1, Target
Android is getting less and less fun, young man. It's time to play IOS. In fact, the routines are almost the same. Don't be stopped by the Arm assembly.
Anyway, Android doesn't talk about martial arts for a long time. Important algorithms are in so, which is almost the same as ios.
First, build the package capturing and frida environment according to the previous [Ios reverse environment (I)].
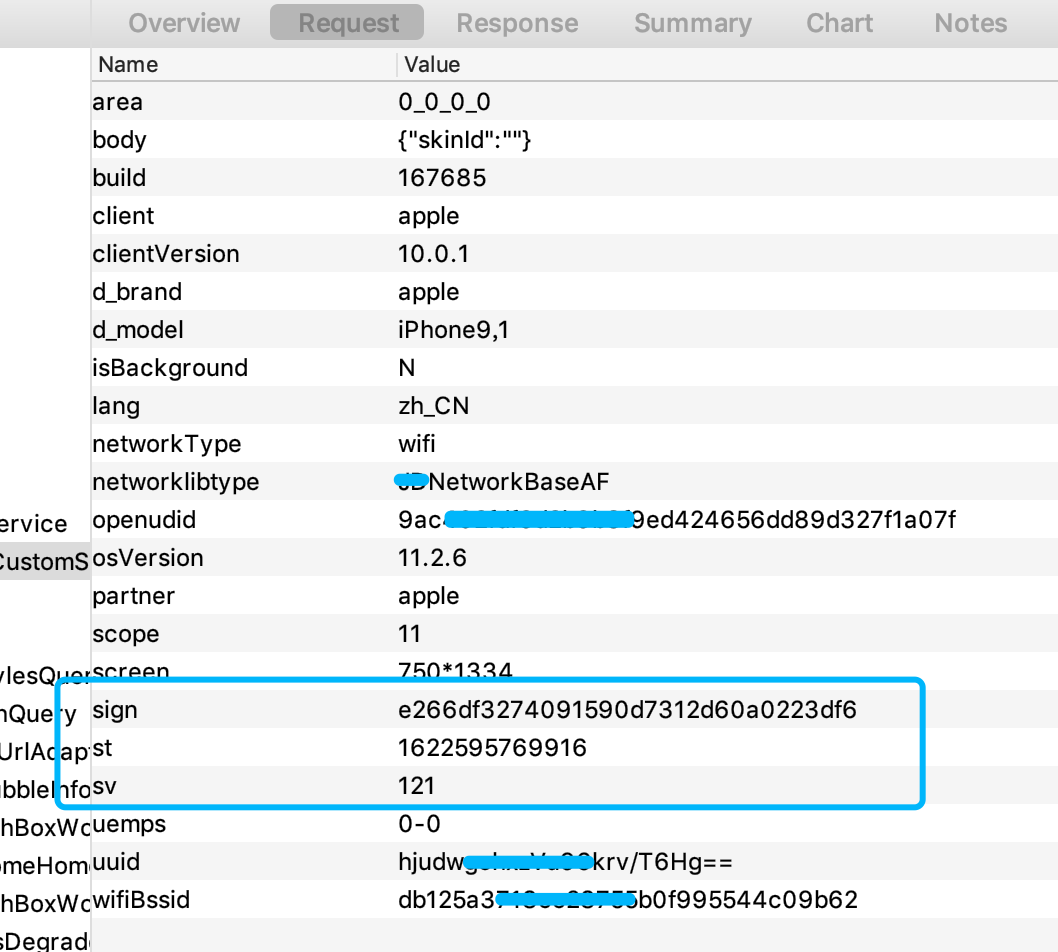
Our goal today is still it, sign
2, Steps
Watch
From the length and parameter type of sign, sign sv st can be seen that the probability of the signature algorithm of IOS version is about the same as that of Android. This can save us a lot of analysis time. Let's go directly to the topic.
The first step is to smash the shell
Under the Frida IOS dump directory, enter the command * * Python dump Py - L * * list the apps in the mobile phone and find the package name we want to do
Then start to run the shell smashing command, and the files after shell smashing will be copied to the computer through ssh.
python dump.py com.3xxbuy.xxmobile
TIP: Note: before smashing the shell, please ensure that SSH is connected. Use usbmuxd to forward the local port 2222 to port 22 on iOS, and configure SSH password free login
iproxy 2222 22 ssh -p 2222 root@127.0.0.1
Step 2 IDA
After smashing the shell successfully, the corresponding ipa file will be generated in the current directory. ipa is similar to apk and is also a compressed package. Let's decompress it first.
