Set up FTP service
One: install ftp service
1.1 mount image file
Install vsftpd package
1.2 yum warehouse can also be used
[root@localhost ~]# yum install vsftpd-sysvinit.x86_64 -y Installed: vsftpd-sysvinit.x86_64 0:3.0.2-25.el7 Complete!
1.3 related file path
[root@localhost ~]# cd /etc/vsftpd/ [root@localhost vsftpd]# ls ftpusers user_list vsftpd.conf vsftpd_conf_migrate.sh
vsftpd.conf configuration file
User list user list: determine whether users in the user list can log in by modifying the configuration file, that is, modify the login authority of the black and white list
- The default profile parameters are as follows
[root@localhost vsftpd]# grep -v '#'vsftpd.conf' filter out valid execution parameters' anonymous_enable=YES 'Enable anonymous users' local_enable=YES 'Enable local users' write_enable=YES 'Enable write access' local_umask=022 'Enable unmask' dirmessage_enable=YES '' xferlog_enable=YES connect_from_port_20=YES xferlog_std_format=YES listen=NO listen_ipv6=YES pam_service_name=vsftpd 'pam Module authentication' userlist_enable=YES 'User list on' tcp_wrappers=YES
It can be used without modification at this time
[root@localhost vsftpd]# systemctl start vsftpd
[root@localhost vsftpd]# systemctl status vsftpd
● vsftpd.service - Vsftpd ftp daemon
Loaded: loaded (/usr/lib/systemd/system/vsftpd.service; disabled; vendor preset: disabled)
Active: active (running) since Sat 2019-12-07 14:35:44 CST; 22s ago
Process: 93638 ExecStart=/usr/sbin/vsftpd /etc/vsftpd/vsftpd.conf (code=exited, status=0/SUCCESS)
Main PID: 93639 (vsftpd)
CGroup: /system.slice/vsftpd.service
└─93639 /usr/sbin/vsftpd /etc/vsftpd/vsftpd.conf
Dec 07 14:35:44 localhost.localdomain systemd[1]: Starting Vsftpd ftp ...
Dec 07 14:35:44 localhost.localdomain systemd[1]: Started Vsftpd ftp d...
Hint: Some lines were ellipsized, use -l to show in full.
2. Optimize ftp services
2.1 it is necessary to close the firewall and setenforce r
