preface
In the previous security, relevant configurations and tests were conducted for configuration items.
But these are based on security config. Myconfig #configure (org. Springframework. Security. Config. Annotation. Web. Builders. Httpsecurity) to restrict the permission of the corresponding request.
If there are multiple requests with different configuration items, and the configuration mode of configure(HttpSecurity http) is still adopted, there will be a lot of inconvenience.
This test
This blog mainly explains how to use annotation to realize the configuration and testing of different requests and different permission settings.
Annotation introduction
Before configuring and setting operations, we will briefly introduce the purpose of the following annotations.
- 1,@Secured
Determine whether the subject has a ROLE access method. Note that the matching string needs to be prefixed with ROLE_. - 2,@PreAuthorize
It is applicable to permission verification before entering the method,
The roles / permissions parameter of the login user can be passed to the method. - 3. @ PostAuthorize (less used)
The permission verification is performed after the method is executed, which is suitable for verifying the permission with the return value. - 4,@PostFilter
After the permission is verified, the data of the specified user name is left. - 5,@PreFilter
Filter the passed parameter values.
Annotation use
@Secured
Determine whether the subject has a ROLE access method. Note that the matching string needs to be prefixed with ROLE_.
Before using annotation configuration, you need to turn on annotation support on the startup class.
@EnableGlobalMethodSecurity(securedEnabled = true) //Enable the security function to add permissions to the method
Write the test interface and use the annotation to limit the access rights of the interface:
@RequestMapping("/update")
@Secured({"ROLE_admin","ROLE_user"})
public String update(){
return "security test 5 update Interfaces to be verified";
}
@RequestMapping("/delete")
@Secured({"ROLE_delete"})
public String delete(){
return "security test 5 delete Interfaces to be verified";
}
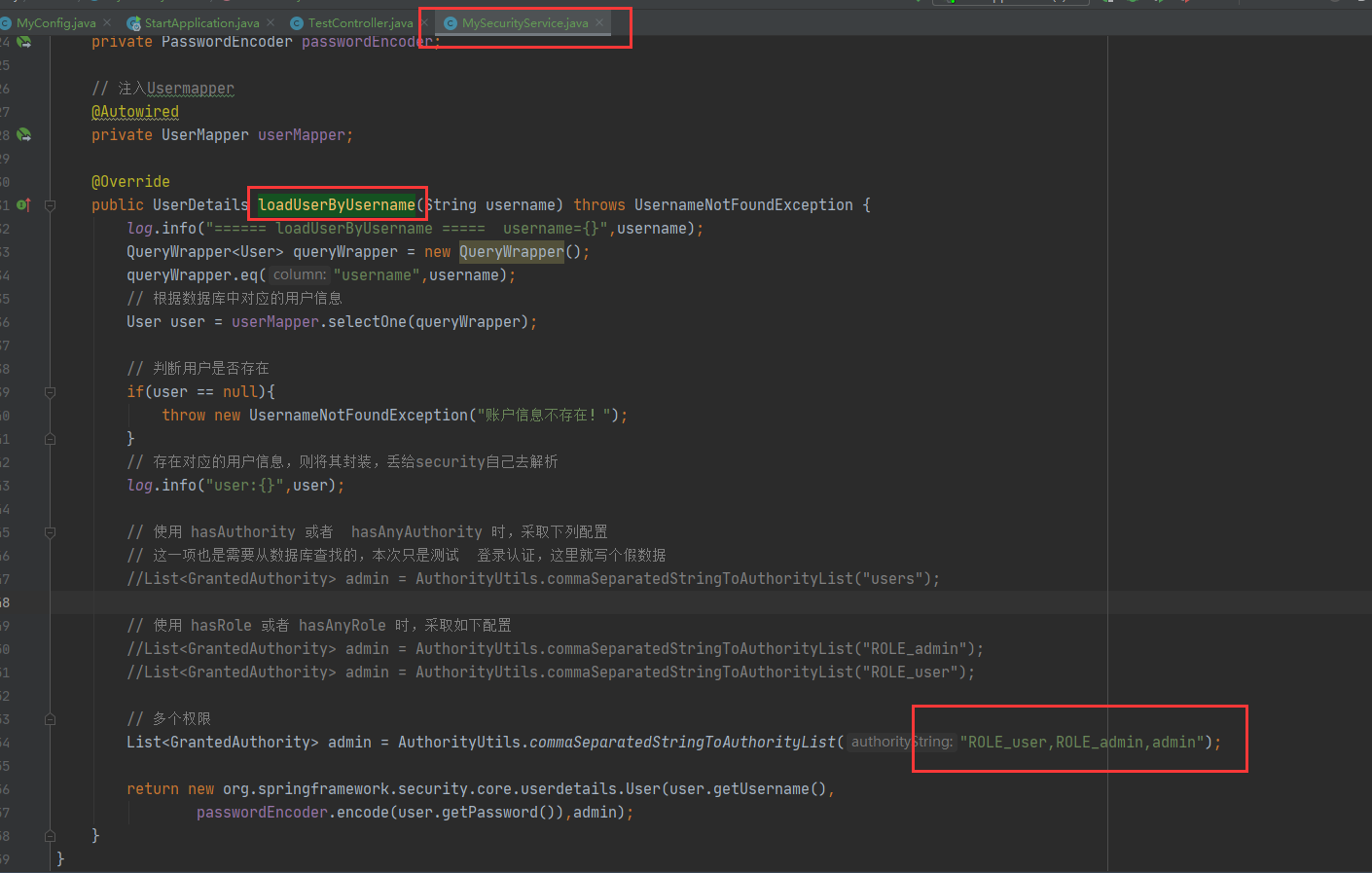
In security service. Set user permission information in mysecurityservice#loaduserbyusername.