Find its executable file under Payload/xx4iPhone, which is more than 100 mb of xx4iphone. Drag it into IDA
IDA chews and swallows slowly for a long time (a long time means several hours...), you can pour a glass of water and have a rest. Brush small videos and fish with pay.
After IDA chews, Shift + F12, enter the string window, and we continue to find the string sign=
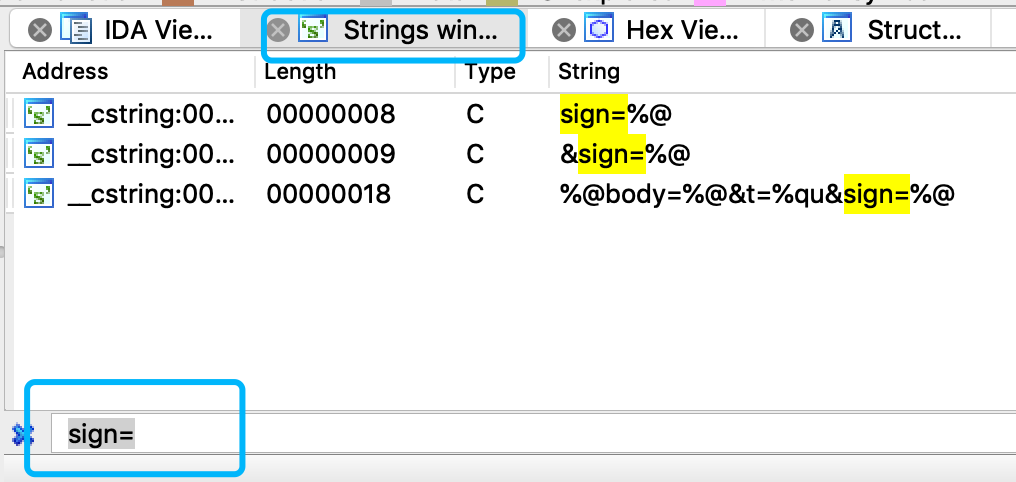
Double click a result, go in and press the X key (cross reference) above the variable name to see where to call the variable.
