#(1) generate flanneld certificate on the springboard machine
#cd /temp/ssl/
cat > flanneld-csr.json <<EOF
{
"CN": "flanneld",
"hosts": [],
"key": {
"algo": "rsa",
"size": 2048
},
"names": [
{
"C": "CN",
"ST": "Hangzhou",
"L": "Hangzhou",
"O": "k8s",
"OU": "System"
}
]
}
EOF#(2) select an etcd cluster node machine, register the relevant information of flannel with etcd and verify
Configure environment variables
export CLUSTER_CIDR="172.30.0.0/16" export ETCD_ENDPOINTS="https://192.168.19.128:2379,https://192.168.19.129:2379,https://192.168.19.130:2379" export FLANNEL_ETCD_PREFIX="/kubernetes/network"
Register flannel information with etcd
etcdctl \
--endpoints=${ETCD_ENDPOINTS} \
--ca-file=/opt/kubernetes/ssl/ca.pem \
--cert-file=/opt/kubernetes/ssl/flanneld.pem \
--key-file=/opt/kubernetes/ssl/flanneld-key.pem \
set ${FLANNEL_ETCD_PREFIX}/config '{"Network":"'${CLUSTER_CIDR}'", "SubnetLen": 24, "Backend": {"Type": "vxlan"}}'Verification
etcdctl \
--endpoints=${ETCD_ENDPOINTS} \
--ca-file=/opt/kubernetes/ssl/ca.pem \
--cert-file=/opt/kubernetes/ssl/flanneld.pem \
--key-file=/opt/kubernetes/ssl/flanneld-key.pem \
get ${FLANNEL_ETCD_PREFIX}/config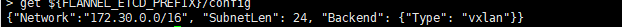
#(3) Download flanneld on the springboard machine
cd /tools wget https://github.com/coreos/flannel/releases/download/v0.10.0/flannel-v0.10.0-linux-amd64.tar.gz tar xf flannel-v0.10.0-linux-amd64.tar.gz
#(4) prepare the flanneld configuration file on the springboard machine
#cat >/temp/ssl/flanneld<<EOF FLANNEL_OPTIONS="-etcd-cafile=/opt/kubernetes/ssl/ca.pem -etcd-certfile=/opt/kubernetes/ssl/flanneld.pem -etcd-keyfile=/opt/kubernetes/ssl/flanneld-key.pem -etcd-endpoints=https://192.168.19.128:2379,https://192.168.19.129:2379,https://192.168.19.130:2379 -etcd-prefix=/kubernetes/network" EOF
#(5) prepare the flanneld startup script on the springboard machine
cat >/temp/ssl/flanneld.service<<EOF [Unit] Description=Flanneld overlay address etcd agent After=network-online.target network.target Before=docker.service [Service] Type=notify EnvironmentFile=/opt/kubernetes/cfg/flanneld ExecStart=/opt/kubernetes/bin/flanneld --ip-masq \$FLANNEL_OPTIONS ExecStartPost=/opt/kubernetes/bin/mk-docker-opts.sh -k DOCKER_NETWORK_OPTIONS -d /run/flannel/subnet.env Restart=on-failure [Install] WantedBy=multi-user.target
#(6) prepare the docker startup script file on the springboard machine
cat > /temp/ssl/docker.service <<EOF [Unit] Description=Docker Application Container Engine Documentation=https://docs.docker.com After=network-online.target firewalld.service Wants=network-online.target [Service] Type=notify EnvironmentFile=/run/flannel/subnet.env ExecStart=/usr/bin/dockerd \$DOCKER_NETWORK_OPTIONS ExecReload=/bin/kill -s HUP \$MAINPID LimitNOFILE=infinity LimitNPROC=infinity LimitCORE=infinity TimeoutStartSec=0 Delegate=yes KillMode=process Restart=on-failure StartLimitBurst=3 StartLimitInterval=60s [Install] WantedBy=multi-user.target EOF
#(7) send the flanneld certificate and private key file, flanneld configuration file, flanneld startup script file and docker startup configuration file to the master and node nodes on the springboard machine
ansible k8s -m copy -a 'src=/temp/ssl/flanneld-key.pem,dest=/opt/kubernetes/ssl/flanneld-key.pem' ansible k8s -m copy -a 'src=/temp/ssl/flanneld.pem,dest=/opt/kubernetes/ssl/flanneld.pem' ansible k8s -m copy -a 'src=/temp/ssl/flanneld dest=/opt/kubernetes/cfg/flanneld' ansible k8s -m copy -a 'src=/temp/ssl/flanneld.service dest=/usr/lib/systemd/system/flanneld.service' ansible k8s -m copy -a 'src=/temp/ssl/docker.service dest=/usr/lib/systemd/system/docker.service' ansible k8s -m copy -a 'src=/tools/flanneld dest=/opt/kubernetes/bin/flanneld' ansible k8s -m copy -a 'src=/tools/mk-docker-opts.sh dest=/opt/kubernetes/bin/mk-docker-opts.sh'
#(8) restart the flanend and docker services at the master and node nodes
systemctl daemon-reload systemctl enable flanneld systemctl restart flanneld systemctl restart docker
#(9) verification
Get the network segment information of flannel in each node
export CLUSTER_CIDR="172.30.0.0/16"
export ETCD_ENDPOINTS="https://192.168.19.128:2379,https://192.168.19.129:2379,https://192.168.19.130:2379"
export FLANNEL_ETCD_PREFIX="/kubernetes/network"
etcdctl --endpoints=${ETCD_ENDPOINTS} --ca-file=/opt/kubernetes/ssl/ca.pem --cert-file=/opt/kubernetes/ssl/flanneld.pem --key-file=/opt/kubernetes/ssl/flanneld-key.pem ls ${FLANNEL_ETCD_PREFIX}/subnetsView the routing table on the master and node nodes: you can see the routes of other nodes on each node
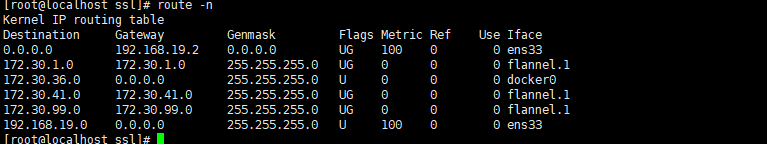
The ip address of master node and node node, docker0 uses the address range of flannel network segment and is also the gateway of pod container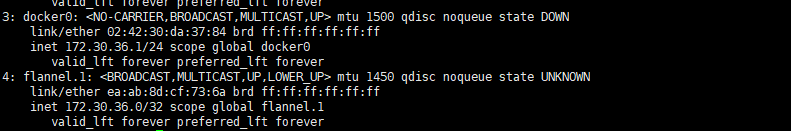
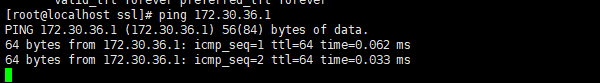
The flannel network segment between the master node and the node node can be ping ed, indicating that the flannel network deployment is completed