Abstract: original source: www.bysocket.com Com Mason BYSocket hopes to reprint and keep the summary, thank you!
Follow< Graphical Http protocol >And< Graphic Cookie >After that, everyone guessed to write Session. This series is mainly based on pictures, trying to be simple and easy to understand~
1, Session origin
HTTP stateless, that is, each request is an independent thread. For example: in shopping, you select item a and add it to the shopping cart. This is thread a. Then select the B product, which is the B thread. However, each time the thread is independent (for the container, a and B become different users), thread a does not know that there is B, and B does not know A. how to pay together?
Simply put: how to save the session state of multiple requests from the same user? HTTPS ensures that the connection is secure and can be associated with a session.
The problem is how to track the same user. There are many choices:
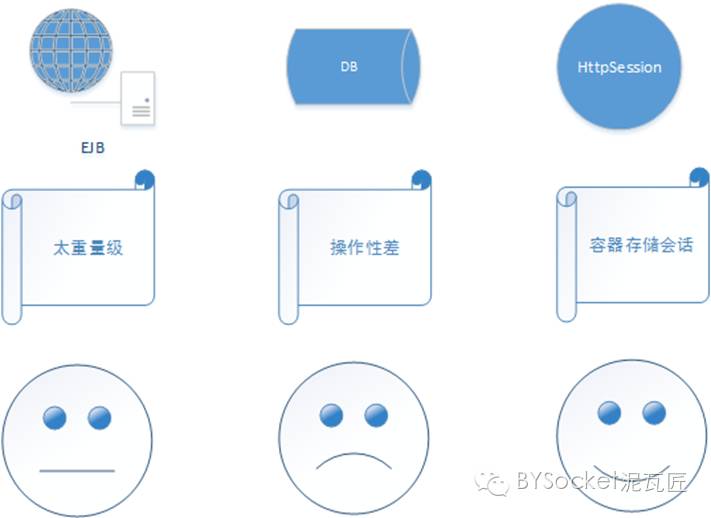
1. EJB (stateful session bean to save session state) environment is harsh, and J2EE server with EJB is required instead of Web container such as Tomcat. 2. Database (this seems omnipotent. For data) 3. This is the HttpSeesion we want to talk about, which saves the session state of multiple requests across a specific user. 4. The HTTPS mentioned above is too harsh.
As shown in the figure:
2, Session mechanism
Mechanism, What words are a little tall. In fact, it is to say something inside it. Two main W: What? How?
What is Session?
Session represents the process of a session between the server and the client. Until the session fails (the server is closed) or the client is closed.
How does session works?
Session is stored on the server side, and different users are distinguished by the SessionID for each client (client). Session is implemented by Cookie technology or URL rewriting. By default, it is implemented by Cookie technology, and the server will create a Cookie value of JSESSIONID for this session.
Supplement:
In fact, there is another technology: Form hiding fields. It can also implement the Session mechanism. This is just a supplement. Before the server responds, it will modify the Form and add a hidden field similar to SessionID, so that this Session can be marked when it is returned to the server. This technology, which can also be used in Web security, can effectively control CRSF cross site request forgery.
3, The process of Seesion mechanism is introduced in detail
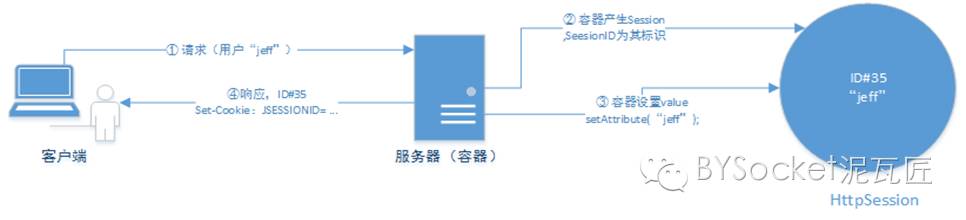
This is the detailed diagram of the first Session request. Implemented with Cookie technology, I also wrote an httpsessionbycookie Servlet t Java Servlet demo, simulating Seesion's life. The code is as follows:
package org.servlet.sessionMngmt;
import java.io.IOException;
import java.io.PrintWriter;
import javax.servlet.ServletException;
import javax.servlet.annotation.WebServlet;
import javax.servlet.http.HttpServlet;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import javax.servlet.http.HttpSession;
/*
* Copyright [2015] [Jeff Lee]
*
* Licensed under the Apache License, Version 2.0 (the "License");
* you may not use this file except in compliance with the License.
