1. Brief introduction
DES, which is called Data Encryption Standard, is a block algorithm using key encryption. It is a symmetric encryption algorithm, the so-called symmetric encryption algorithm is: encryption and decryption using the same key algorithm.
2. Model Analysis
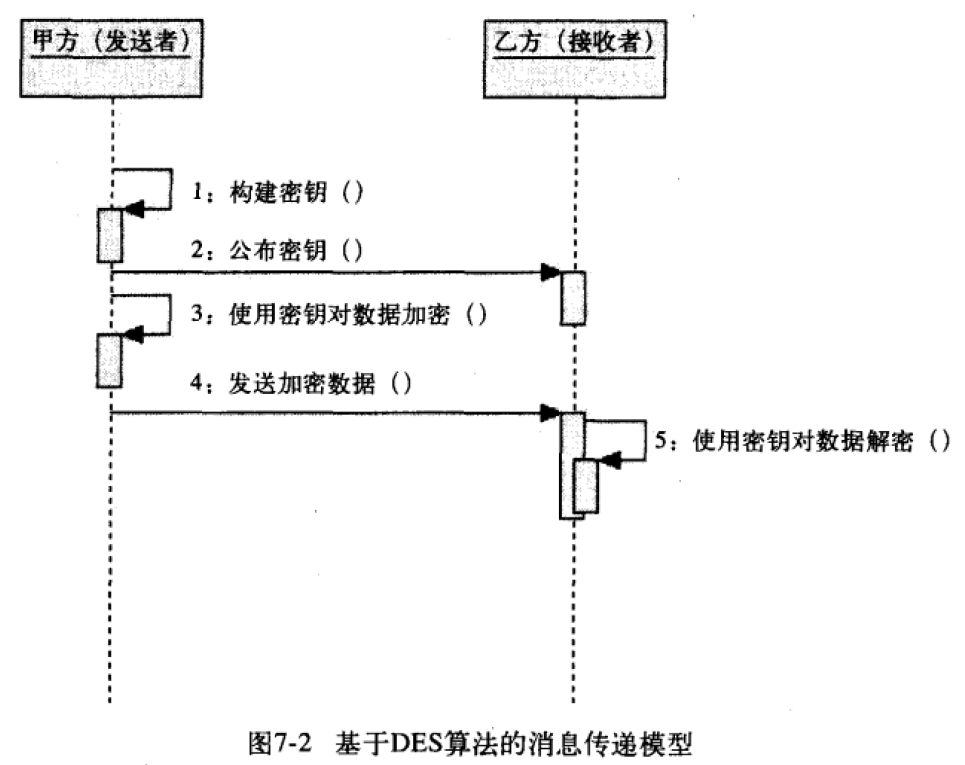
Messaging goes through the following steps:
(1) The key is agreed upon by both parties of the message transmission, where the key is constructed by Party A;
(2) The key is published by the key builder, which is published by Party A to Party B.
(3) The data is encrypted by the sender of the message using the key, where the data is encrypted by the first party.
(4) The encrypted data is sent by the sender to the receiver of the message, where the encrypted data is sent by Party A to Party B;
(5) The message receiver decrypts the encrypted data by using the key. Here, Party B completes the data decryption.
3. Realization
There are three entry parameters: key, data and mode. Key is the key used for encryption and decryption, data is the data encrypted and decrypted, and mode is its working mode. When the mode is encrypted, plaintext is grouped according to 64 bits to form plaintext group. Key is used to encrypt data, and key is used to decrypt data when the mode is decrypted. In practice, the key only uses 56 bits of 64 bits, so it has high security.
At both ends of the communication network, the two sides agree on a key, which encrypts the core data with Key at the source of the communication, and then transmits the data to the end of the communication network in the form of cryptography in the public communication network (such as telephone network). When the data reaches the destination, the same Key decrypts the cryptographic data and reproduces the core data in the form of plain code. In this way, the security and reliability of the core data (such as PIN, MAC, etc.) in the public communication network are guaranteed.
import java.security.SecureRandom; import javax.crypto.Cipher; import javax.crypto.SecretKey; import javax.crypto.SecretKeyFactory; import javax.crypto.spec.DESKeySpec; import sun.misc.BASE64Decoder; import sun.misc.BASE64Encoder; /** * Note: During DES encryption and decryption, the key length must be multiple of 8. */ public class DESCoder { /**Key algorithm*/ private final static String DES = "DES"; /***/ private final static String encode = "utf-8"; /** * DES encryption * @param data * @param key * @return */ public static String encrypt(byte[] data, String key) throws Exception{ SecureRandom secureRandom = new SecureRandom(); DESKeySpec desKeySpec = new DESKeySpec(key.getBytes(encode)); //Create a key factory and use it to convert DESKeySpec SecretKeyFactory keyFactory = SecretKeyFactory.getInstance(DES); SecretKey securekey = keyFactory.generateSecret(desKeySpec); //Cipher Object Actually Completes Encryption Operation Cipher cipher = Cipher.getInstance(DES); //Initialization of Cipher objects with keys cipher.init(Cipher.ENCRYPT_MODE, securekey, secureRandom); //Formal Encryption Operation byte[] bt = cipher.doFinal(data); return new BASE64Encoder().encode(bt); } /** * DES Decrypt * @param src * @param password * @return */ public static String decrypt(String encryStr, String password) throws Exception{ BASE64Decoder decoder = new BASE64Decoder(); byte[] encryArr = decoder.decodeBuffer(encryStr); // DES algorithm requires a trusted random number source SecureRandom random = new SecureRandom(); DESKeySpec desKey; // Create a DESKeySpec object desKey = new DESKeySpec(password.getBytes(encode)); // Create a Key Factory SecretKeyFactory keyFactory = SecretKeyFactory.getInstance("DES"); // Converting DESKeySpec objects to SecretKey objects SecretKey securekey = keyFactory.generateSecret(desKey); // Cipher object actually completes decryption operation Cipher cipher = Cipher.getInstance("DES"); // Initialization of Cipher objects with keys cipher.init(Cipher.DECRYPT_MODE, securekey, random); // Really start decryption byte[] arr = cipher.doFinal(encryArr); return new String(arr, encode); } public static void main(String[] args) { String sourceData = "DES test"; String defaultKey = "test1234"; try { String encStr = encrypt(sourceData.getBytes(encode), defaultKey); System.out.println(sourceData +"-DES After encryption:"+ encStr); String decStr = decrypt(encStr, defaultKey); System.out.println(sourceData +"-DES After decryption:"+ decStr); /*** * Console Result: * DES Test - DES Encryption: VbWhbgtPKdqkyOgovNWCFQ== * DES Testing - DES decryption: DES testing */ } catch (Exception e) { e.printStackTrace(); } } }
4. Summary
DES (Data Encryption Standard) is a typical algorithm in the field of symmetric encryption algorithm.
Advantages: The algorithm is open, the computation is small, the encryption speed is fast, and the encryption efficiency is high.
Disadvantage: Both sides of the transaction use the same key, the security is not guaranteed;
Every time a pair of users use symmetric encryption algorithm, they need to use the only key that others do not know, which will make the number of keys owned by both senders and receivers increase geometrically, and key management becomes the burden of users. Symmetric encryption algorithm is difficult to use in distributed network system, mainly because of the difficulty of key management and high cost.