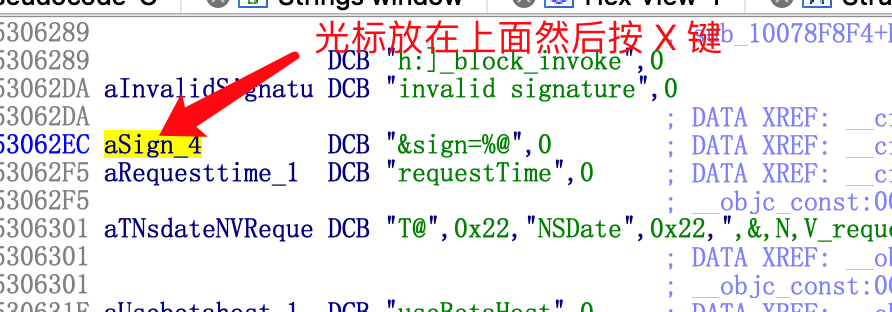
Come to cfstr_Sign_4. Continue X
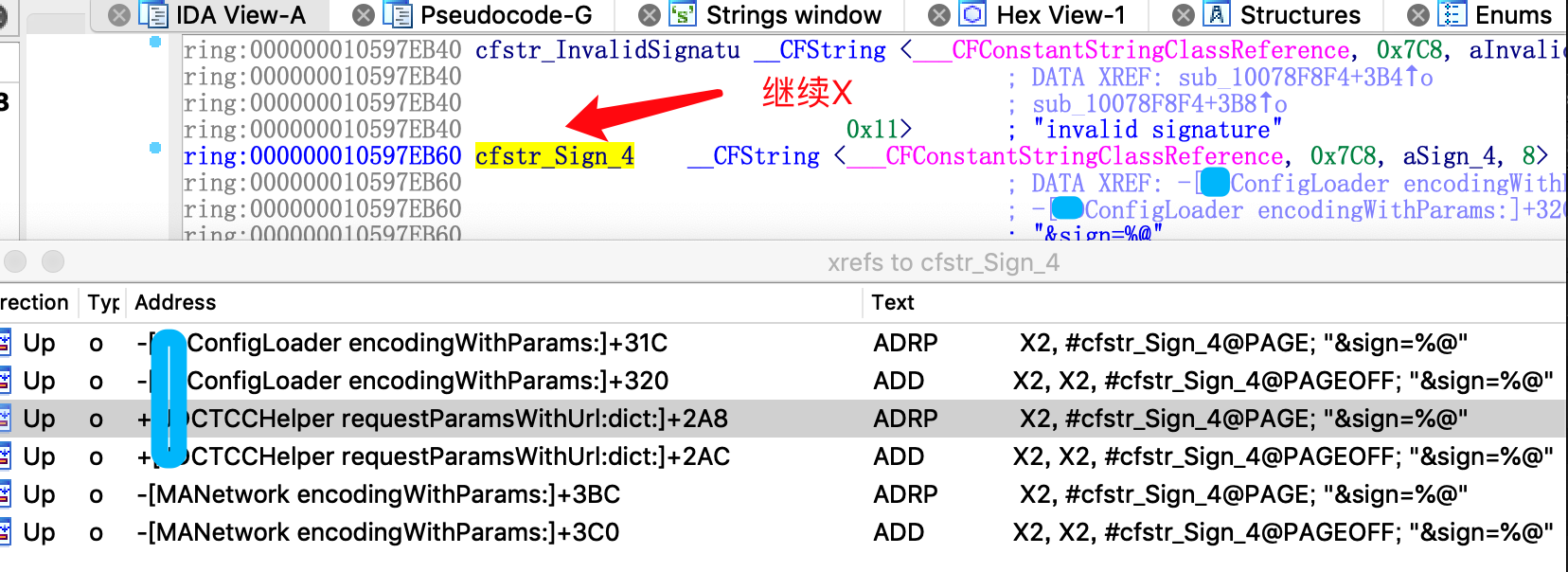
Look at this. It looks like JDCTCCHelper requestParamsWithUrl:dict:, go in and have a look and evoke the F5 method (press F5 after entering the Arm assembly code window, IDA will translate the pseudo code of C)
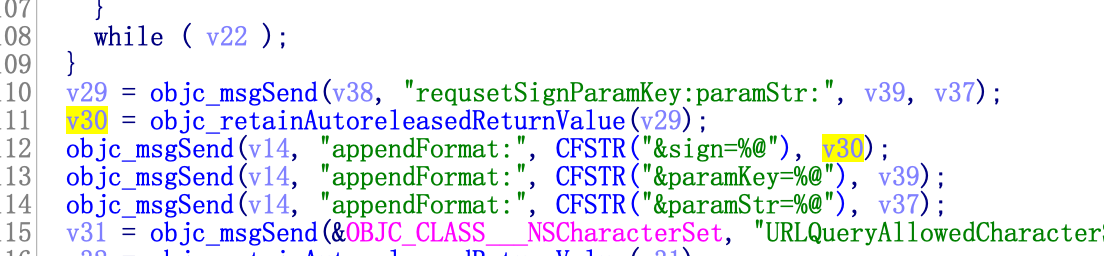
No, there's no calculation process. I've turned over all the results and haven't gained yet.
Try sv =, because sv is a rare field, and the probability with it is the sign calculation process.