* You may obtain a copy of the License at
*
* http://www.apache.org/licenses/LICENSE-2.0
*
* Unless required by applicable law or agreed to in writing, software
* distributed under the License is distributed on an "AS IS" BASIS,
* WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
* See the License for the specific language governing permissions and
* limitations under the License.
*/
/**
* @author Jeff Lee
* @since 2015-7-12 10:58:28
* HttpSession Default Cookie implementation case for
*/
@WebServlet(urlPatterns = "/sessionByCookie")
public class HttpSessionByCookieServletT extends HttpServlet {
private static final long serialVersionUID = 1L;
@Override
protected void doGet(HttpServletRequest req, HttpServletResponse resp)
throws ServletException, IOException {
// Get session
// If it is the first request, an HttpSeesion will be created, which is equivalent to req getSession(true);
// If a session already exists, the session is obtained.
HttpSession session = req.getSession();
if (session.isNew()) {
// Set the session property value
session.setAttribute("name", "Jeff");
}
// Get SessionId
String sessionId = session.getId();
PrintWriter out = resp.getWriter();
// If HttpSeesion is new
if (session.isNew()) {
out.println("Hello,HttpSession! <br>The first response - SeesionId="
+ sessionId + " <br>");
} else {
out.println("Hello,HttpSession! <br>The second response - SeesionId="
+ sessionId + " <br>");
// Get property value from Session
out.println("The second-response - name: "
+ session.getAttribute("name"));
}
}
}The code is on GitHub: https://github.com/JeffLi1993
① The client sends the first request to the server
At this time, the client wants the server to set its name to the session.
② The server container generates the Session object with the unique SessionID of the user and sets the value
As you can see from the code, req Getsession(), a new Session object is generated. setAttribute("name", "Jeff") is set, key is string, and value is object.
At this time, we don't need to process the session through cookie technology. The container helps us.
