Problem finding
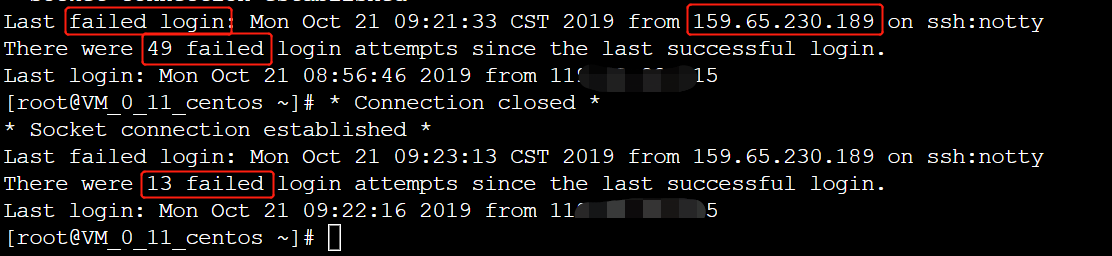
Log in to the virtual machine, and according to the prompt message, it is found that it is suffering from SSH explosion attack, with IP address of 159.65.230.189.
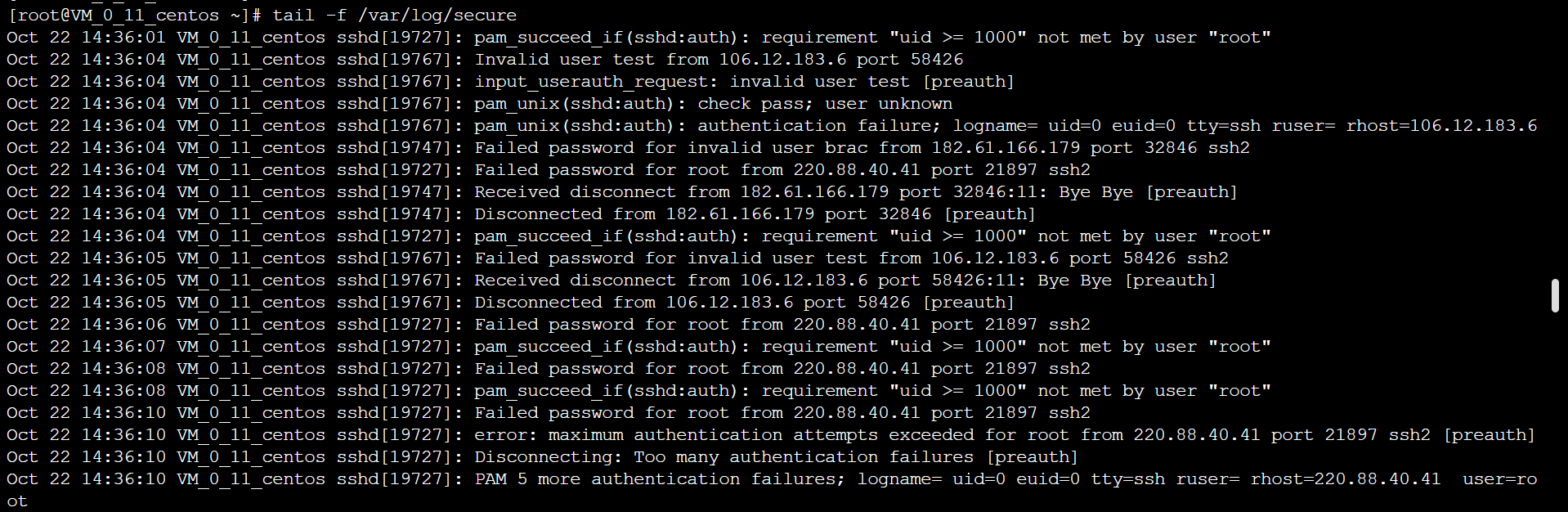
Check the log in related security logs: tail -f /var/log/secure, and find other attempts to blow up IP106.12.183.6, 182.61.166.179, 220.88.40.41.
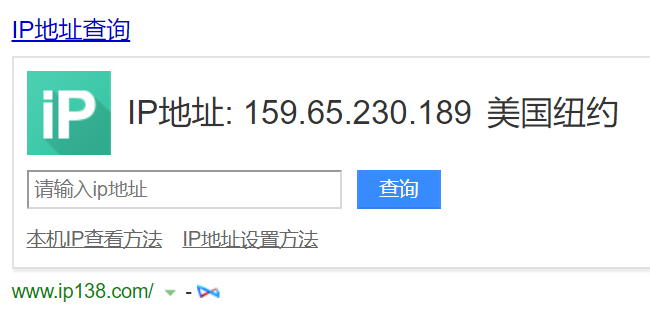
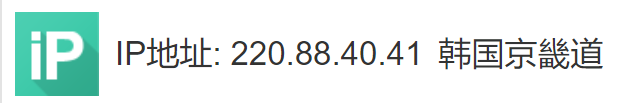
Baidu search IP address for foreign IP, there are 2 IP queries show Baidu, do not know what is the reason.