[root@localhost vsftpd]# systemctl stop firewalld.service [root@localhost vsftpd]# setenforce 0 [root@localhost vsftpd]#
2.1.1 use another host to log in to ftp server and use anonymous login mode
C:\Users\GSY>ftp 192.168.247.140 'open vsftpd Server ip' //Connect to 192.168.247.140. 220 (vsFTPd 3.0.2) 200 Always in UTF8 mode. //User (192.168.247.140:(none)): ftp 331 Please specify the password. //Password: 230 Login successful. ftp> ftp> pwd 'View location' 257 "/" 'The root here does not represent the root directory of the server. It represents vsftpd Site' ftp> ls -a 'See' 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. . .. centos7 ks.cfg pub 'Public folders' 226 Directory send OK. ftp: 32 bytes received, time 0.00 Second 16.00 KByte/Seconds. ftp>
You can go to the corresponding site of the server to view
[root@localhost vsftpd]# ls -a /var/ftp . .. centos7 ks.cfg pub
Create a file on the server to test
[root@localhost vsftpd]# echo "778899" > /var/ftp/test.txt [root@localhost vsftpd]# ls -a /var/ftp . .. centos7 ks.cfg pub test.txt [root@localhost vsftpd]# cat /var/ftp/test.txt 778899
Go to the client to check
ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. centos7 ks.cfg pub test.txt 'Add corresponding file' 226 Directory send OK. ftp: Received 35 bytes, time 0.01 Second 7.00 KByte/Seconds. ftp>
2.2 the client switches to disk e for download test
ftp> get test.txt 200 PORT command successful. Consider using PASV. 150 Opening BINARY mode data connection for test.txt (7 bytes). 226 Transfer complete. ftp: Received 7 bytes, time 0.00 Second 7000.00 KByte/Seconds. ftp>
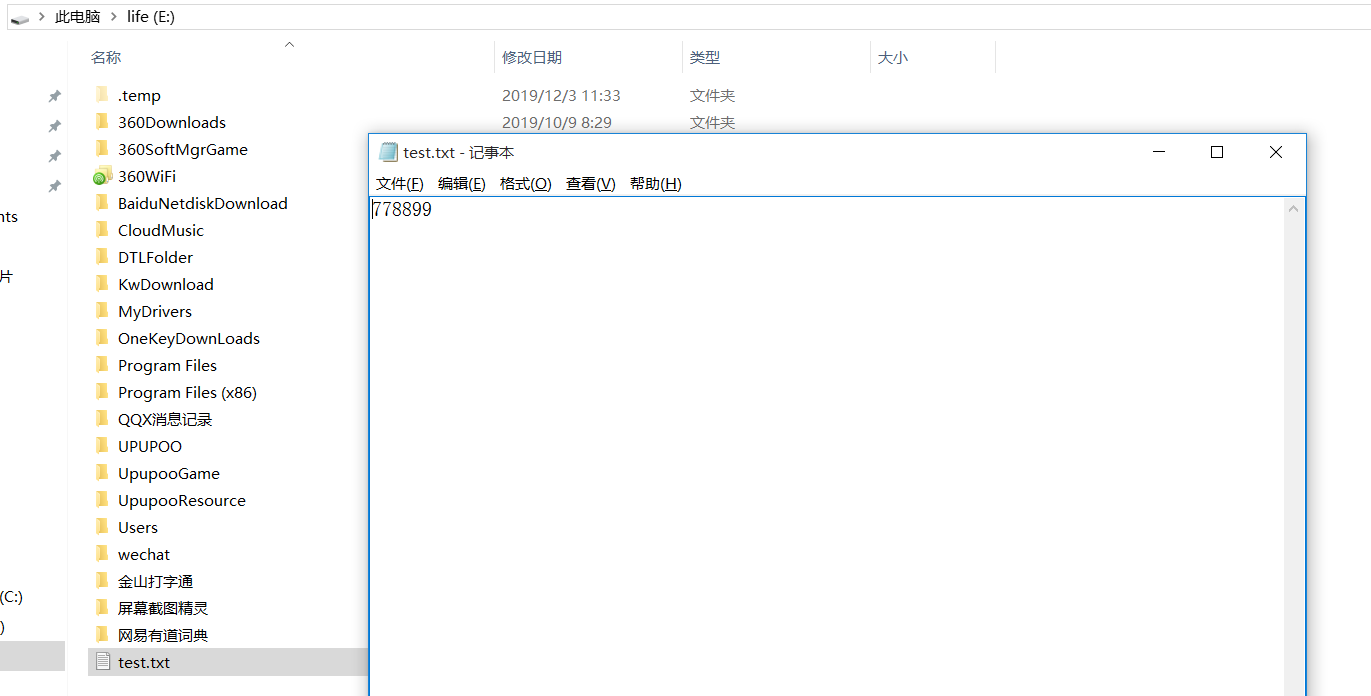
Test download, then test upload
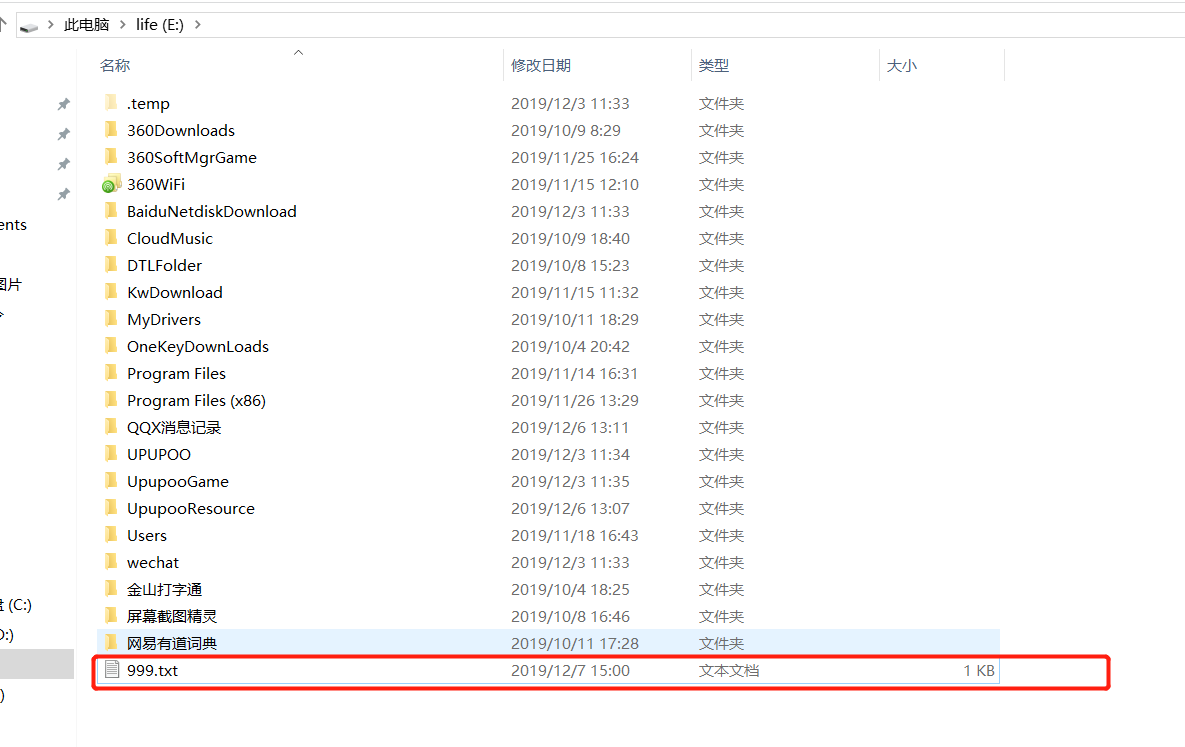
Insufficient feedback authority
ftp> put 999.txt 200 PORT command successful. Consider using PASV. 550 Permission denied. ftp>
2.3 now modify the vsftpd configuration file of the server to maximize the anonymous login permission
