In some enterprises, some DNS requests will be directly modified by the gateway. Cause inaccessibility. The traditional socks proxy can only proxy at the IP level. When the address to be accessed exists in the form of domain name, the DNS resolution is automatically completed by the system, and the previously set socks proxy will not be used, resulting in the IP error, so the proxy used before can not be used at all.
Because security and encryption were not considered in the early DNS protocol design, the default UDP DNS requests were all transmitted in clear text, so they are very easy to be tampered with in the transmission process.
So we need a complete way to deal with this situation:
ISP will directly modify the data packets requested by UDP DNS, causing DNS pollution.
We can try DNS over HTTPS (DoH) and DNS over TLS (DoT).
DoH uses ordinary https requests, which is recommended. 443 port is used for communication.
DoT is likely to be blocked. Because it adopts 853 port, this uncommon port may be directly ban out in the network environment (common port: 80443; 8080). In my network environment, I just can't export port 853.
In the latest version of Windows 10, you can see the shadow of DoT, but you can't use DoH.
In the following scheme, I set up a local UDP DNS Server to parse UDP DNS messages, convert them into DoH request style, send HTTPS requests to DoH service providers through Socks proxy, and then convert them into UDP DNS message mode to return response after receiving the returned request. d
pip install encrypted-dns
For the first time, run the program directly to generate a default configuration file.
encrypted-dns
The generated configuration file is in "C:\Users\Administrator\.config\encrypted_dns\config.json"
The following style is my final configuration. It can be used after replacing the marked [] according to the requirements.
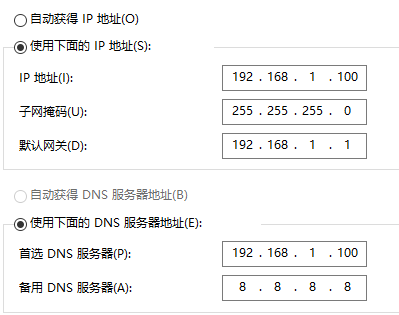
It is recommended to set a fixed ip address in the network and sharing center
In my network environment, https://8.8.8.8 All by ban. Therefore, agents should be used
{
"version": "1.2.0",
"ecs_ip_address": "128.97.0.0",
"dnssec": false,
"dns_cache": {
"enable": true,
"override_ttl": 3600
},
"firewall": {
"refuse_ANY": true,
"AAAA_disabled": false,
"rate_limit": 30,
"client_blacklist": [
"128.97.0.0"
]
},
"rules": {
"force_safe_search": false,
"hosts": {
"localhost": "127.0.0.1",
"cloudflare-dns.com": "1.0.0.1",
"dns.google": "8.8.8.8",
"dns2.google": "8.8.4.4"
}
},
"inbounds": [
"[Native IP Address, be careful not to use 127.0.0.1]:53",
"tcp://[the IP address of this machine should not be 127.0.0.1]: 5301“
],
"outbounds": [
{
"tag": "bootstrap",
"dns": [
"8.8.8.8"
],
"domains": [
"captive.apple.com",
"connectivitycheck.gstatic.com",
"detectportal.firefox.com",
"msftconnecttest.com",
"nmcheck.gnome.org",
"pool.ntp.org",
"time.apple.com",
"time.asia.apple.com",
"time.euro.apple.com",
"time.nist.gov",
"time.windows.com"
]
},
{
"tag": "unencrypted",
"dns": [
"udp://114.114.114.114",
"udp://114.114.115.115",
"udp://223.5.5.5"
],
"concurrent": false,
"domains": [
"sub:163.com",
"include:baidu.com"
]
},
{
"tag": "encrypted",
"dns": [
"https://dns.google",
"https://dns2.google"
],
"proxies": {
"http": "http://[proxy user name]: [proxy password] @ 127.0.0.1: [port] ",
"https": "http://[agent user name]: [agent password] @ 127.0.0.1: [port]“
},
"concurrent": false,
"domains": [
"include:[Domain name to prevent contamination]",
]
}
]
}To remove IPv6 is to remove this tick. Because during the test, it will be found that many applications default to IPv6 for requests. In fact, it can also be set in the DNS of IPv6 address, but it may also cause problems in the subsequent socks proxy, so it can be removed directly.
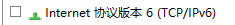
If you want to implement IPv6, first make sure that your socks proxy supports IPv6, and then in the above configuration file
"inbounds": [
"[Native IP Address, be careful not to use 127.0.0.1]:53",
"[Native IP Address, IPv6]:53",
"tcp://[the IP address of this machine should not be 127.0.0.1]: 5301“
"tcp://[local IP address, IPv6]: 5301“
],Set two bind addresses to listen to ipv6 addresses at the same time.
This is set in ipv4. The same goes for ipv6