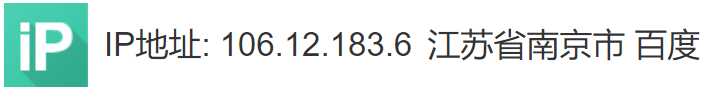
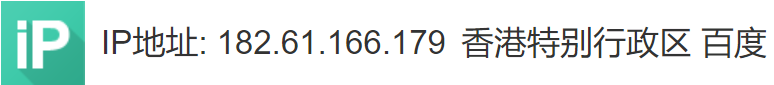
In addition, it is found that there are SSH attacks on this IP in other places. The URL of the link is: http://antivirus.neu.edu.cn/scan/ssh.php , which is the attack record in the network center network threat blacklist system of Northeast University.

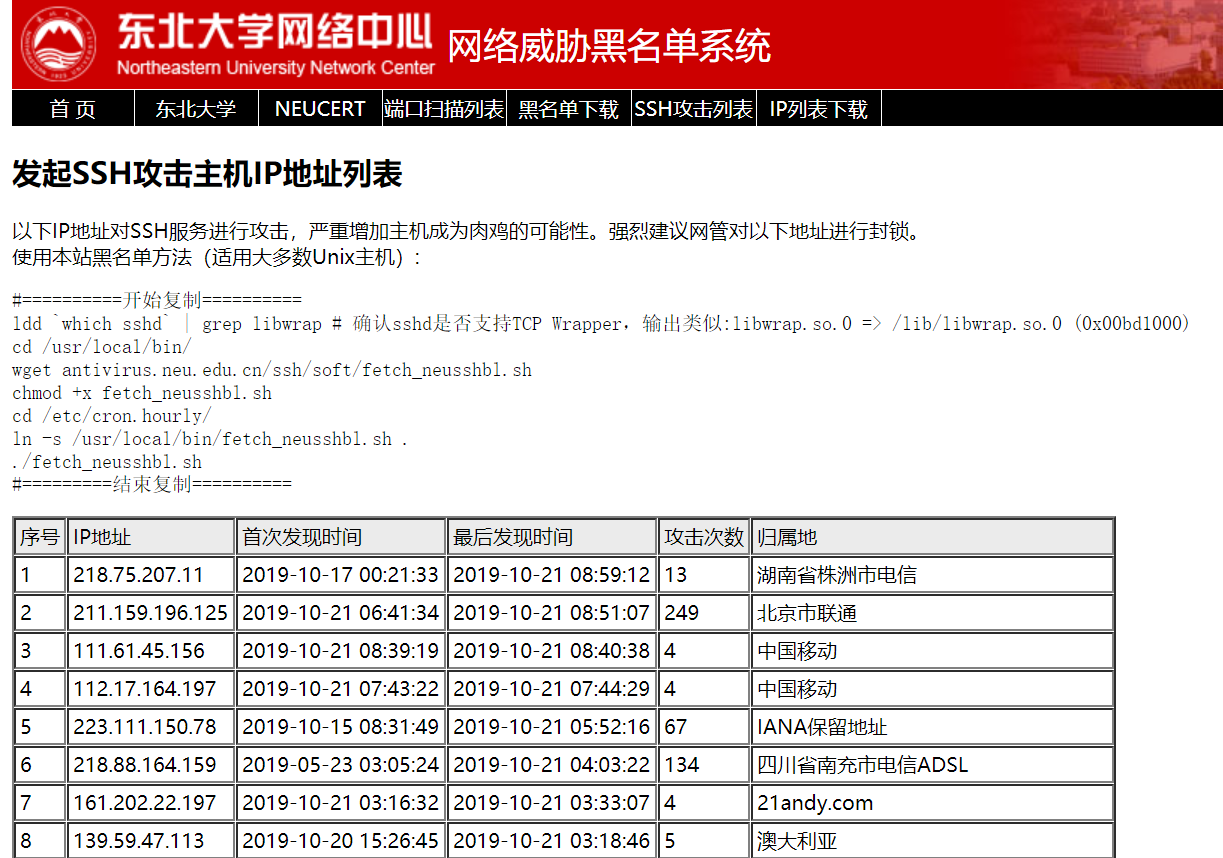

The website gives the methods to block these black IP, which can be used for reference. This system is not used, but uses the following "prevent SSH brute force cracking script".