#Anon? MKDIR? Write? Enable = yes' creates a directory on behalf of an anonymous user ' #Anon? Upload? Enable = yes' means anonymous users can upload '
Remove the number key and save to exit
You can also use man to view the usage of the vsftpd.conf configuration file
[root@localhost vsftpd]# man vsftpd.conf
Enter man mode: anon to view key information
Default: NO
anon_other_write_enable
If set to YES, anonymous users will be permitted to per‐
form write operations other than upload and create direc‐
tory, such as deletion and renaming. This is generally
not recommended but included for completeness.
Default: NO
anon_upload_enable
If set to YES, anonymous users will be permitted to
upload files under certain conditions. For this to work,
the option write_enable must be activated, and the anony‐
mous ftp user must have write permission on desired
upload locations. This setting is also required for vir‐
tual users to upload; by default, virtual users are
treated with anonymous (i.e. maximally restricted) privi‐
lege.The default permission is no
Anon? Other? Write? Enable means that the file can be renamed or deleted
Add this command to the configuration file to maximize the permission of anon
You can use filter to check whether the verification function is on
[root@localhost vsftpd]# grep -v '#' vsftpd.conf anonymous_enable=YES local_enable=YES write_enable=YES local_umask=022 anon_upload_enable=YES anon_mkdir_write_enable=YES anon_other_write_enable=YES dirmessage_enable=YES xferlog_enable=YES connect_from_port_20=YES xferlog_std_format=YES listen=NO listen_ipv6=YES pam_service_name=vsftpd userlist_enable=YES tcp_wrappers=YES [root@localhost vsftpd]#
2.4 the modified configuration file needs to be reloaded to take effect
[root@localhost vsftpd]# systemctl reload vsftpd
Failed to reload vsftpd.service: Job type reload is not applicable for unit vsftpd.service.