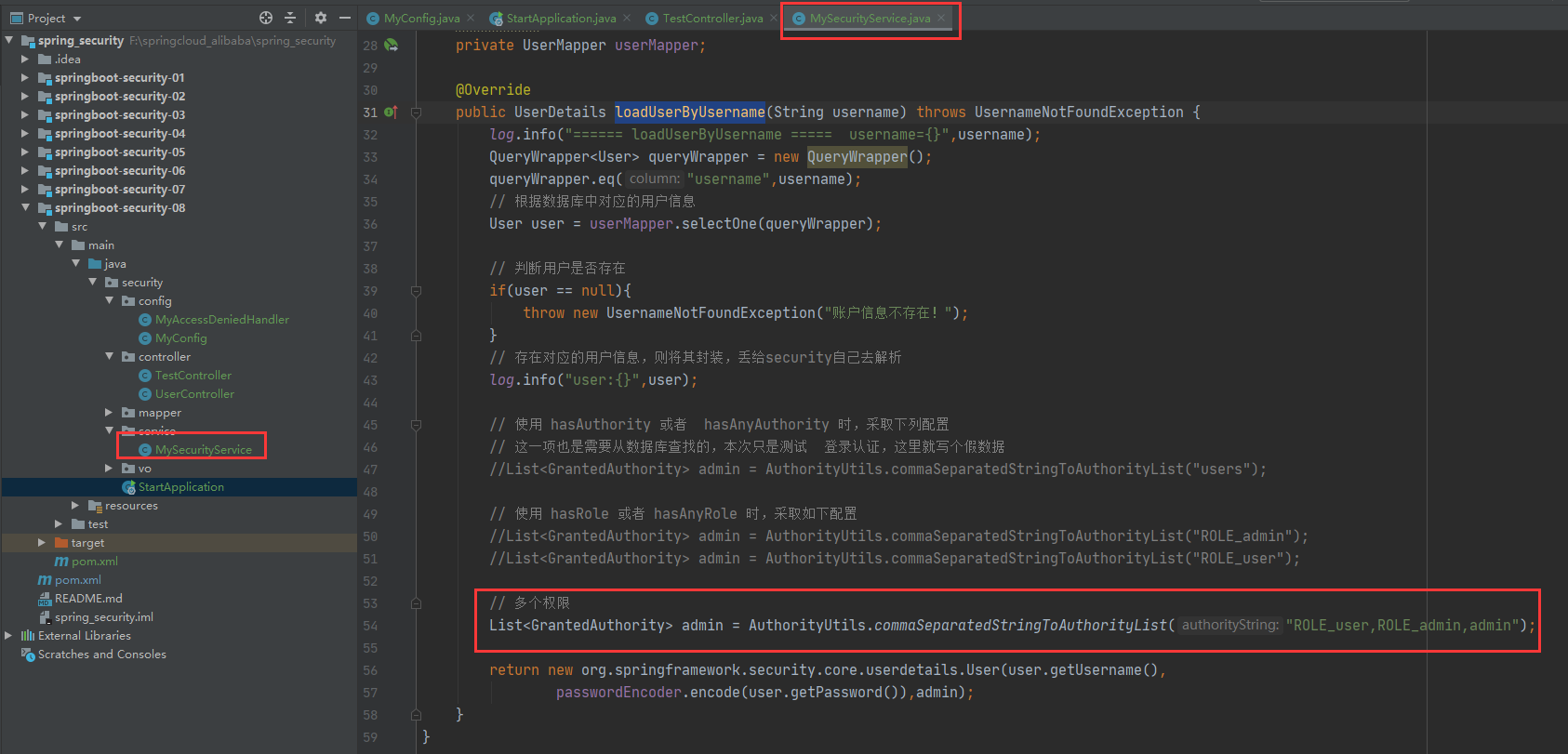
List<GrantedAuthority> admin =
AuthorityUtils.commaSeparatedStringToAuthorityList("ROLE_user,ROLE_admin,admin");
Because the login role is set with ROLE_user,ROLE_admin and admin permissions.