③ Container response set Cookie: JSESSIONID =
We can use F12 to view this response.

As can be seen from the figure, the set of each Cookie has a corresponding set Cookie header. HttpOnly is read-only mode for this Cookie. Only the Session ID is JSESSIONID
④ The browser parses the Cookie and saves it to the browser file.
As shown in the figure, the corresponding Session stored Cookie file is found. The file is protected and cannot be opened. Graphic cookies teach you how to find the file.
What will happen to the second request?
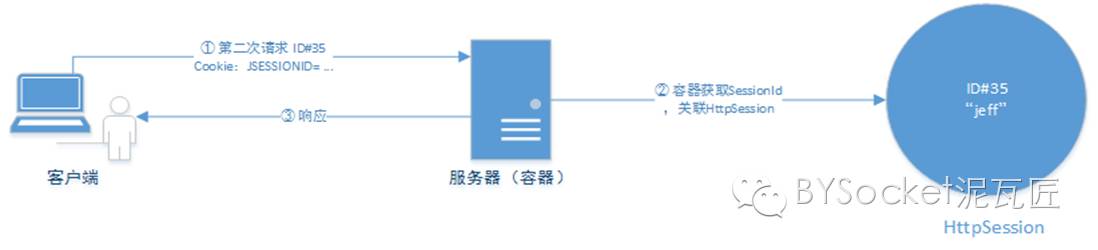
Next, the Mason revisited this address:
① Request again
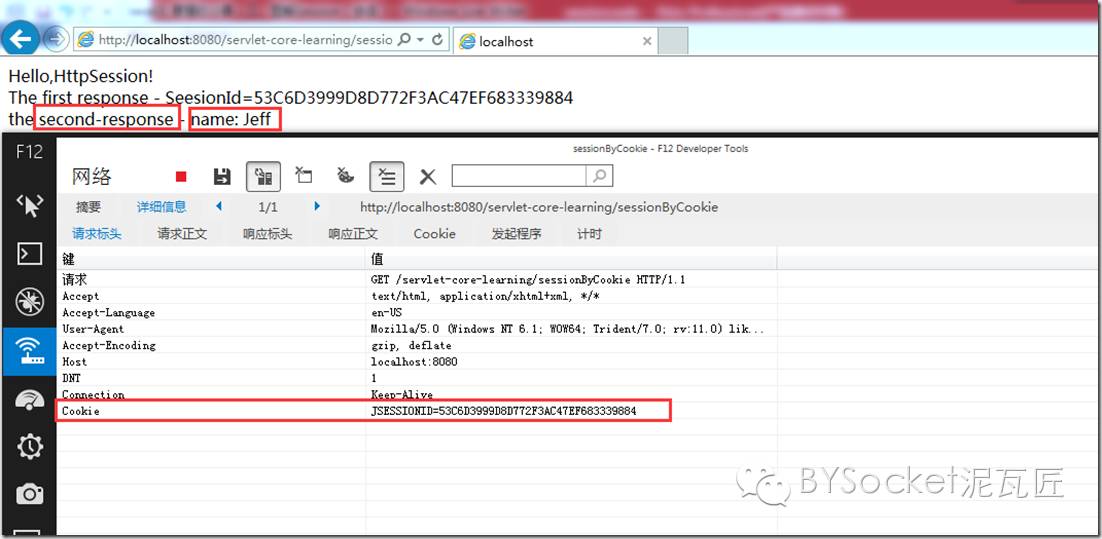
At this time, the request will have a Cookie value: JSESSIONID =... Which is passed to the server
② The container obtains the SessionId and associates HttpSession
③ There is no SetCookie in the response at this time
As shown in the figure:
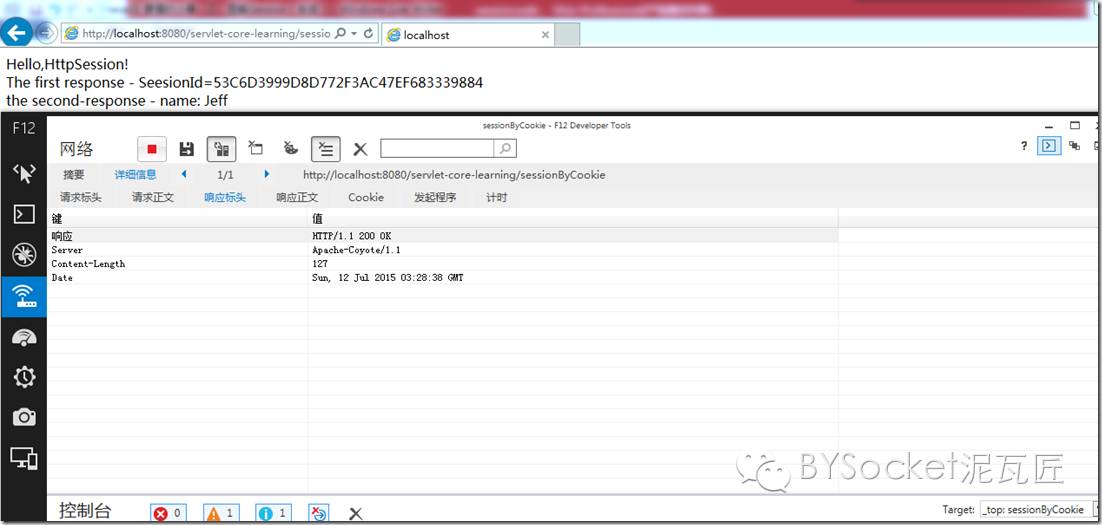
But this time, we respond to the value of the last request set. Jeff printed it out!
For the server to obtain a session, that is, to obtain a session object from the request, the container will help you find a unique session object according to the Cookie.
Mason's memory sketch: Seesion mechanism, remember the request map twice.
4, Supplement
So far, ha ~ write it in detail later. This image is from the network
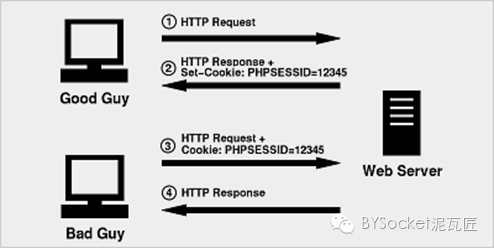
Bad guy, above, is the attacker. Cross Site Request Forgery, forgery of user requests to pose a threat to server data or users. web security is slowly improving from these foundations.
5, Summary
1. The working mechanism of session is roughly described, which is related to some security. Remember what Seesion is, how to use it, and how to transfer it between server and client. 2. Learning from the basics, I wish you all a happy double eleven.
If the above articles or links are helpful to you, don't forget to comment at the end of the article. You can also share and let more people read this article.