#==========Start copying========== ldd `which sshd` | grep libwrap # Confirm whether sshd supports TCP Wrapper. The output is similar: libwrap. So. 0 = > / lib / libwrap. So. 0 (0x00bd1000) cd /usr/local/bin/ wget antivirus.neu.edu.cn/ssh/soft/fetch_neusshbl.sh chmod +x fetch_neusshbl.sh cd /etc/cron.hourly/ ln -s /usr/local/bin/fetch_neusshbl.sh . ./fetch_neusshbl.sh #=========End replication==========
Prevent SSH brute force cracking script
Note: for more than 10 attempts of the same IP address, add / etc/hosts.deny.
- vi ssh_pervent.sh
#! /bin/bash cat /var/log/secure|awk '/Failed/{print $(NF-3)}'|sort|uniq -c|awk '{print $2"="$1;}' > /root/sshPrevent/black.txt DEFINE="10" for i in `cat /root/sshPrevent/black.txt` do IP=`echo $i |awk -F= '{print $1}'` NUM=`echo $i|awk -F= '{print $2}'` if [ $NUM -gt $DEFINE ]; then grep $IP /etc/hosts.deny > /dev/null if [ $? -gt 0 ]; then echo "sshd:$IP" >> /etc/hosts.deny fi fi done
Add scheduled task:
[root@VM_0_11_centos ~]# crontab -e */5 * * * * /bin/bash /root/sshPrevent/ssh_pervent.sh # Check every five minutes # Restart crontab [root@VM_0_11_centos ~]# systemctl restart crond
After five minutes, check to see if it is successful:
[root@VM_0_11_centos sshPrevent]# cat black.txt 101.36.138.61=1 103.133.109.143=4 103.15.62.69=42 103.21.228.3=8 103.23.100.87=50 104.131.113.106=1 104.131.37.34=51 104.131.83.45=51 104.200.110.184=49 104.210.60.66=14 104.211.79.54=50 104.244.76.201=6 104.244.79.242=6 ...... ------------------I'm the divider------------------
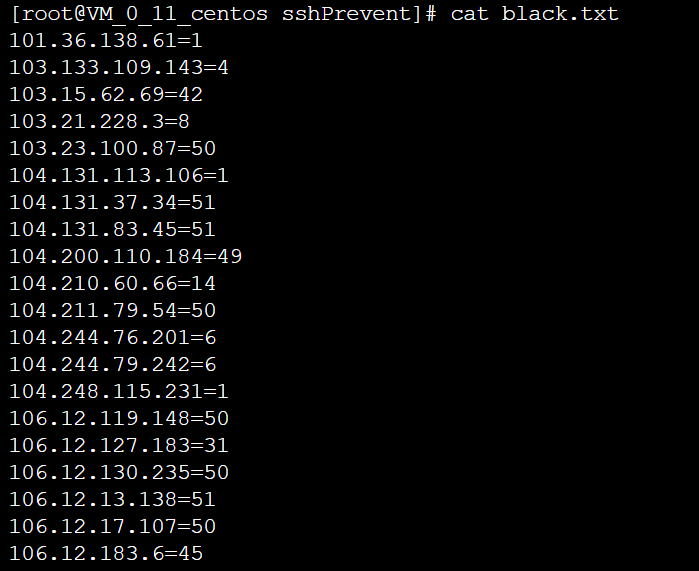