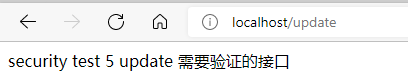
Role is required for interface / update_ Admin and ROLE_user.
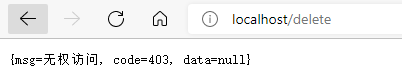
Role is required for interface / delete_ delete.
From the perspective of setting permissions, / update can be accessed, but / delete cannot be accessed because it does not have permission.
Request test:
http://localhost/update
http://localhost/delete
@PreAuthorize
It is applicable to permission verification before entering the method,
The roles / permissions parameter of the login user can be passed to the method.
Before configuration, the following comments must be added to the startup class:
@EnableGlobalMethodSecurity(prePostEnabled = true) //Enable the security function to add permissions to the method
If other annotations are used, the following annotation methods can be used:
@EnableGlobalMethodSecurity(securedEnabled = true,prePostEnabled = true) //Enable the security function to add permissions to the method
Write test controller interface:
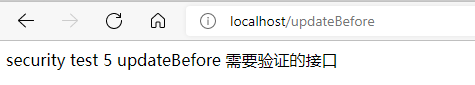
@RequestMapping("/updateBefore")
//@PreAuthorize("hasRole('ROLE_admin')")
//@PreAuthorize("hasAnyRole('ROLE_admin','ROLE_user')")
//@PreAuthorize("hasAuthority('admin')")
@PreAuthorize("hasAnyAuthority('admin','update')") // Note the single quotation mark
public String updateBefore(){
return "security test 5 updateBefore Interfaces to be verified";
}
Check the configuration role information of the login account:
Request test:
http://localhost/updateBefore
@PostAuthorize
The permission verification is performed after the method is executed, which is suitable for verifying the permission with the return value.
Before testing, the following annotations must be included on the startup class to ensure the normal use of annotations:
@EnableGlobalMethodSecurity(prePostEnabled = true) //Enable the security function to add permissions to the method
If other annotations are used, the following annotation methods can be used:
@EnableGlobalMethodSecurity(securedEnabled = true,prePostEnabled = true) //Enable the security function to add permissions to the method