It's another X, which is located to + [XXSignService getSignWithDic:keys:]
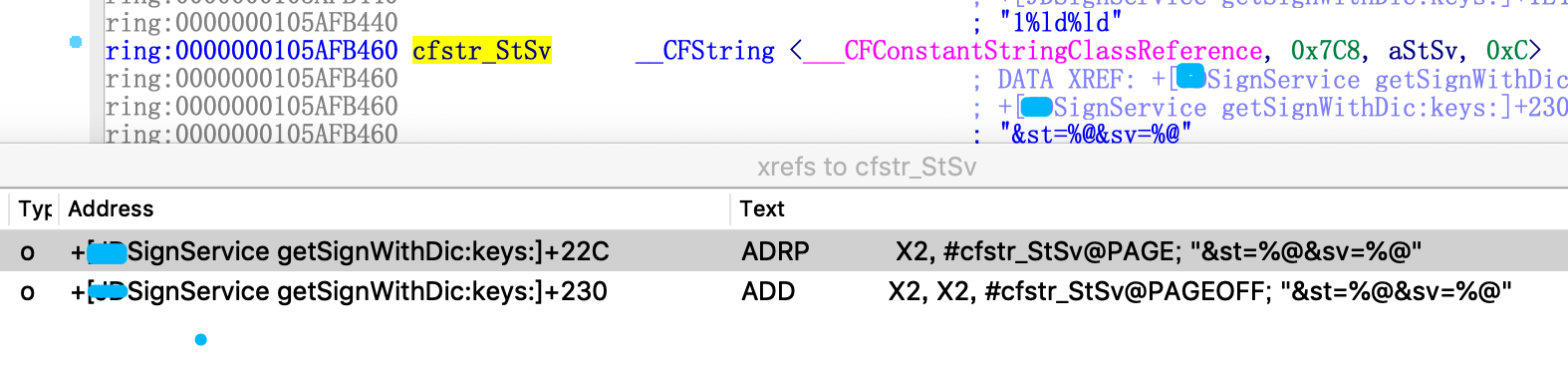
F5, take a closer look at this function. It looks like the calculation process of sign
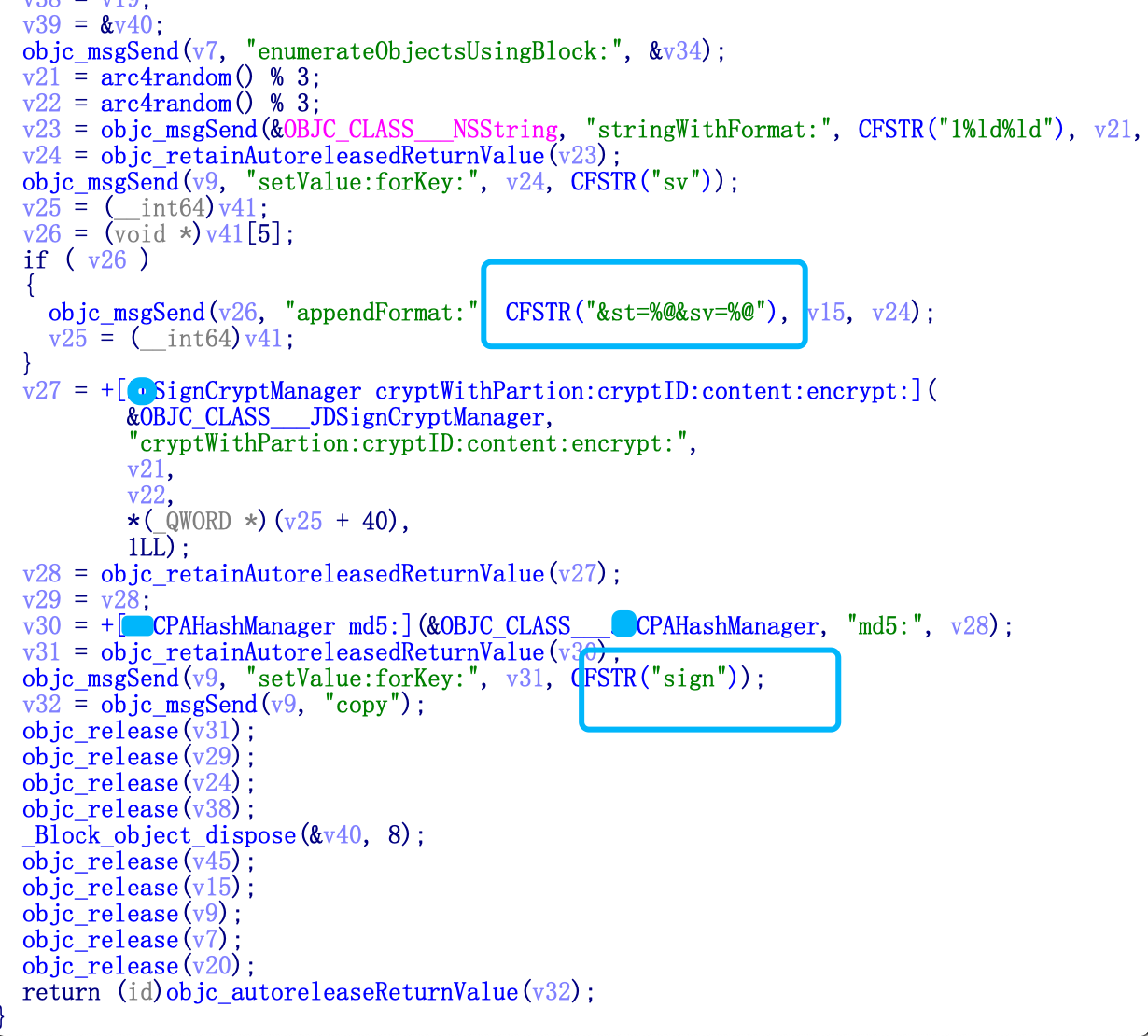
Step 3 Frida
Hang up our beloved Frida
id __cdecl +[XXSignService getSignWithDic:keys:](XXSignService_meta *self, SEL a2, id a3, id a4)
A typical ObjectC function is like this, + indicates that this is a class static function, and the first parameter points to the pointer of the object receiving the Objective-C message. The second parameter is a pointer to the selector or message passed to the object. We don't care about these two parameters for the time being. The third and fourth parameters are the real input parameters we should care about.
