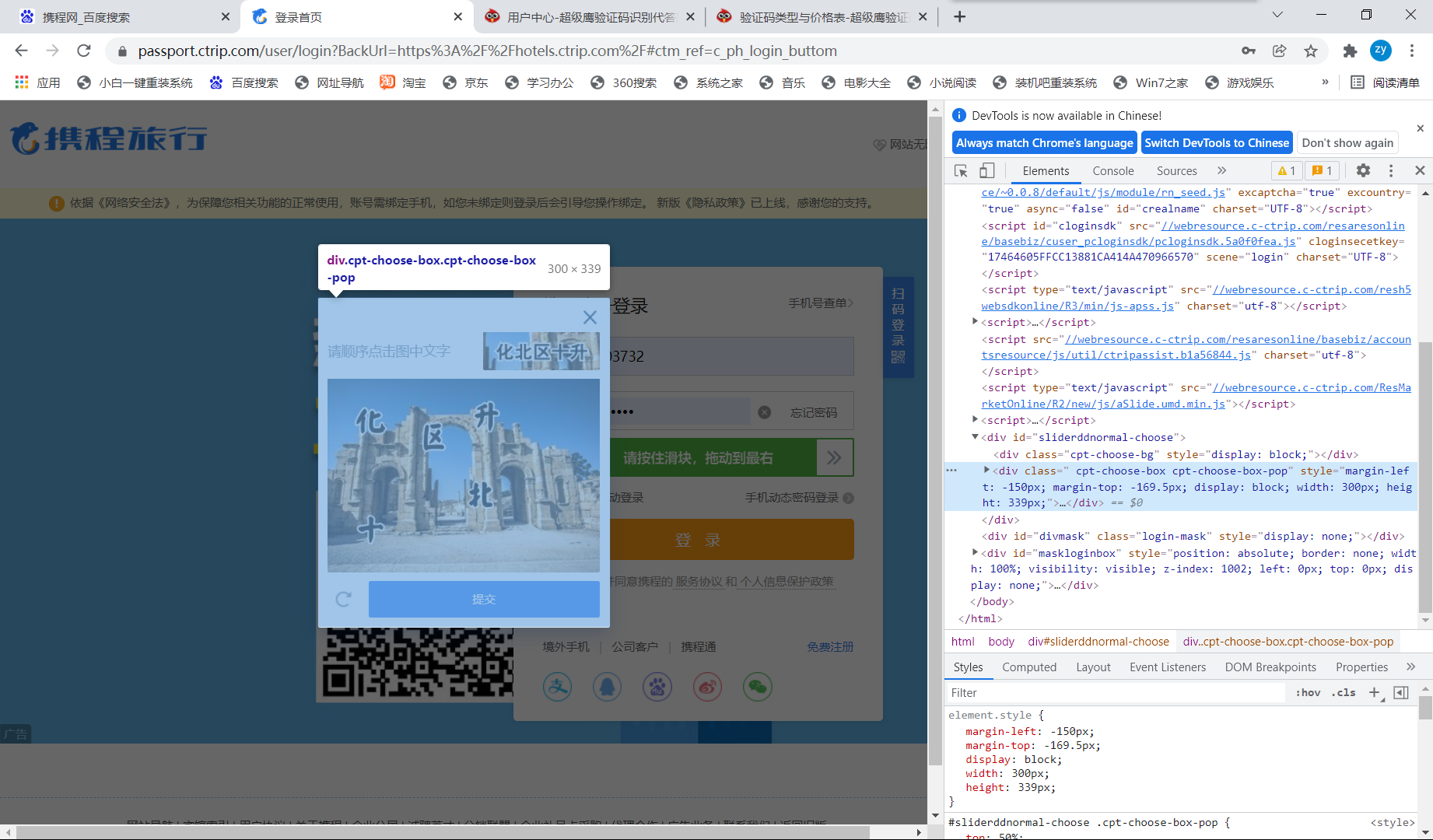
It is reasonable that the verification code area can be successfully intercepted after running, but I do (Figure 1 is a screenshot of the current page and Figure 2 is a screenshot of the verification code area):
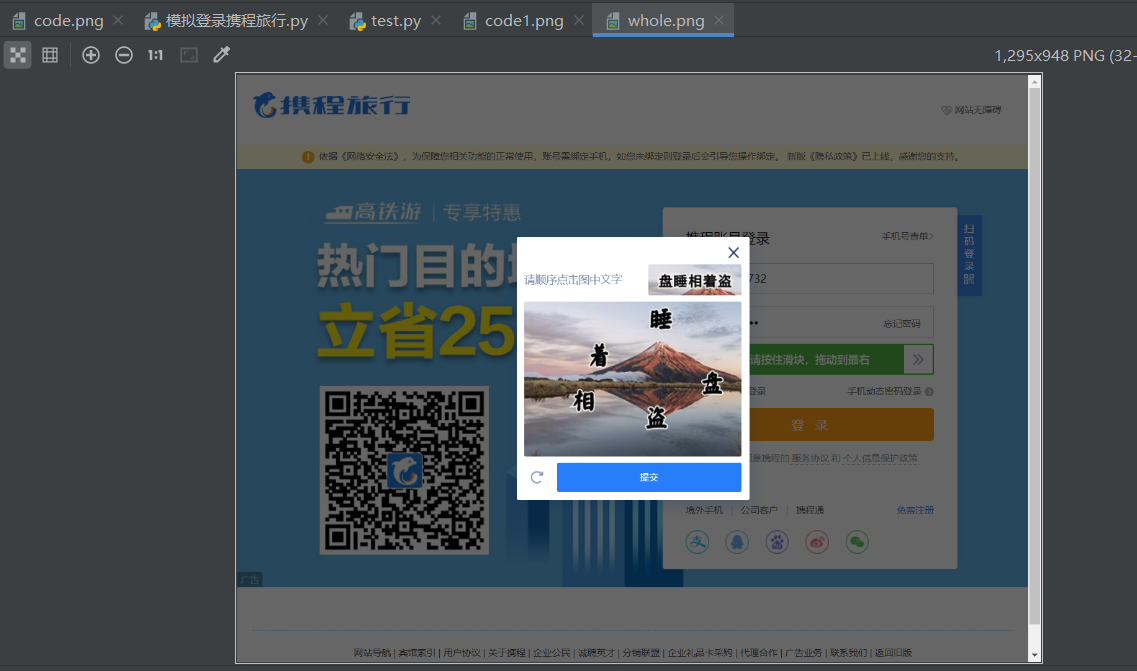
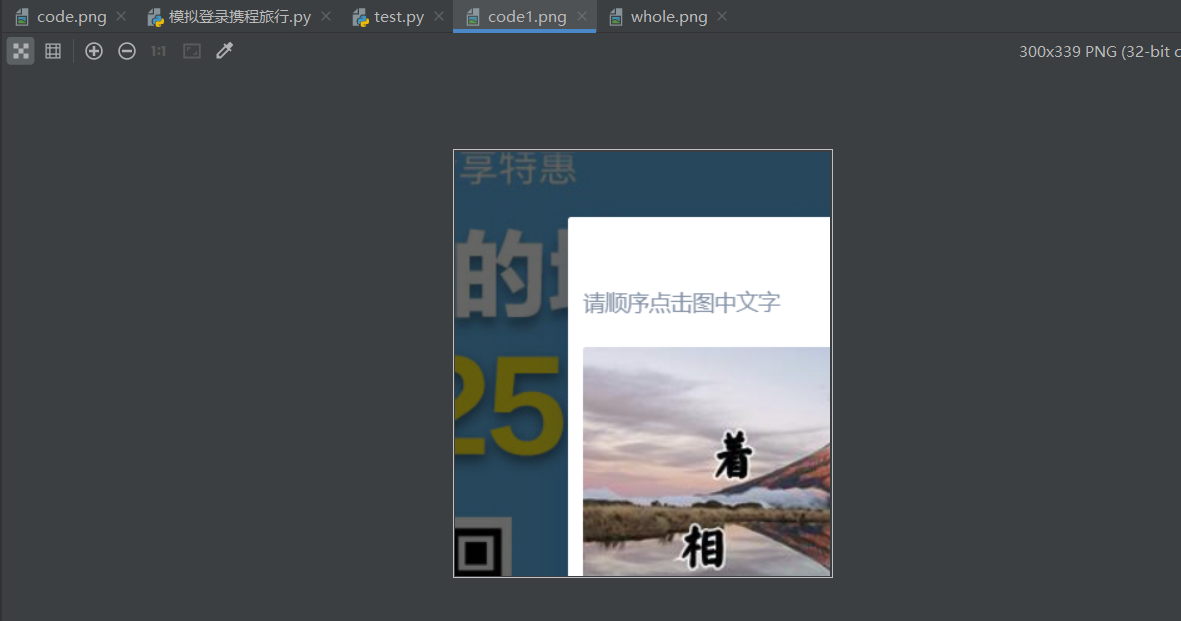
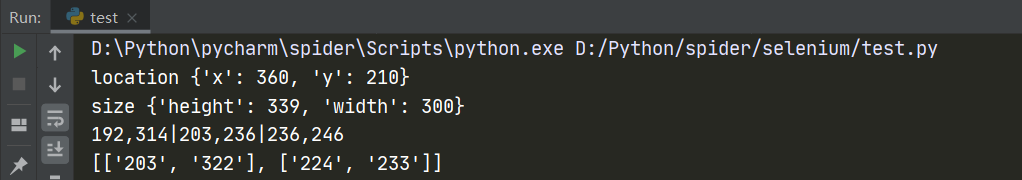
After testing again and again, I finally found that the location and size obtained through label positioning are not the coordinates of the upper left corner of the verification code area, nor the length and width of the verification code area. The reasons are as follows:
1 # Take a screenshot of the current page and save it 2 driver.save_screenshot('whole.png') 3 4 # Coordinates of the upper left corner and lower right corner of the verification code picture (the clipping area is determined) 5 # code_ele = driver.find_element(By.XPATH,'//*[@id="sliderddnormal-choose"]/div[2]') 6 7 # Get the