See system logs and 'systemctl status vsftpd.service' for details.
[root@localhost vsftpd]# systemctl restart vsftpd
[root@localhost vsftpd]# service reload vsftpd
The service command supports only basic LSB actions (start, stop, restart, try-restart, reload, force-reload, status). For other actions, please try to use systemctl.
[root@localhost vsftpd]# service vsftpd reload
Reloading vsftpd configuration (via systemctl): Failed to reload vsftpd.service: Job type reload is not applicable for unit vsftpd.service.
See system logs and 'systemctl status vsftpd.service' for details.
[fail]It's hard to reload, so we have to restart
2.5 in vsftpd, the permission of anon should be maximized, and whether the permission of the file itself has been broadened should also be considered
[root@localhost vsftpd]# cd /var/ftp [root@localhost ftp]# ls -al total 12 drwxr-xr-x. 4 root root 62 Dec 7 14:53 . drwxr-xr-x. 24 root root 4096 Nov 22 14:43 .. drwxr-xr-x. 2 root root 6 Nov 22 14:51 centos7 -rw-r--r--. 1 root root 909 Nov 22 15:17 ks.cfg drwxr-xr-x. 2 root root 6 Oct 31 2018 pub -rw-r--r--. 1 root root 7 Dec 7 14:53 test.txt
Test it first
ftp> put 999.txt 200 PORT command successful. Consider using PASV. 553 Could not create file.
Still can't let go of ftp permission
[root@localhost ftp]# chmod 777 /var/ftp [root@localhost ftp]# ls -al total 12 drwxrwxrwx. 4 root root 62 Dec 7 14:53 . drwxr-xr-x. 24 root root 4096 Nov 22 14:43 .. drwxr-xr-x. 2 root root 6 Nov 22 14:51 centos7 -rw-r--r--. 1 root root 909 Nov 22 15:17 ks.cfg drwxr-xr-x. 2 root root 6 Oct 31 2018 pub -rw-r--r--. 1 root root 7 Dec 7 14:53 test.txt
All right
ftp> put 999.txt 200 PORT command successful. Consider using PASV. 150 Ok to send data. 226 Transfer complete. ftp: Send 7 bytes, time 0.00 Second 3.50 KByte/Seconds.
Go to the server to check and verify
[root@localhost ftp]# ls -al total 16 drwxrwxrwx. 4 root root 77 Dec 7 15:32 . drwxr-xr-x. 24 root root 4096 Nov 22 14:43 .. -rw-------. 1 ftp ftp 7 Dec 7 15:32 999.txt drwxr-xr-x. 2 root root 6 Nov 22 14:51 centos7 -rw-r--r--. 1 root root 909 Nov 22 15:17 ks.cfg drwxr-xr-x. 2 root root 6 Oct 31 2018 pub -rw-r--r--. 1 root root 7 Dec 7 14:53 test.txt
In the same way, you can change pub
2.6 next test and delete the uploaded files
ftp> delete 999.txt 250 Delete operation successful. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. centos7 ks.cfg pub test.txt 226 Directory send OK. ftp: Received 35 bytes, time 0.00 Second 35.00 KByte/Seconds.
[root@localhost ftp]# ls -al total 12 drwxrwxrwx. 4 root root 62 Dec 7 15:36 . drwxr-xr-x. 24 root root 4096 Nov 22 14:43 .. drwxr-xr-x. 2 root root 6 Nov 22 14:51 centos7 -rw-r--r--. 1 root root 909 Nov 22 15:17 ks.cfg drwxr-xr-x. 2 root root 6 Oct 31 2018 pub -rw-r--r--. 1 root root 7 Dec 7 14:53 test.txt
Test delete old file
ftp> delete test.txt 250 Delete operation successful. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. centos7 ks.cfg pub 226 Directory send OK. ftp: Received 25 bytes, time 0.00 Second 12.50 KByte/Seconds.