Write the corresponding test interface:
@RequestMapping("/updateAfter")
@PostAuthorize("hasAnyRole('ROLE_update')") // Role not configured_ Update permission
public String updateAfter(){
log.info("=== Enter current updateAfter ====");
return "security test 5 updateAfter Interfaces to be verified";
}
To view the permission information of the login role in the configuration permission:
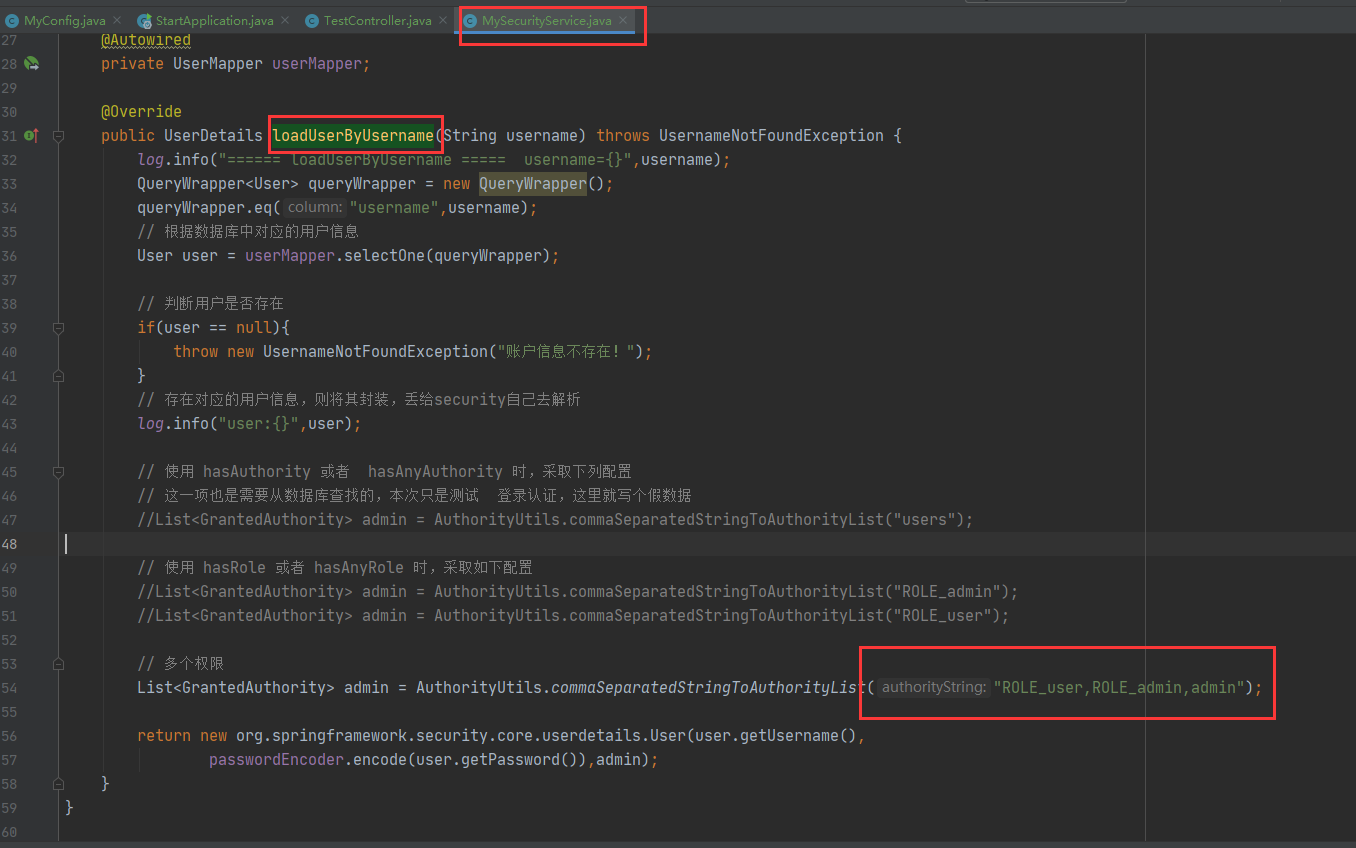
Request test:
http://localhost/updateAfter
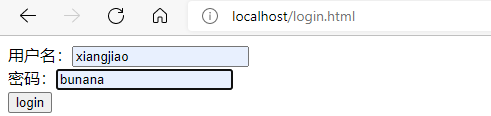
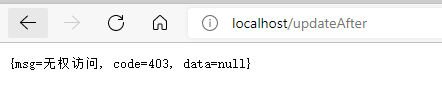
View console:
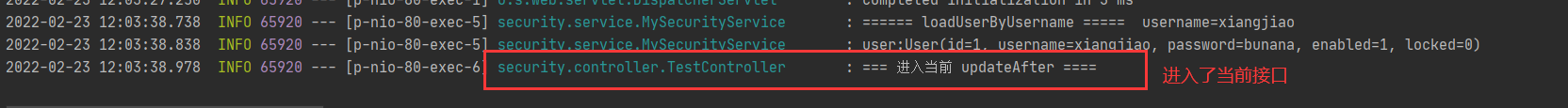
@PostFilter
After the permission is verified, the data of the specified user name is left.
Filter the returned data
Write request interface:
@RequestMapping("/postFilter")
@PreAuthorize("hasAnyAuthority('admin','update')") // Note the single quotation mark
@PostFilter("filterObject.username == 'xiangjiao'") // Filter the returned data
public List<User> postFilter(){
log.info("=== Enter current postFilter ====");
List<User> userLists = new ArrayList<>();
userLists.add(new User(1,"xiangjiao","bunana",1,0));
userLists.add(new User(2,"xiangjiao2","bunana2",1,0));
return userLists;
}
There are two encapsulated data results above!
Request:
http://localhost/postFilter
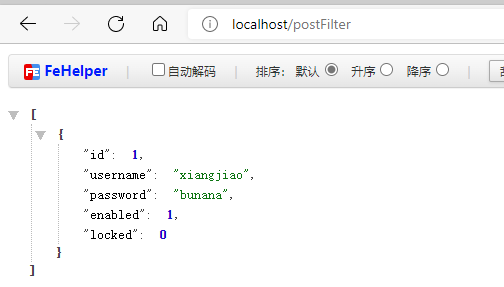
It was originally two pieces of data, but only one was returned,
@PostFilter("filterObject.username = =" xiangjiao ") only returns data whose username is xiangjiao!
@PreFilter
Filter the passed parameter values.
Write request interface:
@PostMapping("/preFilter")
@PreAuthorize("hasAnyAuthority('admin','update')") // Note the single quotation mark
@PreFilter("filterObject.id % 2 == 0") // You can only request if the id is even
public String preFilter(@RequestBody List<User> userLists){
log.info("=== Enter current preFilter ====");
log.info(userLists.toString());
return "security test 5 preFilter Interfaces to be verified";
}
It has not been tested yet, because the front and back separation has not been studied in depth, so it will be supplemented in the later stage!
Code download
springboot-security-08