if (ObjC.available)
{
try
{
console.log('I am Comming in!');
var className = "XXSignService";
var funcName = "+ getSignWithDic:keys:";
var hook = eval('ObjC.classes.' + className + '["' + funcName + '"]');
console.log("[*] Class Name: " + className);
console.log("[*] Method Name: " + funcName);
console.log(hook);
// /*
Interceptor.attach(hook.implementation, {
onEnter: function(args) {
var receiver = new ObjC.Object(args[0]);
console.log("Target class : " + receiver);
var message1 = ObjC.Object(args[2]);
var message2 = ObjC.Object(args[3]);
console.log('msg1=' + message1.toString());
console.log('msg2=' + message2.toString());
},
onLeave: function(retval) {
var message = ObjC.Object(retval);
console.log('getSignWithDic rc is:' + message.toString());
}
});
// */
}
catch(err)
{
console.log("[!] Exception2: " + err.message);
}
}
We print out both input and participation results
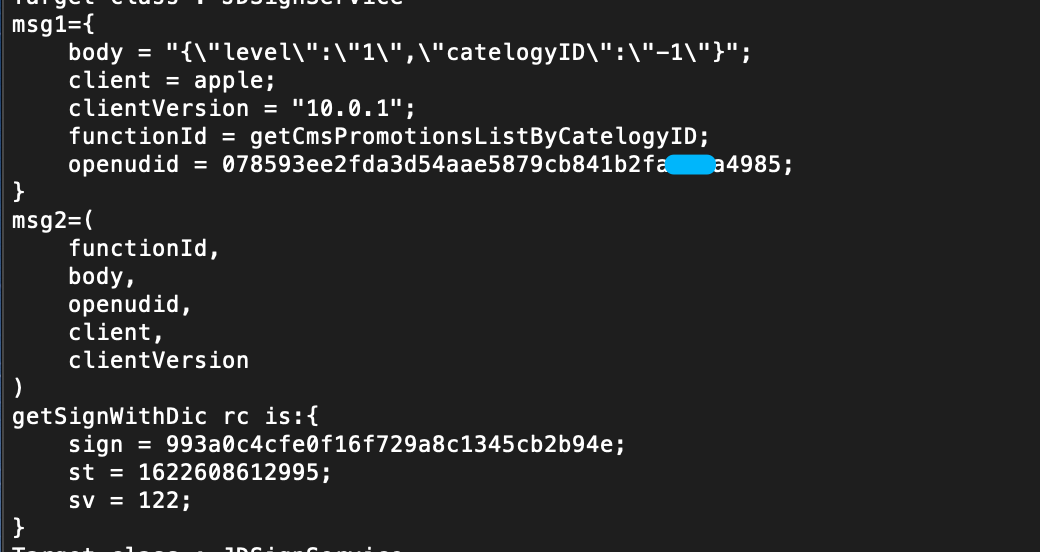
No problem, it's the result we want. Next time, let's talk about how to call RPC.
3, Summary
The executable file is 100MB, and IDA is really slow.
IOS plays like Android. Locate the feature string and hang Frida.
F5 is good.

You must learn routines, so as to effectively shorten the learning time; But when you learn the routine and start using it, you must find a different way to use it, so that you can wave your wings and fly into the air from a pile of chickens that can't fly, and become a flying eagle.