[root@localhost ftp]# ls -al total 8 drwxrwxrwx. 4 root root 46 Dec 7 15:37 . drwxr-xr-x. 24 root root 4096 Nov 22 14:43 .. drwxr-xr-x. 2 root root 6 Nov 22 14:51 centos7 -rw-r--r--. 1 root root 909 Nov 22 15:17 ks.cfg drwxr-xr-x. 2 root root 6 Oct 31 2018 pub
Can also be executed
Third: next test ordinary users
[root@localhost ftp]# useradd zhangsan [root@localhost ftp]# useradd lisi [root@localhost ftp]# echo "123123" | passwd zhangsan --stdin Changing password for user zhangsan. passwd: all authentication tokens updated successfully. [root@localhost ftp]# echo "123123" | passwd lisi --stdin Changing password for user lisi. passwd: all authentication tokens updated successfully.
Next, log in remotely with the newly created user on the client
E:\>ftp 192.168.247.140 //Connect to 192.168.247.140. 220 (vsFTPd 3.0.2) 200 Always in UTF8 mode. //User (192.168.247.140:(none)): zhangsan 331 Please specify the password. //Password: 230 Login successful. ftp> ftp> ftp> ftp> pwd 257 "/home/zhangsan"
3.1 you can find it in your own home directory
Next, upload test
ftp> put 999.txt 200 PORT command successful. Consider using PASV. 150 Ok to send data. 226 Transfer complete. ftp: Send 7 bytes, time 0.00 Second 7.00 KByte/Seconds.
[root@localhost ftp]# ls /home/zhangsan 999.txt [root@localhost ftp]#
3.2 switch directories. It is found that ordinary users can switch at will
ftp> cd / 250 Directory successfully changed. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. bin boot dev etc home lib lib64 media mnt opt proc root run sbin srv sys tmp usr var 226 Directory send OK. ftp: 107 bytes received, time 0.01 Second 9.73 KByte/Seconds.
This is a hidden danger to server security
Next, modify the corresponding configuration options
#Chroot? Local? User = yes' prevent local users from switching directories' allow_writeable_chroot=YES 'centos7 This item needs to be opened additionally in'
Enable it, save exit, restart service
ftp> ls The remote host closes the connection.
Use the bye command to exit ftp mode and log in again
E:\>ftp 192.168.247.142 //Connect to 192.168.247.142. 220 (vsFTPd 3.0.2) 200 Always in UTF8 mode. //User (192.168.247.142:(none)): zhangsan 331 Please specify the password. //Password: 230 Login successful. ftp> ls 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. 226 Directory send OK. ftp> ls -a 200 PORT command successful. Consider using PASV. 150 Here comes the directory listing. . .. .bash_logout .bash_profile .bashrc .mozilla 226 Directory send OK. ftp: 58 bytes received, time 0.00 Second 14.50 KByte/Seconds. ftp> pwd 257 "/" ftp> cd /etc 550 Failed to change directory. ftp>
3.3 next, configure user list user list
If userlist? Deny = no is used, only these users in the list are allowed to access
If you use userlist? Deny = Yes (default), these users in the list are not allowed to access
You can add zhangsan to the test
[root@localhost ftp]# echo "zhangsan" >> /etc/vsftpd/user_list [root@localhost ftp]#
After reloading the service, log in again. The login failed
E:\>ftp 192.168.247.140 //Connect to 192.168.247.140. 220 (vsFTPd 3.0.2) 200 Always in UTF8 mode. //User (192.168.247.140: (none)): Zhan 331 Please specify the password. //Password: 530 Login incorrect. //Login failed. ftp> ftp> ls 530 Please login with USER and PASS. 530 Please login with USER and PASS. ftp>
Increase the user list limit, only allow users in the list to access, and then restart the service
[root@localhost ftp]# vim /etc/vsftpd/vsftpd.conf userlist_enable=YES 'Open on behalf of user list' userlist_deny=NO 'Add allow only users in the user list to access'
Test, discovery takes effect
E:\>ftp 192.168.247.140 //Connect to 192.168.247.140. 220 (vsFTPd 3.0.2) 200 Always in UTF8 mode. //User (192.168.247.140:(none)): lisi 530 Permission denied. //Login failed. ftp> bye 221 Goodbye. E:\>ftp 192.168.247.140 //Connect to 192.168.247.140. 220 (vsFTPd 3.0.2) 200 Always in UTF8 mode. //User (192.168.247.140:(none)): zhangsan 331 Please specify the password. //Password: 230 Login successful. ftp>
Delete the configuration you just added and continue testing
IV. virtual users
4.1 create / etc/vsftpd/vuser file first
It contains the account number and password of the virtual account
[root@localhost ftp]# cd /etc/vsftpd/ [root@localhost vsftpd]# vim vuser [root@localhost vsftpd]# cat vuser lisa 123123 tom 123123
4.2 converting vuser files to database files
-T for conversion - t for type hash for hash algorithm type - f for specified file
[root@localhost vsftpd]# db_load -T -t hash -f vuser vuser.db [root@localhost vsftpd]# [root@localhost vsftpd]# ls -al total 48 drwxr-xr-x. 2 root root 117 Dec 7 16:37 . drwxr-xr-x. 140 root root 8192 Dec 7 15:41 .. -rw-------. 1 root root 125 Oct 31 2018 ftpusers -rw-------. 1 root root 370 Dec 7 16:03 user_list -rw-------. 1 root root 5142 Dec 7 16:11 vsftpd.conf -rwxr--r--. 1 root root 338 Oct 31 2018 vsftpd_conf_migrate.sh -rw-r--r--. 1 root root 23 Dec 7 16:33 vuser -rw-r--r--. 1 root root 12288 Dec 7 16:37 vuser.db
For security, modify these two files to 600 permissions
[root@localhost vsftpd]# chmod 600 vuse* [root@localhost vsftpd]# ls -al total 48 drwxr-xr-x. 2 root root 117 Dec 7 16:37 . drwxr-xr-x. 140 root root 8192 Dec 7 15:41 .. -rw-------. 1 root root 125 Oct 31 2018 ftpusers -rw-------. 1 root root 370 Dec 7 16:03 user_list -rw-------. 1 root root 5142 Dec 7 16:11 vsftpd.conf -rwxr--r--. 1 root root 338 Oct 31 2018 vsftpd_conf_migrate.sh -rw-------. 1 root root 23 Dec 7 16:33 vuser -rw-------. 1 root root 12288 Dec 7 16:37 vuser.db
4.3 create account corresponding to virtual user
[root@localhost vsftpd]# useradd -d /opt/vuser -s /sbin/nologin vuser [root@localhost vsftpd]# grep 'vuser' /etc/passwd vuser:x:1003:1003::/opt/vuser:/sbin/nologin [root@localhost vsftpd]# ls /opt 192.168.139.132 rh vuser
4.4 use pam authentication module to enable and support virtual user login
Create a PAM module file, / etc/pam.d/vsftpd.vu, and write it in it
auth required pam_userdb.so db=/etc/vsftpd/vuser
account required pam_userdb.so db=etc/vsftpd/vuser
Note that the file after db represents the file with db as the suffix
[root@localhost vsftpd]# cd /etc/pam.d/ [root@localhost pam.d]# cat vsftpd #%PAM-1.0 session optional pam_keyinit.so force revoke auth required pam_listfile.so item=user sense=deny file=/etc/vsftpd/ftpusers onerr=succeed auth required pam_shells.so auth include password-auth account include password-auth session required pam_loginuid.so session include password-auth [root@localhost pam.d]# vim vsftpd.vu [root@localhost pam.d]# cat vsftpd.vu auth required pam_userdb.so db=/etc/vsftpd/vuser account required pam_userdb.so db=etc/vsftpd/vuser [root@localhost pam.d]#
4.5 next, modify the configuration file
[root@localhost vsftpd]# vim vsftpd.conf #PAM? Service? Name = vsftpd 'turn off this command' guest_enable=YES 'Add guest features' guest_username=vuser pam_service_name=vsftpd.vu 'pam Module service specifies the module just created' [root@localhost pam.d]# tail -9 /etc/vsftpd/vsftpd.conf # Make sure, that one of the listen options is commented !! listen_ipv6=YES #pam_service_name=vsftpd userlist_enable=YES tcp_wrappers=YES guest_enable=YES guest_username=YES pam_service_name=vsftpd.vu
After modification, restart the service
4.6 next, you can use virtual users to log in and upload files
E:\>ftp 192.168.247.142 //Connect to 192.168.247.142. 220 (vsFTPd 3.0.2) 200 Always in UTF8 mode. //User (192.168.247.142:(none)): lisa 331 Please specify the password. //Password: 230 Login successful. ftp> ftp> ftp> ftp> ftp> ftp> put 999.txt 200 PORT command successful. Consider using PASV. 150 Ok to send data. 226 Transfer complete. ftp: Send 7 bytes, time 0.00 Second 7.00 KByte/Seconds. ftp>
View server authentication
[root@localhost vuser]# cd /etc/vsftpd/ [root@localhost vsftpd]# cd /opt/vuser [root@localhost vuser]# ls 999.txt [root@localhost vuser]#
Switch to another user
E:\>ftp 192.168.247.142 //Connect to 192.168.247.142. 220 (vsFTPd 3.0.2) 200 Always in UTF8 mode. //User (192.168.247.142:(none)): tom 331 Please specify the password. //Password: 230 Login successful. ftp> put 911.txt 200 PORT command successful. Consider using PASV. 150 Ok to send data. 226 Transfer complete. ftp: Send 7 bytes, time 0.00 Second 7.00 KByte/Seconds. ftp>
[root@localhost vuser]# ls -al total 20 drwx------. 3 vuser vuser 108 Dec 8 16:46 . drwxr-xr-x. 5 root root 142 Dec 8 15:13 .. -rw-------. 1 vuser vuser 7 Dec 8 16:46 911.txt -rw-------. 1 vuser vuser 7 Dec 8 16:39 999.txt -rw-r--r--. 1 vuser vuser 18 Aug 3 2017 .bash_logout -rw-r--r--. 1 vuser vuser 193 Aug 3 2017 .bash_profile -rw-r--r--. 1 vuser vuser 231 Aug 3 2017 .bashrc drwxr-xr-x. 4 vuser vuser 39 Oct 23 13:35 .mozilla
4.7 you can also create a configuration directory for users separately to specify their permissions
[root@localhost vuser]# vim /etc/vsftpd/vsftpd.conf user_config_dir=/etc/vsftpd/vu_dir 'Add to' [root@localhost vuser]# cd /etc/vsftpd [root@localhost vsftpd]# mkdir vu_dir [root@localhost vsftpd]# cd vu_dir/ [root@localhost vu_dir]# vim tom anon_umask=022
E:\>ftp 192.168.247.142 //Connect to 192.168.247.142. 220 (vsFTPd 3.0.2) 200 Always in UTF8 mode. //User (192.168.247.142:(none)): tom 331 Please specify the password. //Password: 230 Login successful. ftp> put 744.txt 200 PORT command successful. Consider using PASV. 150 Ok to send data. 226 Transfer complete. ftp>
[root@localhost vuser]# ls -al total 20 drwx------. 3 vuser vuser 138 Dec 8 16:53 . drwxr-xr-x. 5 root root 142 Dec 8 15:13 .. -rw-r--r--. 1 vuser vuser 0 Dec 8 16:53 744.txt -rw-------. 1 vuser vuser 0 Dec 8 16:50 755.txt -rw-------. 1 vuser vuser 7 Dec 8 16:46 911.txt -rw-------. 1 vuser vuser 7 Dec 8 16:39 999.txt -rw-r--r--. 1 vuser vuser 18 Aug 3 2017 .bash_logout -rw-r--r--. 1 vuser vuser 193 Aug 3 2017 .bash_profile -rw-r--r--. 1 vuser vuser 231 Aug 3 2017 .bashrc drwxr-xr-x. 4 vuser vuser 39 Oct 23 13:35 .mozilla