[root@VM_0_11_centos sshPrevent]# cat /etc/hosts.deny # # hosts.deny This file contains access rules which are used to # deny connections to network services that either use # the tcp_wrappers library or that have been # started through a tcp_wrappers-enabled xinetd. # # The rules in this file can also be set up in # /etc/hosts.allow with a 'deny' option instead. # # See 'man 5 hosts_options' and 'man 5 hosts_access' # for information on rule syntax. # See 'man tcpd' for information on tcp_wrappers # sshd:103.15.62.69 sshd:103.21.228.3 sshd:103.23.100.87 sshd:104.131.37.34 sshd:104.131.83.45 sshd:104.200.110.184 sshd:104.210.60.66 sshd:104.211.79.54 sshd:106.12.119.148 sshd:106.12.127.183 sshd:106.12.130.235 sshd:106.12.13.138 sshd:106.12.17.107 sshd:106.12.183.6 sshd:106.12.199.98 sshd:106.12.24.1 sshd:106.12.241.109 sshd:106.12.30.229 sshd:106.12.60.137 sshd:106.12.80.204 sshd:106.13.52.234 sshd:106.13.56.45 ...... ------------------I'm the divider------------------
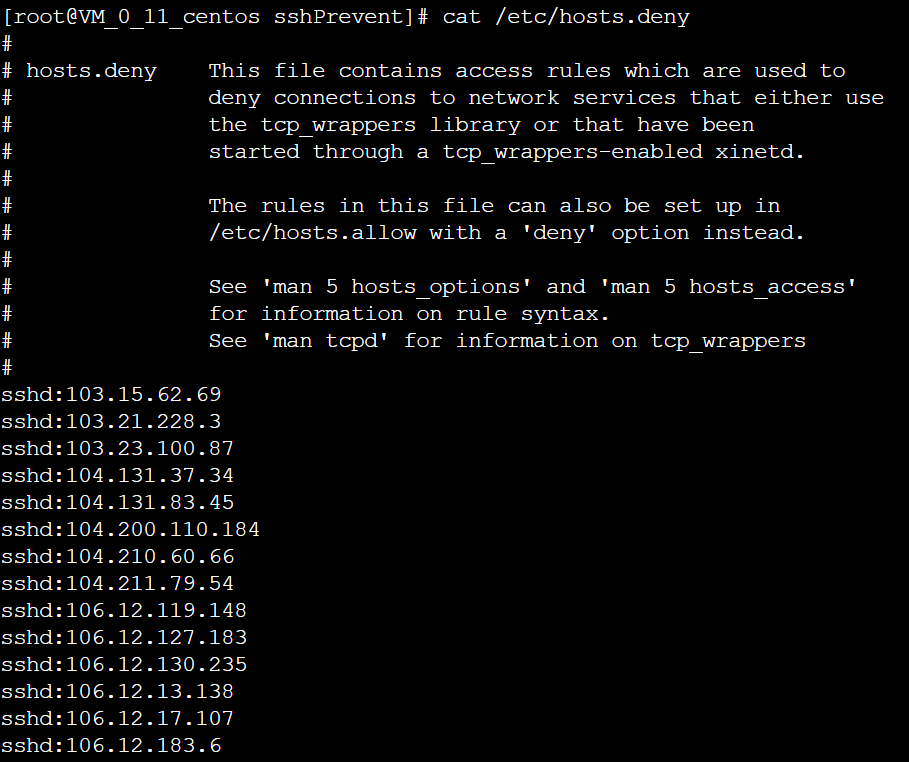
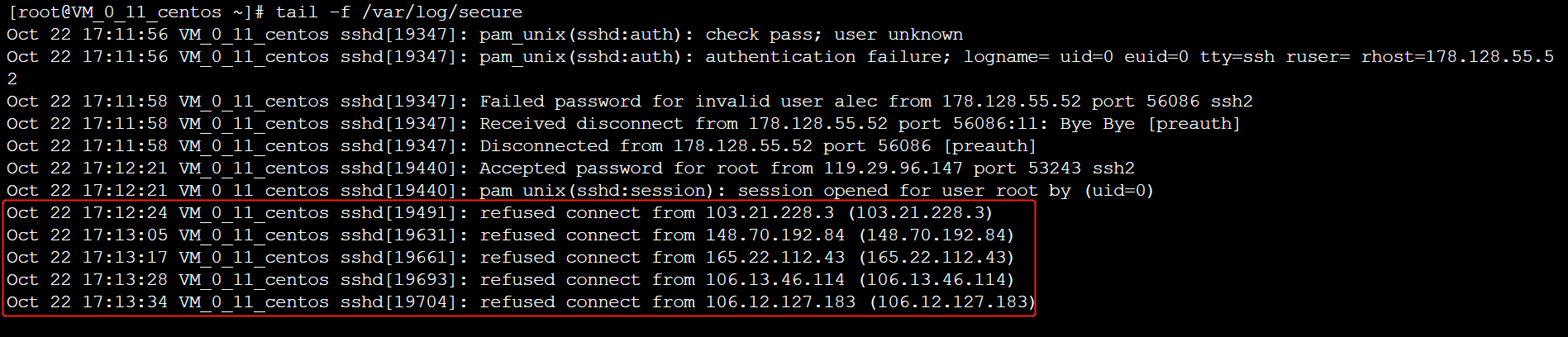
The blasting source IP successfully joins the block list, check the security log, and you can see that the IP joining the block list is refused to connect, and the blasting is successful.
Reference link
- [Linux CentOS prevents SSH brute force cracking] https://www.cnblogs.com/l-hh/p/11204251.html
- [prevent ssh brute force cracking under Centos] https://www.jianshu.com/p/fc41ad4399d9
This article starts from Lufei station http://www.noofi.cn
Long press QR code to follow us