coordinates of the upper left corner of the verification code picture x,y 8 # location = code_ele.location 9 location = {'x':448,'y':260} 10 11 # Get the length and width of the verification code picture 12 # size = code_ele.size 13 print('location',location) 14 # print('size',size) 15 16 # Calculate the coordinates of the lower right corner, and then determine the verification code area 17 rangle = ( 18 int(location['x']),int(location['y']), 19 int(location['x'] + 380),int(location['y'] + 405) 20 ) 21 22 # adopt crop()Crop the verification code area 23 i = Image.open('./whole.png') 24 code_img_name = './code.png' 25 frame = i.crop(rangle) 26 frame.save(code_img_name) 27 28 # Submit the verification code picture to super eagle for identification 29 chaojiying = Chaojiying_Client('yyy666', 'a123456789', '928028') # User name, password, software ID 30 im = open('./code.png', 'rb').read() # Local picture file path 31 print(chaojiying.PostPic(im, 9005)['pic_str']) 32 result = chaojiying.PostPic(im,9005)['pic_str'] 33 34 # Store the coordinates of the verification code to be clicked[[x1,y1],[x2,y2],[x3,y3]] 35 all_list = [] 36 if '|' in result: 37 list_1 = result.split('|') 38 for i in range(len(list_1)): 39 x = list_1[i].split(',')[0] 40 y = list_1[i].split(',')[1] 41 xy_list = [] 42 xy_list.append(x) 43 xy_list.append(y) 44 all_list.append(xy_list) 45 else: 46 x = int(result.split(',')[0]) 47 y = int(result.split(',')[1]) 48 xy_list = [] 49 xy_list.append(x) 50 xy_list.append(y) 51 all_list.append(xy_list) 52 print(all_list) 53 54 # Traverse the list and use the action chain to check the corresponding of each list element x,y Click at the specified location 55 for l in all_list: 56 x = l[0] 57 y = l[1] 58 action = ActionChains(driver) 59 # move_to_element_with_offset()On the verification code area, according to x And y Perform offset positioning (the scope is first adjusted from the current page to the verification code area) 60 # move_by_offset()Directly perform offset positioning on the current page 61 action.move_to_element_with_offset(code_ele,x,y).click().perform() 62 sleep(0.5) 63 sleep(1)
location and size successfully intercepted the verification code area through their own settings:
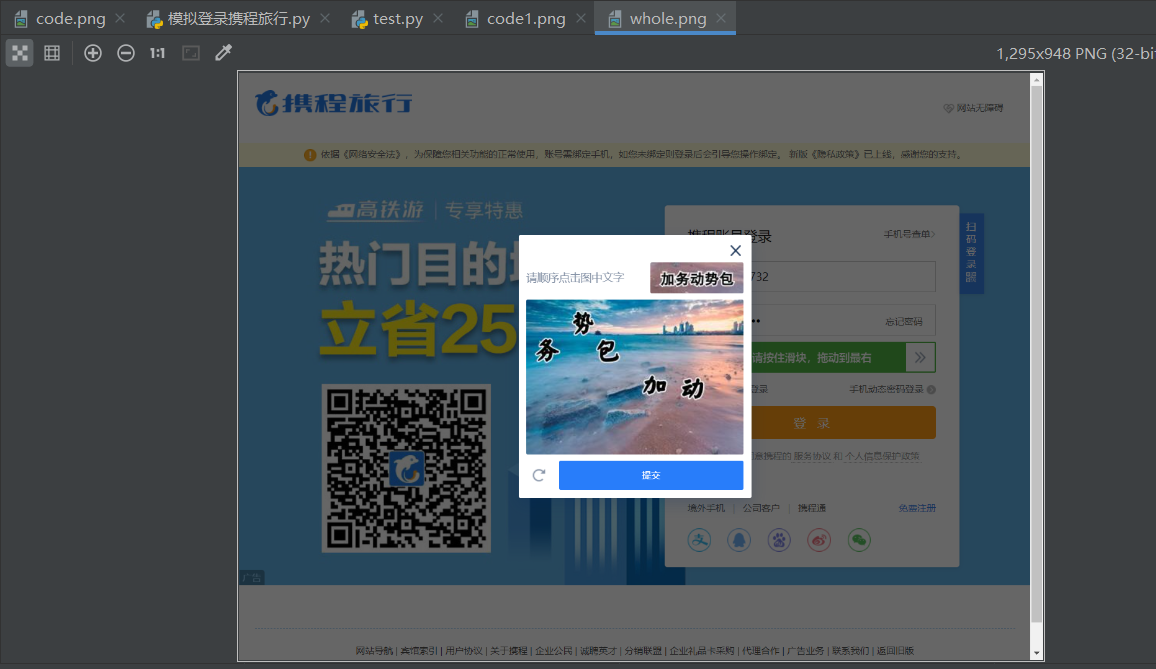
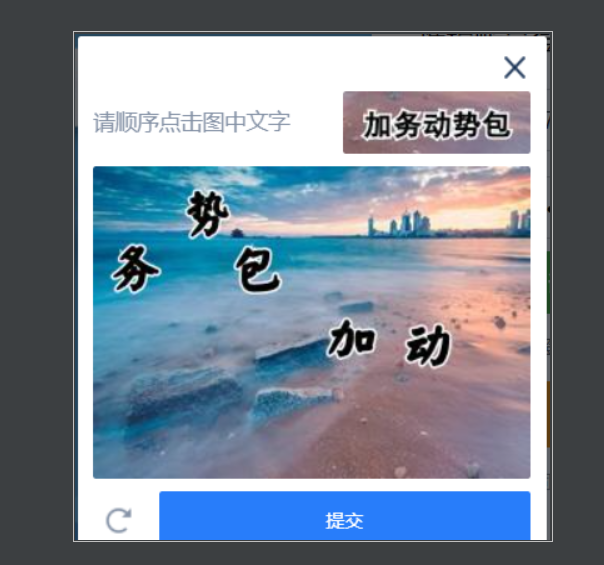
But then the question comes again, move_ to_ element_ with_ The first parameter of offset () needs to adjust the scope to the verification code area, but because my verification code area is written by myself and not obtained through label positioning, I can't pass the parameter here, so an error is reported again
Finally, I want to say that I know it's wrong to write location and size directly in the code. We should use the traditional label to locate and obtain location, but obviously in that case, the area of the verification code is not intercepted successfully. why???

If you see this blog, please give me some advice:
