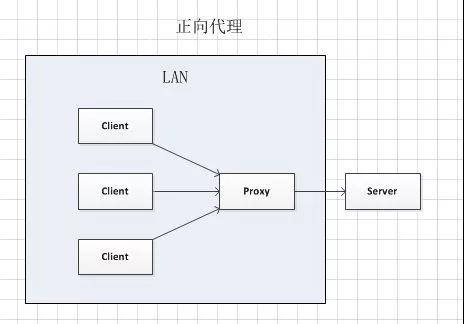
The forward proxy is a server between the client and the original server. In order to obtain content from the original server, the client sends a request to the proxy and specifies the target (the original server), and then the proxy delivers the request to the original server and returns the obtained content to the client. The client can use the forward proxy.
The typical use of forward proxy is to provide access to the Internet for LAN clients in the firewall. The forward proxy can also use the buffering feature (provided by mod_cache) to reduce network usage. The forward proxy allows clients to access any website through it and hide the client itself, so you must take security measures to ensure that only authorized clients are served. Unlike reverse proxy, a typical forward proxy is one that end users know and use actively.
Use two diagrams to explain the forward agent: https://www.zhihu.com/question/24723688

Effect
Access resources that were previously inaccessible, such as google
Cache to speed up access to resources
Authorization of client access and online authentication
Agents can record user access records (online behavior management) and hide user information
Ordinary agent
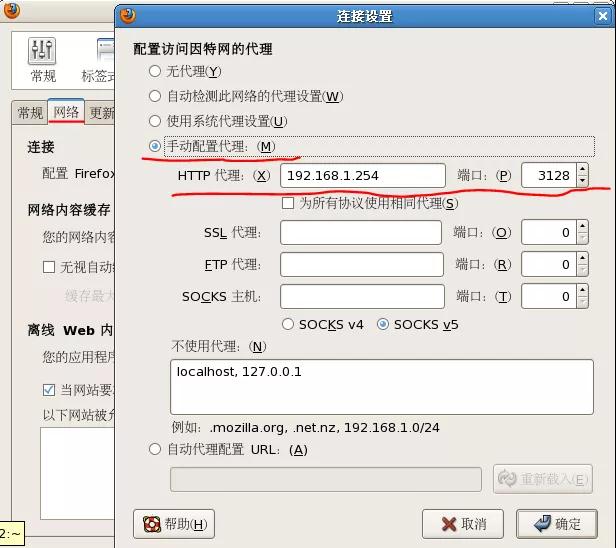
General agent: instead of all hosts in the local area network to access the website service of the public network, the hosts in the local area network need to specify the ip address of the proxy server and the port number to be monitored in their own browser
Install package squid
[root@ECS58979490c134 ~]# yum -y install squid
Edit the main configuration file / etc/squid/squid.conf
[root@ECS58979490c134 ~]# vim /etc/squid/squid.conf
http_port 3128 //Port number of squid default listening
cache_mem 8MB //Default cache capacity 8MB
cache_dir ufs /var/spool/squid 100 16 256 //Set the size of cache directory, format of cache file, size 100M, 16 first level subdirectories, 256 second level subdirectories under each first level subdirectory
access_log /var/log/squid/access.log squid //Access log file, on by default
visible_hostname proxy.eflycloud.com //By default, the hostname of the loopback is used as the hostname of the proxy server. Must be bound to physical interface when specifying host name manually
maximum_object_size //The maximum number of cache data allowed. When not set, unlimited
reply_body_max_size //Maximum target objects that are allowed to be accessed through a proxy server
http_access allow all //Reject all hosts by default
[root@ECS58979490c134 ~]# cat /etc/hosts127.0.0.1 localhost.localdomain localhost::1 localhost6.localdomain6 localhost6192.168.1.254 proxy.eflycloud.com proxy //Physical interface binding host name
Startup service
[root@ECS58979490c134 ~]# service squid start
init_cache_dir /var/spool/squid... Starting squid: .[ OK ]
[root@ECS58979490c134 ~]# netstat -anptu | grep :3128
Tcp 0 0 0.0.0.0:3128 0.0.0.0:* LISTEN 10439/(squid)
Setting up proxy server in client browser
Transparent proxy
Transparent proxy: the client does not need to specify the IP address of the proxy server and the port number to listen to in the browser of this machine, which gives the client the feeling of communicating with the public network directly. However, the client needs to specify or add a transparent proxy server as the gateway.
Configure transparent proxy server
[root@ECS58979490c134 ~]# vim /etc/squid/squid.conf
http_port 3128 transparent //Transparent transmission
[root@ECS58979490c134 ~]#service squid restart
Write the firewall rule, and transfer the request that the access target port is 80 to port 3128. If no port is specified, all requests will go to port 3128
[root@ECS58979490c134 ~]# service iptables start //Turn on Firewall Service
[root@ECS58979490c134 ~]#setup[root@ECS58979490c134 ~]# iptables -t filter -F //Clear table filter firewall rule
[root@ECS58979490c134 ~]# iptables -t nat -F //Clear table nat firewall rules
[root@ECS58979490c134 ~]# iptables -t nat -A PREROUTING -i eth0 -s 192.168.1.0/24 -p tcp --dport 80 -j REDIRECT --to-ports 3128 //PREROUTING - before routing, - i - which port does the packet come from, - s - source IP address, - p - Protocol, - dport - destination port, - to ports
[root@ECS58979490c134 ~]#service iptables save / / permanent
The ip address of the intranet interface that the client points the gateway to the proxy server
[root@ECS58979490c164 ~]# route add default gw 192.168.1.254
Ruijiang cloud official website link: https://www.eflycloud.com/home?from=RJ0035